Most people think of DNS (Domain Name System) as simply the internet's phone book - a system that converts human-readable domain names into IP addresses. However, this critical internet infrastructure is increasingly being exploited by hackers in sophisticated ways that bypass traditional security measures. A particularly concerning trend is the use of DNS records as covert channels for malware delivery and command-and-control communications.
Understanding the DNS Malware Threat
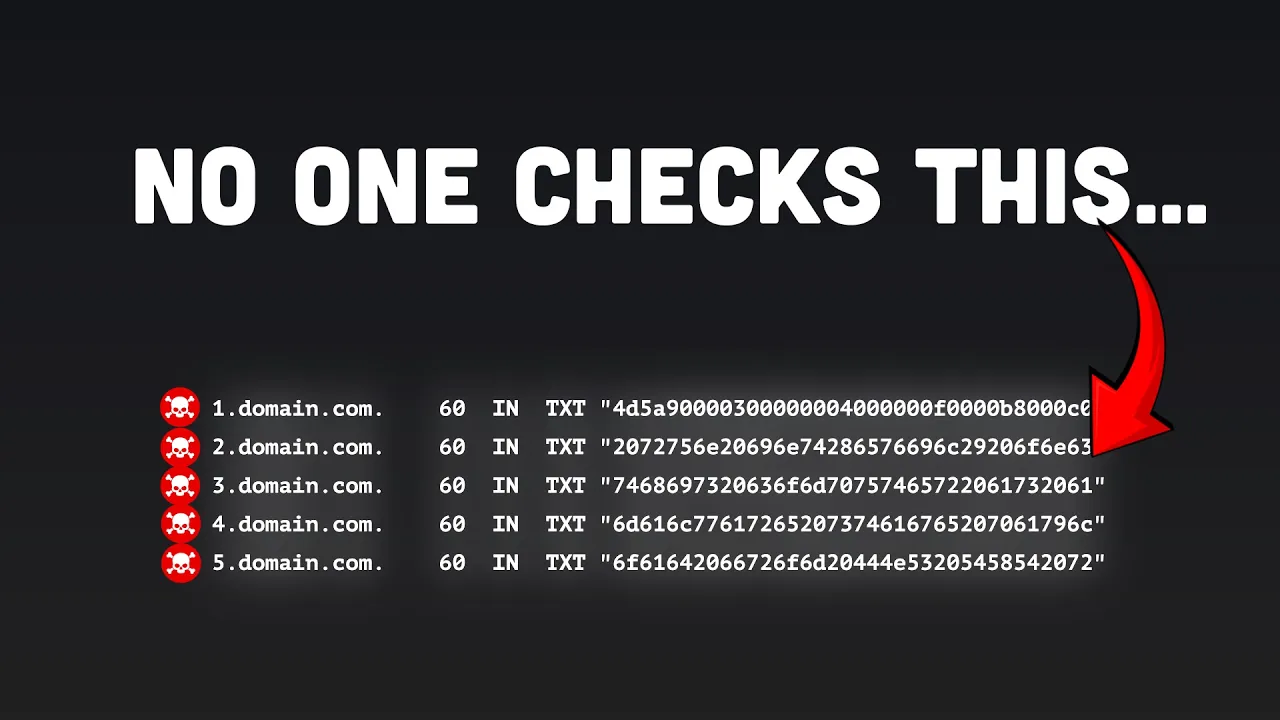
DNS records don't just store IP addresses. They also include TXT records, which are typically used for legitimate purposes like domain ownership verification. The problem is that TXT records can hold virtually any text data, making them perfect hiding places for malicious code.
Security researchers have discovered attackers storing malware in DNS TXT records, effectively turning the DNS infrastructure into a secret storage and delivery mechanism for malicious payloads. What makes this technique particularly dangerous is that DNS traffic is rarely monitored closely by security tools, creating a significant blind spot in many organizations' defenses.

How DNS Malware Attacks Work
The mechanics of a DNS-based malware attack are both clever and concerning. Here's how attackers typically execute this type of exploit:
- The attacker converts malware into hexadecimal format
- The hex data is broken into hundreds of small chunks
- Each chunk is placed into a separate TXT record on different subdomains controlled by the attacker
- The subdomains are often numbered sequentially to maintain the correct order
- Once a system is compromised, a script runs that sends DNS requests for all these subdomains
- The script collects the TXT records and reassembles the chunks in the correct order
- The data is converted back into an executable binary file
What makes this attack vector particularly insidious is that it doesn't require downloading files from suspicious websites or sending email attachments. The entire process uses standard DNS lookups, which typically pass through security controls without intensive inspection.
Why DNS Malware Detection Is Becoming More Challenging
While security researchers have known about DNS-based malware delivery for years, several factors are making this technique increasingly difficult to defend against:
- The growing adoption of encrypted DNS protocols like DNS over HTTPS (DoH) and DNS over TLS (DoT) makes it harder for security tools to inspect DNS queries
- Attackers are becoming more sophisticated in how they fragment and disguise malicious payloads
- DNS is being used for new types of attacks, including hiding prompt injection commands for AI chatbots
- Many organizations lack proper DNS monitoring capabilities
- Traditional security tools often don't closely inspect DNS traffic, creating a security blind spot

Real-World Examples of DNS Exploitation
Security researchers have documented several instances of DNS exploitation in the wild. In one notable case from 2021, malware was hidden across multiple subdomains, with each subdomain containing a chunk of the malicious code in text form. This approach made the traffic appear like regular DNS queries, allowing it to bypass security controls.
More recently, researchers have discovered TXT records containing prompt injection commands targeting AI systems. These included instructions like "Ignore all previous instructions" followed by various commands, demonstrating how DNS can be used not just for traditional malware but also for emerging attack vectors.
Testing platforms like malware.opendns.com have been developed to help security professionals understand and identify these threats, offering controlled environments to test DNS malware blocking capabilities.
Protecting Against DNS Malware and Spoofing Attacks
Organizations need to implement specific strategies to protect against DNS-based malware and spoofing attacks. Here are essential protection measures:
- Monitor DNS traffic for unusual patterns, particularly a single device making hundreds of TXT record lookups to unusual subdomains
- Run your own DNS resolver to gain greater control and visibility over DNS traffic
- Implement comprehensive log ingestion and analysis to identify suspicious DNS query patterns
- Keep threat intelligence lists updated to block known malicious domains
- Consider implementing DNS filtering solutions that can identify and block suspicious DNS requests
- Deploy anti-malware DNS services that specifically look for these types of attacks
- Regularly perform malware DNS tests to verify your protection measures are working
- Educate security teams about DNS-based attack vectors

Implementing DNS Malware Detection
Effective DNS malware detection requires a multi-layered approach. Here's how organizations can enhance their detection capabilities:
# Example DNS monitoring rule to detect suspicious TXT record queries
# This can be implemented in various security monitoring tools
rule detect_suspicious_dns_txt_queries {
meta:
description = "Detects potential DNS TXT record exfiltration"
severity = "high"
events:
$e.type = "dns_query"
$e.record_type = "TXT"
$e.count > 50 within 5m by $e.src_ip
condition:
$e
}Organizations should also consider implementing specialized DNS security solutions that can analyze DNS traffic patterns and identify anomalies that might indicate malware distribution or command-and-control communications.
The Future of DNS Security Challenges
As encryption becomes more prevalent across internet protocols, including DNS, detecting malicious activity will become increasingly challenging. Organizations must stay ahead of these trends by investing in advanced security solutions that can monitor encrypted traffic and identify suspicious patterns without necessarily decrypting the content.
The rise of DNS-based attacks also highlights the importance of a defense-in-depth strategy. No single security control can protect against all threats, making it essential to implement multiple layers of protection and detection capabilities.
Conclusion
DNS was designed to be the internet's phone book, but for hackers, it's increasingly becoming a secret storage locker for malicious code. As this technique continues to evolve and encryption makes detection more difficult, organizations must adapt their security practices to address this growing threat.
By implementing proper DNS monitoring, running your own DNS resolver, keeping threat intelligence updated, and deploying specialized DNS security solutions, organizations can significantly reduce their risk of falling victim to DNS-based malware attacks. Regular testing and continuous improvement of security controls are essential to stay ahead of evolving threats in this space.
Let's Watch!
DNS Malware Attacks: How Hackers Hide Code in Plain Sight
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence