
Virtual machines are widely regarded as secure sandboxes for running untrusted code, but recent vulnerabilities discovered at the Pwn2Own hacking competition reveal that this isolation isn't always perfect. With over $1 million in prizes awarded, researchers demonstrated several critical vulnerabilities in VMware products that allow attackers to break out of virtual machine boundaries and potentially compromise host systems.
Understanding Virtual Machine Architecture
To understand how VM escape vulnerabilities work, we first need to understand what a virtual machine actually is. At its core, a virtual machine is a simulated computer running inside your real computer. Your physical hardware (the host) runs software called a hypervisor, which creates and manages one or more virtual machines (guests).
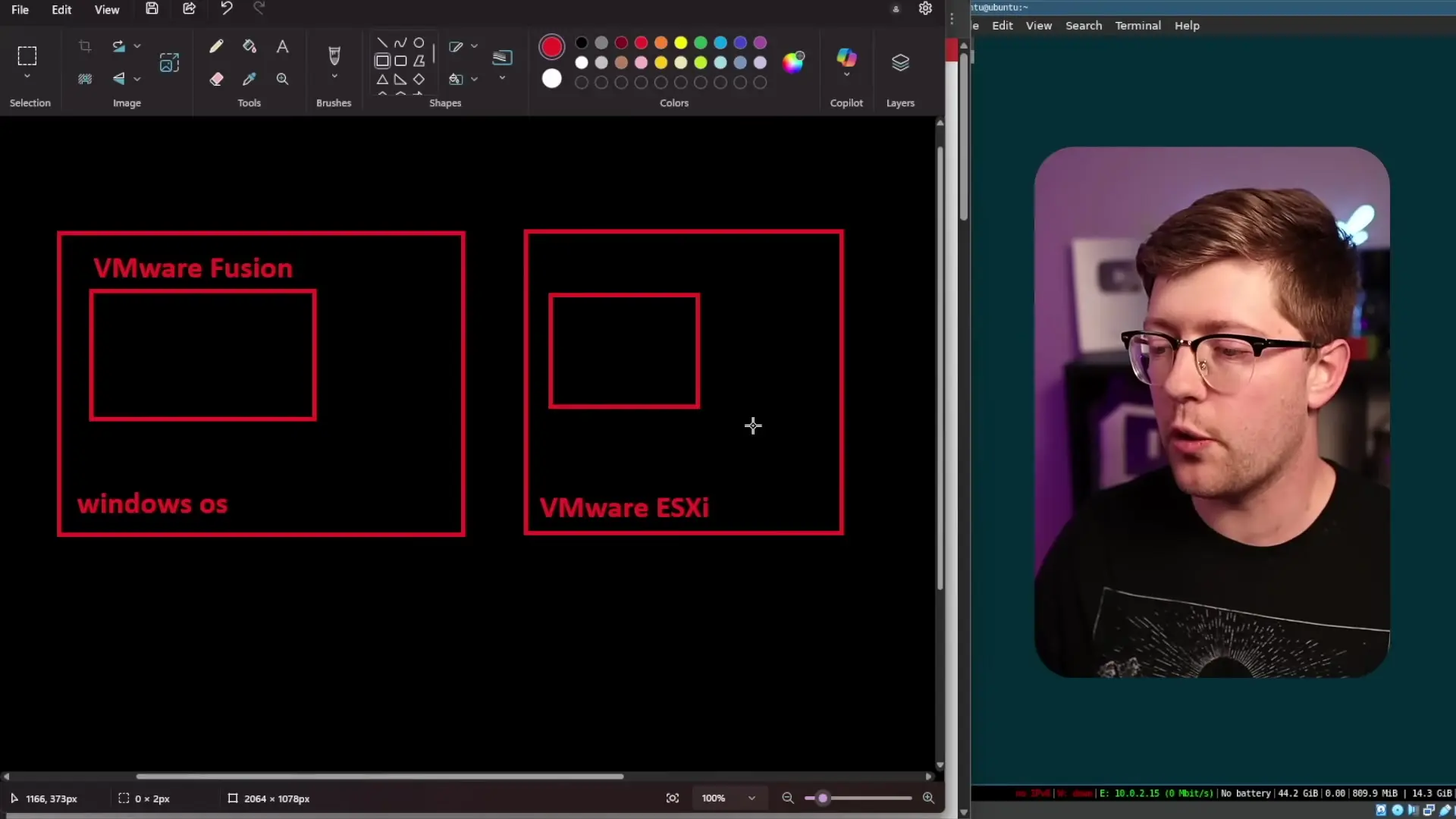
There are two main types of hypervisors:
- Type 1 hypervisors (like VMware ESXi): Run directly on hardware with no operating system underneath
- Type 2 hypervisors (like VMware Fusion or Workstation): Run as applications on top of a host operating system
The hypervisor creates the illusion for the guest OS that it has direct access to hardware resources like CPU, memory, storage, and network interfaces. In reality, these are all virtualized and controlled by the hypervisor, which enforces isolation between the guest and host systems.
Recent VMware Zero-Day Vulnerabilities
At the Pwn2Own competition, security researchers demonstrated several critical vulnerabilities in VMware products that could allow attackers to escape from a guest virtual machine and execute code on the host system. These vulnerabilities affected multiple VMware products including ESXi, Workstation, and Fusion.
The discovered vulnerabilities include:
- An integer underflow in the VMXNet3 virtual network adapter
- Vulnerabilities in the VM Communication Interface (VMCI)
- A heap overflow in the paravirtualized SCSI controller
- An information disclosure vulnerability
What makes these vulnerabilities particularly concerning is that they allow attackers to not just escape the VM but potentially gain kernel-level access on the host system. This represents a complete compromise of the security model that virtual machines are built upon.
How VM Escape Vulnerabilities Work
VM escape vulnerabilities typically exploit flaws in the interfaces between the guest VM and the hypervisor. These interfaces are necessary to provide virtualized hardware to the guest, but they also represent potential attack surfaces.
1. VMXNet3 Network Adapter Vulnerability
The VMXNet3 virtual network adapter allows the guest VM to communicate with the network. The vulnerability discovered is an integer underflow that could be exploited to write data outside the bounds of an array. Since network adapters typically run as drivers in the host kernel, this vulnerability potentially allows attackers to write arbitrary data to the host kernel memory.
2. VMCI (VM Communication Interface) Vulnerabilities
The VMCI is a messaging system that allows communication between the guest VM and the hypervisor. It's used for operations like USB device passthrough. The vulnerability here involves an integer overflow that could lead to bypassing security checks and potentially executing arbitrary code in the hypervisor context.
For example, if a length value is set to the maximum possible value for an unsigned integer and then incremented, it would overflow to zero. If the code then checks whether this length exceeds some maximum allowed value, the check would pass because zero is less than any maximum, even though the actual data being processed might be much larger.
3. Paravirtualized SCSI Heap Overflow
The SCSI interface is used for storage device access. The paravirtualized SCSI controller in VMware products had a heap overflow vulnerability that could be triggered by specially crafted commands from within the guest VM. A heap overflow occurs when data is written beyond the bounds of a memory allocation on the heap, potentially corrupting adjacent memory.
When exploited, this vulnerability could allow attackers to corrupt heap metadata and potentially achieve arbitrary code execution in the hypervisor or host kernel context.
The Technical Details of Exploitation
Let's dive deeper into how these vulnerabilities could be exploited:
Integer Underflow Exploitation
An integer underflow occurs when an operation results in a value below the minimum that can be represented by the variable's type. For unsigned integers, this means going below zero, which causes the value to wrap around to the maximum possible value.
// Example of integer underflow vulnerability
unsigned int length = 0;
// Decrement the value (dangerous when it's already 0)
length--;
// Now length has wrapped around to the maximum value (e.g., 4294967295 for 32-bit)
// If this is used as an array index or allocation size, it can lead to exploitationInteger Overflow Exploitation
Integer overflow occurs when an operation results in a value above the maximum that can be represented by the variable's type. For unsigned integers, this causes the value to wrap around to zero.
// Example of integer overflow vulnerability
unsigned int length = 0xFFFFFFFF; // Maximum value for 32-bit unsigned int
// Increment the value
length++;
// Now length is 0 due to overflow
// If code checks: if (length <= MAX_ALLOWED_SIZE) { ... }
// The check will pass even though the original intent was to process a massive amount of dataHeap Overflow Exploitation
Heap overflows can be particularly dangerous because they can lead to corruption of heap metadata, which can then be leveraged to achieve arbitrary code execution.
// Example of heap overflow vulnerability
char* buffer = (char*)malloc(32); // Allocate 32 bytes
// If the code doesn't properly validate input size:
memcpy(buffer, user_controlled_data, user_controlled_size); // Potential overflow
// If user_controlled_size > 32, this will overflow into adjacent heap memoryBy corrupting heap metadata, attackers can potentially manipulate the memory allocator to return pointers to arbitrary locations when subsequent allocations are made. This can lead to arbitrary write primitives and eventually code execution.
Impact and Implications
The discovery of these vulnerabilities has significant implications for organizations relying on virtualization for security isolation:
- Cloud service providers using VMware products could be vulnerable to attacks that compromise multiple customer VMs from a single compromised VM
- Organizations using VMs as sandboxes for malware analysis could find their analysis environments compromised
- Development and testing environments isolated in VMs could potentially be used as stepping stones to production environments
The financial incentives for discovering these vulnerabilities are substantial. At Pwn2Own Berlin alone, over $1 million in prizes was awarded, with a single research company earning $320,000 for their discoveries.
Mitigation and Best Practices
While these vulnerabilities are concerning, there are several steps organizations can take to mitigate the risks:
- Keep hypervisor software updated with the latest security patches
- Implement defense-in-depth strategies rather than relying solely on VM isolation
- Use additional security controls like network segmentation to limit the impact of potential VM escapes
- Consider using different virtualization technologies for different security contexts
- Monitor for unusual activity that might indicate a VM escape attempt
- Apply the principle of least privilege to limit what guest VMs can access
Could Memory-Safe Languages Have Prevented These Issues?
An interesting question is whether memory-safe languages like Rust could have prevented these vulnerabilities. For many of these issues, particularly the memory corruption vulnerabilities like heap overflows and integer overflows/underflows, a memory-safe language would indeed have made exploitation much more difficult or impossible.
Rust's ownership model and compile-time checks would catch many of these issues at compile time rather than allowing them to become runtime vulnerabilities. However, rewriting complex systems like hypervisors in new languages is a significant undertaking that comes with its own challenges.
Conclusion
Virtual machines remain one of the most effective isolation technologies available, but they are not perfect. The vulnerabilities discovered at Pwn2Own remind us that all software, including hypervisors, can contain bugs that undermine their security properties.
Understanding these vulnerabilities helps security professionals make informed decisions about when and how to use virtualization as part of their security strategy. By staying informed about the latest vulnerabilities and implementing appropriate mitigations, organizations can continue to benefit from virtualization while managing the associated risks.
As with all security technologies, virtual machines should be part of a layered defense strategy rather than being relied upon as the sole security boundary.
Let's Watch!
VM Escape Vulnerabilities: Can Hackers Break Out of Virtual Machines?
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence