
A sophisticated vulnerability chain targeting WhatsApp has recently been discovered and patched, demonstrating how multiple seemingly minor security issues can be combined to create devastating zero-click attacks. This case study provides valuable insights into modern exploit chains and highlights critical security considerations for developers working with image processing libraries and messaging applications.
Understanding Zero-Click Attacks
Zero-click attacks represent one of the most dangerous threat vectors in mobile security. Unlike traditional attacks requiring user interaction (such as clicking a malicious link), zero-click exploits can execute code on a victim's device without any action from the user. What makes this particular WhatsApp vulnerability especially concerning is the application's fundamental purpose: receiving messages from anyone.
In this scenario, anyone who could send a WhatsApp message to a target could potentially gain code execution privileges on the recipient's device, enabling them to steal data and maintain persistent access. The implications for privacy and security are profound, particularly for high-risk individuals who rely on messaging apps for sensitive communications.
The Vulnerability Chain: How It Worked
What makes this case particularly interesting from a development security perspective is that it wasn't a single vulnerability but a chain of exploits working together. The attack combined two separate issues:
- A WhatsApp vulnerability involving incomplete authorization of linked devices synchronization messages
- A vulnerability in Apple's ImageIO framework affecting the DNG (Digital Negative) image format
The WhatsApp vulnerability (CVE with a CVSS score of 5.4) allowed attackers to make a target's device process content from an arbitrary URL. While this alone wasn't enough for code execution, it created the necessary conditions for the second part of the attack.
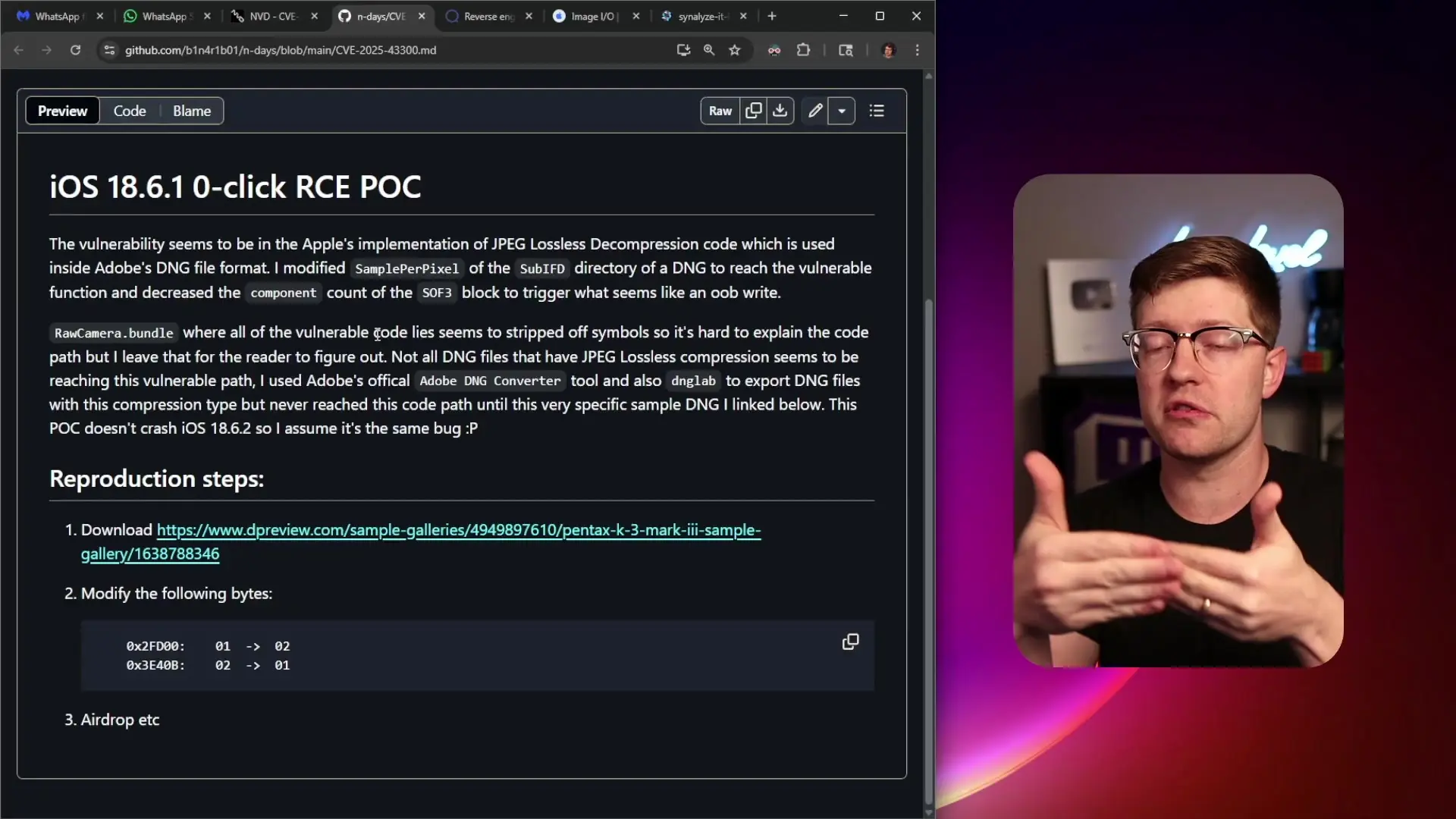
The ImageIO Vulnerability: A Parser's Nightmare
The second component involved Apple's ImageIO library, which handles image processing across iOS. The vulnerability specifically affected how the system processed DNG files—an open lossless RAW image format used primarily by photographers and visual professionals.
The ImageIO framework is fundamental to iOS operation, as it's responsible for parsing and rendering images across the entire operating system. When any device encounters an image, it must process that image to display it correctly, making image parsers a prime target for attackers.
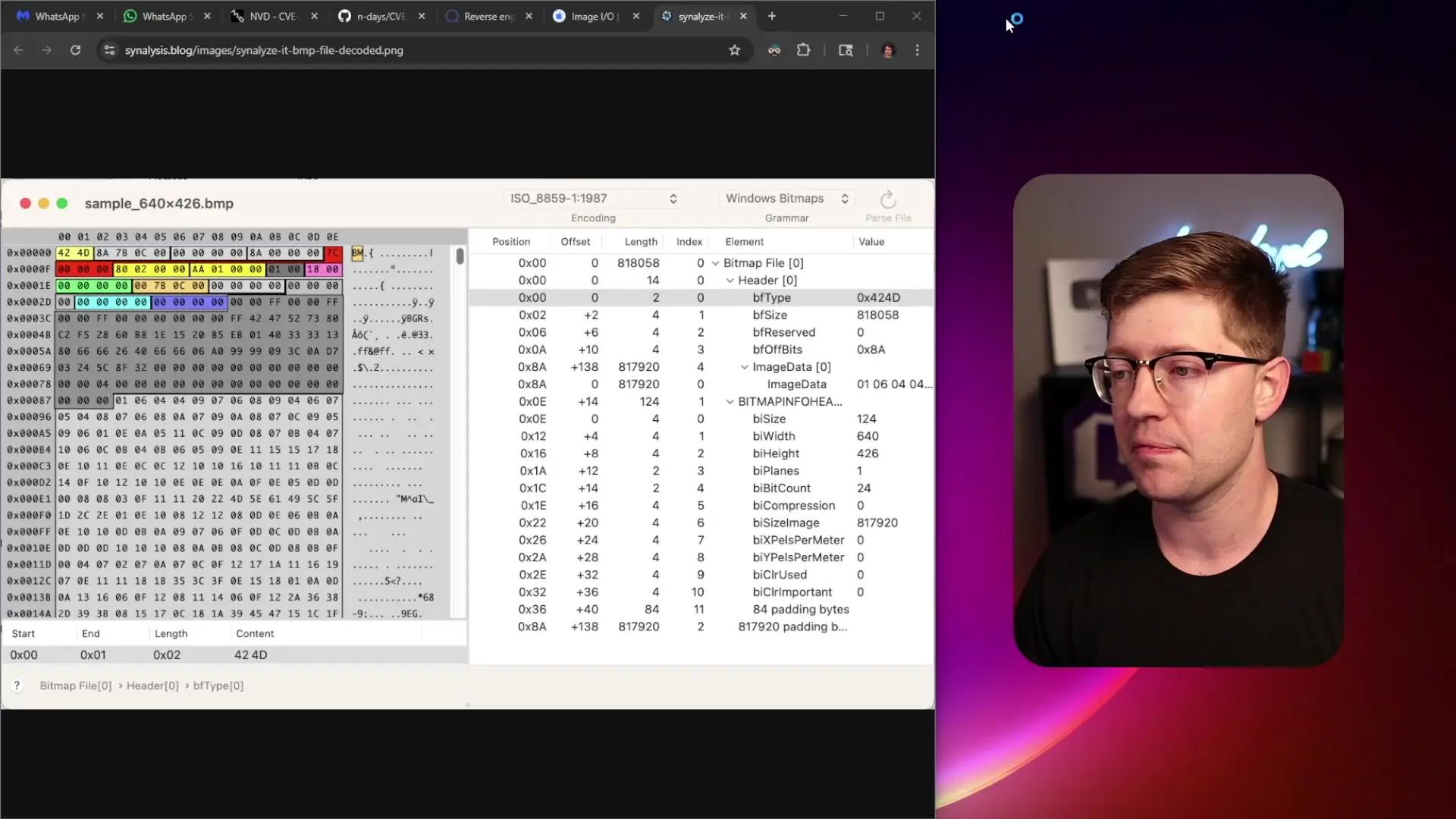
Technical Details of the DNG Vulnerability
The vulnerability in the DNG parser stemmed from a mismatch between the number of components declared in an image and the actual buffer allocation. When processing a specially crafted DNG file, the code would assume there were two components based on the samples per pixel value, but would only allocate buffer space for one component.
This discrepancy led to an out-of-bounds write vulnerability during the decompression process. When the parser attempted to decompress the image data, it would write beyond the allocated buffer, allowing attackers to place data in memory locations they shouldn't have access to—a classic memory corruption vulnerability that could lead to code execution.
// Pseudo-code illustrating the vulnerability
void processImage(DNG_Image *image) {
// Bug: Buffer allocation based on incorrect assumption
int bufferSize = image->samplesPerPixel; // Should be samplesPerPixel * numComponents
char *buffer = malloc(bufferSize);
// Later during decompression
for (int i = 0; i < image->samplesPerPixel * image->numComponents; i++) {
// This writes beyond buffer boundaries when numComponents > 1
buffer[i] = decompressedData[i];
}
}Why This Vulnerability Chain Is Significant
This exploit chain demonstrates several important security concepts that developers should understand:
- Attack surface expansion: The WhatsApp vulnerability alone wasn't severe, but it expanded the attack surface by allowing remote content loading
- Parser vulnerabilities: Image parsers remain a high-value target due to their complexity and necessity for automatic processing
- Less-common formats: The vulnerability existed in a less commonly used image format (DNG), highlighting how attackers target less scrutinized code paths
- Automatic processing: The most dangerous aspect was that image processing happens automatically, requiring no user interaction
- Chaining tactics: Modern exploits often chain multiple lower-severity vulnerabilities to achieve high-impact results
Development Best Practices to Prevent Similar Vulnerabilities
This case offers valuable lessons for developers working on applications that process user-supplied content:
- Implement strict input validation for all content, especially from untrusted sources
- Use memory-safe programming practices and languages where possible
- Carefully audit code that handles less common file formats, as these often receive less security scrutiny
- Employ fuzzing and other automated testing techniques specifically designed to find parser vulnerabilities
- Implement proper bounds checking for all buffer operations
- Consider sandboxing components that process untrusted data
- Maintain a security-first mindset when designing synchronization features between devices
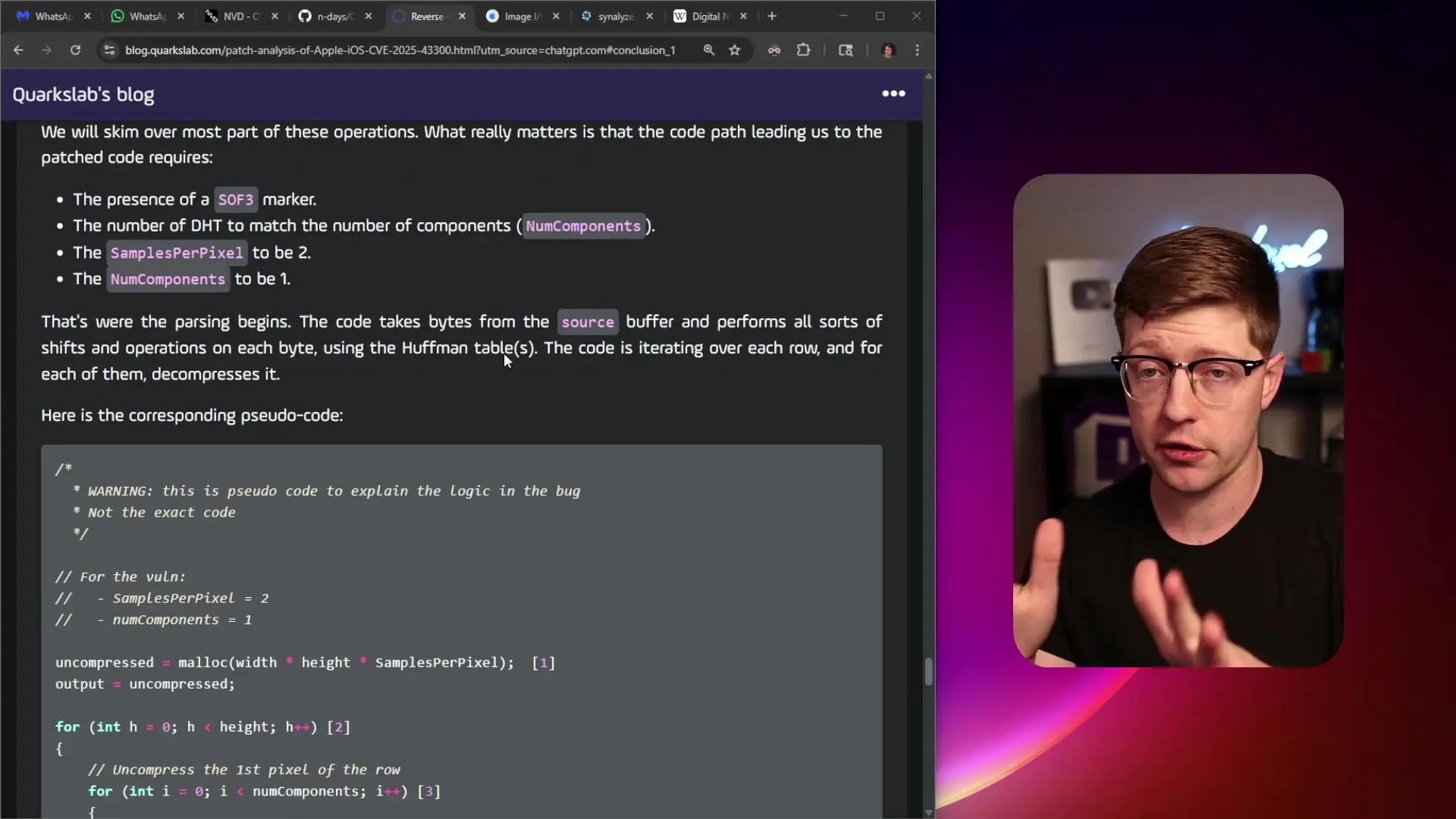
The Challenge of Finding These Vulnerabilities
What makes these vulnerabilities particularly challenging to discover through standard testing is their dependency on specific edge cases. The DNG vulnerability required a precise combination of parameters—specific samples per pixel values combined with mismatched component numbers—and proper compression to trigger the issue.
Traditional fuzzing techniques might miss these vulnerabilities because they depend on generating valid compressed data that can be properly decompressed while still triggering the buffer overflow. This highlights the sophisticated nature of modern exploit development and the challenges faced by security teams.
Conclusion: Implications for Developers
The WhatsApp/ImageIO vulnerability chain serves as an important reminder that security vulnerabilities often exist at the intersection of multiple systems. For developers, this case emphasizes the importance of considering how your code might interact with system libraries and other applications, potentially creating unexpected attack vectors.
As applications continue to become more complex and interconnected, understanding these vulnerability chains becomes increasingly important for creating secure software. By implementing rigorous security testing, proper input validation, and defensive programming techniques, developers can help protect their users from these sophisticated attacks.
Let's Watch!
7 Critical Security Lessons from the WhatsApp Zero-Click Exploit
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence