
In the world of containerization and cloud computing, isolation between workloads is a fundamental security principle. When this isolation breaks down, the consequences can be severe. Recently, a critical vulnerability dubbed 'NvidiaCape' was discovered in Nvidia's container toolkit that completely breaks container isolation - representing one of the most significant software deployment failures in recent cloud security history.
Understanding the NvidiaCape Vulnerability
The NvidiaCape vulnerability affects the Nvidia container toolkit, an add-on to Docker that allows containers to access GPU resources. This toolkit is widely used in cloud environments where service providers need to give customers access to GPU resources for AI and machine learning workloads while maintaining isolation between different customers' environments.
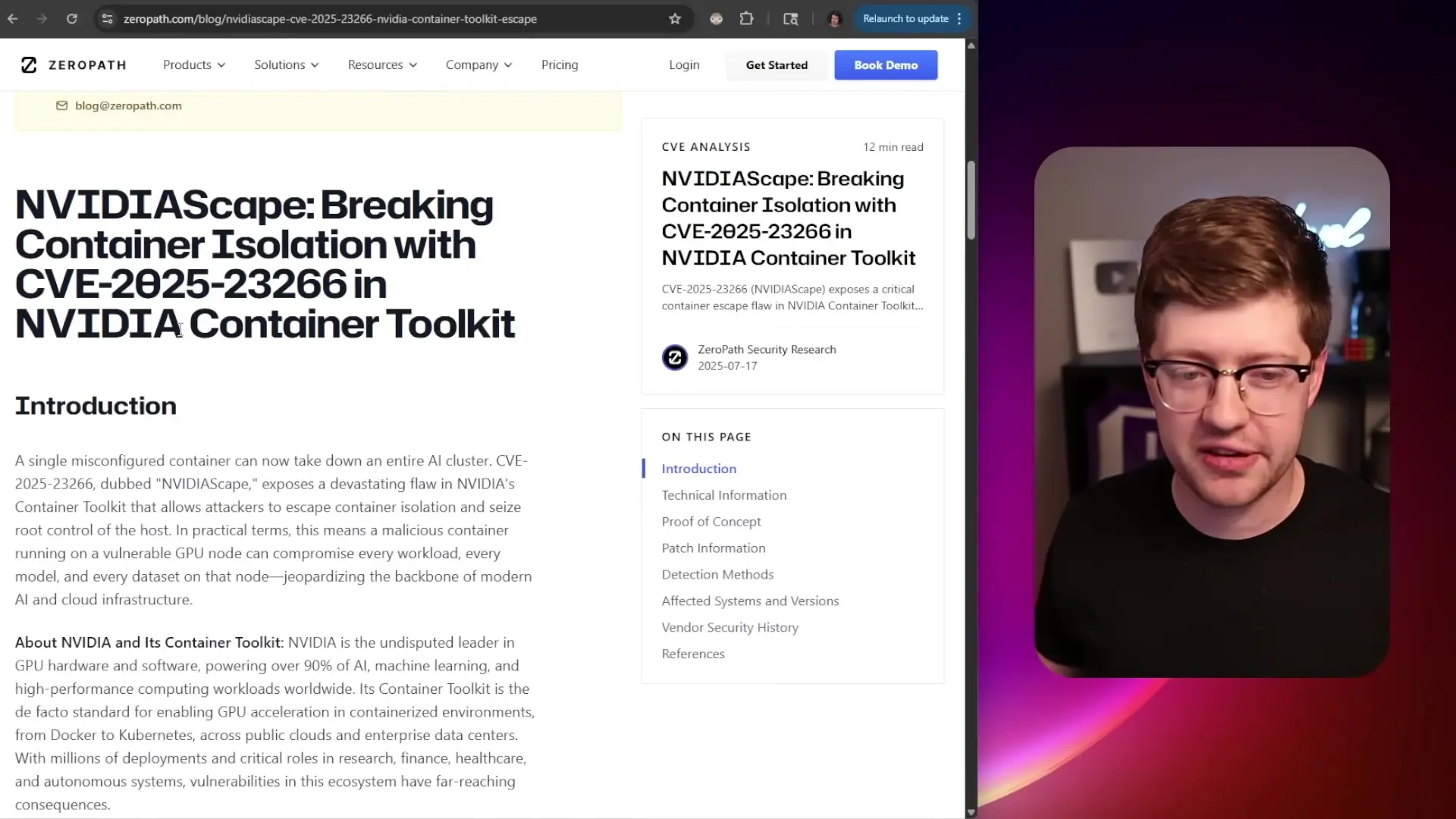
At its core, the vulnerability is surprisingly simple yet devastating: the Nvidia container toolkit blindly trusts environment variables from container images, including the dangerous LD_PRELOAD variable.
The Technical Details: How LD_PRELOAD Creates a Security Nightmare
To understand why this vulnerability is so serious, we need to examine how LD_PRELOAD works in Linux systems. The LD_PRELOAD environment variable is a powerful feature of the Linux dynamic linker (ld.so) that allows users to specify shared libraries to be loaded before all others when a program runs.
This capability is typically used for legitimate purposes like instrumentation, debugging, or function interception. However, when abused, it can allow attackers to inject malicious code into processes by replacing standard library functions with their own versions.
# Example of how LD_PRELOAD can be used to inject code
LD_PRELOAD=./evil_library.so ./target_applicationIn secure systems, privileged processes should never trust environment variables from less privileged contexts. For example, the 'sudo' command explicitly clears potentially dangerous environment variables to prevent this exact type of attack. Unfortunately, the Nvidia container toolkit failed to implement this basic security practice.
The Real-World Impact: Container Escape and Tenant Isolation Failure
In cloud environments, multiple customers (tenants) often share the same physical infrastructure. Container technology helps maintain isolation between these tenants, ensuring one customer cannot access another's data or processes.
The NvidiaCape vulnerability completely undermines this isolation. Here's how an attack might unfold in a real-world scenario:
- An attacker creates a container image with a malicious LD_PRELOAD setting pointing to their custom shared library
- When deployed on a cloud service provider's infrastructure using the Nvidia container toolkit, this environment variable is blindly trusted
- The attacker's code is loaded and executed in the context of the host OS, not just within the container
- The attacker now has access to the host system and potentially to other customers' containers running on the same host
A Simple Example of LD_PRELOAD Exploitation
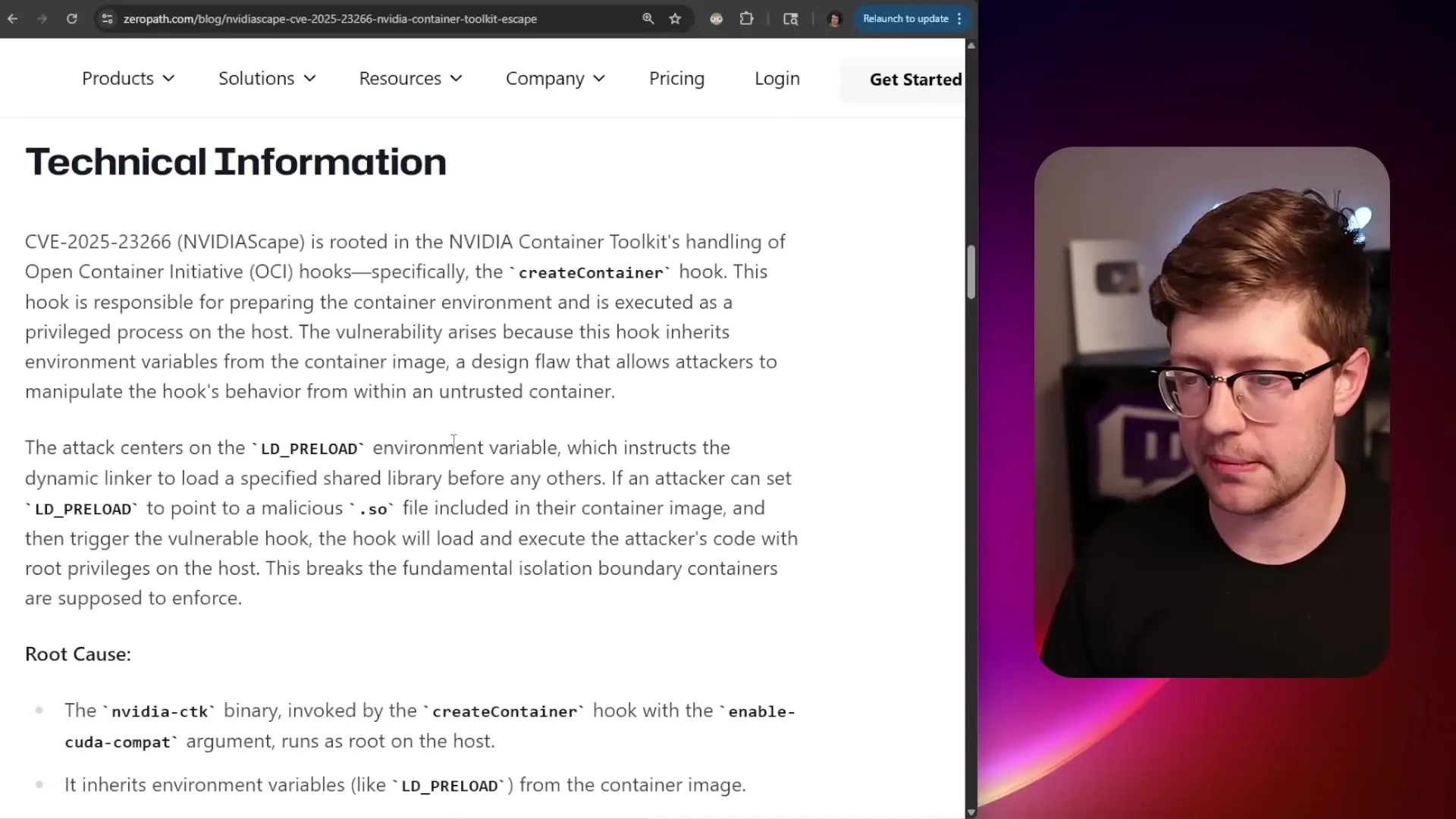
To demonstrate how LD_PRELOAD can be exploited, consider this simplified example. First, imagine a program that simply reads a password from a user:
// victim.c
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
int main() {
char *password = getpass("Enter password: ");
printf("You entered: %s\n", password);
return 0;
}Now, an attacker can create a malicious shared library that intercepts the getpass() function:
// evil_preload.c
#define _GNU_SOURCE
#include <stdio.h>
#include <dlfcn.h>
char *getpass(const char *prompt) {
// Find the real getpass function
char *(*real_getpass)(const char *) = dlsym(RTLD_NEXT, "getpass");
// Call the real function to maintain normal behavior
char *result = real_getpass(prompt);
// Malicious action: log the password
FILE *f = fopen("/tmp/stolen_passwords", "a");
if (f) {
fprintf(f, "%s\n", result);
fclose(f);
}
return result;
}When this library is loaded via LD_PRELOAD, it intercepts all calls to getpass(), executes the original function, but also secretly logs the password. In the context of the Nvidia container toolkit vulnerability, similar techniques could be used to escape the container and execute code on the host system.
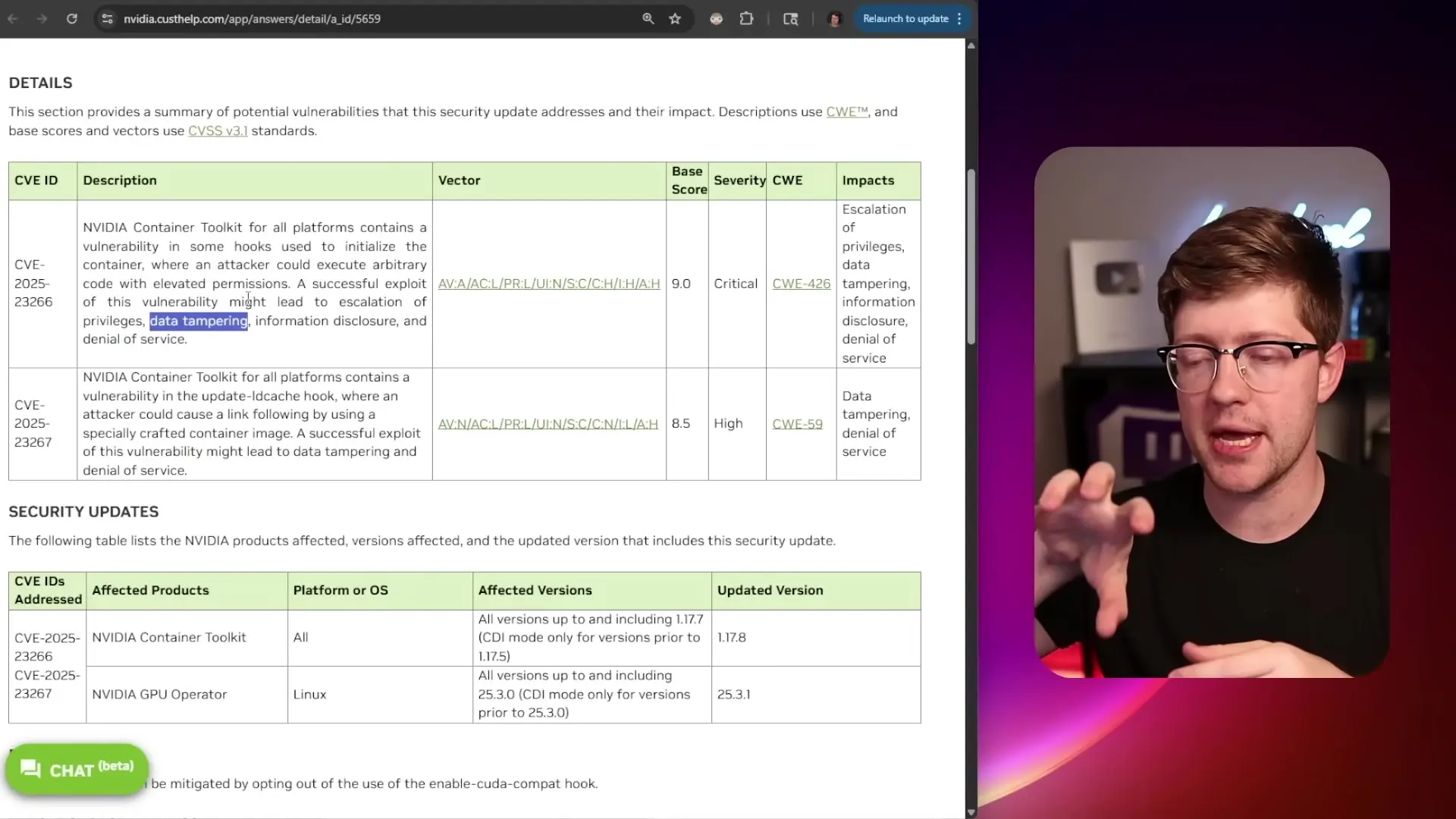
Not Nvidia's First Container Security Issue
Unfortunately, this isn't Nvidia's first significant container security issue. Last year, they addressed another vulnerability in the same container toolkit - a time-of-check-time-of-use (TOCTOU) vulnerability that allowed attackers to put malicious files into container images after security checks were performed.
This pattern of software deployment failures in security-critical components raises serious concerns about Nvidia's security practices, especially as their GPU technologies become increasingly central to cloud computing and AI workloads.
Mitigation and Best Practices for DevOps Teams
If you're using the Nvidia container toolkit in your environment, here are some essential steps to mitigate this and similar vulnerabilities:
- Update to the latest version of the Nvidia container toolkit immediately
- Implement additional container security measures such as seccomp profiles, AppArmor, or SELinux policies
- Consider using container-specific security scanning tools to identify potential vulnerabilities
- Implement the principle of least privilege for all container workloads
- Consider using a runtime security solution that can detect and prevent container escape attempts
- Regularly audit your container configurations and images for security issues
The Broader Implications for Cloud Security
The NvidiaCape vulnerability highlights a critical aspect of modern cloud security: as computing moves increasingly to shared infrastructure, the security boundaries between tenants become crucial attack surfaces. Traditional security models focused primarily on preventing remote code execution, but in cloud environments, the threat model expands to include tenant isolation failures.
Cloud service providers must carefully evaluate the security of all components in their stack, especially those that bridge the gap between hardware resources (like GPUs) and customer workloads. The failure of any component in this chain can lead to catastrophic software deployment issues affecting multiple customers.
Conclusion
The NvidiaCape vulnerability serves as a stark reminder that even the most basic security principles can be overlooked in complex systems. The failure to properly validate environment variables - a security practice that has been standard for decades - led to a complete breakdown of container isolation in a widely-used toolkit.
As organizations continue to embrace containerization and cloud-native development, security must remain a primary concern throughout the software development lifecycle. Regular security audits, adherence to secure coding practices, and a defense-in-depth approach are essential to preventing similar software deployment failures in the future.
Let's Watch!
Nvidia's Critical Container Isolation Bug: What DevOps Teams Need to Know
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence