Spring Security is a powerful framework that integrates seamlessly with Spring Boot applications to provide comprehensive security features. Whether you're building a simple web application or a complex microservices architecture, understanding how Spring Security works is essential for protecting your applications from various security threats.
What is Spring Security?
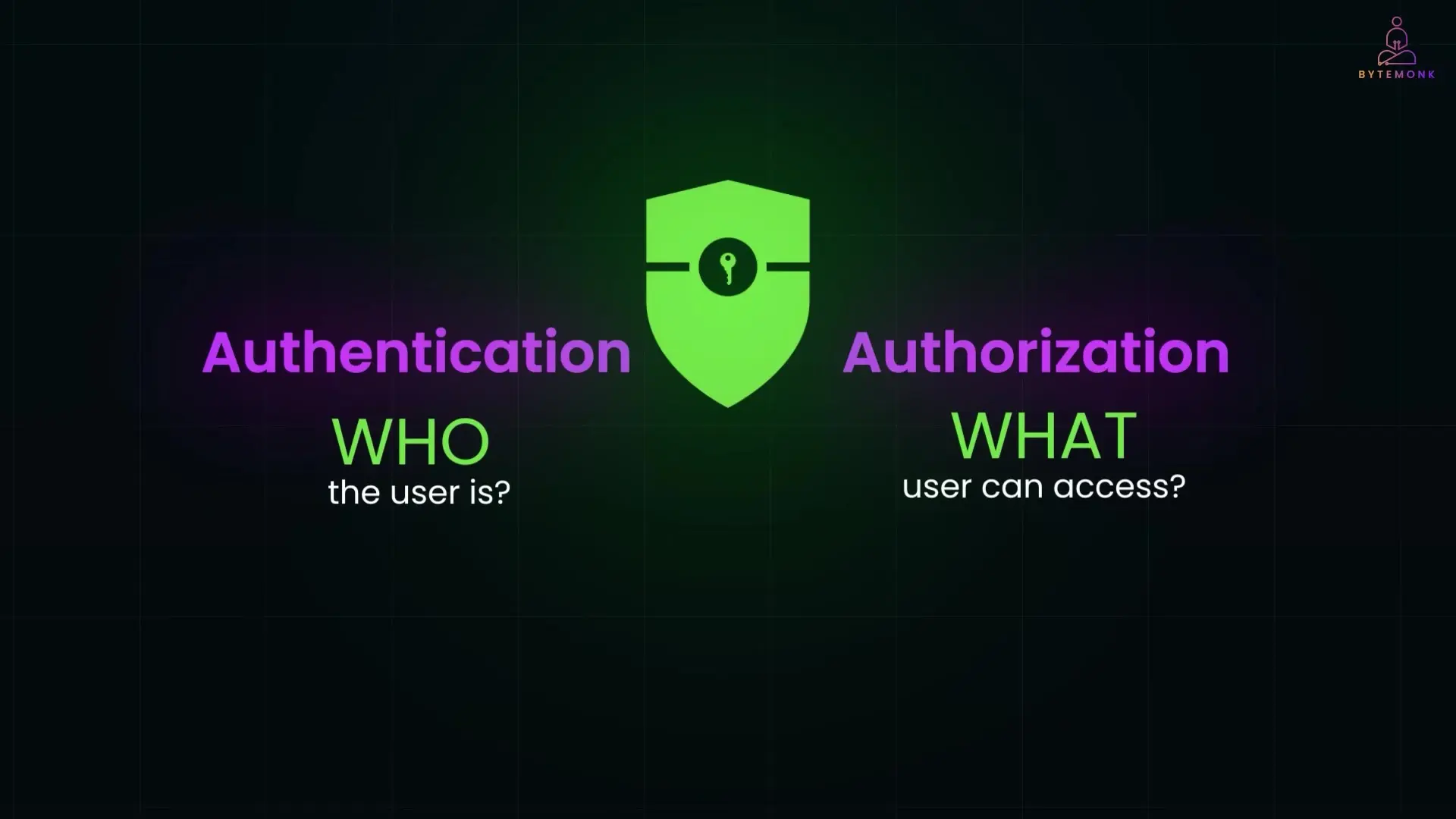
Spring Security is a module that works naturally with Spring Boot and Spring MVC applications. It addresses two primary security concerns: authentication (verifying who the user is) and authorization (determining what the user can access).
Beyond basic login functionality, Spring Security provides robust features including password encoding, role-based access control (RBAC), session management, OAuth2 integration, and JWT support. It operates with sensible defaults while offering full customization capabilities when needed.
Understanding Spring Security Filters
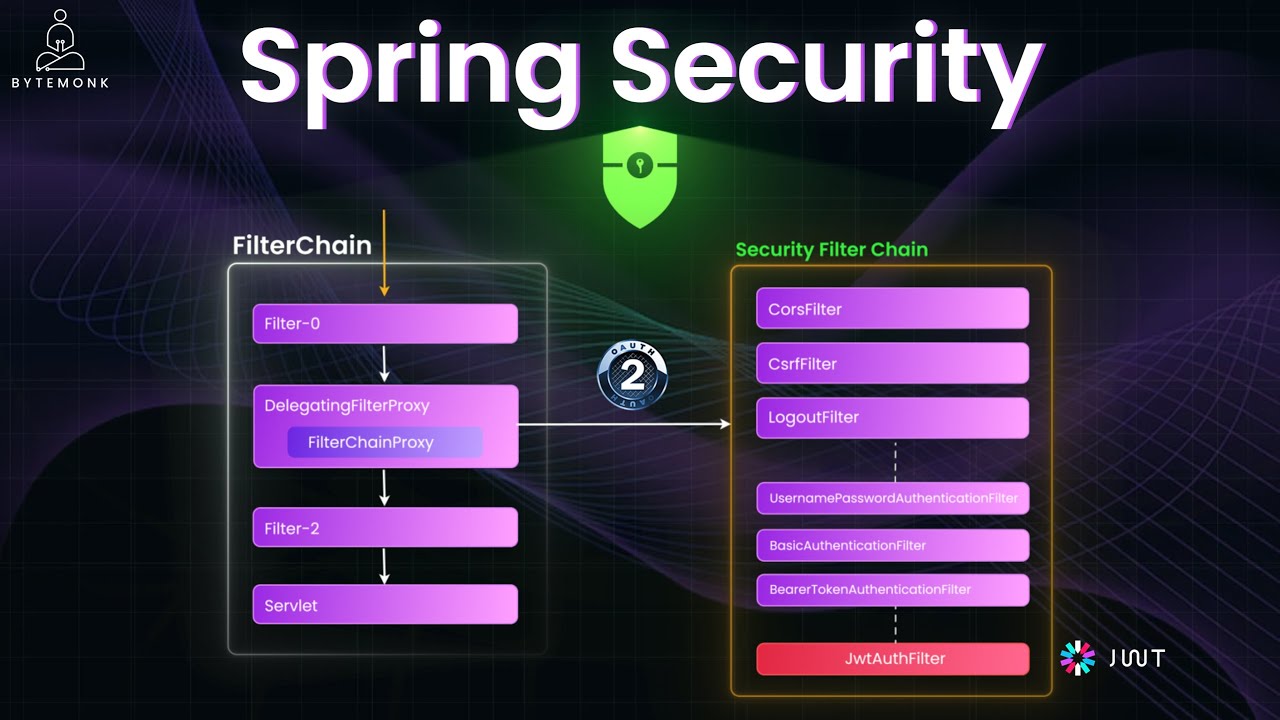
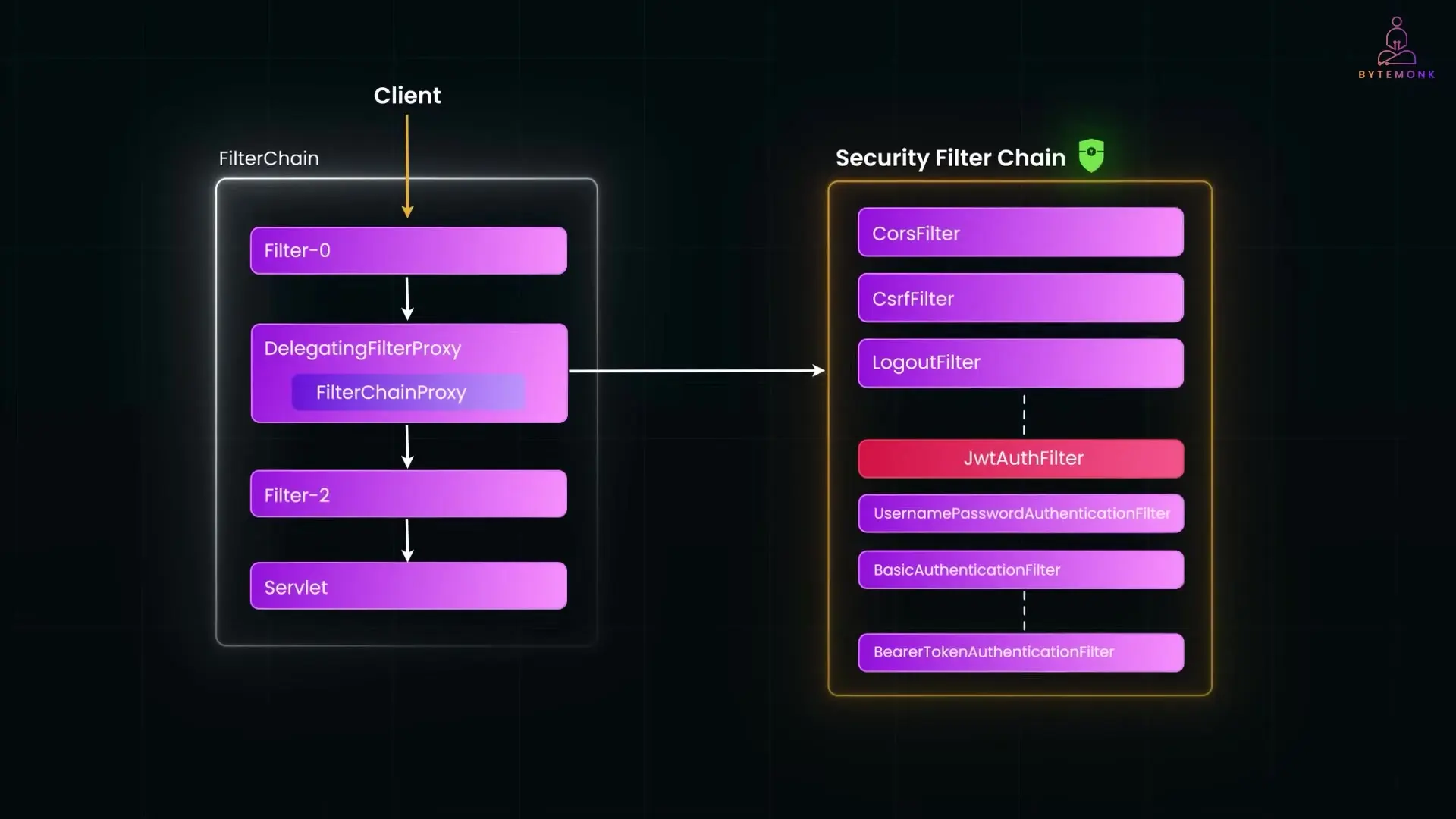
Filters are the foundation of Spring Security's architecture. They act as gatekeepers, inspecting every request before it reaches your controllers. Spring Security provides a comprehensive filter chain with built-in components for various authentication mechanisms.
- UsernamePasswordAuthenticationFilter: Processes login forms, capturing username/password credentials and triggering authentication
- BasicAuthenticationFilter: Handles HTTP Basic Auth by reading and validating Authorization headers
- BearerTokenAuthenticationFilter: Used for OAuth2 resource servers or JWT bearer tokens, validating the Authorization bearer token header
For custom authentication requirements, you can implement your own filters. For example, if you're creating a custom JWT authentication system, you might implement a JwtAuthFilter and insert it into the security filter chain.
http.addFilterBefore(jwtAuthFilter, UsernamePasswordAuthenticationFilter.class);This configuration tells Spring Security to check your custom token filter before attempting standard username/password authentication. Custom filters can be positioned anywhere in the chain to suit your application's security requirements.
Authentication Flow in Spring Security
When a request reaches your application, Spring Security's filter chain intercepts it to determine if the user is authenticated and authorized to access the requested resource. Here's the high-level authentication flow:
- User sends login credentials
- Spring Security filter captures the request
- UserDetailsService loads user information (username, password, roles)
- Password encoder validates credentials
- If authentication succeeds, a security context is created and stored
- Future requests use this context to verify access permissions
UserDetailsService
The UserDetailsService interface is central to Spring Security's authentication process. It answers the question "Who is the user?" by implementing a single method that tells Spring how to find users from your data source.
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
User user = userRepository.findByUsername(username)
.orElseThrow(() -> new UsernameNotFoundException("User not found"));
return new org.springframework.security.core.userdetails.User(
user.getUsername(),
user.getPassword(),
user.getAuthorities()
);
}Password Encoding
Spring Security never stores passwords in plain text. Instead, it uses password encoders to securely hash passwords. The BCrypt encoder is commonly used for this purpose.
@Bean
public PasswordEncoder passwordEncoder() {
return new BCryptPasswordEncoder();
}When a user logs in, Spring takes the raw password from the login form, hashes it using the configured encoder, and compares it to the stored hash value. If they match, authentication succeeds.
Getting Started with Spring Security
Adding Spring Security to your application is straightforward. Simply include the dependency in your Spring Boot project:
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>With this single addition, your application is immediately secured. By default, every endpoint requires authentication, and Spring Security auto-generates a login form with a default user and random password (printed in the console logs).
Configuring Custom Users
To define your own users instead of using the default one, you can configure an in-memory user store:
@Bean
public UserDetailsService userDetailsService() {
UserDetails admin = User.builder()
.username("admin")
.password(passwordEncoder().encode("password123"))
.roles("ADMIN")
.build();
return new InMemoryUserDetailsManager(admin);
}URL-Based Security Configuration
You can configure fine-grained access control based on URL patterns:
@Bean
public SecurityFilterChain filterChain(HttpSecurity http) throws Exception {
http
.authorizeHttpRequests(authorize -> authorize
.requestMatchers("/public/**").permitAll()
.requestMatchers("/admin/**").hasRole("ADMIN")
.anyRequest().authenticated()
)
.formLogin();
return http.build();
}OAuth2 Integration
Spring Security makes it easy to implement social login with providers like Google, GitHub, or Facebook. Simply add the appropriate configuration to your application.yml file:
spring:
security:
oauth2:
client:
registration:
google:
client-id: ${GOOGLE_CLIENT_ID}
client-secret: ${GOOGLE_CLIENT_SECRET}This configuration automatically generates an OAuth2 login page that redirects to Google and handles the callback. For security best practices, always use environment variables or external configuration files for sensitive information like client secrets.

CSRF and CORS Protection
CSRF Protection
Cross-Site Request Forgery (CSRF) protection is enabled by default in Spring Security for non-GET requests (POST, PUT, DELETE). This prevents unauthorized commands from being sent from an authenticated user's browser.
For stateless REST APIs, it's common to disable CSRF protection since these applications typically don't use sessions or cookies, making CSRF attacks less effective:
http.csrf().disable();CORS Configuration
Cross-Origin Resource Sharing (CORS) is a browser security feature that blocks requests from one domain to another unless explicitly allowed by the server. Spring Security blocks CORS by default, but you can configure it to allow specific origins.
@Bean
public CorsConfigurationSource corsConfigurationSource() {
CorsConfiguration configuration = new CorsConfiguration();
configuration.setAllowedOrigins(Arrays.asList("http://localhost:3000"));
configuration.setAllowedMethods(Arrays.asList("GET", "POST", "PUT", "DELETE"));
configuration.setAllowedHeaders(Arrays.asList("Authorization", "Content-Type"));
UrlBasedCorsConfigurationSource source = new UrlBasedCorsConfigurationSource();
source.registerCorsConfiguration("/**", configuration);
return source;
}Then enable it in your security configuration:
http.cors();Method-Level Security
Spring Security provides powerful annotations for controlling access at the class and method levels. To enable method-level security, add the @EnableMethodSecurity annotation to your configuration class:
@Configuration
@EnableMethodSecurity
public class SecurityConfig {
// configuration code
}Once enabled, you can use annotations like @PreAuthorize to control access to specific methods:
@PreAuthorize("hasRole('ADMIN')")
public List<User> getAllUsers() {
return userRepository.findAll();
}
@PreAuthorize("#userId == authentication.principal.id")
public User getUserDetails(@PathVariable Long userId) {
return userRepository.findById(userId).orElseThrow();
}The second example demonstrates Spring Expression Language (SpEL) capabilities, allowing only users to access their own data by comparing the requested user ID with the authenticated user's ID.
Conclusion
Spring Security provides a comprehensive security framework that integrates seamlessly with Spring Boot applications. From authentication and authorization to password encoding, role-based access control, and integration with OAuth2 providers, it offers powerful tools to secure your applications with minimal configuration.
By understanding the core concepts of filters, UserDetailsService, password encoding, and security contexts, you can implement robust security measures tailored to your application's specific requirements. Whether you're building a simple web application or a complex microservices architecture, Spring Security gives you the flexibility to implement the right security controls for your needs.
Let's Watch!
Spring Security Mastery: Authentication and Authorization in 10 Minutes
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence