
Imagine this scenario: a new employee joins your company. Someone must now create their accounts across Gmail, Slack, HR tools, finance systems, and dozens of other applications. Managing this process manually is inefficient, error-prone, and becomes increasingly complex as your organization grows. This is precisely where the System for Cross-Domain Identity Management (SCIM) protocol comes to the rescue.
What is the SCIM Protocol?
SCIM (sometimes pronounced "skim") is a standardized protocol that automates the exchange of user identity information between systems. It defines how user data should be represented and transferred, enabling automatic provisioning, updating, and deprovisioning of user accounts across multiple applications and services.
At its core, SCIM is a specification that defines how to build a REST API for managing users and groups. When your system implements the SCIM protocol, identity providers like Okta or Azure Active Directory can automatically create, update, or delete users in your system without manual intervention.
How SCIM Works: The Identity Management Flow
In a typical SCIM implementation, the process works as follows:
- A company maintains user accounts in an Identity Provider (IdP) such as Okta, Azure Active Directory, or Google Workspace.
- When a new user is created in the IdP, or an existing user's information is updated, the IdP uses SCIM to push that information to connected applications.
- Each application that supports SCIM receives the user data through standardized REST API endpoints.
- The applications create or update user accounts based on the received information, maintaining consistency across the entire ecosystem.
For example, when a new employee named Jane Doe joins a company, her profile is created in the identity provider with details like name, email, department, and role. The identity provider then uses SCIM to automatically provision Jane's account in all connected applications. Later, if Jane changes departments, the identity provider updates her information, and SCIM ensures this change propagates to all systems automatically.
The Technical Architecture of SCIM Protocol 2.0
SCIM 2.0, the current version of the protocole SCIM, defines a standardized RESTful API with specific endpoints and operations:
- /Users - For managing user resources
- /Groups - For managing group resources
- /ServiceProviderConfig - For retrieving service provider configuration
- /ResourceTypes - For discovering available resource types
- /Schemas - For discovering resource schemas
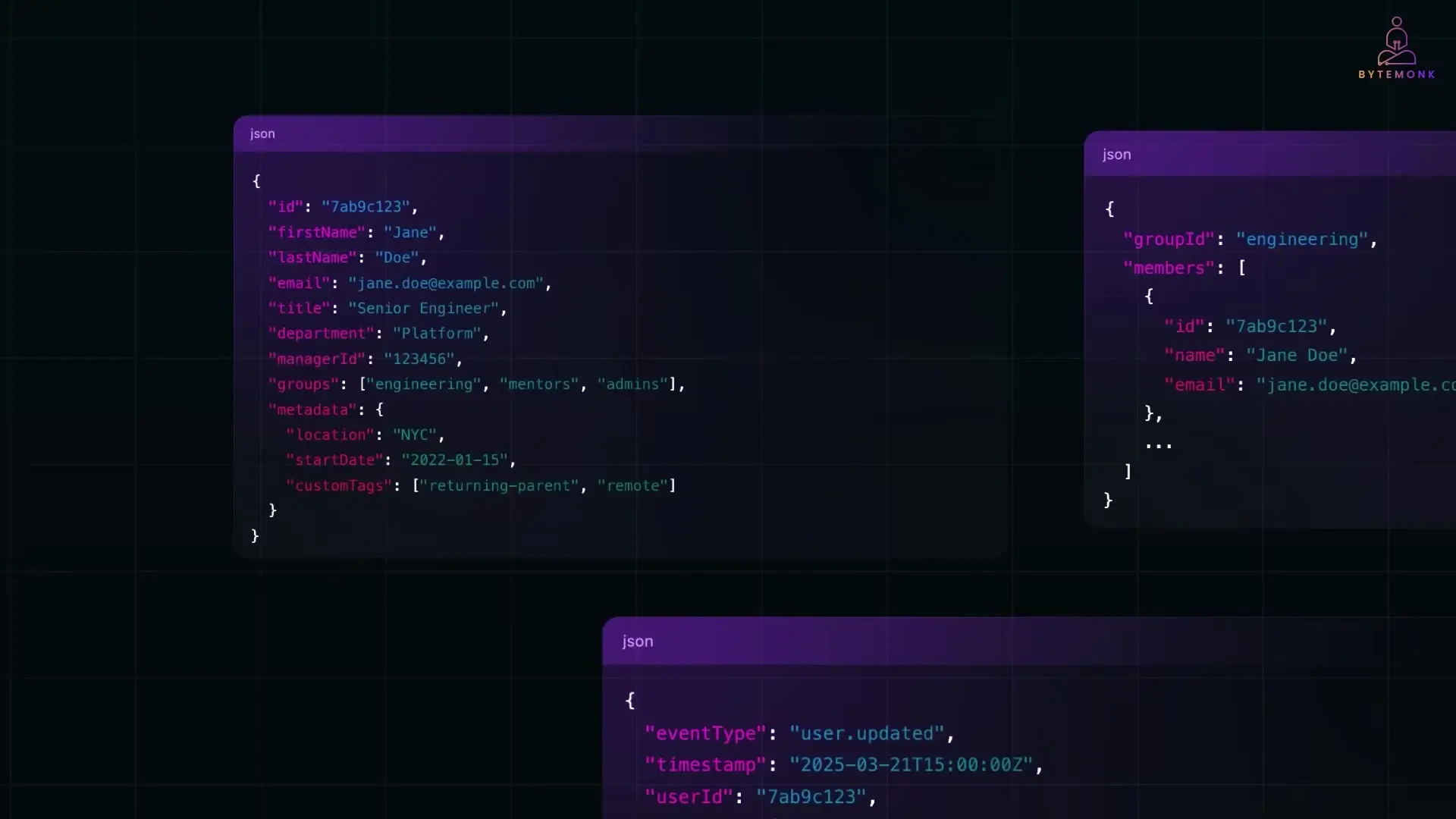
These endpoints support standard HTTP methods like GET, POST, PUT, PATCH, and DELETE to perform various operations on users and groups. The data exchange format is JSON, with a well-defined schema that includes core attributes like id, userName, name, emails, and more.
// Example SCIM 2.0 user creation request
POST /Users HTTP/1.1
Host: example.com
Content-Type: application/scim+json
{
"schemas": ["urn:ietf:params:scim:schemas:core:2.0:User"],
"userName": "jdoe",
"name": {
"familyName": "Doe",
"givenName": "Jane"
},
"emails": [
{
"type": "work",
"value": "[email protected]",
"primary": true
}
],
"active": true,
"department": "Engineering"
}Centralized Identity Sync Services: Enterprise-Scale SCIM Implementation
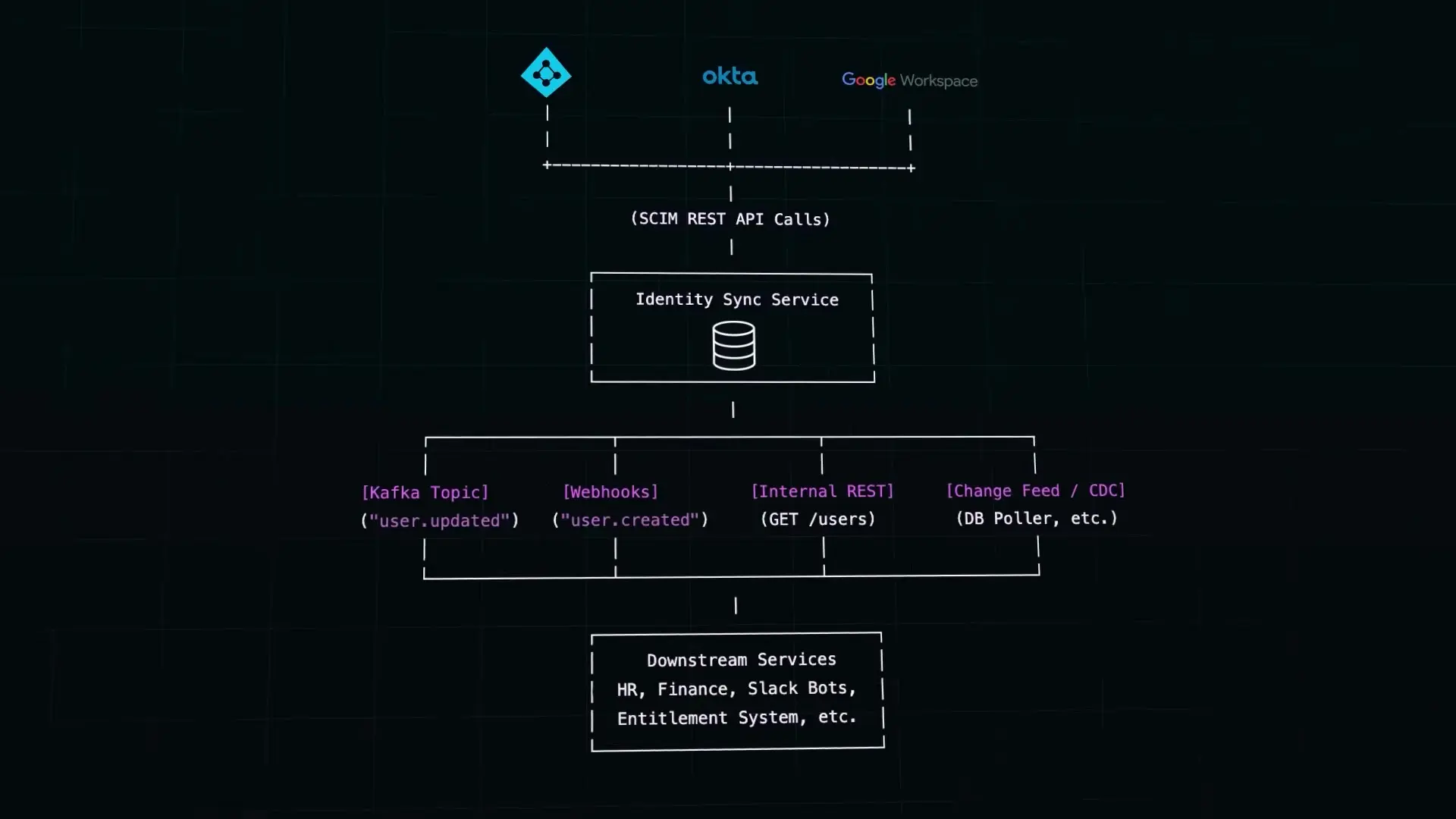
Large organizations often implement a centralized approach to SCIM. Instead of having each internal application directly implement the SCIM protocol, they build a central identity sync service that acts as an intermediary between identity providers and internal systems.
This centralized service plays two key roles:
- Passive Role: It exposes SCIM-compliant endpoints to receive updates from identity providers, storing this information in an internal database.
- Active Role: It distributes user data to internal systems through various mechanisms like message queues (Kafka, SNS), webhooks, or custom APIs.
This architecture offers several advantages:
- Centralized SCIM protocol implementation and maintenance
- Consistent handling of identity data across the organization
- Simplified debugging with centralized logging
- Ability to extend the identity data model with custom attributes
- Flexibility in how internal systems consume identity data
Companies like Netflix and Airbnb have implemented such centralized identity sync services. Netflix's "People Service" and Airbnb's identity sync service both abstract away the complexities of the SCIM protokoll while efficiently distributing user data across their internal tools and systems.
SCIM in the Real World: Enterprise Implementation Example
Let's examine a real-world scenario of SCIM implementation:
- A company manages employee identities on-premise using Active Directory
- They sync this data to Azure AD in the cloud using Azure AD Connect
- Azure AD becomes the primary identity provider (IdP)
- Azure AD uses the SCIM protocol to automatically provision users in cloud applications like Zoom, Slack, and Salesforce
- For authentication, Azure AD implements protocols like SAML or OIDC to enable single sign-on
- Employees can access all their applications with one set of credentials
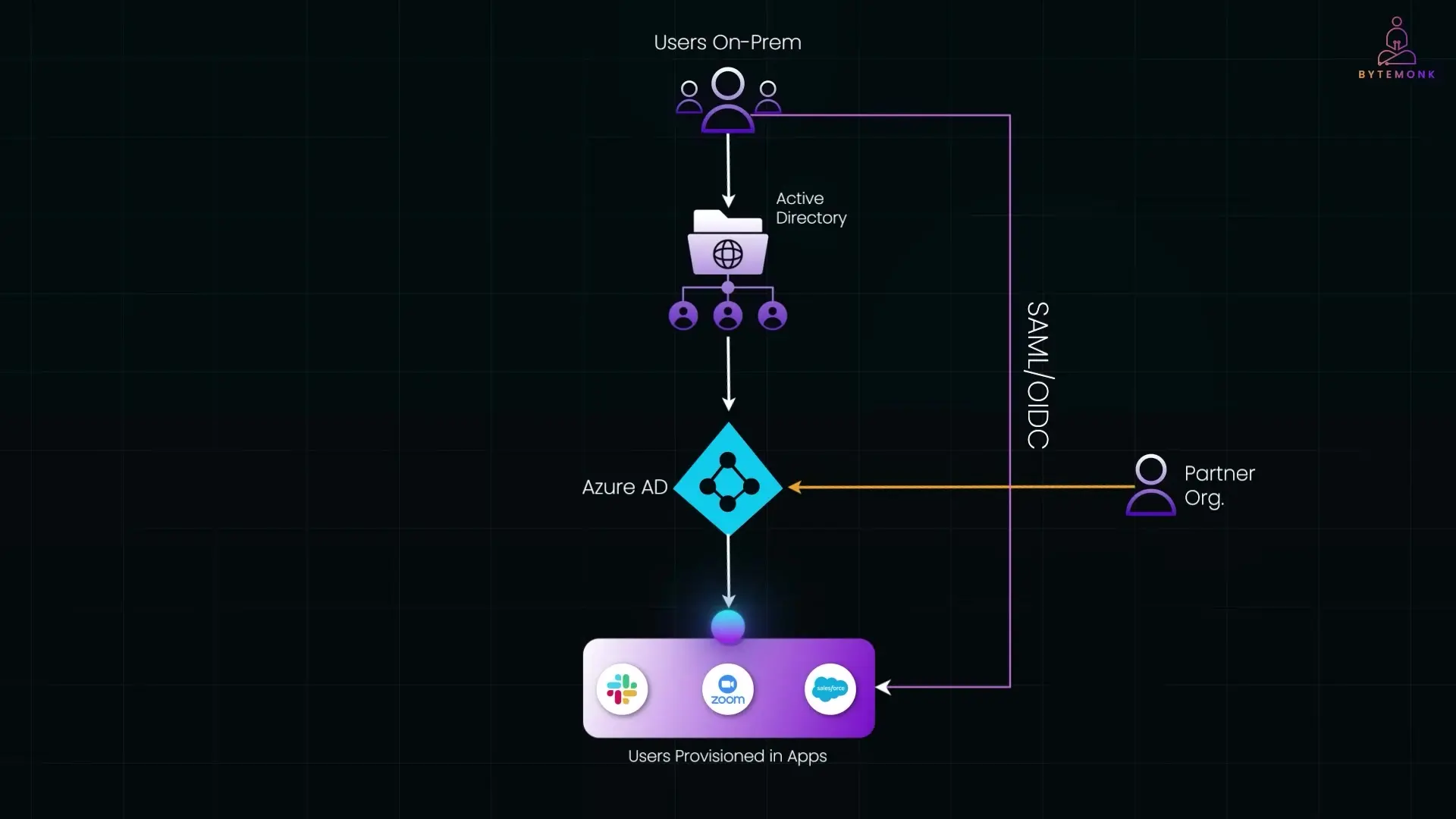
This implementation can be extended further with identity federation, allowing external users from partner organizations to securely access internal systems without needing separate accounts—all while maintaining proper security boundaries.
Benefits of Implementing the SCIM Protocol
The System for Cross-Domain Identity Management (SCIM) protocol offers numerous advantages for organizations of all sizes:
- Automated User Provisioning: Eliminates manual account creation across multiple systems
- Reduced Administrative Overhead: IT teams spend less time on account management
- Improved Security: Ensures prompt deprovisioning when employees leave
- Consistent User Data: Maintains synchronized identity information across all systems
- Scalability: Easily accommodates organizational growth and new applications
- Standardization: Uses a widely-adopted protocol supported by major identity providers and SaaS applications
- Better User Experience: Employees gain immediate access to required tools without delays
Implementing SCIM in Your Organization
If you're considering implementing the SCIM protocol in your organization, here are some key steps to follow:
- Assess your current identity management infrastructure and identify gaps
- Select an appropriate identity provider (IdP) that supports SCIM
- Inventory your applications and determine which ones support SCIM natively
- For applications without native SCIM support, consider building a centralized identity sync service
- Implement proper security measures, including authentication and authorization for SCIM endpoints
- Test thoroughly before full deployment
- Monitor and maintain your SCIM implementation to ensure continued functionality
For applications you develop in-house, implementing SCIM support can make them more attractive to enterprise customers who expect seamless integration with their identity management systems.
Conclusion: The Invisible Protocol Powering Modern Identity Management
The System for Cross-Domain Identity Management (SCIM) protocol works silently behind the scenes in many organizations, efficiently synchronizing user identities across countless applications. While end users rarely notice it, IT administrators and developers appreciate the automation and consistency it brings to identity management.
As organizations continue to adopt more cloud services and SaaS applications, the importance of standardized identity management protocols like SCIM will only grow. By understanding and implementing SCIM, organizations can create a more seamless, secure, and efficient digital workplace where identity data flows automatically to where it's needed—without manual intervention or support tickets.
Let's Watch!
SCIM Protocol: The Identity Management System Powering Enterprise User Synchronization
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence