
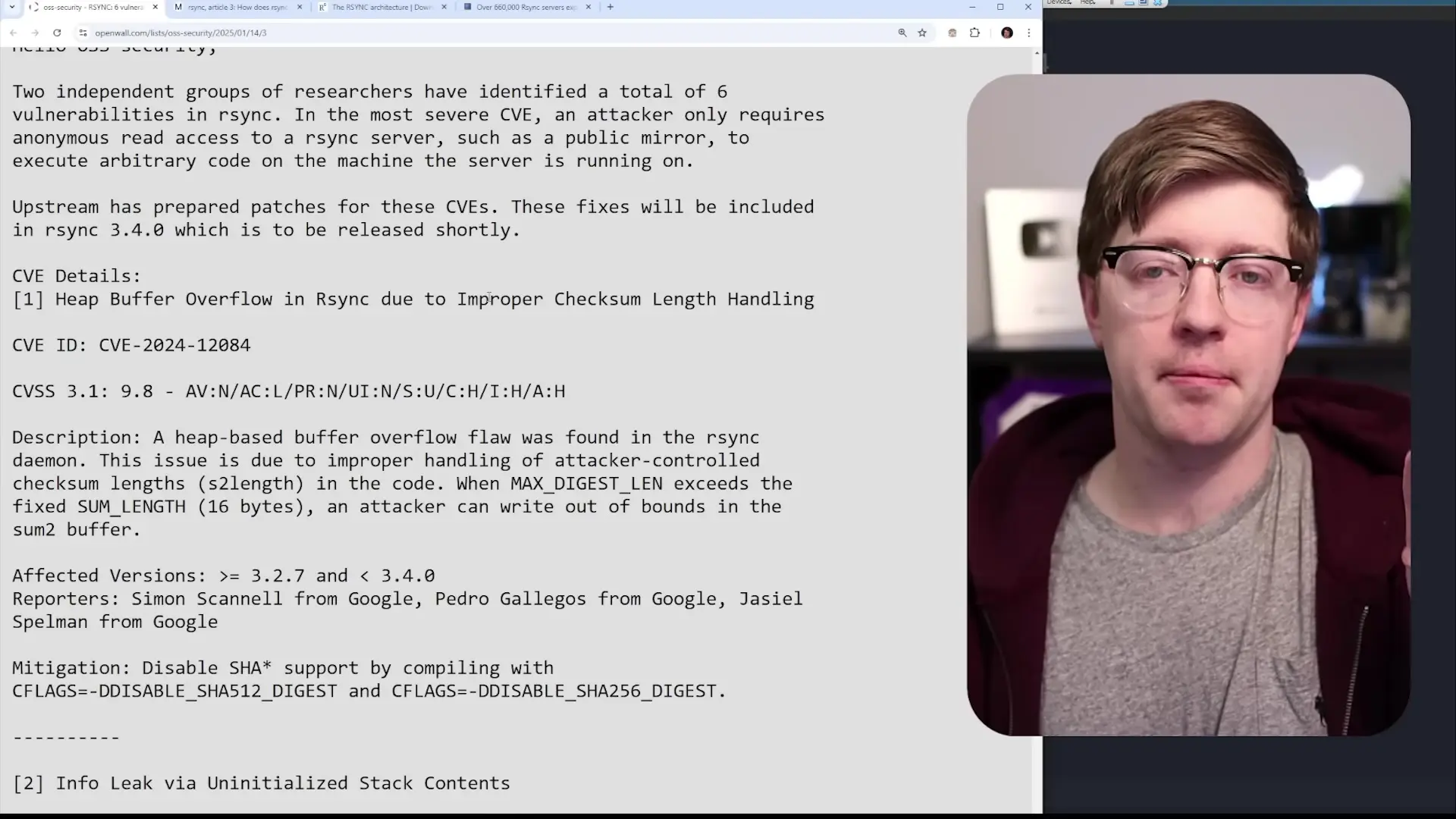
A critical security vulnerability with a 9.8 severity rating has been discovered in RSync, the widely-used file synchronization utility. This vulnerability is particularly concerning because it demonstrates that even in modern times, basic buffer overflow issues continue to plague important software tools. The flaw allows remote attackers to potentially execute arbitrary code on affected systems, making it a serious threat for organizations using RSync in their infrastructure.
Understanding RSync and Its Importance
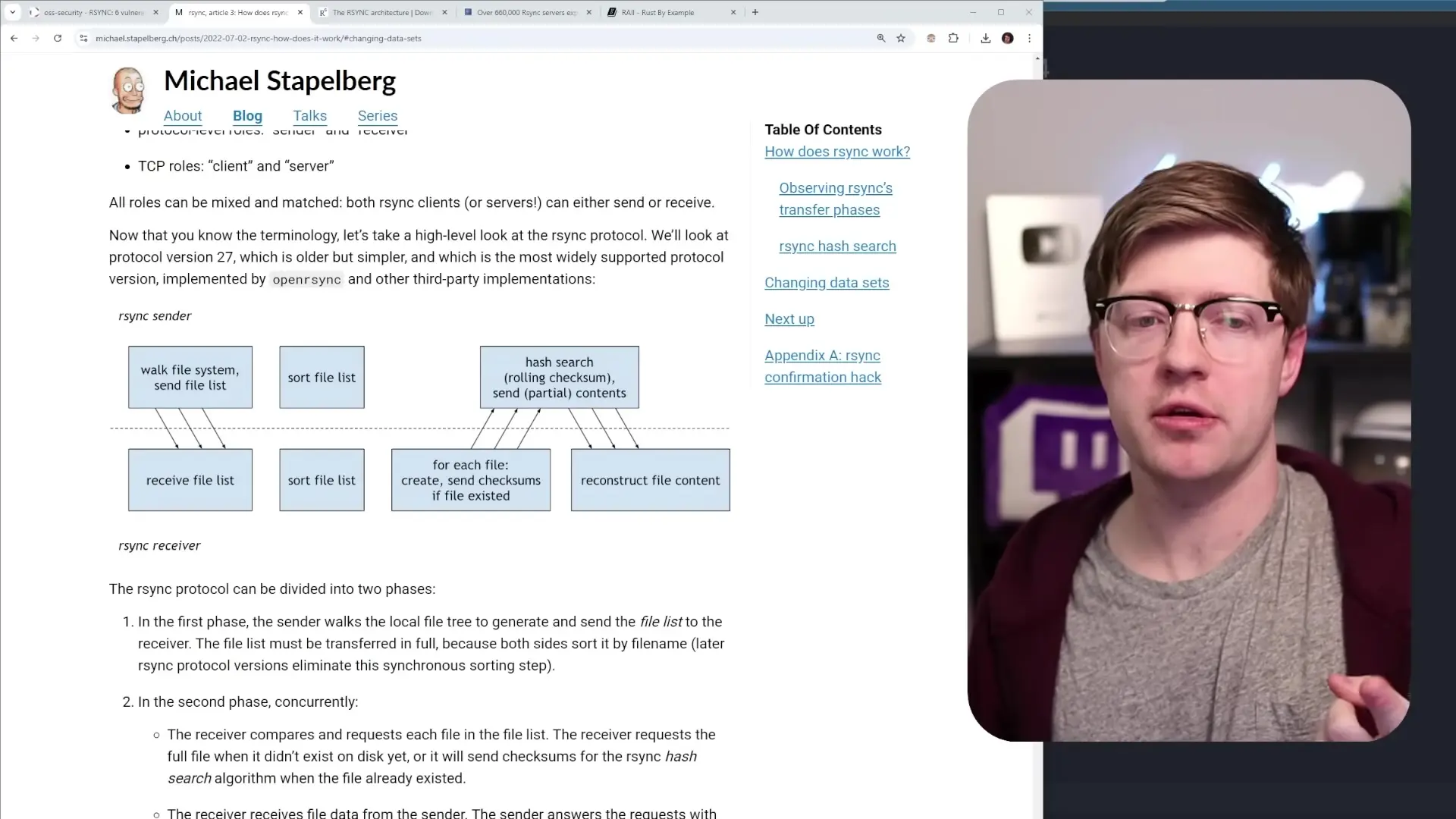
RSync (Remote Sync) is a widely-adopted utility used for efficiently synchronizing files between different locations. The name comes from "remote sync," as it allows users to specify synchronization between a client and server for particular folders. What makes RSync particularly valuable is its efficiency - instead of transferring entire files, it only transmits the parts that have changed.
The protocol works by walking through the file system and creating a list of files that exist in both locations. It then generates checksums for each file, allowing it to identify only the specific chunks that have changed. This approach significantly reduces bandwidth usage and transfer times, which is why RSync has remained a staple tool for system administrators and DevOps professionals for decades.
The Buffer Overflow Vulnerability Explained
The primary vulnerability discovered in RSync is a heap buffer overflow flaw that allows remote attackers to potentially execute arbitrary code. Understanding the technical details helps illustrate why this vulnerability is so serious.
At its core, the issue stems from how RSync handles checksums. When the server reads checksums from a client, it uses a buffer with a statically defined size of 16 bytes. The problem occurs when using a checksum algorithm that produces values larger than 16 bytes (such as SHA-256). While the code does validate that the checksum length doesn't exceed a maximum value, it fails to ensure that this maximum value matches the actual size of the allocated buffer.
/* Vulnerable code pattern */
// sum_length is statically defined as 16
char sum[sum_length];
// S2_length can be larger than sum_length
read_buf(S2_length, sum);This mismatch creates a classic heap buffer overflow vulnerability. When a checksum larger than 16 bytes is written into the buffer, it overflows into adjacent memory, potentially corrupting heap data structures. An attacker can exploit this to gain control of the program execution flow.
Why Wasn't This Caught Earlier?
One might wonder how such a fundamental issue could go undetected in widely-used software. The likely explanation is that the small size of the buffer structure meant that when overflow occurred, it was often padded by the heap allocator, making the issue less apparent. With at most 48 bytes of overflow in most cases, the corruption might not have immediately caused crashes or observable misbehavior.
Additionally, exploiting heap overflows typically requires chaining multiple vulnerabilities together. A single overflow is rarely sufficient to achieve complete system compromise.
Multiple Vulnerabilities Working Together
What makes this rsync security vulnerability particularly dangerous is that it was discovered alongside five other flaws that, when combined, create a much more exploitable scenario. These additional vulnerabilities include:
- Information leak via uninitialized stack contents - allowing attackers to bypass Address Space Layout Randomization (ASLR)
- Server leaking arbitrary client files through specially constructed checksum values
- Path traversal issues with the recursive option
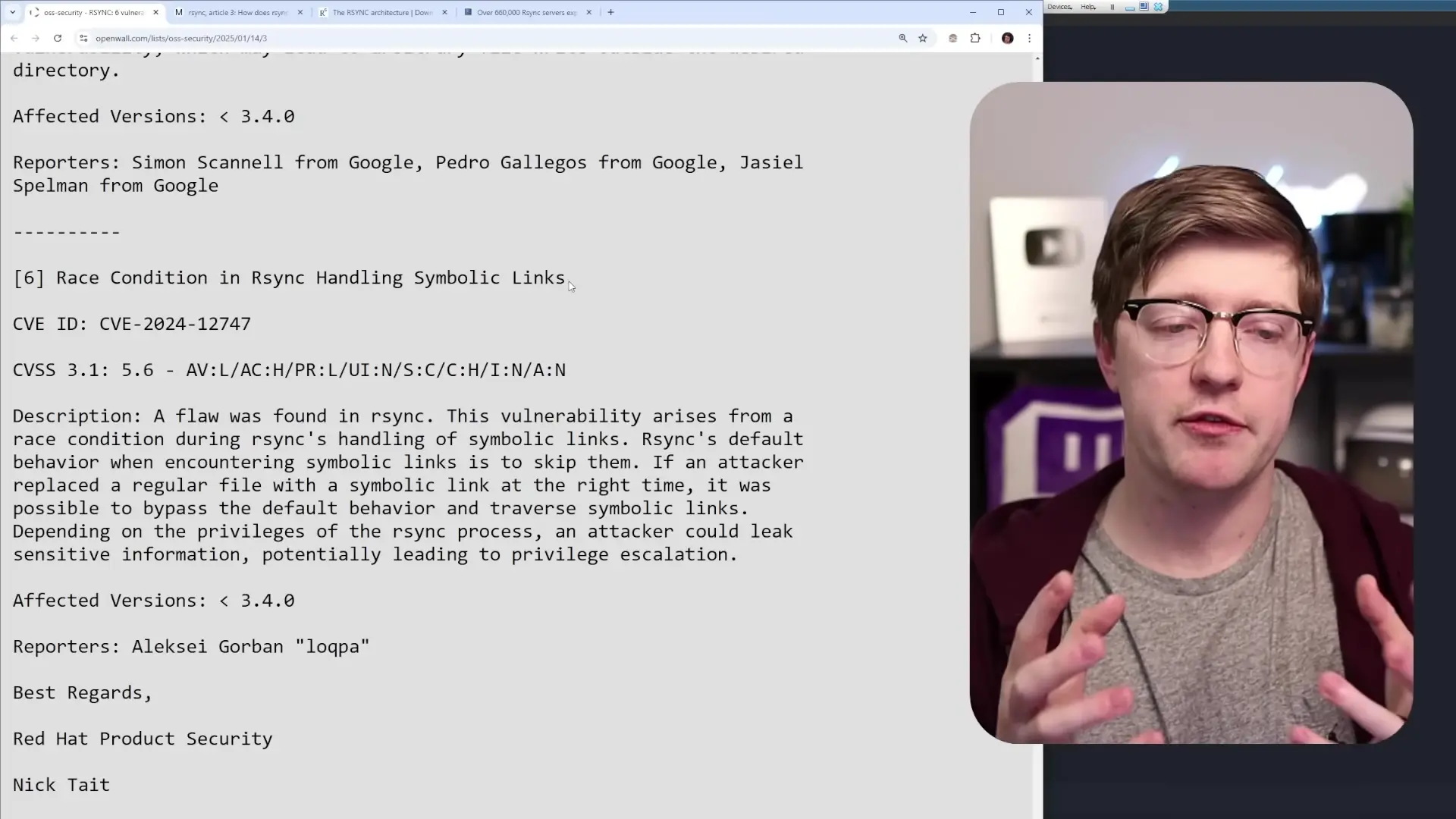
- Time-of-check-time-of-use (TOCTOU) race condition in symbolic link handling
- Additional symbolic link reversal issues
The information leak vulnerability is particularly significant as it helps bypass ASLR (Address Space Layout Randomization), a critical security mitigation that randomizes where programs are loaded in memory. By leaking memory addresses, attackers can determine the memory layout of the process and more effectively exploit the heap overflow.
The Time-of-Check-Time-of-Use Vulnerability
The TOCTOU vulnerability in RSync's symbolic link handling is another serious issue. By default, RSync doesn't handle symbolic links - it checks if a file is a symbolic link and backs off if it is. However, there's a time gap between checking a file's type and acting on it. During this window, an attacker could replace a regular file with a symbolic link, potentially gaining access to files outside the intended directory structure.
// Vulnerable pattern
if (is_regular_file(path)) { // Check
// Time gap where attacker can replace file with symlink
process_file(path); // Use
}Would Modern Languages Have Prevented This?
An interesting question is whether using a modern memory-safe language like Rust would have prevented these vulnerabilities. For the buffer overflow and information leak vulnerabilities, the answer is yes. Rust's memory safety guarantees would have caught the buffer overflow at runtime, turning it into a denial-of-service issue rather than a remote code execution vulnerability. Similarly, Rust's requirement for variable initialization would have prevented the information leak.
However, not all the vulnerabilities would have been prevented. The side-channel issue with checksums, the path traversal problems, and the logic issues in recursion implementation are language-agnostic design flaws. The TOCTOU race condition might even be exacerbated in Rust due to the additional overhead that could widen the time window between checking and using.
Mitigation and Protection Strategies
If you're using RSync in your environment, here are some steps to protect against these vulnerabilities:
- Update to the latest version of RSync immediately
- Consider running RSync in a restricted environment using containers or virtual machines
- Implement network-level controls to restrict who can connect to RSSync servers
- Use secure authentication methods when configuring RSSync
- Monitor for unusual activity or unexpected file access patterns
Lessons for Developers
This rsync server vulnerability offers several important lessons for developers:
- Never trust user-controlled input sizes without proper validation against actual buffer sizes
- Always initialize variables before use, especially when they might be exposed to external systems
- Be aware of race conditions in file system operations
- Consider memory-safe languages for new security-critical applications
- Implement comprehensive testing, including security-focused fuzzing and static analysis
Conclusion
The discovery of these rsync vulnerabilities serves as a stark reminder that even well-established software can harbor serious security flaws. Basic buffer overflows continue to plague software in modern times, and when combined with other vulnerabilities, they can create significant security risks.
This case also highlights the importance of ongoing security research and the value of memory-safe programming languages. While no solution is perfect, adopting modern development practices and security-focused design principles can significantly reduce the risk of such vulnerabilities in future software.
Let's Watch!
Critical RSync Vulnerability: How a 9.8 Severity Buffer Overflow Exposes Servers
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence