
In today's complex software environments, managing sensitive credentials has become a critical challenge for organizations. HashiCorp Vault addresses this challenge by providing a robust, centralized solution for secret management. This comprehensive tutorial will explain what Vault is, why it was created, and how it solves common security problems that plague modern applications and infrastructure.
What is HashiCorp Vault?
HashiCorp Vault is a secrets management tool designed to securely store and control access to tokens, passwords, certificates, API keys, and other sensitive data. Available as both a free open-source solution and an enterprise version, Vault provides a unified interface to any secret while providing tight access control and recording a detailed audit log.
Understanding the Problem: Secret Sprawl
Before diving into how Vault works, it's important to understand the problem it solves. In modern applications, secrets are everywhere. These include:
- Username and password credentials
- API tokens for external services
- SSH keys for server access
- TLS certificates for secure communications
- Database connection strings
- Payment processor API keys (like Stripe)
- Social media API credentials
These secrets are needed by both human users (like engineers accessing a Kubernetes cluster) and system users (like CI/CD pipelines deploying applications or applications connecting to databases).
The challenge arises when these secrets start appearing in multiple locations—a phenomenon known as "secret sprawl." Secrets might be:
- Stored locally on engineers' computers
- Shared in KeyPass files between team members
- Listed in plain text on internal documentation (like Confluence pages)
- Stored as environment variables in CI/CD pipelines
- Hardcoded in application source code (a dangerous but common practice)
- Embedded in configuration files
- Set as environment variables on servers
The Two Major Problems with Secret Sprawl
Secret sprawl creates two significant security challenges for organizations:
1. Lack of Visibility and Control
When secrets are scattered across various systems, it becomes nearly impossible to track:
- Who has access to which secrets
- Who has used specific credentials and when
- Where all instances of a particular secret are stored
- If a secret has been compromised and how it happened
2. Difficult Secret Rotation
When a secret needs to be changed—either proactively as part of security best practices or reactively after a breach—finding and updating all instances becomes a major challenge. Without knowing where all copies of a secret exist, organizations can't ensure complete rotation, leaving potential security gaps.
How HashiCorp Vault Solves These Problems
Vault addresses secret sprawl and its associated challenges through several key mechanisms:
Centralized Secret Storage
Instead of having secrets scattered across various systems, Vault provides a single, secure repository. This centralization immediately reduces the attack surface and simplifies management.
Encryption at Rest and in Transit
All secrets in Vault are encrypted both while stored (at rest) and when being transmitted (in transit). Even if someone were to intercept the data or gain access to the storage, they would be unable to read the encrypted secrets without proper authorization.
Fine-grained Access Control
Vault implements detailed access policies that determine which users or systems can access which secrets. This follows the principle of least privilege, ensuring entities only have access to the specific secrets they need.
Comprehensive Audit Logging
Every interaction with Vault—whether successful or failed—is logged. This creates a detailed audit trail showing who accessed what secrets and when, providing crucial visibility for security monitoring and compliance.
Dynamic Secret Generation
Rather than storing long-lived static credentials, Vault can generate short-lived, dynamic credentials on demand. For example, instead of storing a permanent database password, Vault can create temporary credentials with limited permissions that automatically expire after use.
Automated Secret Rotation
Vault can automatically rotate secrets based on policies or schedules, ensuring credentials are regularly refreshed without manual intervention. This significantly reduces the risk associated with long-lived credentials.
Setting Up HashiCorp Vault: A Beginner's Guide
Getting started with HashiCorp Vault is straightforward. Here's a basic guide to installing Vault on Ubuntu, one of the most common deployment platforms:
Installing HashiCorp Vault on Ubuntu
# Add the HashiCorp GPG key
curl -fsSL https://apt.releases.hashicorp.com/gpg | sudo apt-key add -
# Add the official HashiCorp repository
sudo apt-add-repository "deb [arch=amd64] https://apt.releases.hashicorp.com $(lsb_release -cs) main"
# Update and install Vault
sudo apt-get update && sudo apt-get install vaultAfter installation, you'll need to configure Vault by creating a configuration file. Here's a basic development configuration to get started:
# config.hcl
storage "file" {
path = "/opt/vault/data"
}
listener "tcp" {
address = "127.0.0.1:8200"
tls_disable = 1 # Only for development; use TLS in production
}
api_addr = "http://127.0.0.1:8200"
ui = trueYou can then start Vault with the following command:
vault server -config=config.hclAfter starting the server, you'll need to initialize and unseal Vault before it's ready for use. This involves generating encryption keys and setting up initial access credentials.
Key Features of HashiCorp Vault
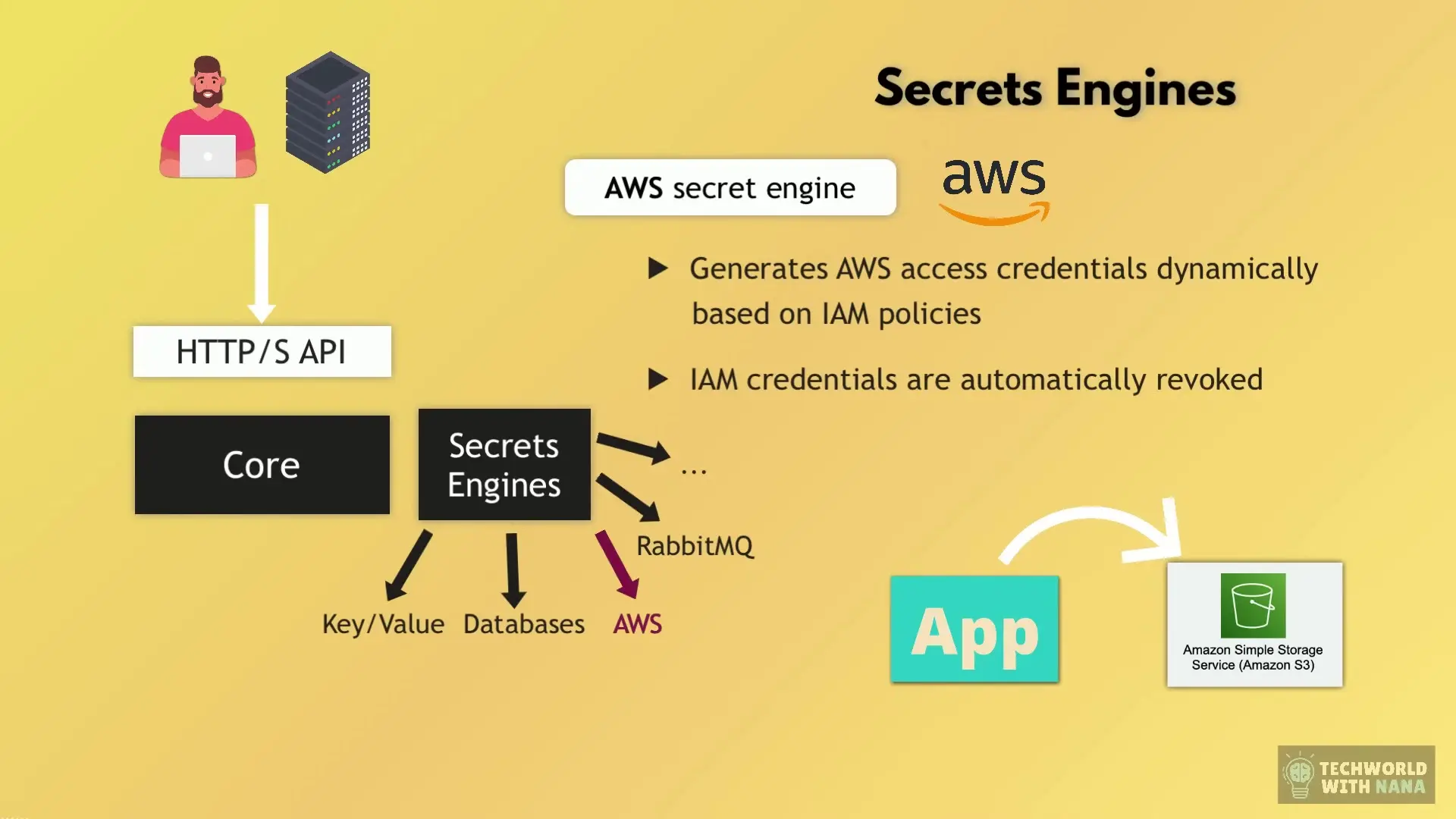
Secrets Engines
Vault uses pluggable components called "secrets engines" to interface with various external systems. These engines can store, generate, or encrypt data. Some common secrets engines include:
- Key/Value: Store static secrets
- AWS: Dynamically generate AWS access credentials
- Database: Create dynamic database credentials
- PKI: Generate X.509 certificates
- Transit: Perform encryption as a service
Authentication Methods
Vault supports multiple authentication methods to verify identities before granting access to secrets:
- Token: The default method using Vault-generated tokens
- Username/Password: Traditional credential-based authentication
- AppRole: Machine-to-machine authentication
- AWS/Azure/GCP: Cloud provider identity verification
- Kubernetes: Authentication using Kubernetes service accounts
- LDAP: Integration with directory services
- GitHub: Authentication via GitHub teams

HashiCorp Vault Deployment Considerations
While a development setup is easy to create, a production deployment of Vault requires careful planning:
High Availability Setup
For production environments, Vault should be deployed in a high-availability (HA) configuration with multiple nodes to ensure reliability. This typically involves:
- Multiple Vault server instances
- A consistent backend storage like Consul
- Load balancing across instances
- Automated unsealing processes
Storage Backend
Vault requires a storage backend to persist its data. While the file backend works for development, production environments should use a more robust solution:
- Consul (recommended by HashiCorp)
- PostgreSQL
- MySQL
- DynamoDB
- Integrated storage (Raft)
Unsealing Strategy
When Vault starts, it begins in a sealed state and needs to be unsealed before use. For production, consider auto-unsealing options using cloud KMS services from AWS, GCP, or Azure.
Using HashiCorp Vault with Applications
Integrating Vault with your applications typically follows these patterns:
AppRole Authentication for Services
AppRole is designed for machine-to-machine authentication, making it ideal for applications to authenticate with Vault. The process involves:
- Creating an AppRole with appropriate policies
- Configuring the application with a RoleID and SecretID
- The application authenticates to Vault using these credentials
- Vault provides a token the application can use to access secrets
# Create an AppRole
vault write auth/approle/role/my-app \
token_ttl=1h \
token_max_ttl=4h \
token_policies=my-app-policy
# Get RoleID
vault read auth/approle/role/my-app/role-id
# Generate SecretID
vault write -f auth/approle/role/my-app/secret-idKubernetes Integration
Vault integrates seamlessly with Kubernetes through the Vault Kubernetes auth method and the Vault Agent Injector, which can automatically inject secrets into pods as files or environment variables.
Is HashiCorp Vault Free?
HashiCorp Vault comes in two versions:
- Vault Community Edition (Vault CE): This is the free, open-source version that includes all core functionality for secret management.
- Vault Enterprise: This paid version adds advanced features like namespaces for multi-tenancy, automated replication across data centers, and enhanced MFA capabilities.
For most organizations starting with secret management, the free community edition provides all the necessary functionality to solve the core problems of secret sprawl and credential management.
Conclusion: Why HashiCorp Vault is Essential for Modern Infrastructure
Secret management is no longer optional in today's complex, distributed systems. HashiCorp Vault provides a comprehensive solution to the challenges of secret sprawl by centralizing storage, implementing strong encryption, providing fine-grained access control, and maintaining detailed audit logs.
By implementing Vault, organizations can significantly improve their security posture, simplify credential management, and ensure that sensitive information remains protected throughout its lifecycle. Whether you're managing a small application or a large enterprise infrastructure, Vault's flexible architecture and robust feature set make it an essential tool in your security arsenal.
As you begin your journey with HashiCorp Vault, start with simple use cases like storing static secrets, then gradually expand to more advanced features like dynamic credentials and automated rotation. With each step, you'll be building a more secure, manageable foundation for your sensitive data.
Let's Watch!
HashiCorp Vault Tutorial: Why Every DevOps Engineer Needs This Free Secret Management Tool
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence