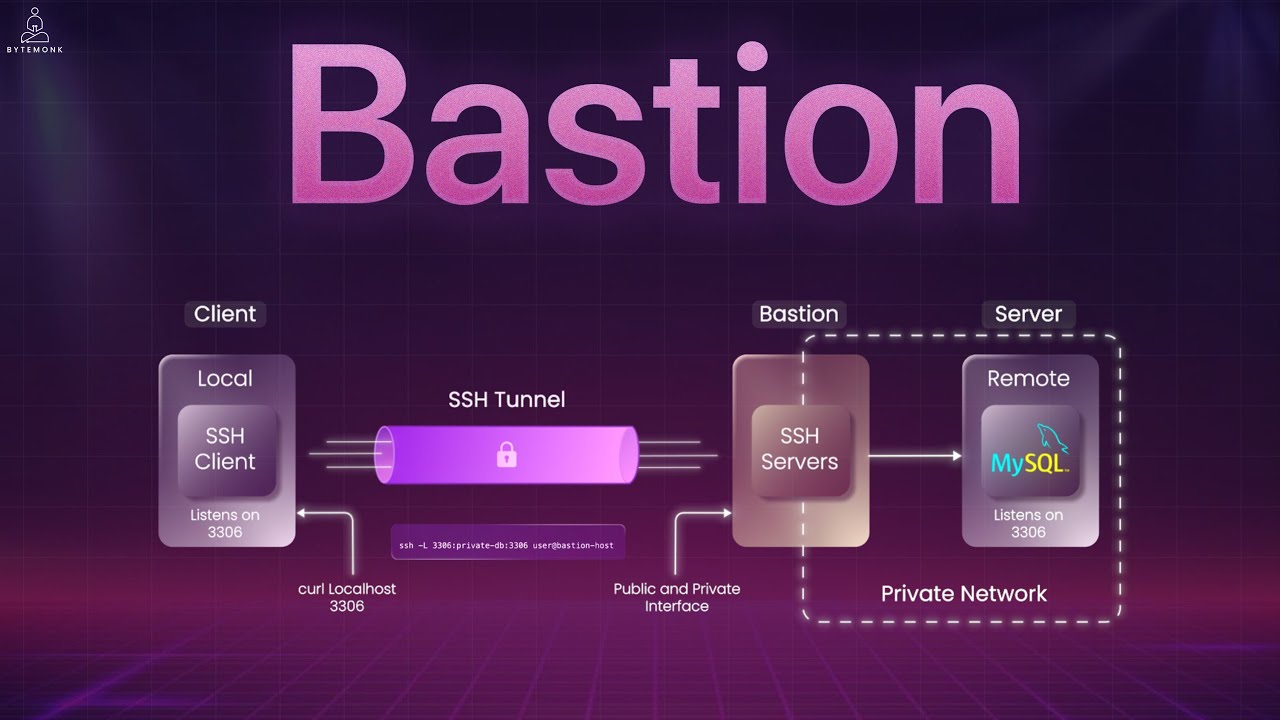
In modern infrastructure environments, sensitive resources like production databases, application servers, and internal dashboards are intentionally isolated within private networks. This isolation is a fundamental security practice that reduces the attack surface and prevents unauthorized access. However, this creates a challenge: how do engineers access these systems for legitimate purposes like deployments, troubleshooting, and maintenance when these resources have no public IP addresses and sit behind strict firewalls?
The Challenge of Secure Access to Private Networks
Private networks are designed to be invisible to the public internet. The machines within these networks don't have public IP addresses, can't be reached directly over the internet, and are protected by strict firewall rules and security groups. While this isolation is excellent for security, it creates a practical problem for engineers who need legitimate access to these systems.
One traditional solution is to set up a Virtual Private Network (VPN) that connects an engineer's laptop directly to the private network. While VPNs work in some scenarios, they often present several drawbacks:
- VPNs typically provide broad network access once connected, violating the principle of least privilege
- They can be slower to provision for new team members
- Session activity is harder to audit at a granular level
- They offer less control over which specific internal resources a user can access
What is a Bastion Host? The Secure Gateway Solution
A bastion host (also called a jump host or jump box) solves the secure access problem differently. Instead of providing blanket connection to an entire network, it acts as a single, tightly controlled entry point. Engineers connect to the bastion host first, and from there, they can reach only the specific resources they're authorized to access.
This approach keeps the private network invisible to the outside world while still allowing secure, auditable access for authorized personnel.
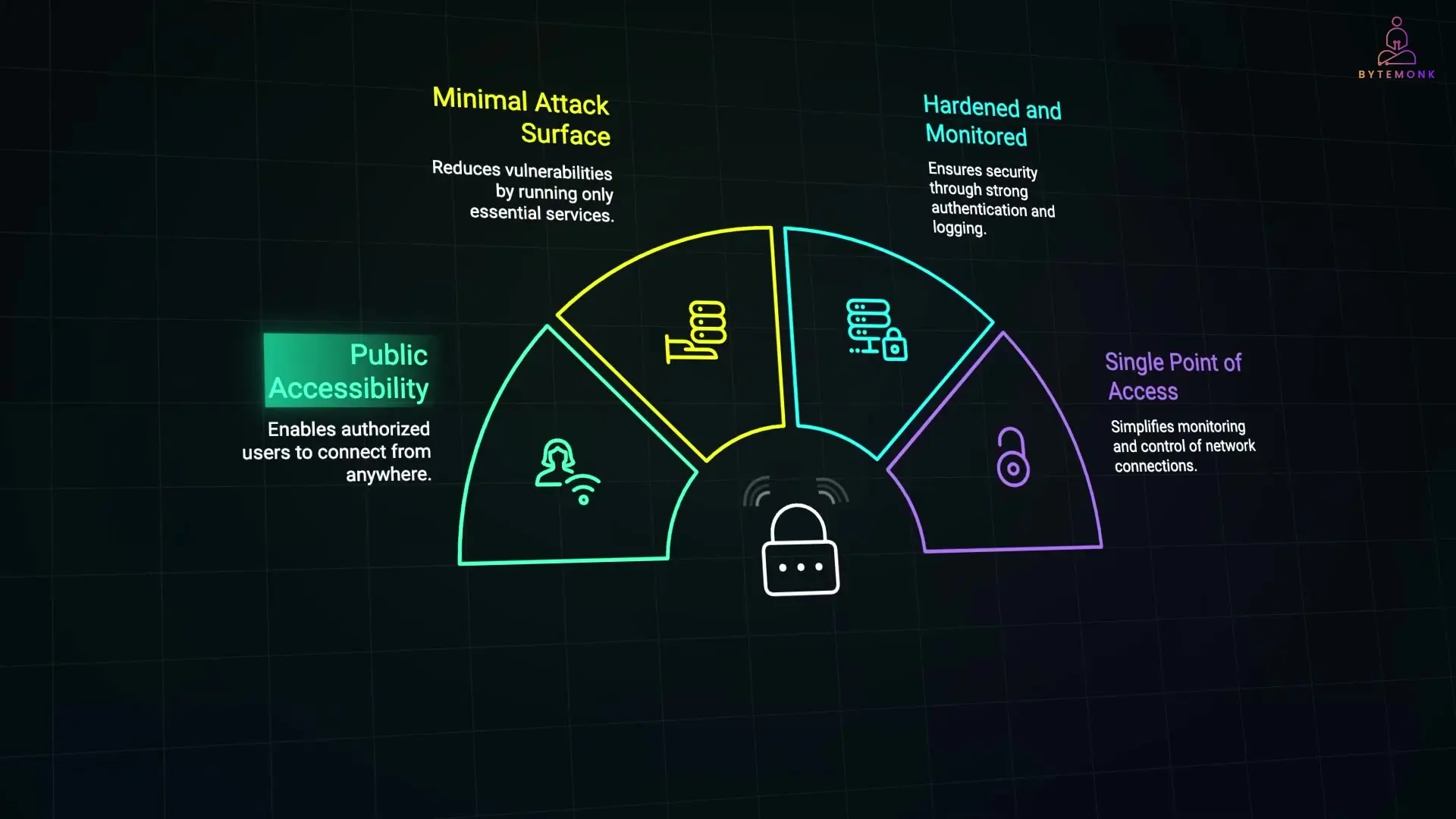
Key Characteristics of a Bastion Host
What makes a bastion host different from a normal server is its specialized role and configuration:
- It has a public IP address so authorized users can connect to it from anywhere
- It runs only the essential services required for remote access (most commonly SSH for Linux or RDP for Windows)
- It implements strong authentication, often including multi-factor authentication (MFA)
- It maintains detailed logging of every session for security auditing
- It enforces strict firewall rules controlling what systems it can communicate with
- All administrative connections to the private network flow through this single point, making monitoring and access control more manageable
How Bastion Hosts Work: Connection Patterns
When you connect to a bastion host, it's just the first hop in your journey. From there, you establish connections to the actual target systems within the private network. There are several common connection patterns used with bastion hosts.
SSH Jump
The SSH jump approach allows you to connect to a target machine through the bastion host in a single command, avoiding the need for multiple SSH steps. In OpenSSH, this is implemented using the -J (ProxyJump) flag.
ssh -J user@bastion-host user@private-webserverThis command tells SSH to automatically hop through the bastion host before connecting to the final destination. It's cleaner, faster, and more convenient than manually establishing multiple SSH connections.
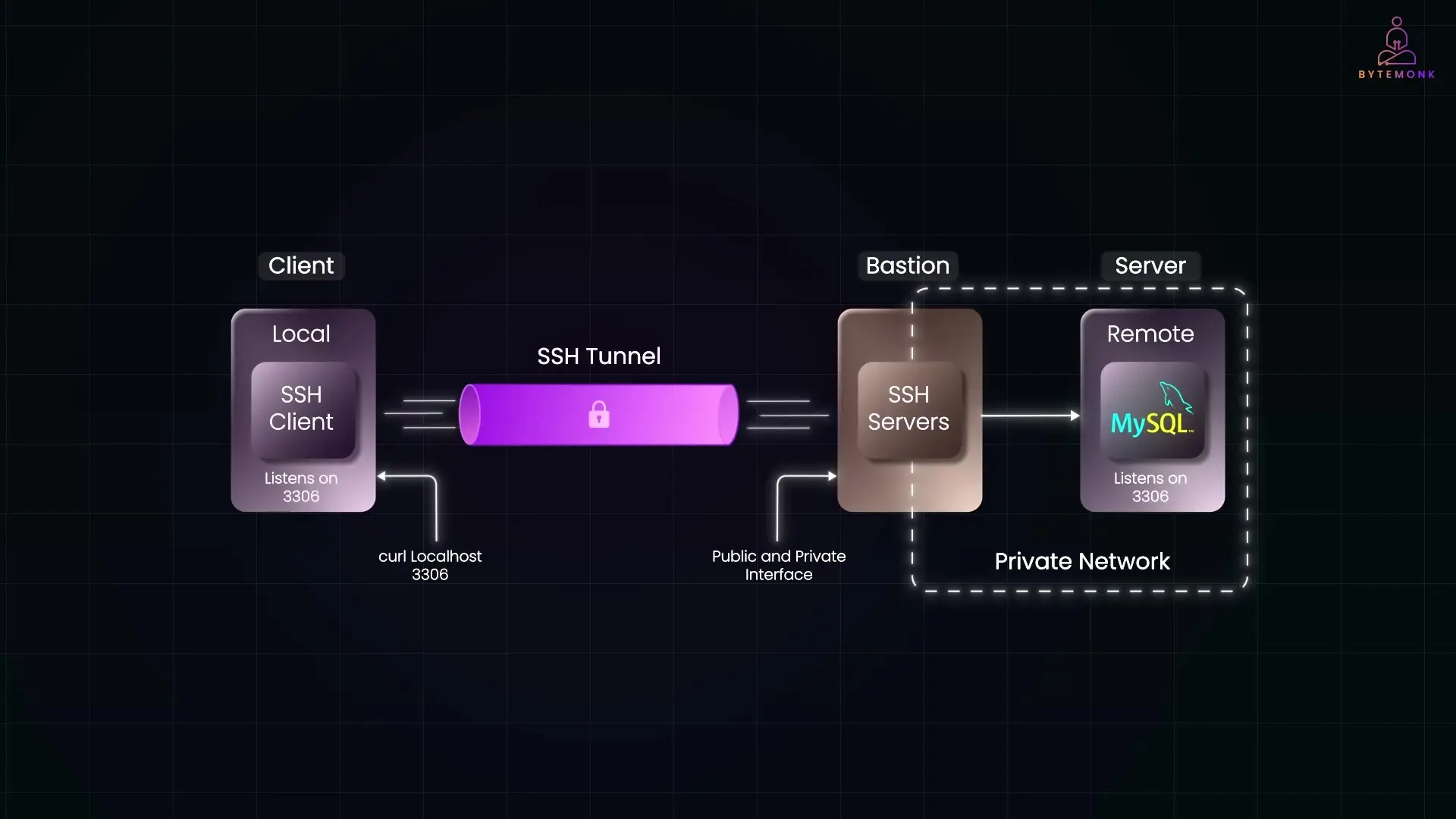
Local Port Forwarding
Local port forwarding is ideal when you want to use local applications (like database clients or web browsers) to connect to services in the private network without installing those applications on the bastion host.
ssh -L 3306:private-db:3306 user@bastion-hostThis command creates a tunnel that forwards traffic from your local machine's port 3306 to the database server's port 3306 via the bastion host. When you connect to localhost:3306 on your laptop, you're actually communicating with the private database server through the secure SSH tunnel.
Multi-Hop Bastion Chains
In large enterprise or highly sensitive environments, networks are often segmented into multiple security layers. This might require traversing multiple bastion hosts before reaching your target system.
ssh -J user@bastion1,user@bastion2 user@private-serverThis command chains multiple jumps together, automatically hopping through bastion1 and bastion2 before connecting to the final private server—all in a single command.
Real-World Implementation: Netflix's Bastion Host Security
Netflix provides an excellent case study of bastion host implementation at enterprise scale. The streaming giant runs thousands of microservices and data stores inside private AWS VPCs, none of which are exposed to the public internet—not even for employees.
Instead, Netflix uses a hardened bastion host layer integrated with their internal identity platform. Here's how their approach works:
- Engineers must pass through Okta MFA before even starting an SSH session to the bastion host
- Once connected to the bastion, engineers can only reach systems related to their specific role (enforced by AWS security groups and IAM policies)
- Every command executed through the bastion is logged, and session activity can be replayed during security investigations if needed
- Access to the bastion is time-bound, with sessions automatically expiring to reduce risk if an engineer's machine is compromised
Netflix values this approach because it maintains tight security controls with a single internet-facing entry point, ensures engineers only see what they're authorized to access, and centralizes all administrative access for easier monitoring and incident response.
Bastion Host Alternatives and When to Use Them
While bastion hosts are powerful security tools, they're not always the optimal solution for every scenario. Several alternative approaches have emerged:
- AWS Systems Manager Session Manager - Allows connections to private instances directly from browsers or CLI without requiring public IPs
- Google Cloud Identity-Aware Proxy (IAP) - Adds identity verification before granting access to applications or SSH sessions
- Zero Trust platforms like Teleport or StrongDM - Designed to replace traditional bastions with more modern identity-based access controls
- VPN solutions with granular access controls, strong logging, and MFA
These alternatives authenticate users based on identity rather than network location, often removing the need for a public jump box entirely. For CI/CD pipelines or automated scripts connecting to private resources, direct VPC peering or service endpoints are frequently used instead of routing through bastion hosts.
Bastion Host Security Best Practices
If you're implementing bastion hosts in your infrastructure, follow these security best practices:
- Implement strong authentication with public key authentication and multi-factor authentication
- Maintain detailed logging of all session activity for audit purposes
- Configure strict firewall rules to limit which private resources the bastion can access
- Keep the bastion host minimally configured with only essential services
- Implement automatic session timeouts to limit the risk of compromised connections
- Regularly update and patch the bastion host to address security vulnerabilities
- Use IAM roles or similar access control mechanisms to enforce least privilege principles
- Consider implementing just-in-time access where bastion access is granted only when needed and automatically revoked afterward
Conclusion: The Strategic Value of Bastion Hosts
Bastion hosts are more than just another server in your infrastructure—they're a strategic security component that acts as a secure front door to your private resources. By providing a controlled, auditable entry point to sensitive systems, bastion hosts enable organizations to maintain robust security while still allowing engineers to perform necessary work.
Whether you're debugging a production database, deploying to internal servers, or managing cloud workloads, understanding bastion host architecture and implementation makes you a more effective and security-conscious engineer. As cloud infrastructures grow more complex, the principles behind bastion hosts—controlled access, least privilege, and detailed auditing—remain fundamental to modern security architecture.
Let's Watch!
What is a Bastion Host? Security Architecture Explained for DevOps
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence