
Environment variables are essential for managing sensitive information in your applications, but mishandling them can lead to serious security breaches and potentially cost you thousands of dollars. In this article, we'll explore five critical .env file mistakes that developers commonly make and provide practical solutions to avoid them.
Mistake #1: Pushing .env Files to Your Repository
One of the most dangerous mistakes developers make is pushing their .env files to public repositories. This exposes sensitive information like API keys, database credentials, and other secrets to anyone who can access your code. Surprisingly, this happens more often than you might think—a simple GitHub search for 'env' or 'API keys' reveals thousands of exposed credentials.
The proper approach is to create an env.example file that contains only the variable names without actual values. This file can safely be committed to your repository as a template for other developers.
To prevent accidentally pushing your actual .env file, make sure to add it to your .gitignore file. This is a crucial step that many developers overlook.
# .gitignore file example
.env
.env.local
.env.development
.env.production
.env.stagingMistake #2: Neglecting Documentation and Example Files
Another common mistake is failing to document your project's environment requirements properly. Without clear documentation or example files, both you and other developers will struggle to set up the project correctly, especially after some time has passed.
To address this, create comprehensive documentation in your README.md file that explains all required environment variables and their purposes. Additionally, provide an env.example file that serves as a template for setting up the project.
# Environment Setup
This project requires the following environment variables:
- `DATABASE_URL`: Connection string for your PostgreSQL database
- `API_KEY`: Your API key for the external service
- `SECRET_KEY`: A secret key for JWT token generation
- `PORT`: The port on which the server will run (default: 3000)
Copy the `.env.example` file to `.env` and fill in your values.Mistake #3: Thinking Git rm Will Save You After Exposing Secrets
If you've accidentally pushed your .env file to a repository, you might think that removing it with git rm will solve the problem. Unfortunately, this is a dangerous misconception.

When you push a file to a Git repository, it becomes part of the commit history. Even if you delete the file in a subsequent commit, anyone with access to the repository can still view the file in the commit history. This means your secrets remain exposed.
If you accidentally expose sensitive information, the only proper solution is to immediately revoke and regenerate all exposed credentials. This includes API keys, passwords, and any other secrets. Consider them compromised and act accordingly.
Mistake #4: Using One .env File for All Environments
Using a single .env file for local development, staging, and production environments is a recipe for disaster. Many developers try to manage this by commenting and uncommenting different sets of variables depending on the environment they're working in.
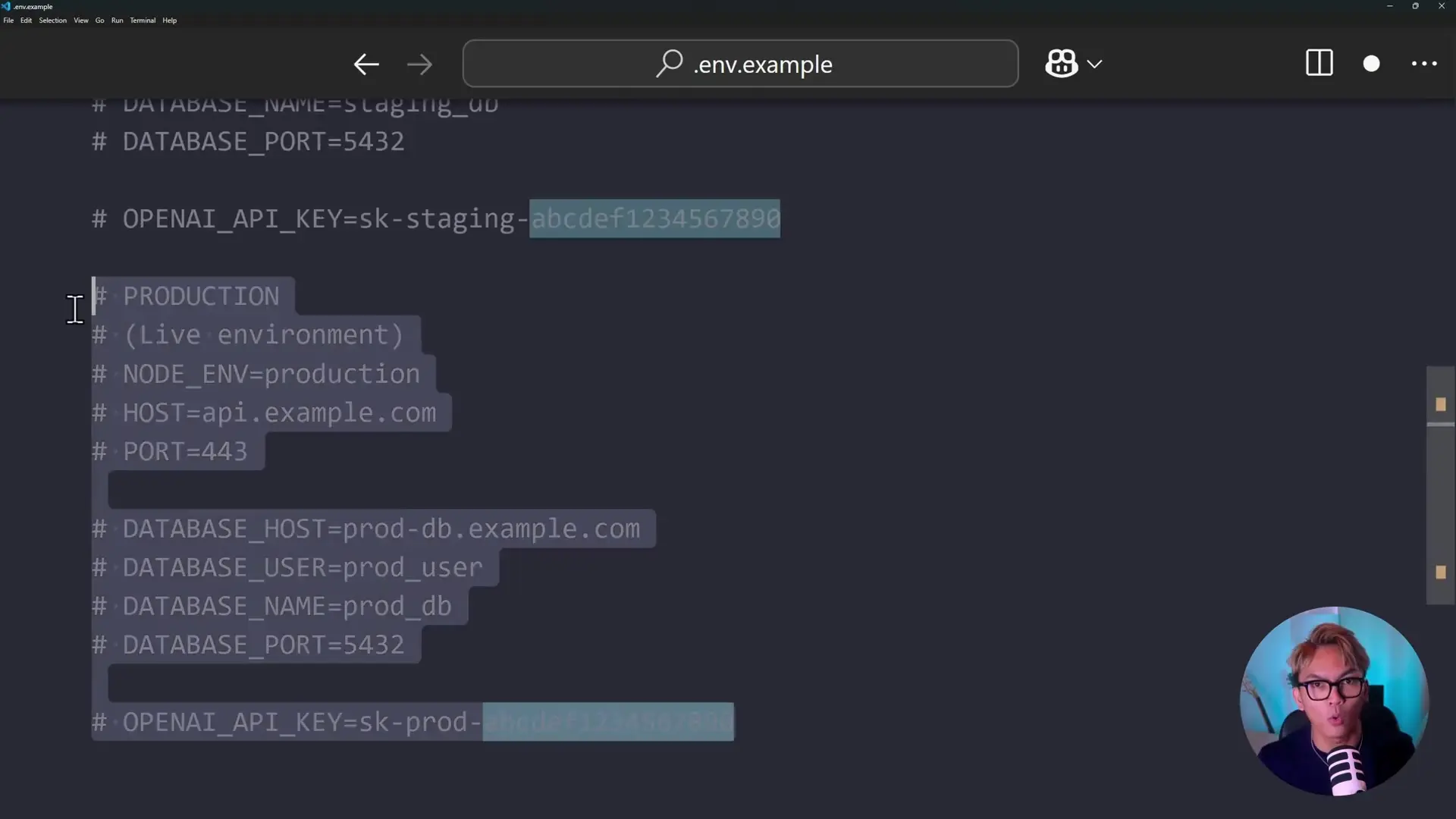
This approach is error-prone and can lead to serious mistakes, such as accidentally running tests against production databases or deleting production data when you thought you were in a development environment.
The solution is to maintain separate environment files for each context:
- .env.development or .env.local for local development
- .env.staging for the staging environment
- .env.production for the production environment
Then, use environment-specific configuration in your application to load the correct file based on the current environment (e.g., using NODE_ENV).
// Load environment variables based on NODE_ENV
require('dotenv').config({
path: `.env.${process.env.NODE_ENV || 'development'}`
});Mistake #5: Exposing Secrets in Frontend Applications
A particularly dangerous mistake occurs when developers inadvertently expose secrets in frontend applications. When working with frameworks like React, Next.js, or Vite, environment variables can be bundled into client-side code, making them visible to anyone who inspects your application in the browser's developer tools.
Frontend frameworks typically have special prefixes to explicitly mark variables that should be exposed to the client:
- Next.js: NEXT_PUBLIC_*
- Create React App: REACT_APP_*
- Vite: VITE_*
Never prefix sensitive information like API keys, passwords, or secrets with these prefixes. The golden rule is to ask yourself: "Would I lose my job if this information became public? Would it cost me or my company thousands of dollars?" If the answer is yes, keep it server-side only.
For situations where you need to use API keys in frontend code, consider using read-only API keys (like Supabase's publishable key) or, better yet, create a server-side API that proxies requests to third-party services without exposing your credentials.
Best Practices for Managing Environment Variables
- Always add .env files to your .gitignore file extension list
- Provide an env.example file with variable names but no values
- Document all required environment variables in your README.md
- Use separate .env files for different environments
- Never prefix sensitive variables with client-side prefixes in frontend applications
- Consider using environment variable validation libraries to ensure all required variables are present
- For large projects or teams, consider using a secrets management service
- Regularly rotate sensitive credentials, especially API keys
When dealing with larger files or binary data, remember that .gitignore file size limitations may come into play. While .gitignore itself handles patterns rather than storing the actual files, you should be mindful of adding patterns for large files or zip files that shouldn't be tracked.
# Ignore large files and archives
*.zip
*.rar
*.7z
*.tar.gz
*.mp4
*.mov
# Ignore large data directories
data/
uploads/
node_modules/Conclusion
Properly managing environment variables is crucial for maintaining the security of your applications. By avoiding these five common mistakes, you can protect sensitive information and prevent potentially costly security breaches. Remember that once secrets are exposed, they should be considered compromised and must be regenerated immediately.
When in doubt about security practices, don't hesitate to consult with more experienced developers or security professionals. A little caution today can save you from significant problems tomorrow.
Let's Watch!
5 Critical .env File Mistakes Costing Developers Thousands
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence