FortiWeb, a popular web application firewall (WAF), recently faced significant security challenges with two critical CVEs that expose dangerous authentication bypass vulnerabilities. These vulnerabilities in binary firmware could potentially allow attackers to gain administrative access to systems protected by FortiWeb. This article examines the technical details of one particularly concerning authentication bypass vulnerability and explores how such vulnerabilities could be automatically detected and prevented.
Understanding Web Application Firewalls
Before diving into the vulnerability, it's important to understand what a Web Application Firewall (WAF) does. A WAF like FortiWeb sits between the internet and your web application, acting as a filter that inspects all incoming traffic. It analyzes requests for suspicious patterns that might indicate attacks such as SQL injection, cross-site scripting, or other common web application vulnerabilities.
The primary purpose of a WAF is to distinguish between legitimate traffic (normal users accessing your application) and potentially malicious requests that could compromise your application's security. Given this critical security role, vulnerabilities in WAFs themselves can have severe consequences.
The FortiWeb Authentication Bypass Vulnerability
The vulnerability in question affects FortiWeb's authentication mechanism. When users authenticate to the FortiWeb application, they receive an authentication cookie containing several key fields:
- era - Appears to indicate which cryptographic era or algorithm version is being used
- payload - Contains the actual session data (user identity, role, permissions)
- offash - A Hash-based Message Authentication Code (HMAC) that verifies the cookie's integrity
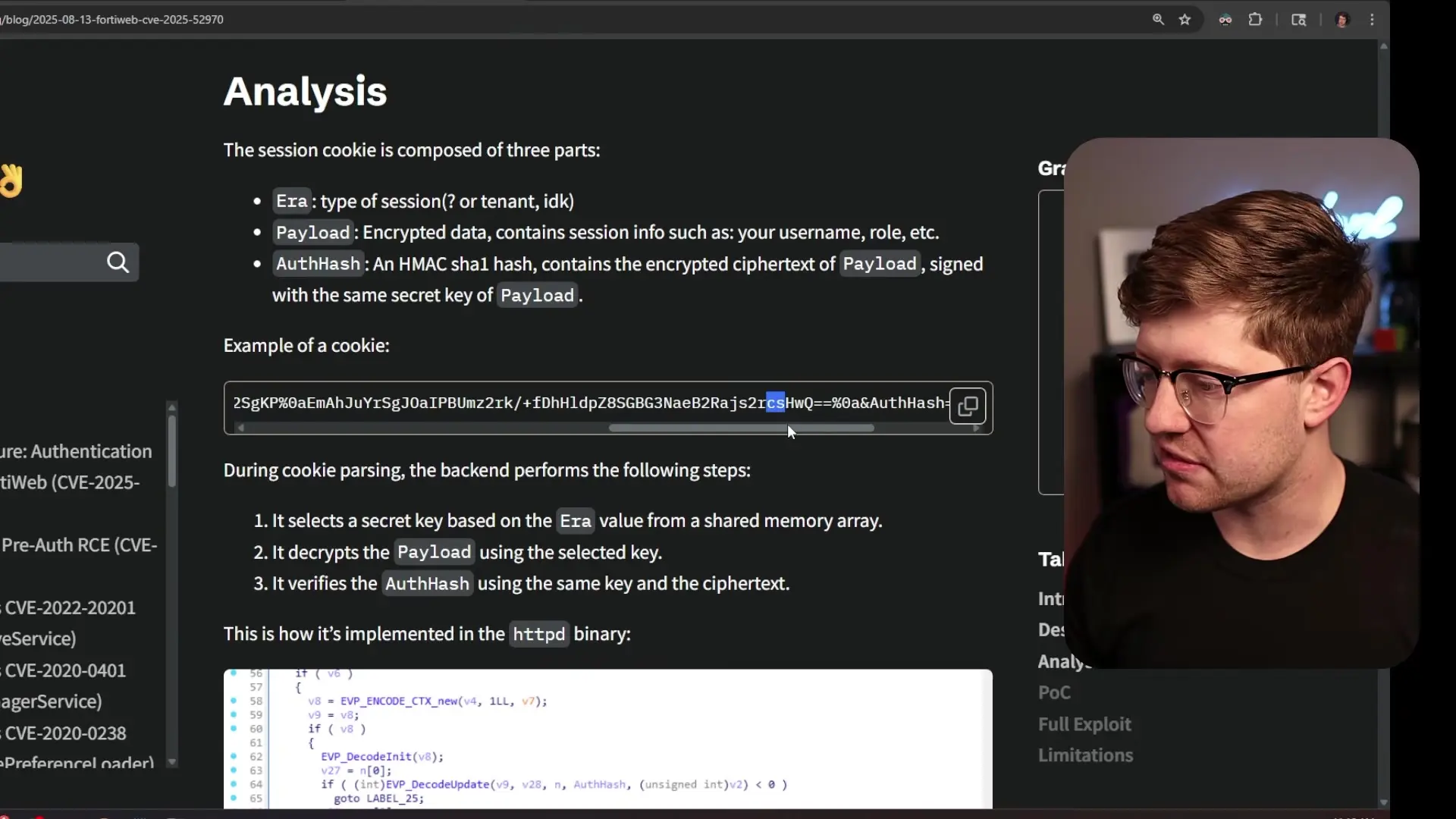
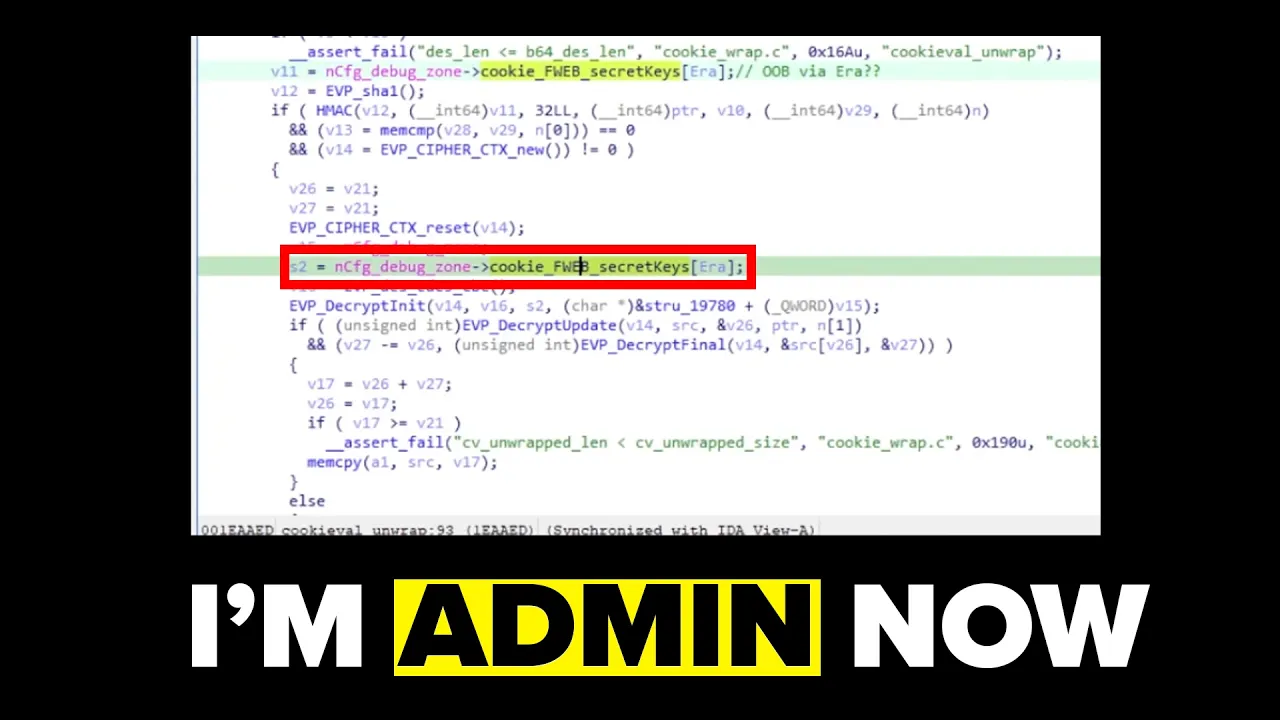
The vulnerability stems from how FortiWeb handles the 'era' field in the cookie. This field is supposed to act as an index into an array of secret keys used to validate the HMAC. However, the critical flaw is that the application doesn't validate this index value before using it to access the key array.
Technical Breakdown of the Authentication Bypass
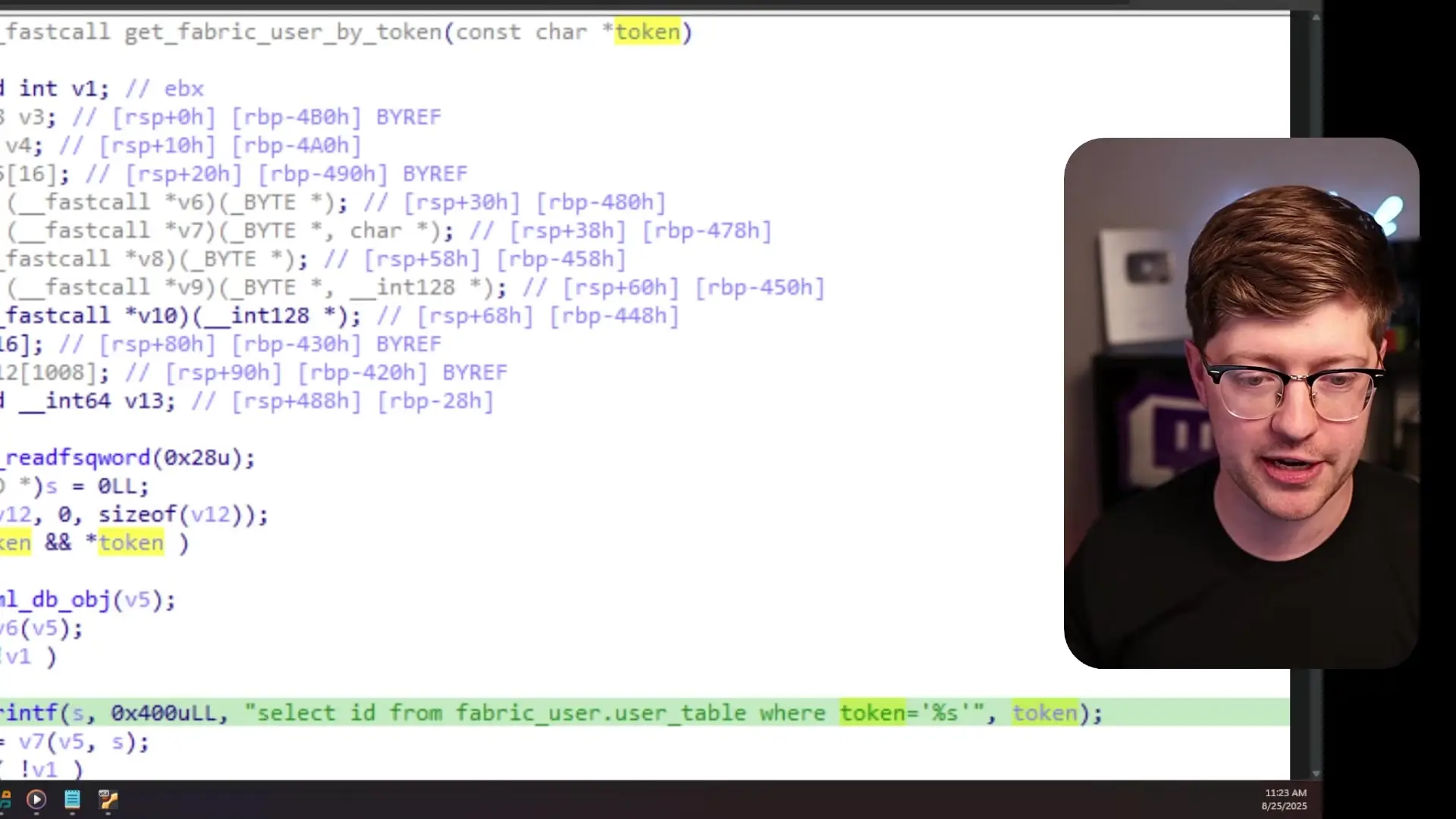
The security researcher who discovered this vulnerability performed reverse engineering on the FortiWeb binary. Using IDA Pro, they analyzed the disassembled code and found that the HMAC validation process works as follows:
- The application extracts the 'era' value from the cookie
- This value is used as an index into an array called 'cookie_fb_secret_keys'
- The key at that index is retrieved and used to validate the HMAC
- If the calculated HMAC matches the one in the cookie, authentication succeeds
The critical vulnerability is an out-of-bounds read: there's no validation that the 'era' value stays within the bounds of the key array. By manipulating this value, an attacker can force the application to use a predictable key (such as all zeros) for HMAC validation.
Once attackers know which key is being used, they can forge their own authentication cookies with arbitrary payload data, effectively granting themselves administrative privileges in the application.
Exploiting the Authentication Bypass Vulnerability
The exploitation process involves several steps:
- The attacker sends a specially crafted request with a manipulated 'era' value
- This forces the application to use a predictable key (like all zeros) for HMAC validation
- With knowledge of the key, the attacker can forge their own cookie with administrative privileges
- The forged cookie is then used to access authenticated APIs in the firewall
While there are some limitations (the user needs to be active for the session to run, and some brute forcing may be required), this vulnerability represents a serious security risk for organizations using FortiWeb.
Detecting Authentication Bypass Vulnerabilities in Binary Firmware
This type of vulnerability raises an important question: how can developers automatically detect authentication bypass vulnerabilities in binary firmware before they become exploitable issues?
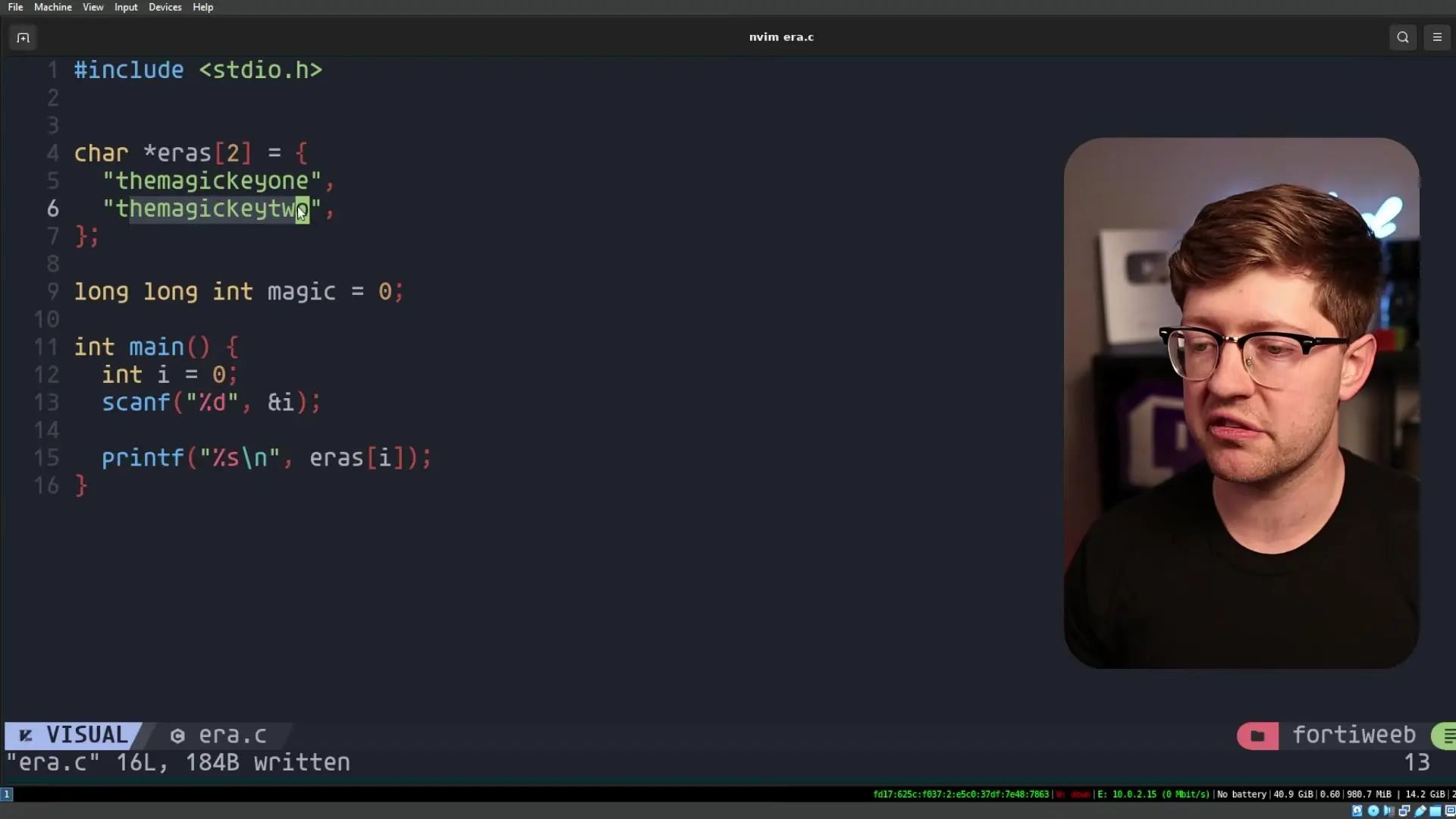
One effective approach is using memory safety tools like AddressSanitizer (ASAN). ASAN is a runtime memory error detector that can identify various memory-related issues, including out-of-bounds reads and writes.
// Simplified example of vulnerable code
char* keys[2] = {"MAGIC_SECRET_KEY", "NORMAL_KEY"};
void authenticate(int era_value) {
// No validation of era_value before using it as an index
char* key = keys[era_value];
// Use key for HMAC validation
}By compiling code with ASAN enabled (using the -fsanitize=address flag in Clang), developers can detect potential out-of-bounds reads during testing. When an out-of-bounds access occurs, ASAN will generate a detailed error report showing exactly where the problem occurred.
Best Practices for Preventing Authentication Bypass in API Vulnerability
To prevent authentication bypass vulnerabilities in web applications and APIs, developers should follow these security best practices:
- Always validate user inputs, especially those used as array indices or for authentication purposes
- Implement proper bounds checking for all array accesses
- Use memory safety tools like AddressSanitizer during development and testing
- Conduct regular security audits and code reviews focused on authentication mechanisms
- Implement defense-in-depth strategies so that a single vulnerability doesn't compromise the entire system
- Follow the principle of least privilege for all authentication tokens and sessions
- Consider using established authentication libraries rather than implementing custom solutions
Automatic Detection of Authentication Bypass Vulnerabilities
For organizations developing security-critical applications, implementing automatic detection of authentication bypass vulnerabilities should be a priority. This can be achieved through:
- Integrating memory safety tools like ASAN into the CI/CD pipeline
- Implementing fuzz testing specifically targeting authentication mechanisms
- Using static analysis tools that can detect potential out-of-bounds accesses
- Conducting regular penetration testing with a focus on authentication bypasses
- Employing tools like Firmalice that are specifically designed to detect authentication bypass vulnerabilities in binary firmware
Conclusion
The FortiWeb authentication bypass vulnerability demonstrates how seemingly minor programming errors can lead to significant security breaches. By not validating an index value before using it to access an array, the application inadvertently exposed a mechanism that allowed attackers to forge authentication tokens and gain administrative access.
This case study highlights the importance of rigorous security testing, particularly for security-critical components like web application firewalls. By implementing automatic detection methods and following security best practices, developers can identify and mitigate authentication bypass vulnerabilities before they can be exploited.
For organizations using FortiWeb or similar products, staying current with security updates and implementing additional security layers is essential for protecting against authentication bypass and other API vulnerabilities.
Let's Watch!
Critical FortiWeb Authentication Bypass: How Outbound Reads Lead to Admin Access
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence