
At first glance, a simple string comparison like checking if an API key matches seems completely secure. After all, it's just verifying whether two strings are identical. But what if I told you that this basic operation could potentially expose your system to sophisticated attacks? In this article, we'll explore timing attacks - a subtle but powerful technique that exploits the time it takes for operations to complete in order to extract sensitive information.
What is a Timing Attack?
A timing attack is a form of side-channel attack in information security where the attacker analyzes the time taken to execute cryptographic algorithms or other security-critical operations. Instead of directly attacking the cryptographic implementation, the attacker exploits variations in how long different operations take to complete.
In the context of web security, timing attacks can be used to extract sensitive information such as passwords, API keys, or private keys by measuring and analyzing the response times of a system under different inputs.
How String Comparisons Create Vulnerability
To understand timing attacks, we need to examine how string comparisons typically work in programming languages. When comparing two strings, most implementations follow this process:
- First, compare the lengths of both strings. If they don't match, return false immediately.
- If lengths match, compare the strings character by character.
- As soon as a character mismatch is found, return false without checking the rest of the string.
- If all characters match, return true.
This early-exit behavior creates a timing vulnerability. If an attacker can measure how long the comparison takes, they can infer information about the secret string. For example, if comparing the first character takes longer than comparing an incorrect length, the attacker can deduce that the first character was correct.
Demonstrating a Timing Attack
Let's walk through a practical example of how a timing attack might work against an API protected by an API key. For demonstration purposes, we'll use an exaggerated version where we've added artificial delays to make the timing differences more pronounced.
Step 1: Finding the API Key Length
The first step in our attack is to determine the length of the API key. We'll do this by sending requests with API keys of different lengths and measuring the response times.
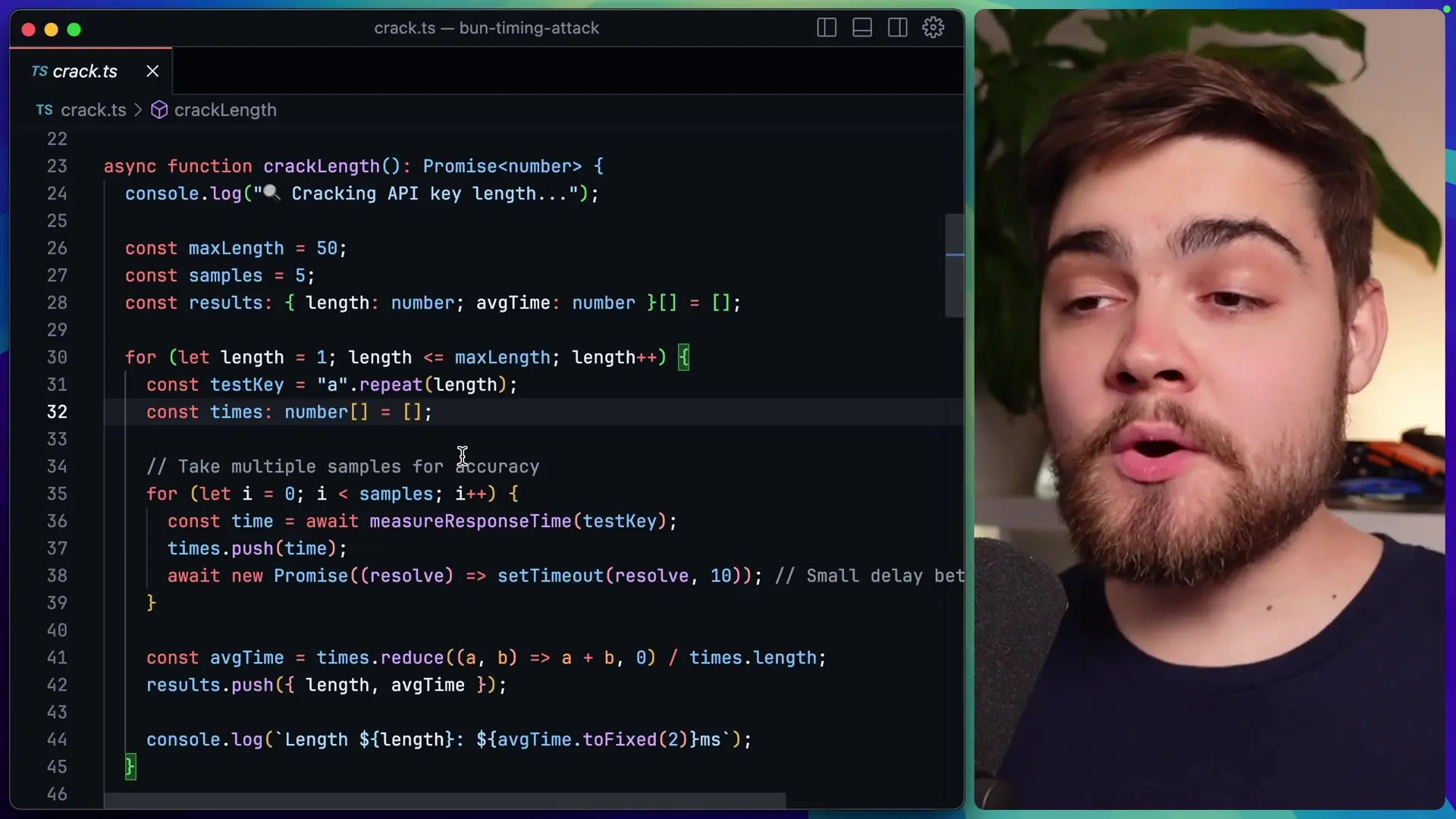
The function tries API keys of various lengths (up to 50 characters) against our endpoint. It records the average response time for each length after multiple samples. The key length that produces the longest average response time is likely the correct one, as it would have proceeded to character comparison rather than failing early at the length check.
Step 2: Cracking the Individual Characters
Once we know the API key length, we can crack each character position one by one. For each position, we try every possible character and measure the response time. The character that takes the longest to process is likely the correct one for that position.

For example, if we're testing the first character position, we'd send requests with API keys starting with 'a', 'b', 'c', etc. If the actual first character is 'b', then the request with 'b' would take slightly longer because the comparison would proceed to check the second character before failing.
By repeating this process for each position, we can eventually reconstruct the entire API key without ever seeing it directly.
Real-World Practicality and Limitations
While our demonstration used exaggerated timing differences, real-world timing attacks face several challenges:
- Network jitter and latency can introduce significant noise that masks the tiny timing differences.
- Modern string comparison operations are extremely fast, making differences hard to detect.
- Other server operations and load can further obscure timing patterns.
- Rate limiting and other security measures can prevent the large number of requests needed.
However, research has shown that timing differences as small as 30 microseconds can be sufficient for successful attacks under the right conditions. This is particularly true for operations that are more complex than simple string comparisons.
Real-World Examples of Timing Attacks
Timing attacks aren't just theoretical concerns. They've been successfully used in various contexts:
- Username enumeration: When a login system checks if a username exists before checking the password, it typically takes longer for valid usernames than invalid ones.
- Cryptocurrency private key extraction: The Minerva attack (CVEs up to 2024) can recover ECDSA private keys by measuring signature generation times.

Other operations found vulnerable to timing attacks include MD5 hashing of strings, complex JSON parsing, SQLite memory selects, and various cryptographic operations.
Protecting Against Timing Attacks
Given the potential risks, how can developers protect their applications against timing attacks? Here are some effective strategies:
1. Use Constant-Time Comparison Functions
Most modern programming languages and frameworks provide constant-time comparison functions specifically designed to prevent timing attacks. These functions take the same amount of time regardless of how many characters match before a difference is found.
// In Node.js, use the crypto module's timingSafeEqual function
const crypto = require('crypto');
function safeCompare(a, b) {
// Convert strings to buffers if they aren't already
const bufA = Buffer.isBuffer(a) ? a : Buffer.from(a);
const bufB = Buffer.isBuffer(b) ? b : Buffer.from(b);
// Return false early if lengths don't match (without leaking timing info)
if (bufA.length !== bufB.length) {
// Create dummy buffers of equal length to prevent timing analysis
const dummyA = Buffer.alloc(bufA.length);
const dummyB = Buffer.alloc(bufA.length);
crypto.timingSafeEqual(dummyA, dummyB);
return false;
}
// Perform constant-time comparison
return crypto.timingSafeEqual(bufA, bufB);
}2. Implement Rate Limiting
Rate limiting restricts the number of requests a client can make within a specific time period. This makes timing attacks impractical as they typically require a large number of requests to gather statistically significant timing data.
// Example using Express and express-rate-limit
const rateLimit = require('express-rate-limit');
const apiLimiter = rateLimit({
windowMs: 15 * 60 * 1000, // 15 minutes
max: 100, // limit each IP to 100 requests per windowMs
message: 'Too many requests, please try again later'
});
// Apply to all API endpoints
app.use('/api/', apiLimiter);3. Add Random Delays
While not as robust as constant-time functions, adding small random delays to responses can help obscure timing patterns. This approach should be combined with other protection methods.
4. Use HMAC for Comparisons
When comparing sensitive values like API keys or password hashes, consider using HMAC (Hash-based Message Authentication Code) in a constant-time implementation to prevent timing attacks.
Secure Authentication Flow
For login systems, ensure that username validation and password validation take the same amount of time regardless of whether the username exists or not. A secure approach might look like this:
async function login(username, password) {
// Retrieve user or a dummy user if not found
const user = await getUserByUsername(username) || getDummyUser();
// Even if user doesn't exist, we still do password verification
// against a dummy hash to ensure consistent timing
const isPasswordValid = await verifyPassword(password, user.passwordHash);
// Only proceed if user exists AND password is valid
if (user.id && isPasswordValid) {
return generateAuthToken(user);
} else {
throw new Error('Invalid username or password');
}
}Conclusion
Timing attacks represent a subtle but real security threat that can compromise sensitive information in web applications. While simple string comparison vulnerabilities may be difficult to exploit in practice due to network noise and other factors, more complex operations remain at risk.
By understanding how timing attacks work and implementing appropriate countermeasures like constant-time comparison functions, rate limiting, and secure authentication flows, developers can significantly reduce the risk of these sophisticated attacks.
Remember that security is about defense in depth - no single measure provides complete protection. Always consider timing attacks as part of your overall security strategy, especially when handling sensitive authentication, cryptographic operations, or API key validations.
Let's Watch!
Timing Attacks Exposed: How Hackers Crack Passwords Using Response Times
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence