
Linux system administrators face a constant battle against security vulnerabilities that could allow unauthorized users to gain elevated privileges. Two particularly concerning vulnerabilities—CVE-2025-6018 and CVE-2025-6019—demonstrate how attackers can exploit logical flaws rather than memory corruption to gain root access on vulnerable systems. Let's examine how these vulnerabilities work and what makes them particularly dangerous.
Understanding PAM and the First Vulnerability (CVE-2025-6018)
The first vulnerability (CVE-2025-6018) affects Open SUSE's implementation of PAM (Pluggable Authentication Modules). PAM is a critical security framework that manages authentication, authorization, and account management on Linux systems. Applications that are PAM-aware rely on these libraries to determine what users can and cannot do on a system.
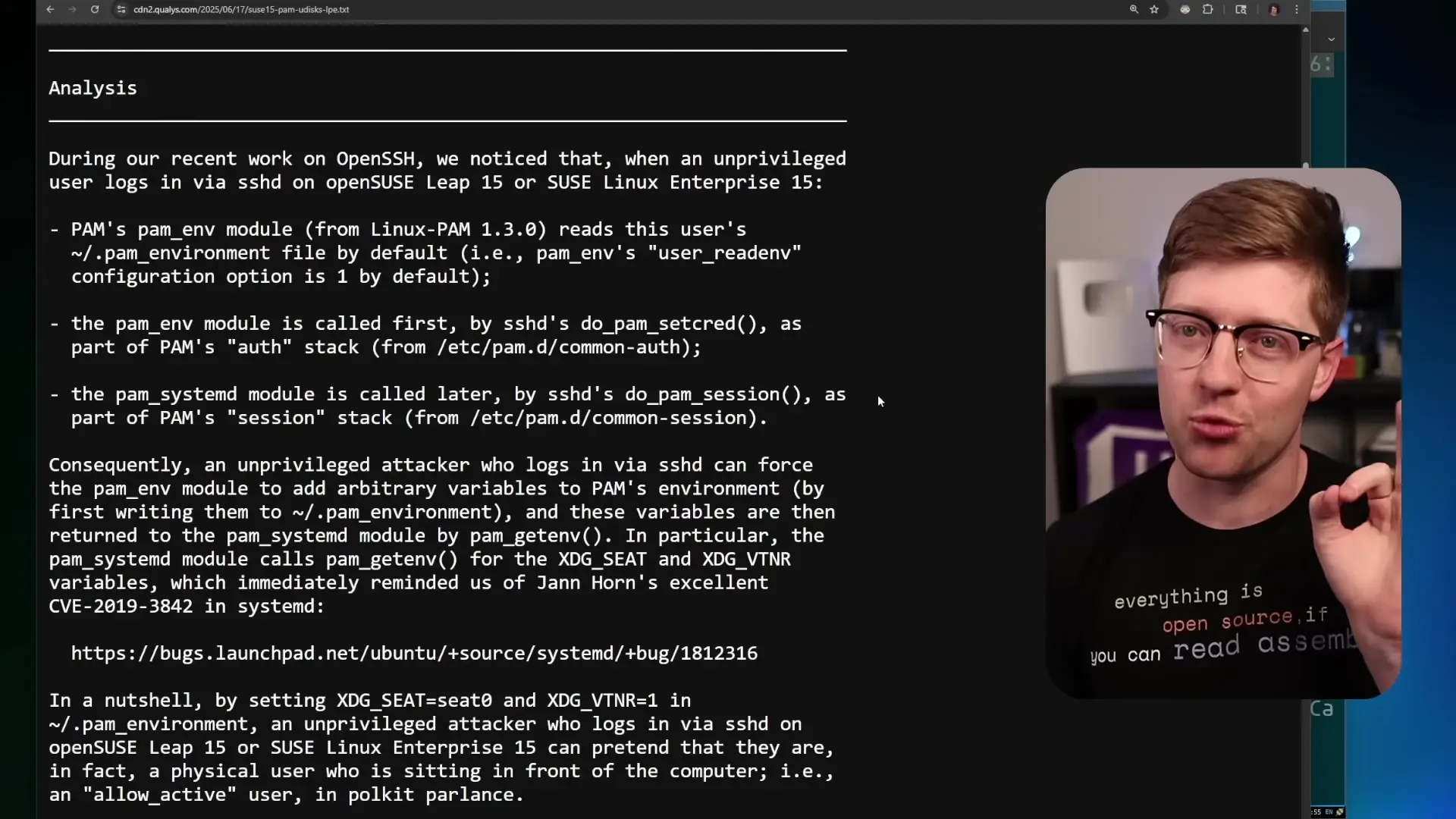
The vulnerability stems from how Open SUSE's PAM implementation processes environment variables. Environment variables are key-value pairs that define the operating context for processes, such as specifying the shell type, current working directory, or user session information. The PAM stack uses these variables to pass authentication parameters between components.
The critical flaw occurs in the ordering of how PAM reads its environment file. An unprivileged user can exploit this by creating a file with specific environment variables that trick the system into believing they have physical access to the machine.
# Creating malicious PAM environment file
echo "XDG_SEAT=seat0" > ~/.pam_environment
echo "XDG_VTNR=1" >> ~/.pam_environmentWhen a user logs back into the system after setting these variables, the PAM modules will interpret them as evidence that the user is physically sitting at the computer (at "seat0" with virtual terminal number 1). This grants the user the "allow_active" flag, which enables them to perform actions normally restricted to users with physical access, such as rebooting the system.
The Second Vulnerability: Exploiting File System Mounting (CVE-2025-6019)
While the first vulnerability grants additional privileges, it doesn't directly provide root access. This is where the second vulnerability (CVE-2025-6019) comes into play, affecting any distribution using lib-blockdev.
This vulnerability exploits how Linux handles setuid binaries on mounted file systems. Setuid (Set User ID) binaries are programs that run with the privileges of the file owner rather than the user executing them. For security reasons, when mounting external file systems, Linux typically disables setuid binaries using the "nosuid" flag.
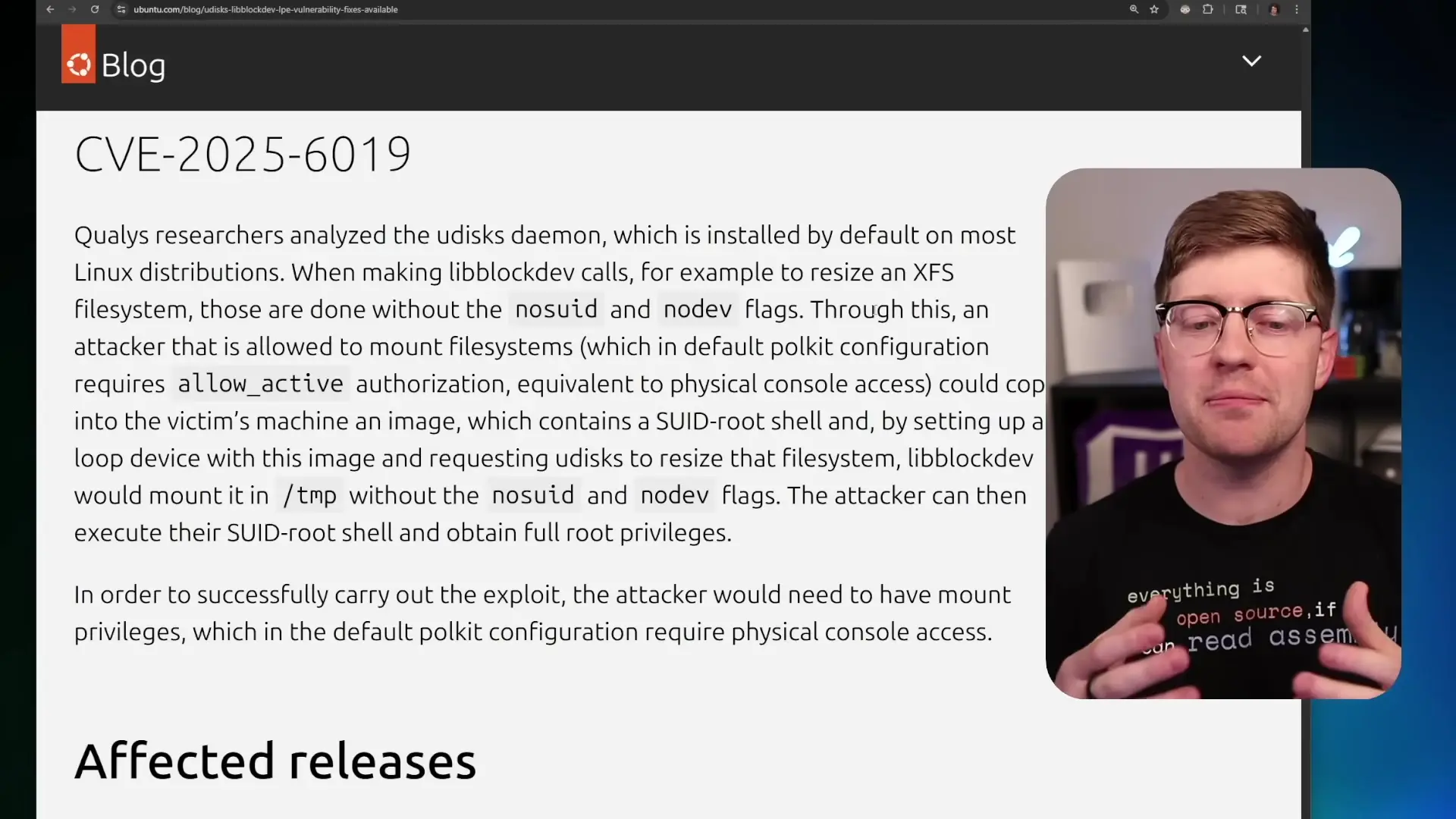
The vulnerability occurs when a user with the "allow_active" privilege (gained from the first exploit) requests the system to resize an XFS file system. During the resize operation, the system temporarily mounts the file system without the "nosuid" flag. This creates a brief window where setuid binaries on that file system can be executed with their elevated privileges.
To exploit this, an attacker can:
- Create an XFS file system image containing a setuid root bash binary
- Upload this image to the target system
- Use a while loop to keep the file system busy, preventing automatic unmounting
- Trigger a resize operation on the file system
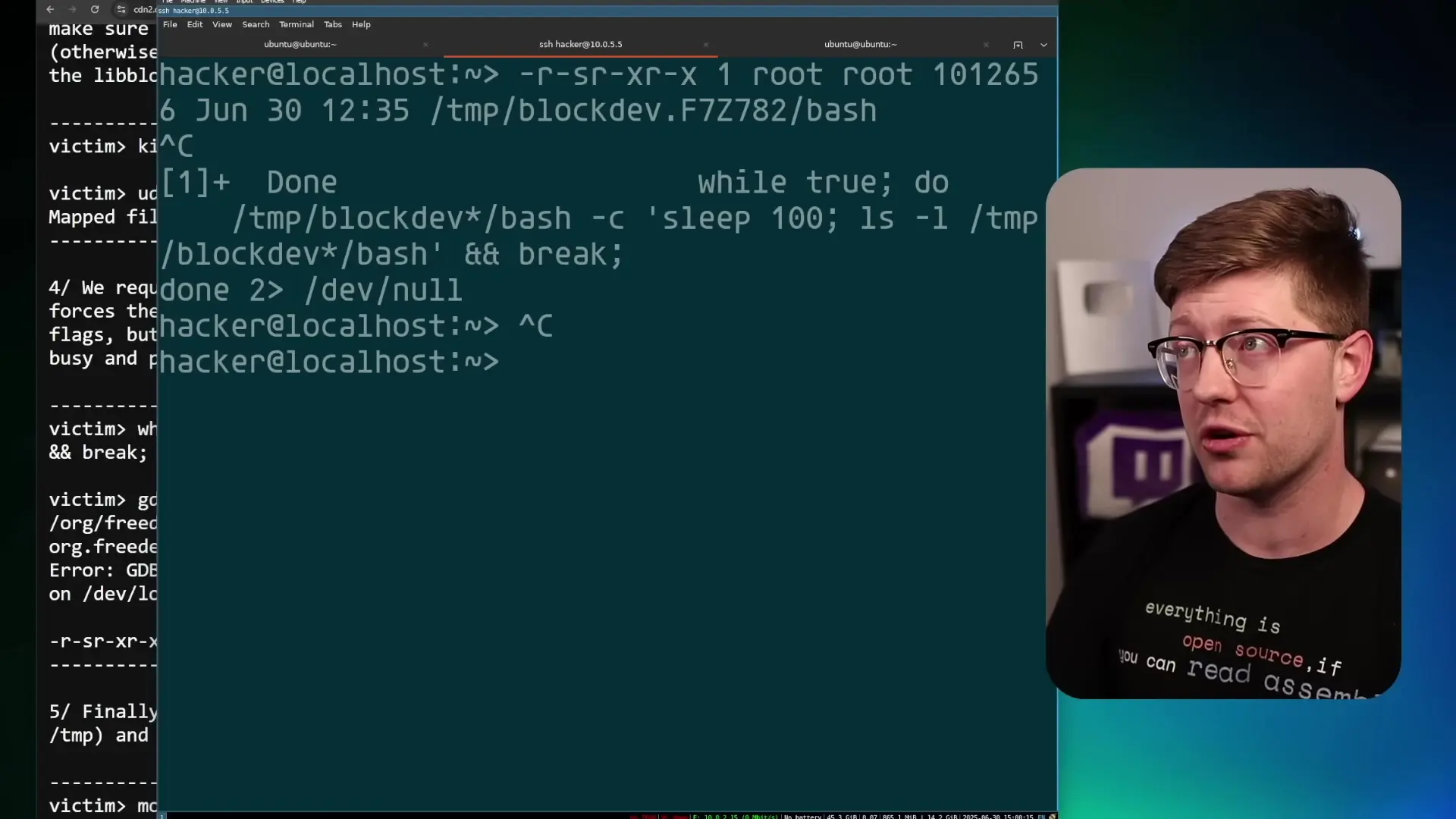
- Execute the setuid bash binary from the mounted file system, gaining root privileges
# Creating a malicious XFS image
mkfs.xfs -f image.xfs
# Mounting the image
mount image.xfs /mnt/tmp
# Keeping the file system busy
while true; do cat /mnt/tmp/file > /dev/null; done &
# Triggering resize operation
xfs_growfs /mnt/tmp
# Executing setuid bash to gain root
/mnt/tmp/bash -pWhy These Vulnerabilities Are Particularly Dangerous
- They don't rely on memory corruption, making them more reliable to exploit
- They exploit logical flaws in system design rather than implementation errors
- The exploits require minimal technical skills to execute
- They can be chained together for a complete privilege escalation attack
- The vulnerabilities affect widely used components (PAM and lib-blockdev)
Mitigation and Protection Measures
To protect your Linux systems from these and similar vulnerabilities, system administrators should implement the following security measures:
- Keep all system packages updated, especially security-related components like PAM and lib-blockdev
- Apply the latest security patches from your distribution's repositories
- Implement the principle of least privilege for all user accounts
- Monitor system logs for suspicious activities, especially related to mounting operations
- Use intrusion detection systems to identify potential exploitation attempts
- Consider implementing mandatory access control systems like SELinux or AppArmor
For Open SUSE users, updating the PAM implementation is critical. For all Linux distributions using lib-blockdev, ensure you're running the latest patched version to prevent the file system mounting vulnerability.
Understanding the Broader Implications
These vulnerabilities highlight a critical aspect of system security: even without memory corruption or complex exploitation techniques, logical flaws in system design can lead to complete system compromise. The PAM environment variable issue demonstrates how security systems can be undermined when they trust user-controllable data without proper validation.
Similarly, the file system mounting vulnerability shows how temporary conditions during system operations can create security windows that attackers can exploit. Both vulnerabilities remind us that security is not just about preventing buffer overflows or injection attacks, but also about ensuring logical consistency in system operations.
Conclusion
The Linux privilege escalation vulnerabilities discussed here demonstrate that security threats continue to evolve in sophistication and approach. By understanding how these vulnerabilities work, system administrators can better protect their systems and develop more robust security practices.
Remember that system security is an ongoing process, not a one-time task. Regular updates, proper configuration, and continuous monitoring are essential components of a comprehensive security strategy. By staying informed about the latest vulnerabilities and their exploitation techniques, you can better defend your Linux systems against unauthorized privilege escalation attempts.
Let's Watch!
2 Dangerous Linux Privilege Escalation Bugs Explained for System Admins
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence