
A new development trend called 'wipe coding' has taken the tech world by storm, promising to revolutionize how SaaS applications are built. But beneath this exciting innovation lies a concerning reality: applications built this way often contain critical SaaS security vulnerabilities that put both businesses and users at risk.
What Is 'Wipe Coding' and Why Is It Trending?
At its core, wipe coding represents a fundamental shift in software development. It's a methodology where developers rely heavily on AI tools like GPT-4, GitHub Copilot, Cursor, or DeepSeek to generate code based on simple English prompts. The approach prioritizes speed and experimentation over structure and maintainability.
The trend gained significant traction after several high-profile success stories of indie developers rapidly building and monetizing applications through this method. The appeal is undeniable: build MVPs in days instead of months, with minimal technical knowledge required.

The wipe coding approach embodies a new mindset where developers trust AI to handle the technical details while they focus on product vision and user experience. You simply describe what you want in plain language, and the AI tools generate the corresponding code—no setup, no boilerplate, no Stack Overflow searches required.
The Critical SaaS Vulnerabilities Created by Wipe Coding
While wipe coding enables rapid development, it introduces serious SaaS security vulnerabilities that can compromise application integrity. The fundamental problem is that English is not a programming language—it lacks the precision needed to ensure security, scalability, and maintainability.
- Lack of security context: AI models don't understand the security implications of the code they generate unless explicitly prompted
- Missing authentication safeguards: Proper token expiry, permission boundaries, and rate limiting are often overlooked
- Inadequate input validation: Leading to SQL injection and XSS vulnerabilities
- Poor error handling: Exposing sensitive system information to potential attackers
- Insecure default configurations: Creating backdoors for exploitation
The result is working code that appears functional but contains hidden SaaS exploits waiting to be discovered. These vulnerabilities create the perfect conditions for data breaches, unauthorized access, and service disruptions.
Real-World Consequences: When Wipe Coding Goes Wrong
The dangers of wipe coding aren't theoretical—they've already manifested in real-world incidents. Developers who built SaaS applications using AI tools without proper security knowledge have faced devastating consequences, including:
- Complete system compromises where hackers gained administrative access
- Customer data breaches exposing sensitive personal information
- Serverless function abuse leading to thousands in unexpected cloud costs
- Reputational damage that destroyed nascent businesses overnight
- Legal liability for regulatory non-compliance
One particularly alarming pattern involves developers proudly announcing their AI-built SaaS applications on social media, only to be targeted and hacked within days or even hours. These incidents highlight the critical need for SaaS vulnerability scanners and proper vulnerability management as a service solutions in the development process.

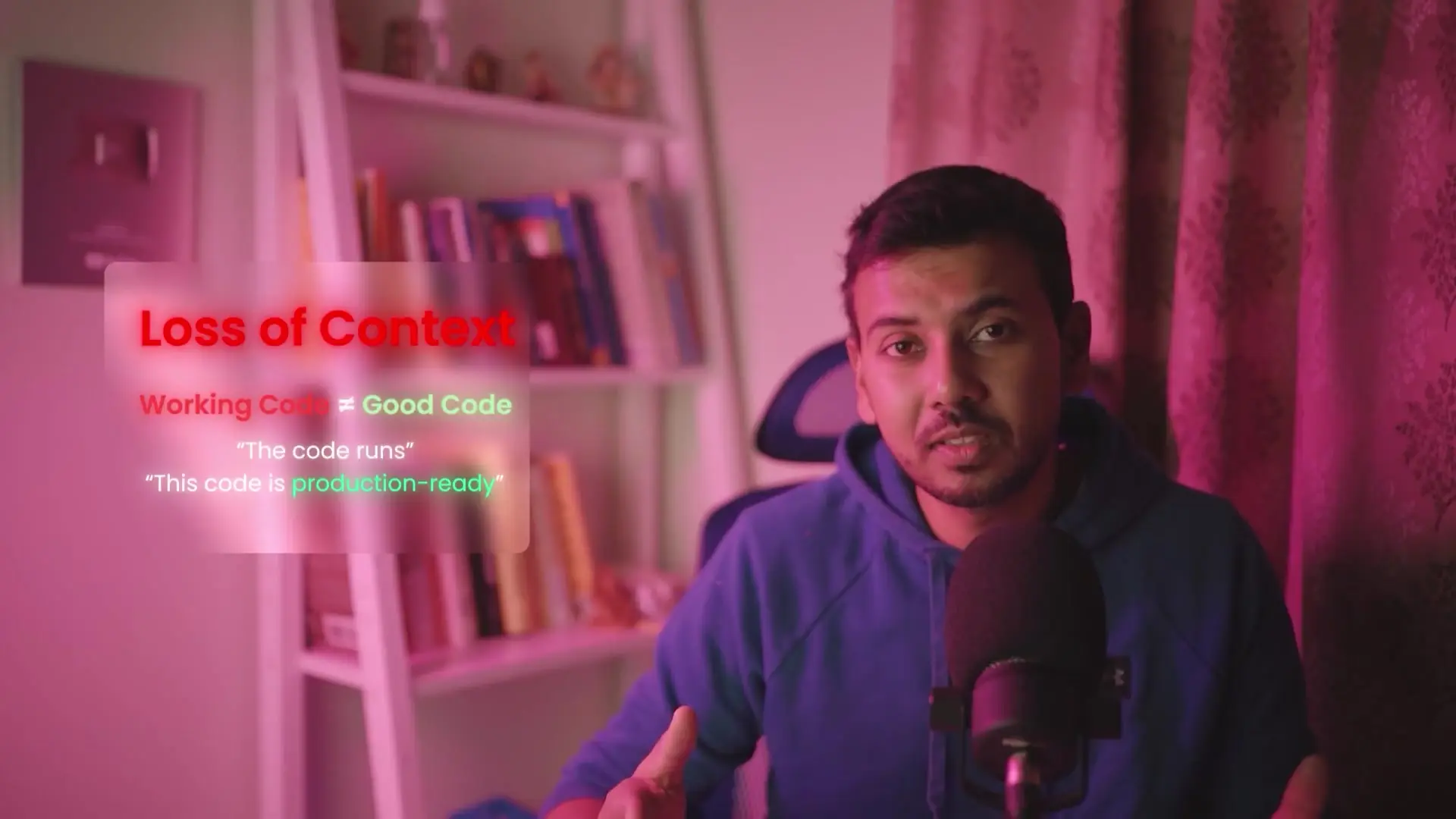
The Fundamental Disconnect: Working Code vs. Production-Ready Code
The core issue with wipe coding lies in the dangerous misconception that code that runs is equivalent to code that's production-ready. This fundamental disconnect creates a false sense of security among developers new to SaaS application development.
Production-ready code requires numerous qualities beyond basic functionality:
- Comprehensive security testing and hardening
- Performance optimization for scale
- Proper error handling and logging
- Maintainable architecture and documentation
- Compliance with relevant regulations and standards
AI-generated code rarely meets these standards without significant human oversight and expertise. Without implementing proper SaaS vulnerability management practices, developers are essentially deploying ticking time bombs to production environments.
Responsible AI-Assisted Development: Finding the Balance
Despite these risks, wipe coding isn't inherently bad—it's the uncritical deployment of AI-generated code that creates problems. When used responsibly, AI coding assistants can dramatically accelerate development while maintaining security standards.
Here's how to integrate AI tools into a secure development workflow:
- Use AI for initial code generation but review every line with security in mind
- Implement a SaaS vulnerability scanner as part of your CI/CD pipeline
- Consider vulnerability management as a service for ongoing protection
- Don't deploy code you don't understand—take time to learn what the AI has generated
- Keep experimental projects local until you've conducted proper security reviews
- Gradually build security expertise alongside your development skills
The goal should be to evolve from "AI builds it for me" to "I use AI as a tool, but I am still the engineer." This mindset shift ensures you maintain control over your application's security posture while benefiting from AI's productivity enhancements.
Best Practices for Secure SaaS Development with AI Assistance
For developers looking to leverage AI tools while avoiding SaaS security vulnerabilities, consider implementing these best practices:
- Start with security requirements: Define security parameters before generating code
- Use specialized prompts: Ask AI specifically about security implications and potential vulnerabilities
- Implement defense in depth: Add multiple layers of security controls
- Conduct regular security testing: Use both automated tools and manual review
- Maintain a security-first mindset: Consider security at every development stage
- Stay educated: Continuously learn about common SaaS exploits and prevention techniques
Additionally, consider implementing formal vulnerability management processes, including regular scanning with a SaaS vulnerability scanner and establishing proper incident response procedures.
The Future of AI-Assisted Development
Wipe coding represents both a challenge and an opportunity for the software development industry. As AI coding tools continue to evolve, they will likely incorporate more security-focused features and guardrails to prevent common vulnerabilities.
The most successful developers will be those who embrace AI assistance while maintaining security discipline. This balanced approach allows for rapid innovation without compromising on the fundamental security requirements that protect businesses and users from harm.
Conclusion: Responsible Innovation in the AI Era
The wipe coding phenomenon highlights a critical inflection point in software development. AI tools have democratized coding, allowing more people than ever to build software products. However, this accessibility comes with responsibility.
By implementing proper SaaS vulnerability management practices, using specialized vulnerability scanners, and maintaining a security-first mindset, developers can harness AI's power while avoiding its pitfalls. The future belongs not to those who simply build fastest, but to those who build both quickly and securely.
As we navigate this new era of AI-assisted development, let's ensure that innovation doesn't come at the expense of security, privacy, and trust—the foundational elements upon which sustainable software businesses are built.
Let's Watch!
The SaaS Security Crisis: Why 'Wipe Coding' With AI Is a Vulnerability Timebomb
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence