
The Arch Linux User Repository (AUR) has recently been targeted by sophisticated attacks, with multiple malicious packages being uploaded that contain harmful code. These attacks specifically target users of popular browsers by disguising malware as patches or fixes for common issues.
Understanding the Attack Vector
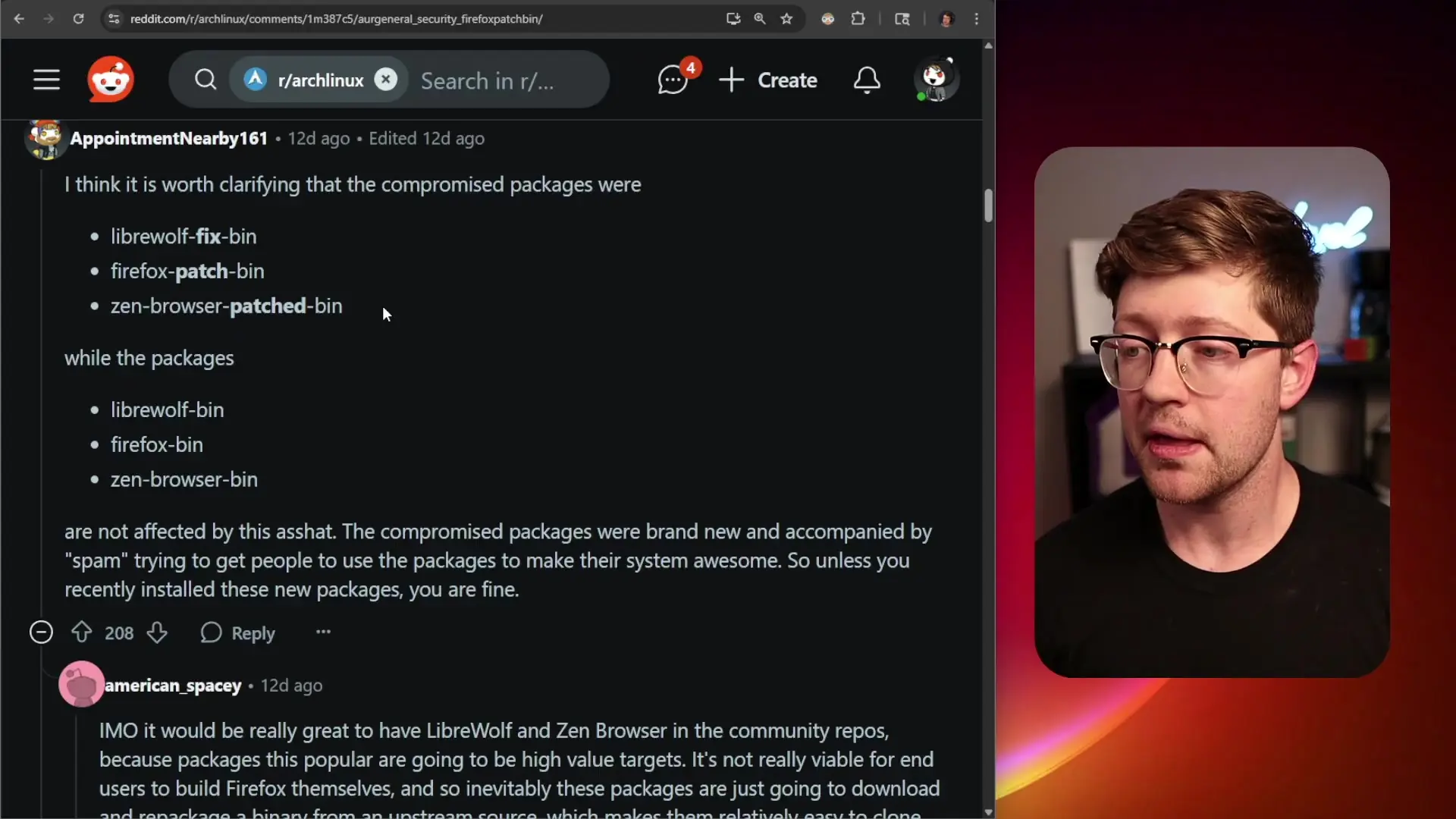
The compromised packages discovered in the AUR include 'Libreywolf-fix-bin', 'Firefox-patch-bin', and 'Zen-browser-patched-bin'. What makes these particularly dangerous is their naming similarity to legitimate packages: 'Libreywolf-bin', 'Firefox-bin', and 'Zen-browser-bin'. This subtle difference—the addition of words like 'fix' or 'patch'—creates a situation where users can easily install malware through a simple typo or tab completion error.
These malicious packages were removed approximately two days after their upload (on July 16th), but not before potentially affecting users who installed them during this window.
How the AUR Differs from Traditional Package Repositories
To understand why this attack was possible, it's important to recognize how the AUR differs from other package repositories like Debian's apt:
- The AUR is a community repository where anyone can upload packages with minimal verification
- Unlike apt, which contains pre-compiled binaries maintained by official teams, AUR packages are source-based
- AUR packages use PKGBUILD scripts (bash scripts) that can execute arbitrary code during installation
- When users install AUR packages, they're essentially running code from potentially untrusted sources
This open nature is both the AUR's strength and weakness—it provides unparalleled access to software but creates significant security challenges.
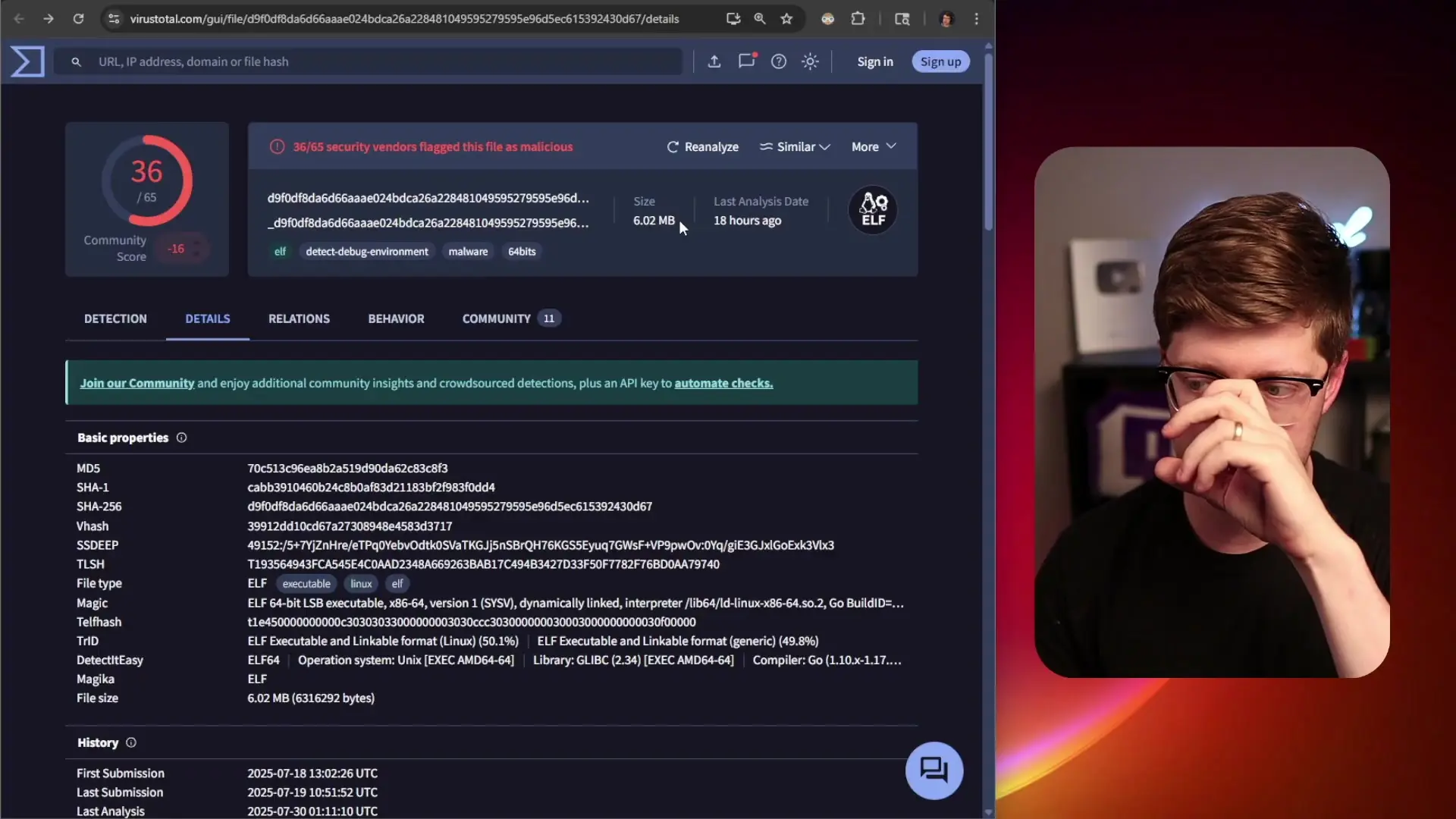
The Malware Analysis: Chaos RAT
Analysis of the malicious packages revealed they contained Chaos RAT (Remote Access Trojan), an open-source tool that provides attackers with extensive control over infected systems. The malware was configured to connect to a specific IP address on port 8080, establishing a backdoor connection.
Chaos RAT provides attackers with powerful capabilities on infected Linux systems:
- Reverse shell access (complete command control)
- File manipulation (download, upload, and delete)
- Screenshot capture
- Network communication
- Shared memory access
The malware was written in Go, evidenced by its 6MB size (typical of statically compiled Go binaries) and the symbols extracted by reverse engineering tools. Using an existing open-source RAT helps attackers blend in with other threat actors using similar tools, making attribution more difficult.
A Coordinated Attack Campaign
Evidence suggests this wasn't an isolated incident but part of a coordinated campaign. Multiple suspicious accounts were involved in promoting these packages, including accounts that appeared to be artificially building credibility through unrelated posts on other platforms.
Beyond the browser-related packages, other malicious uploads were discovered in the same timeframe, including 'Minecraft-cracked-ttf', 'MS-fonts-all', and 'Vesttopin-patched'. This pattern indicates a systematic attempt to compromise Arch Linux users through multiple vectors.
Protecting Yourself from AUR Security Threats
If you've installed any of these compromised packages, immediate action is required. Unlike official repositories, revoking a package from the AUR doesn't remove it from your system—you must manually uninstall it.
- Check your installed packages for any of the compromised names
- Immediately remove any suspicious packages using pacman
- Scan your system for potential backdoors or persistent threats
- Consider reinstalling your system if you suspect compromise
Best Practices for AUR Security
To minimize risks when using the AUR or any community-driven package repository, follow these security best practices:
- Always inspect PKGBUILD scripts before installing AUR packages
- Verify package maintainers and check their history/reputation
- Be wary of packages with names similar to popular software but with additional terms like 'fix' or 'patch'
- Use an AUR helper that encourages PKGBUILD review (like yay with its review option)
- Implement multi-factor authentication for your important accounts to limit damage if compromised
- Regularly update your system and monitor security advisories
The Broader Security Implications
This incident highlights a broader security concern in the open-source ecosystem. Many package managers (npm for JavaScript, pip for Python, etc.) operate on similar trust models where packages can be uploaded with minimal verification. This creates a systemic vulnerability where one compromised account or malicious package can affect thousands of systems.
The Arch Linux security team responded quickly in this case, but the fundamental challenge remains: balancing the openness that makes community repositories valuable with the security controls needed to protect users.
Conclusion: Vigilance in an Open Ecosystem
The recent attacks on Arch Linux's AUR repository serve as a reminder that security requires constant vigilance, especially in community-driven ecosystems. While the flexibility and breadth of software available through systems like the AUR provide tremendous value, they also create unique security challenges.
By understanding these risks and implementing proper security practices, users can continue to benefit from the AUR while minimizing exposure to malicious software. Remember that in package management, convenience should never come at the expense of security.
# To check if you have any of the compromised packages installed
pacman -Qs "firefox-patch-bin\|libreywolf-fix-bin\|zen-browser-patched-bin"
# To remove a compromised package
sudo pacman -R package-name
# Always inspect PKGBUILD before installing
less PKGBUILDLet's Watch!
Arch Linux Security Alert: Malicious Packages Threaten Users
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence