
API security vulnerabilities can have serious consequences for businesses and their customers. In this in-depth case study, we'll examine a particularly concerning example of API security flaws discovered in McDonald's India's delivery system. These vulnerabilities not only serve as a warning but also provide valuable insights into how developers can better secure their APIs against similar threats.
The McDonald's India M-Delivery System
McDonald's India operates a custom web application called MCD Delivery that allows customers to order food for delivery, dine-in, or takeout. This system is immensely popular in India, with over 10 million downloads on Google Play and ranking 16th in the Food & Drink category on the Apple App Store. Unlike McDonald's in many other countries, the Indian operation developed their own unique web app specifically for their market.
The application is built using Angular, a popular single-page application framework that's well-suited for high-interactivity consumer-facing apps. While the choice of technology was appropriate, the implementation contained several critical security vulnerabilities that could be exploited by malicious actors.
Broken Object Level Authorization: The Gateway Vulnerability
The most significant vulnerability discovered was Broken Object Level Authorization (BOLA), which is considered a gateway to other API security vulnerabilities. BOLA occurs when an application fails to verify that a user has the appropriate permissions to access or modify a specific object or resource. In the OWASP API Security Top 10 vulnerabilities list, BOLA is consistently ranked as one of the most critical security risks.
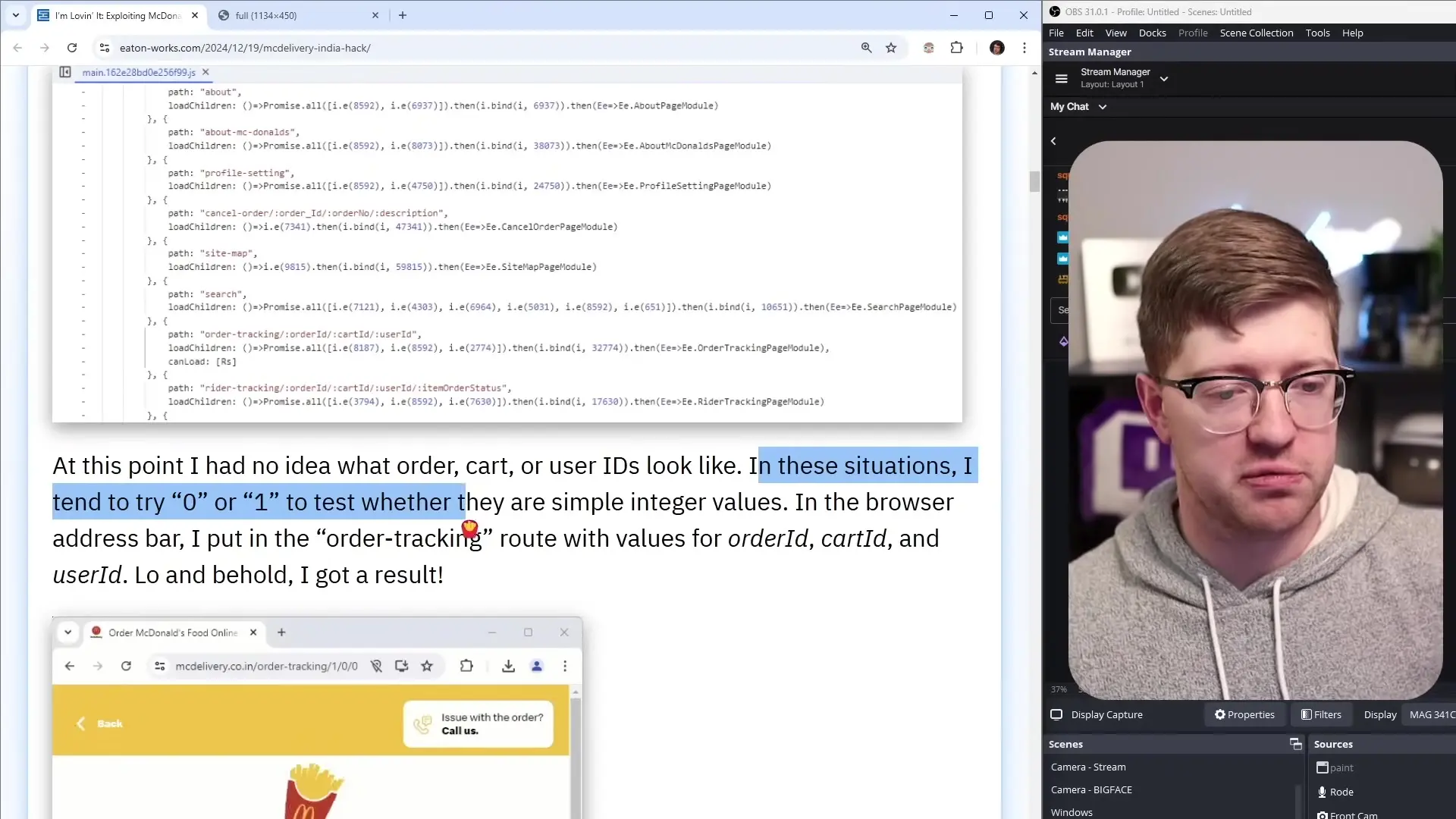
In the case of McDonald's India delivery system, the researcher discovered that by simply manipulating order IDs in the URL, they could access order details belonging to other users. This vulnerability was exploited through the order tracking route:
/order-tracking/{orderId}/{cartId}/{userId}Despite including parameters for orderId, cartId, and userId in the URL, the application only validated the orderId parameter. This meant that anyone could access any order in the system by simply incrementing the orderId value, regardless of whether they were the legitimate owner of that order.
The Extent of the Vulnerabilities
Further investigation revealed a range of exploitable vulnerabilities in the McDonald's India delivery system. These security flaws allowed unauthorized users to:
- Order any number of food items for one rupee (approximately one US cent)
- Steal, hijack, or redirect other people's deliveries through carefully timed API calls
- Retrieve details of any order in the system
- Track orders that were in the "on the way" status
- Download invoices for any order in the system
- Submit feedback for orders that were not their own
- View administrative KPI reports and sensitive driver information
These vulnerabilities represent a serious breach of security best practices and demonstrate how a single flaw like BOLA can cascade into multiple exploitable security issues.
Authentication Flaws: JWT Implementation Issues
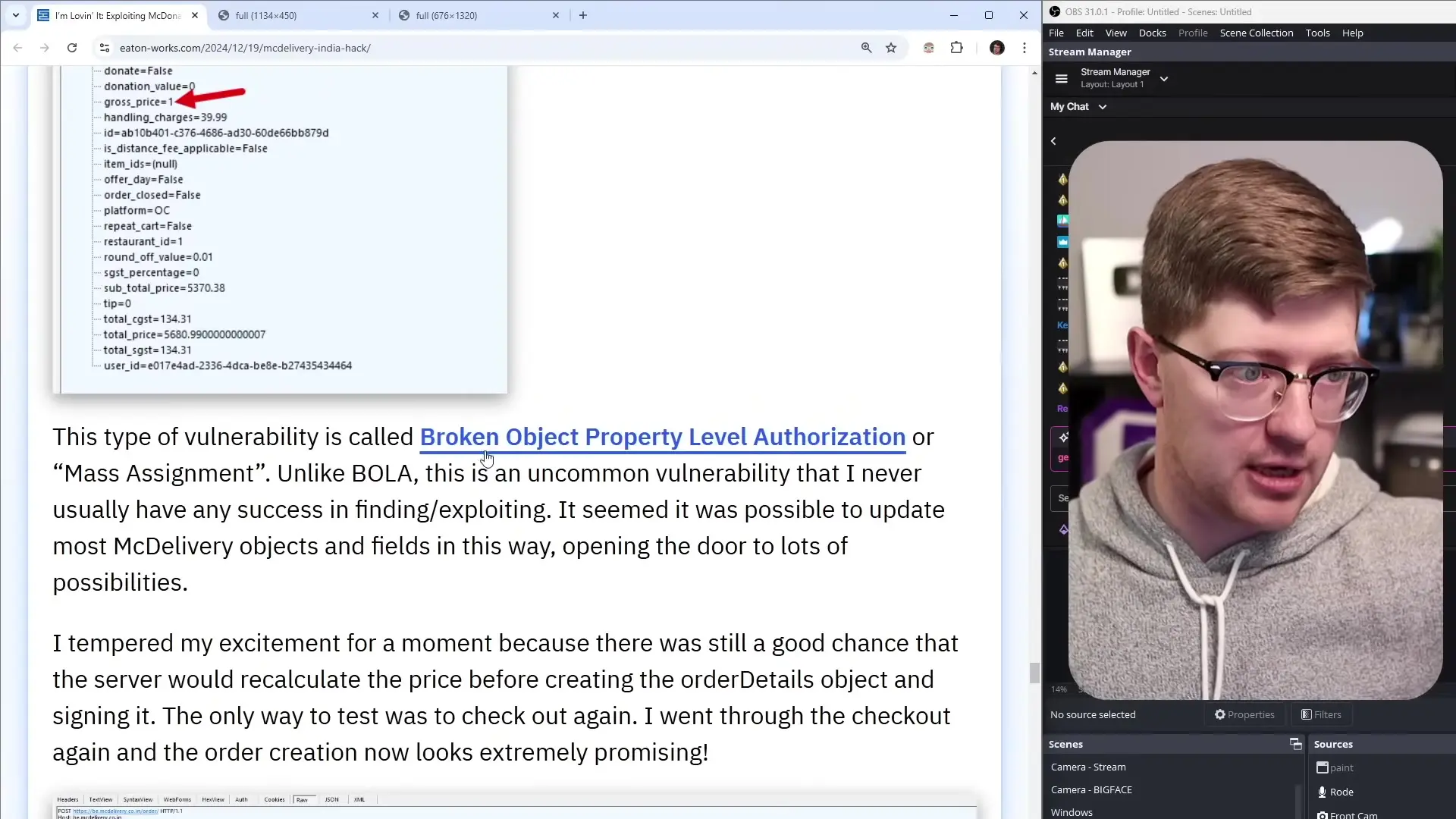
The McDonald's India delivery system did implement JSON Web Tokens (JWT) for authentication, which is generally considered a secure approach. However, the implementation had critical flaws that undermined its effectiveness as a security measure.
Even without creating an account or logging in, visitors to the site were automatically assigned a "guest" JWT token. This token was generated by a separate subdomain and was used for API authentication. While using JWT tokens is a good practice, the system failed to properly validate that the token holder had the appropriate permissions to access specific resources.
As one security researcher noted: "They're doing JWT to get you access to the API but not doing any authentication in the back end to confirm that it actually matches the order you're looking at."
Sequential IDs: A Recipe for Enumeration Attacks
Another significant security flaw was the use of sequential order IDs. This made it trivially easy for an attacker to enumerate all orders in the system by simply incrementing the order ID value in their requests. This type of predictable resource location is a common API vulnerability that can lead to unauthorized access to sensitive data.
The researcher demonstrated this vulnerability by accessing order details, leaving reviews on orders that weren't their own, and even retrieving other users' reviews by manipulating the review ID parameter in API calls.
Key API Security Lessons from the McDonald's India Case
This case study highlights several important API security best practices that developers should implement to protect their applications from similar vulnerabilities:
- Implement proper object-level authorization checks to ensure users can only access resources they own or have permission to view
- Use non-predictable, non-sequential IDs for resources to prevent enumeration attacks
- Validate all parameters in API requests, not just some of them
- Ensure that authentication mechanisms like JWT are properly integrated with authorization checks
- Implement rate limiting to prevent brute force attacks against API endpoints
- Conduct regular security audits and penetration testing of API implementations
- Consider implementing a bug bounty program to encourage responsible disclosure of vulnerabilities
The Impact of API Security Breaches
The vulnerabilities in McDonald's India delivery system could have had serious consequences if exploited by malicious actors. These potential impacts include:
- Financial losses due to fraudulent orders placed for minimal cost
- Theft of customer data, including names, addresses, and order history
- Compromise of delivery driver information, potentially putting their safety at risk
- Damage to brand reputation and customer trust
- Potential regulatory penalties for failing to protect user data
This isn't the first time McDonald's India has faced security issues. In 2017, their delivery app reportedly leaked data of approximately 2.2 million users. The discovery of these new vulnerabilities suggests that comprehensive security improvements were needed across their systems.
Tools and Techniques for API Security Testing
To identify similar vulnerabilities in your own APIs, consider implementing these security testing approaches:
- Static Application Security Testing (SAST) to analyze code for security vulnerabilities
- Dynamic Application Security Testing (DAST) to test running applications for exploitable vulnerabilities
- API-specific security testing tools like OWASP ZAP, Burp Suite, or Postman
- Manual penetration testing by security professionals
- Automated security scanning integrated into CI/CD pipelines
Resources like the OWASP API Security Top 10 and Web Security Academy GraphQL API vulnerabilities guides provide valuable information for developers looking to secure their APIs against common threats.
Conclusion: The Importance of Comprehensive API Security
The vulnerabilities discovered in McDonald's India delivery system serve as a stark reminder of the importance of comprehensive API security. Broken Object Level Authorization (BOLA) is considered a gateway to other API security vulnerabilities, and this case clearly demonstrates why. A single flaw in authorization logic cascaded into multiple exploitable vulnerabilities that could have had serious consequences for both the business and its customers.
By implementing proper authorization checks, using non-predictable resource identifiers, and ensuring that authentication mechanisms are correctly integrated with authorization logic, developers can significantly reduce the risk of similar vulnerabilities in their own APIs. Regular security testing and a commitment to addressing vulnerabilities promptly are essential components of a robust API security strategy.
As APIs continue to form the backbone of modern web and mobile applications, securing them against common vulnerabilities must be a priority for development teams. The lessons from this case study provide valuable insights that can help developers build more secure APIs and protect their users' data from potential breaches.
Let's Watch!
7 Critical API Security Vulnerabilities Exposed in McDonald's India Delivery System
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence