
A recent series of security breaches in a popular social verification application has exposed critical flaws in its architecture, leaking personally identifiable information (PII) of thousands of users. These incidents highlight fundamental security oversights that every developer should understand to prevent similar vulnerabilities in their own applications.
The First Breach: Unsecured Storage Buckets
The first major security incident involved improperly secured cloud storage. The application used Firebase buckets to store verification documents, including government IDs and selfies submitted by users during the verification process. Unfortunately, these storage buckets were configured with inadequate access controls.
The Firebase buckets lacked proper authentication requirements, allowing anyone with basic access to download the stored files. This meant that approximately 13,000 users had their personal identification documents exposed to potential unauthorized access.
What makes this breach particularly concerning is that many of the exposed images contained EXIF data - metadata embedded in photos that can include precise GPS coordinates of where the photos were taken. This effectively exposed not just users' identities but potentially their home addresses or other sensitive locations.
The Second Breach: Exposed API Keys
Just when users thought the situation couldn't get worse, a second security flaw was discovered. The application was providing API keys directly to users on the frontend, violating fundamental security principles of application design.
These exposed API keys allowed anyone to query the database directly and access private messages between users, including sensitive conversations about personal matters. This represents a complete breakdown of proper access control and authentication architecture.
Fundamental Security Architecture Flaws
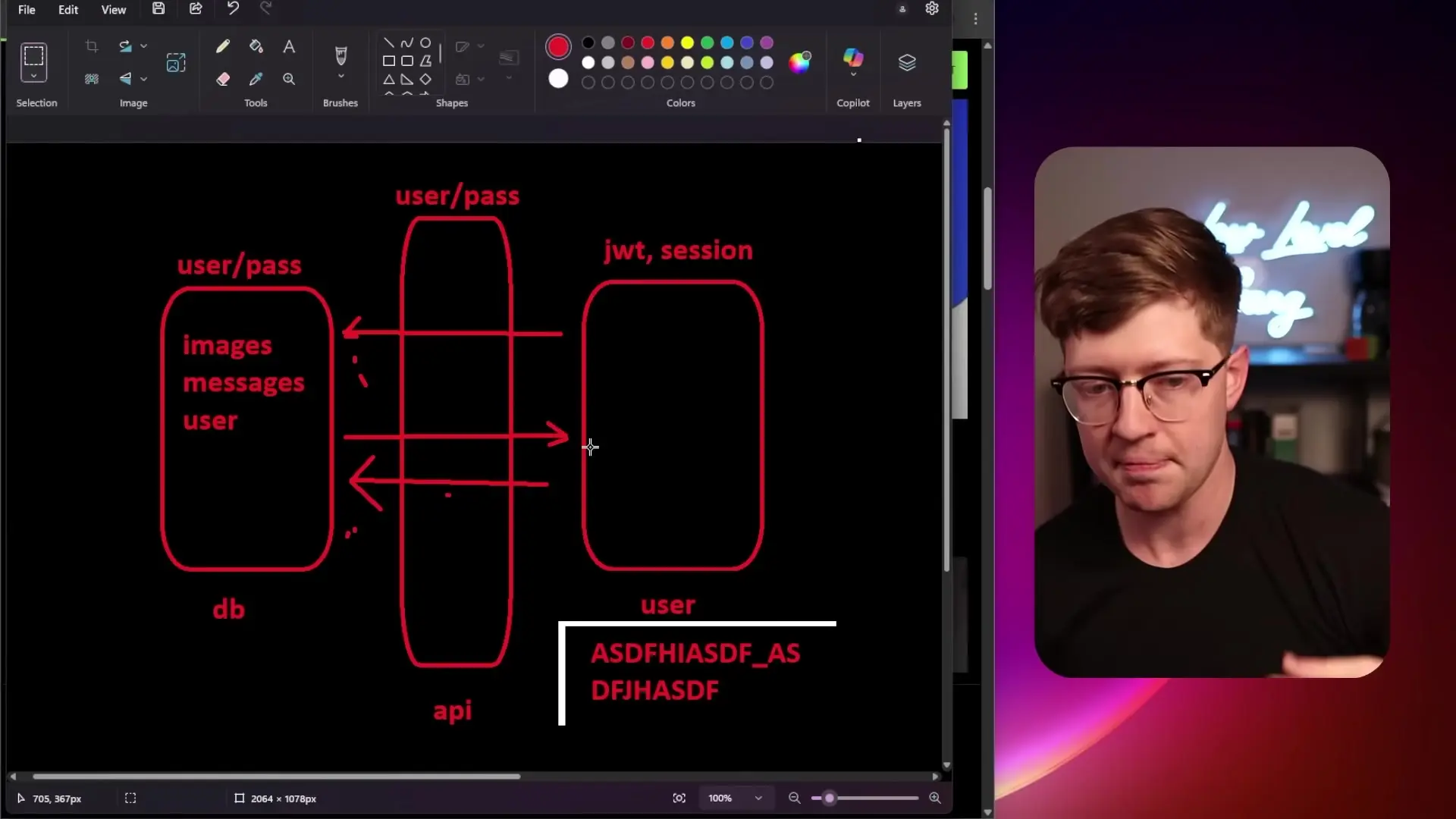
Both breaches reveal critical misunderstandings of basic security principles. In a properly designed application, sensitive credentials like database passwords and API keys should never be exposed to end users. Instead, they should be securely stored in environment variables or security vaults accessible only to backend services.
The proper architecture would include:
- A database with credentials known only to the backend API
- An API layer that handles authentication and authorization
- User-specific tokens or cookies for maintaining authenticated sessions
- Proper access control checks on every database query
- Data segregation ensuring users can only access their own data
Lessons for Developers
These security incidents provide valuable lessons for all developers working on applications that handle sensitive user data:
- Never store API keys, database credentials, or other secrets in client-side code
- Always configure proper access control lists (ACLs) for cloud storage services
- Remove EXIF data from user-uploaded images before storage
- Implement proper authentication and authorization at every layer
- Ensure database queries are scoped to the authenticated user's permissions
- Follow through on data deletion promises made to users
- Treat security as a fundamental requirement, not an add-on feature
Proper Authentication Flow
A secure application should implement authentication flows that maintain clear separation between user authentication and backend service credentials:
// FRONTEND (Client-side)
// User provides credentials
const loginUser = async (email, password) => {
const response = await fetch('/api/auth/login', {
method: 'POST',
headers: { 'Content-Type': 'application/json' },
body: JSON.stringify({ email, password })
});
if (response.ok) {
const { token } = await response.json();
// Store JWT token securely (HttpOnly cookie is best)
// Never store API keys or database credentials
localStorage.setItem('authToken', token);
return true;
}
return false;
};// BACKEND (Server-side)
// API credentials stay on the server
const authenticateUser = async (req, res) => {
const { email, password } = req.body;
try {
// Database credentials never exposed to client
const user = await db.users.findOne({ email });
if (user && await bcrypt.compare(password, user.passwordHash)) {
// Generate token that only identifies the user
// NOT a token that provides direct database access
const token = jwt.sign({ userId: user.id }, process.env.JWT_SECRET);
return res.json({ token });
}
return res.status(401).json({ error: 'Invalid credentials' });
} catch (error) {
return res.status(500).json({ error: 'Server error' });
}
};
Firebase Security Best Practices
When using Firebase or similar cloud services, developers should follow these security best practices:
- Configure proper security rules that restrict access based on user authentication
- Never expose Firebase API keys with unrestricted permissions in client-side code
- Use Firebase Authentication to manage user sessions properly
- Implement data validation both on the client and server sides
- Regularly audit your security rules and access patterns
- Pay attention to security warnings from the Firebase console
- Use Firebase Admin SDK on the server for privileged operations
// Secure Firebase Storage Rules Example
{
"rules": {
"users": {
"$uid": {
// Users can only read/write their own data
".read": "$uid === auth.uid",
".write": "$uid === auth.uid"
}
},
"messages": {
"$messageId": {
// Messages can only be read by participants
".read": "data.child('participants').child(auth.uid).exists()",
// New messages must include the author's ID
".write": "newData.child('author').val() === auth.uid"
}
}
}
}Conclusion: Security as a Priority, Not an Afterthought
The team app security incidents serve as a stark reminder that security cannot be an afterthought in application development. When applications handle sensitive user data, proper security architecture must be a foundational consideration from day one.
As more applications are developed rapidly, it's crucial that developers maintain focus on security fundamentals. Users trust applications with their most sensitive information - from identification documents to private conversations. Breaching that trust through preventable security flaws can have serious consequences both for users and for the reputation of the application.
By learning from these incidents and implementing proper security practices, developers can build applications that both provide value to users and protect their sensitive information.
Let's Watch!
Critical Security Flaws in Team App: What Every Developer Should Learn
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence