
In a surprising move to support the modding community, EA recently released the source code for Command and Conquer Generals: Zero Hour. This beloved strategy game from 2003 now offers unprecedented access for developers and security enthusiasts to examine how games were built in an era before cybersecurity was a primary concern.
While the source code is now publicly available (released on February 7th), it's important to note that the game assets remain EA's proprietary property. This means you can study the code but cannot compile a complete working game from scratch without the original assets.
Network Protocol Analysis: A Security Perspective
From a security researcher's perspective, the network code is particularly fascinating. Command and Conquer Generals: Zero Hour uses port 8086 for multiplayer communication – a subtle nod to the Intel 8086 processor from computing history. This port handles all the game's LAN multiplayer traffic.
What makes this codebase particularly interesting is how it reflects software development practices from an era before cybersecurity became a mainstream concern. The code prioritizes functionality over security, with several design choices that would be considered problematic by today's standards.
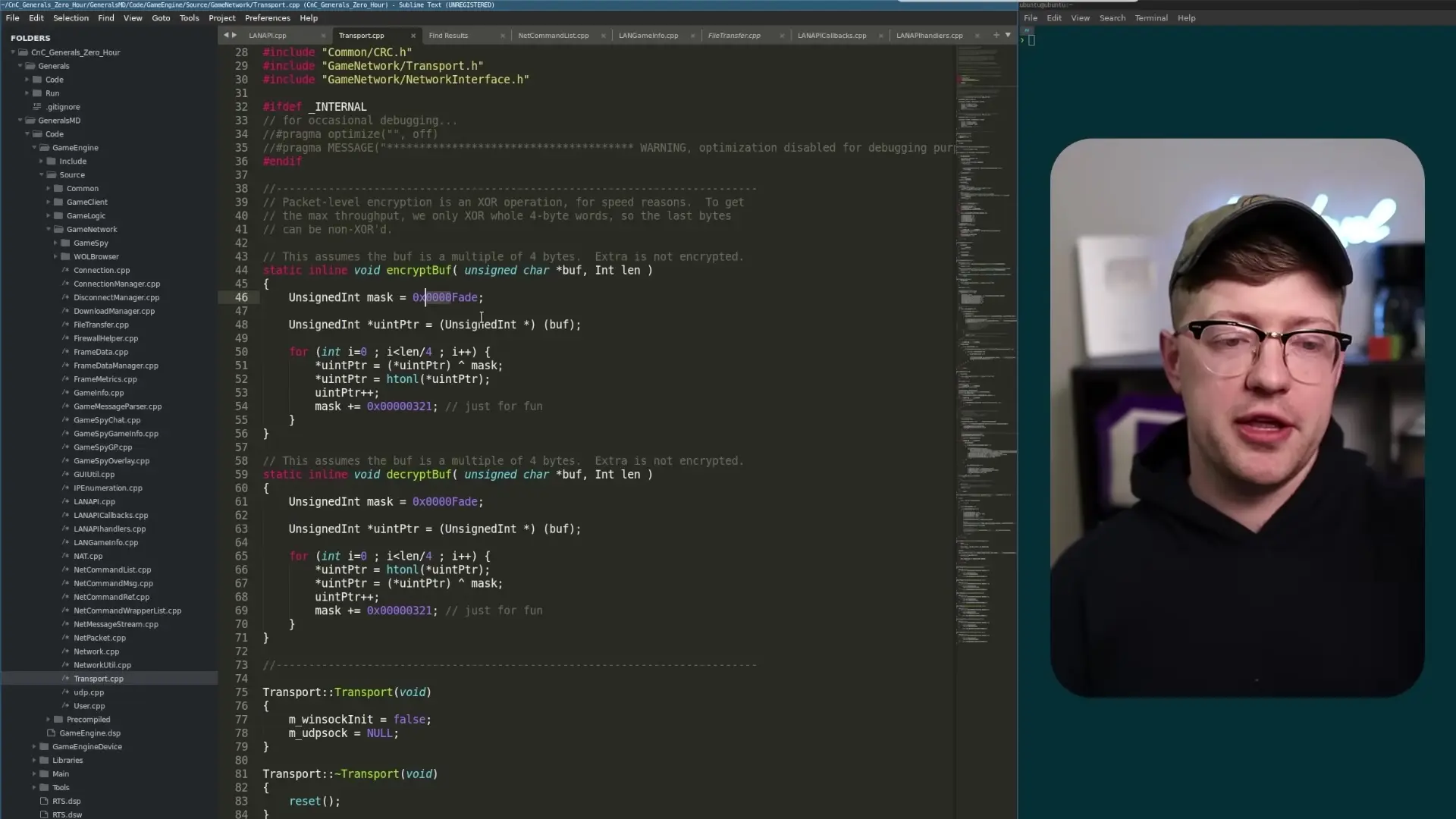
The 'Encryption' That Isn't Really Encryption
One of the most interesting discoveries in the source code is the implementation of functions called 'encrypt_buff' and 'decrypt_buff'. Despite their names, these functions don't provide actual encryption by modern standards - they implement a simple XOR operation.
Modern encryption typically involves complex mathematical operations, substitutions, and multiple rounds of transformations. In contrast, Command and Conquer's implementation has several notable security weaknesses:
- It uses a 4-byte mask where the first two bytes are zeros - meaning half of each data chunk isn't even modified
- The mask is incremented by a small value with each iteration, but remains predictable
- The implementation only processes data in 4-byte chunks, leaving any remaining bytes unencrypted
- There's no key exchange mechanism or proper cryptographic protocol
This approach was common in early 2000s game development, where the focus was on creating functional network code with minimal overhead rather than securing against potential attacks. Remember, this was developed before major security events like MS08-067 and before the term "zero-day vulnerability" had entered the mainstream vocabulary.
Packet Validation and the "Magic Number"
Another interesting aspect of the network code is how it validates incoming packets. The game implements a cyclical redundancy check (CRC) to verify that packets haven't been corrupted during transmission - a standard practice even today.
However, what's particularly amusing is the "magic number" used to identify valid game packets. After verifying the CRC, the code checks if the packet header contains a specific value called "generals_magic_number" - which is simply defined as "food". This unexpected value serves as a signature to identify legitimate game traffic.
Understanding the Historical Context
It's important to view these findings within their historical context. Command and Conquer Generals: Zero Hour was developed in 2003, when:
- Games were primarily focused on functionality rather than security
- Cybersecurity wasn't the priority it is today
- Network attacks against games were less common and less sophisticated
- Development teams prioritized performance on the limited hardware of the time
The simplicity of these implementations also reflects a different era of gaming - when LAN parties were common and online play was still in its relative infancy. The game was designed primarily for local network play among friends rather than the global online environment we take for granted today.
Lessons for Modern Developers
Examining this legacy code offers valuable insights for today's developers and security professionals:
- Never implement your own encryption - use established libraries and protocols
- Always validate input data thoroughly, beyond simple signature checks
- Consider potential attack vectors even in seemingly benign applications
- Document your code clearly for future maintainers (and potential security researchers)
- Remember that what seems secure today may be vulnerable tomorrow as technology evolves
The Value of Source Code Releases
EA's decision to release the Command and Conquer source code is valuable not just for the modding community but also for educational purposes. It provides a fascinating glimpse into game development practices from nearly two decades ago and allows us to see how far the industry has come in terms of security awareness.
For developers interested in game networking, security research, or simply appreciating the evolution of coding practices, the Command and Conquer Generals: Zero Hour source code offers a treasure trove of insights. While we might chuckle at some of the implementation details, they represent the standard practices of their time and the foundation upon which modern game development has been built.
This release joins other notable source code releases like Command and Conquer Red Alert, providing valuable historical documentation of game development practices and allowing the community to learn from, preserve, and potentially improve upon these classic titles.
Let's Watch!
Inside Command and Conquer's Source Code: Revealing Security Flaws from 2003
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence