
The npm ecosystem recently experienced two major security attacks affecting packages with billions of weekly downloads. These sophisticated attacks deployed malicious code, stole secrets from development machines, and used worm-like behavior to spread across the dependency network. Understanding what happened and implementing proper security measures is now crucial for every JavaScript developer.
Understanding the Recent NPM Package Attacks
The first attack began with a phishing email that compromised a package maintainer's npm account. The attackers published a malicious version of their package containing code designed to steal cryptocurrency from website visitors. While this attack had limited success (reportedly stealing only about $1,000), it demonstrated a concerning vulnerability in the npm ecosystem.
The second, more dangerous attack targeted developer machines and CI/CD environments. This attack was particularly harmful because:
- It stole credentials including AWS access keys, npm tokens, and GitHub access tokens from development machines
- It exhibited worm-like behavior, using stolen credentials to spread to other packages
- It compromised hundreds of packages through dependency chains
- It created public GitHub repositories to exfiltrate stolen credentials
This second attack successfully compromised many packages by targeting an infrequently updated but widely used dependency. The malicious code would run during the build process, searching for and exfiltrating credentials while simultaneously using those credentials to spread further.

How to Check If You're Affected
If you're concerned your projects might be affected by these attacks, here are immediate steps to take:
- Check your package-lock.json file (not just package.json) for any known compromised packages and versions
- Look for unauthorized public GitHub repositories in your account, particularly ones with suspicious names
- Review your GitHub security logs for unauthorized actions like repository creation or visibility changes
- Audit your CI/CD environments for potential credential compromise
The package-lock.json file is particularly important because it lists all dependencies (including nested ones) with their exact versions, making it easier to identify compromised packages.
7 Essential NPM Security Practices to Implement Now
To protect your projects from similar attacks in the future, consider implementing these security practices:
1. Limit Package Usage
One of the most effective security measures is simply using fewer packages. While packages are convenient, each one represents a potential security risk. Before adding a new dependency, ask yourself if you really need it or if you could implement the functionality yourself, possibly with AI assistance for complex algorithms.
For simple operations like checking if a number is odd or even, writing your own code is safer than adding a dependency. With modern AI tools, generating secure code for many common tasks is easier than ever before.
2. Pin Dependency Versions
Fix your dependency versions completely, including patch versions. While many developers pin major and minor versions, leaving patch versions open can still create security vulnerabilities.
// Instead of this (allows patch updates)
{
"dependencies": {
"some-package": "^1.2.0"
}
}
// Use this (pins exact version)
{
"dependencies": {
"some-package": "1.2.0"
}
}By pinning exact versions, you ensure that no automatic updates occur without your explicit approval, reducing the risk of malicious code being introduced through updates.
3. Implement a Minimum Release Age Policy
Consider setting a minimum release age for package updates. This approach allows the community time to detect malicious packages before you install them.
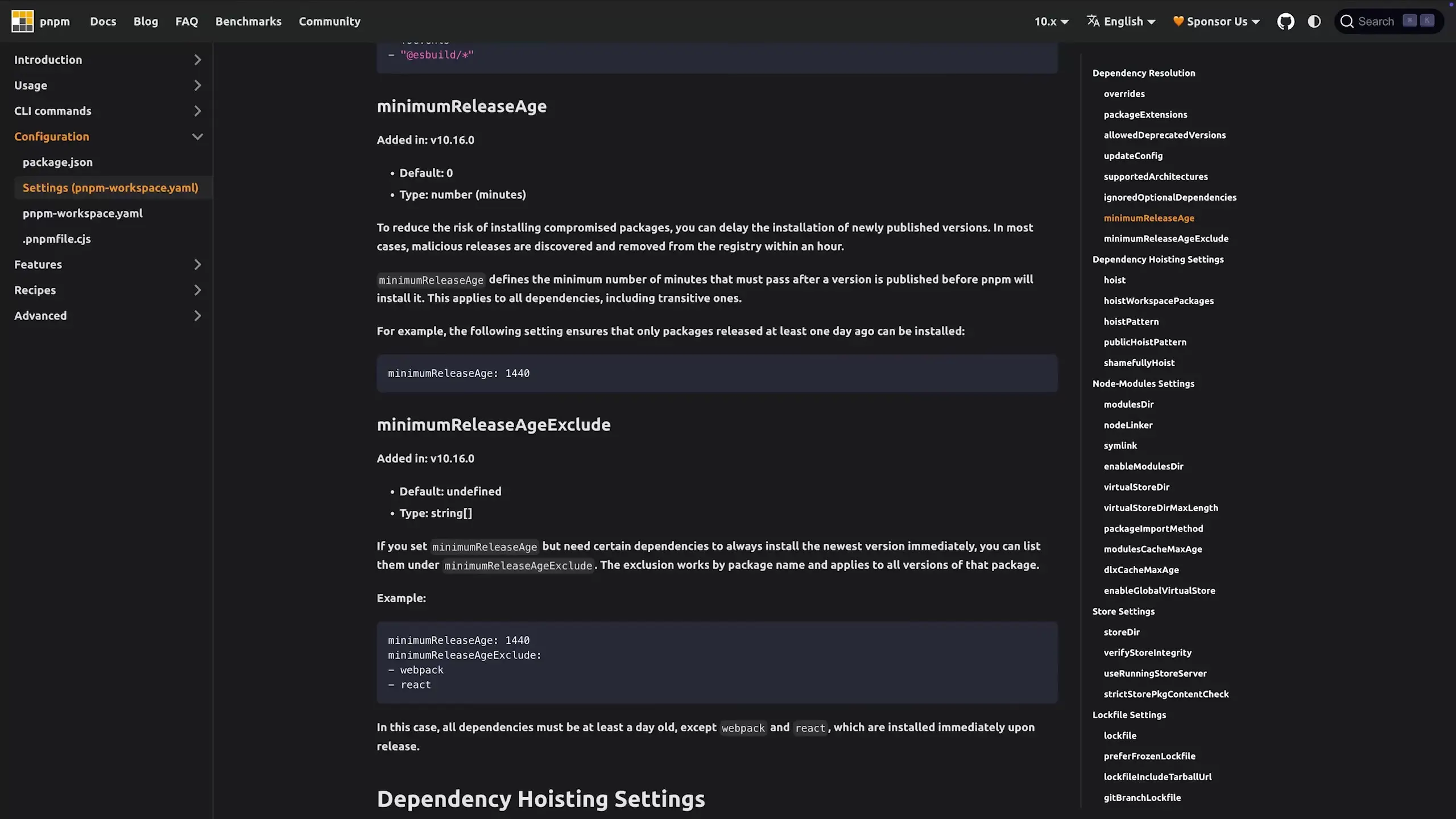
By waiting a few days or weeks before adopting new package versions, you give security researchers and the broader community time to identify and report potential security issues.
4. Use npm audit and Security Tools
Regularly run security audits on your dependencies. The npm ecosystem provides built-in tools for this purpose:
# Basic npm security audit
npm audit
# Fix automatically when possible
npm audit fix
# Get detailed information
npm audit --jsonAdditionally, consider using third-party security tools like Snyk, which can provide more comprehensive vulnerability scanning and monitoring.
5. Implement Lockfile Security
Your package-lock.json file is critical for security. Make sure to:
- Always commit your package-lock.json to version control
- Never manually edit this file
- Use npm ci instead of npm install in CI/CD environments to ensure exact versions are installed
- Regularly update and audit your lockfile
6. Use Private Registries or Proxies
For teams and organizations, consider using a private npm registry or proxy service. These services can:
- Cache approved packages
- Scan packages for vulnerabilities before allowing them into your environment
- Enforce organization-wide security policies
- Provide an additional layer of protection against supply chain attacks
Services like Verdaccio, npm Enterprise, or JFrog Artifactory can help implement this approach.
7. Secure Your CI/CD Environment
Since the recent attacks specifically targeted CI/CD environments to steal credentials, implementing proper security measures is essential:
- Use temporary, scoped credentials for CI/CD processes
- Implement the principle of least privilege for all service accounts
- Use secrets management solutions instead of environment variables when possible
- Regularly rotate all access tokens and credentials
- Consider using isolated build environments for each build
The Broader Impact on the NPM Ecosystem
These attacks highlight fundamental security challenges in the npm ecosystem and open-source dependencies in general. The interconnected nature of packages means that compromising one package can affect thousands of projects downstream.
The npm community and GitHub (which owns npm) are likely to implement additional security measures in response to these attacks. However, as developers, we cannot rely solely on platform-level protections. Taking personal responsibility for our dependency security is now an essential part of modern JavaScript development.
Conclusion
The recent npm package attacks serve as a wake-up call for the JavaScript community. By implementing the security practices outlined above, you can significantly reduce your risk of being affected by similar attacks in the future. Remember that security is a continuous process, not a one-time fix. Regularly review and update your security practices as new threats and defenses emerge.
While these attacks are concerning, they also provide an opportunity to strengthen our security posture and build more resilient systems. By taking security seriously and implementing proper precautions, we can continue to benefit from the npm ecosystem while minimizing the associated risks.
Let's Watch!
7 Critical NPM Security Practices After Recent Package Attacks
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence