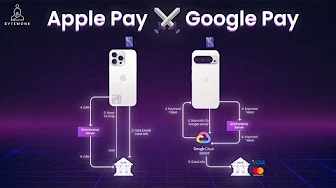
Mobile payment systems have revolutionized how we make purchases, but beneath their seamless interfaces lie sophisticated security architectures designed to protect your sensitive financial information. Apple Pay and Google Pay, the two dominant platforms in this space, take fundamentally different approaches to mobile payment system architecture while achieving the same goal: keeping your card details secure from potential threats.
The Fundamentals of Mobile Payment Security
Before diving into the specific implementations, it's important to understand the core security principle that both systems employ: tokenization. Rather than transmitting your actual credit card number during transactions, both platforms generate substitute values (tokens) that can be used for payments while keeping your real card details protected. However, the way they implement this tokenization reveals significant architectural differences in their security models.
Apple Pay: On-Device Tokenization Architecture
Apple Pay employs what security experts call an on-device tokenization model. This mobile payment architecture prioritizes keeping sensitive data localized to your device rather than in the cloud.
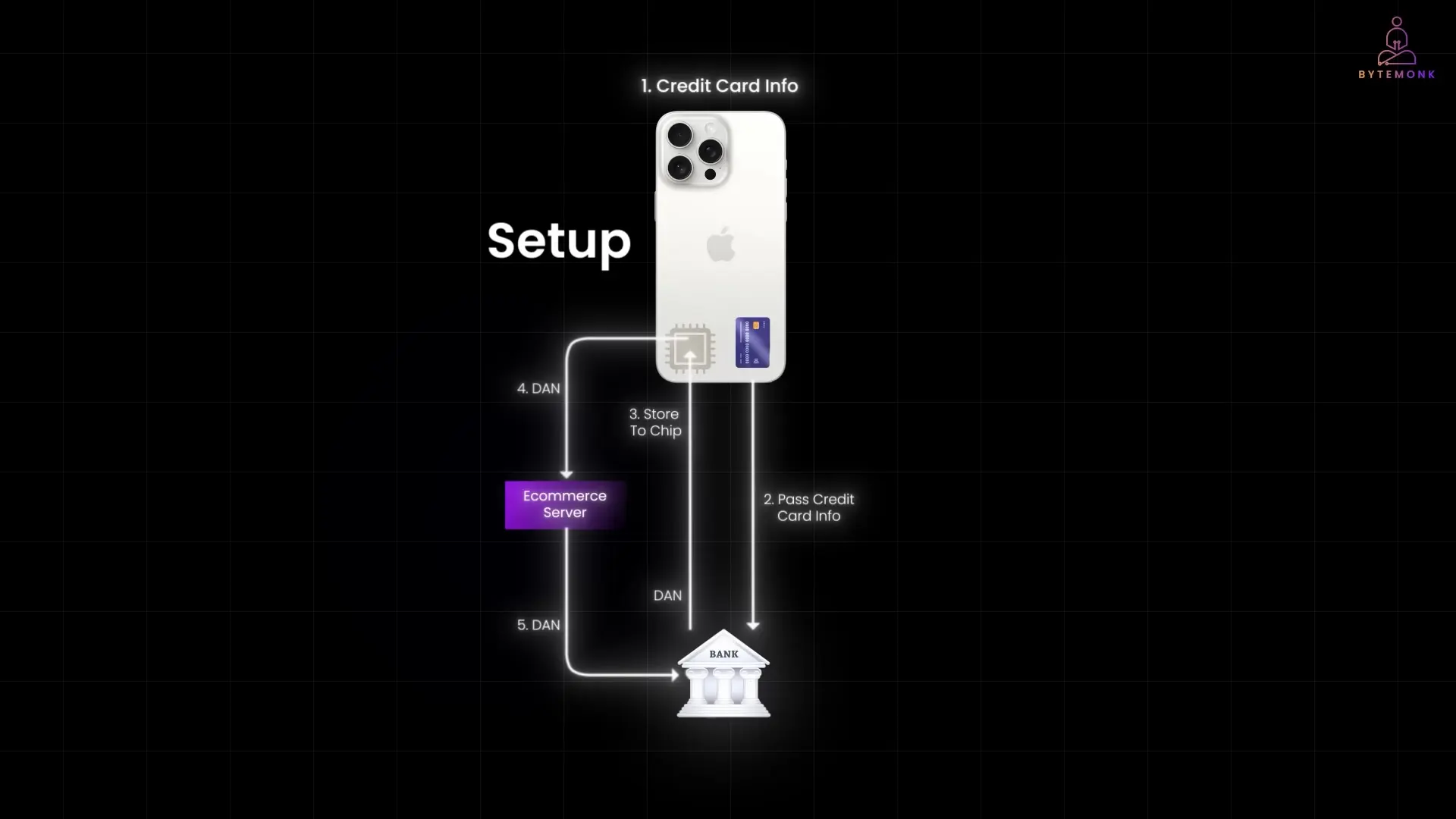
When you add a card to Apple Pay, the system follows these security protocols:
- Your credit card information is encrypted and sent to your card issuer or network (like Visa or Mastercard) for verification.
- Once verified, the bank or card network issues a Device Account Number (DAN) – a tokenized version of your card.
- This DAN is stored in a specialized hardware component called the Secure Element – essentially a dedicated chip isolated from the rest of your device's operating system.
- For all future transactions, only this tokenized DAN is used, never your actual card number.
This architecture creates a significant security advantage: your actual card details are only transmitted once during setup. After that, the system operates using the secure token, making Apple Pay functional even without an internet connection for in-store purchases. The secure element acts as a hardware-level vault, isolating payment credentials from potential software vulnerabilities in the main operating system.
Google Pay: Cloud-Based Tokenization Architecture
Google Pay takes a fundamentally different approach to mobile payment security architecture. Instead of storing payment credentials primarily on the device, Google employs a cloud-based tokenization model.
- When adding a card to Google Pay, your credit card information is encrypted and sent to Google's secure servers.
- Google verifies the card with your bank or card network.
- Rather than storing a permanent token on your device, Google stores your encrypted card information in its secure cloud infrastructure.
- During payment, your device requests a fresh payment token from Google's servers.
- This temporary token is what gets transmitted to merchants and payment processors, not your actual card details.
This cloud-centric mobile payment app architecture creates a different security paradigm. Your device becomes more of a requestor of tokens rather than a storage vault for them. This approach enables greater cross-device flexibility but requires an internet connection to generate fresh payment tokens for transactions.
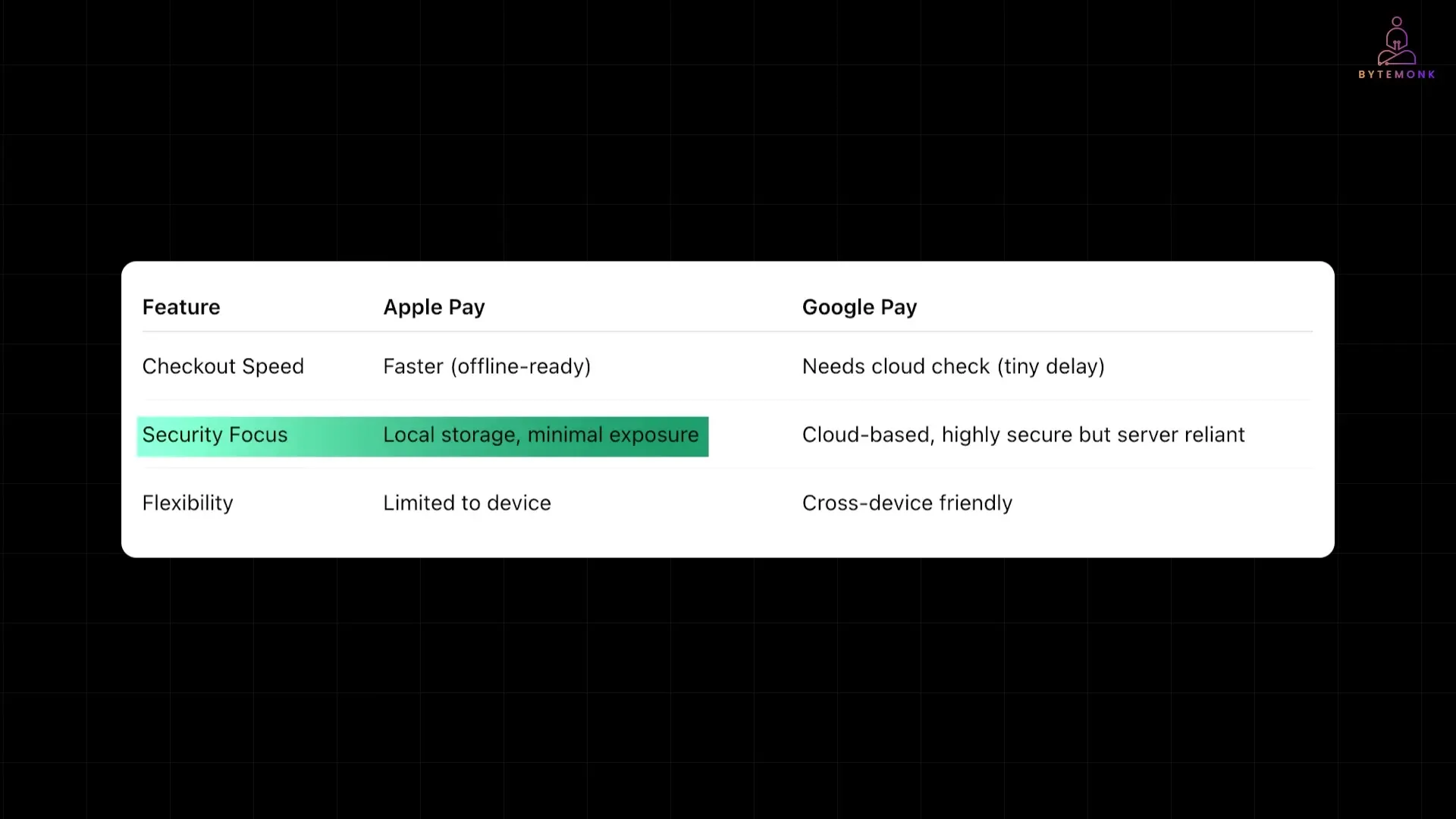
Architectural Trade-offs in Mobile Payment Systems
Both mobile payment system architectures present distinct advantages and limitations that impact security, convenience, and functionality.
Speed and Offline Capability
Apple Pay's on-device architecture typically delivers faster checkout experiences since all necessary components for authentication and tokenization are already present on the device. This also enables offline payments in situations where internet connectivity is limited or unavailable.
Google Pay's cloud-dependent model requires a network connection to request fresh payment tokens, which may introduce millisecond delays. In areas with poor connectivity, this architectural choice can impact the payment experience.
Security Implications
From a security perspective, Apple Pay's architecture minimizes attack surface by keeping sensitive data localized to the device's secure element, which is hardware-isolated from potential operating system vulnerabilities. Your payment credentials rarely leave your device, reducing transmission risks.
Google Pay's architecture places greater emphasis on cloud security, requiring Google to maintain robust server-side protections against potential cyber threats. While this centralizes security management, it also creates a more attractive target for attackers seeking access to payment credentials.
Device Independence and Recovery
Apple Pay's device-bound architecture means your payment credentials are tightly coupled to your specific device. If you lose your phone, you'll need to go through complete reverification to set up your cards on a new device, as the secure tokens don't transfer.
Google Pay's cloud architecture offers greater flexibility for cross-device usage. Since your credentials are primarily stored in Google's cloud infrastructure, transitioning to a new device is typically more seamless, requiring only authentication to your Google account.
The Technical Implementation of Secure Network Protocols
Both mobile payment systems employ sophisticated secure network protocols to protect data in transit, though they implement them differently based on their architectural models.
Apple Pay's Secure Network Implementation
When an Apple Pay transaction occurs, the system creates a dynamic security code unique to each transaction. This one-time code, combined with the Device Account Number, forms a secure payment packet that's transmitted using industry-standard protocols like NFC (Near Field Communication) for in-store payments or TLS (Transport Layer Security) for online transactions.
The payment terminal receives this encrypted packet but never sees your actual card details. The transaction data passes through the payment network to your bank, which can decrypt the token using keys established during the initial setup process.
Google Pay's Network Security Framework
Google Pay relies heavily on TLS/SSL encryption for all communications between your device, Google's servers, and payment processors. When you initiate a transaction, your device establishes a secure connection to Google's servers to request a payment token.
This token is generated using cryptographic techniques that make it valid only for a specific transaction within a limited timeframe. The token is then transmitted to the merchant, who forwards it to the payment processor. The processor communicates with Google's token service to validate the transaction before final approval from your bank.
The Future of Mobile Payment Architectures
As mobile payment technologies continue to evolve, we're likely to see hybrid architectures that combine the strengths of both approaches. Emerging technologies like zero-knowledge proofs may enable systems that maintain Apple Pay's strong local security while offering Google Pay's flexibility across devices.
These hybrid mobile payment gateway architectures might allow credentials to remain securely stored on devices while enabling proof of validity across multiple services without exposing the actual data. This would reduce reliance on centralized authorities while maintaining robust security.
Conclusion: Choosing the Right Mobile Payment Architecture
The architectural differences between Apple Pay and Google Pay highlight a fundamental trade-off in mobile payment systems: device-bound security versus cloud-enabled flexibility. For users who prioritize maximum security and offline capability, Apple Pay's architecture offers advantages. For those who value cross-device flexibility and seamless transitions between devices, Google Pay's cloud-based approach may be preferable.
Both systems have successfully implemented secure mobile payment architectures that protect users from common threats while making digital payments convenient. As these technologies continue to evolve, we can expect to see further innovations in mobile payment security protocols that balance security, privacy, and convenience in increasingly sophisticated ways.
Understanding these architectural differences helps users make informed decisions about which mobile payment system aligns best with their personal security preferences and usage patterns in an increasingly cashless world.
Let's Watch!
Apple Pay vs Google Pay: Inside the Security Architecture Battle
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence