
A significant security vulnerability has been discovered in Next.js, the popular React framework for building web applications with server-side rendering capabilities. This critical authorization bypass vulnerability in Next.js middleware (rated 9.1 in severity) allows attackers to completely bypass security checks by simply manipulating a request header. If you're using Next.js for your applications, this is something you need to address immediately.
Understanding the Next.js Middleware Vulnerability
Next.js is a powerful framework that enables developers to create applications with both frontend and server-side rendering capabilities. One of its key features is middleware - functions that inspect incoming requests to determine whether certain operations should proceed, often handling critical security checks like authentication and authorization.
The recently discovered vulnerability (CVE-2025-29927) allows attackers to completely bypass these middleware checks by adding a simple header to their requests: `X-Middleware-Subrequest: true`. When this header is present, the middleware security checks are skipped entirely, potentially giving unauthorized users access to protected routes and resources.

Why Does This Vulnerability Exist?
The root cause of this vulnerability lies in how Next.js handles internal subrequests. The `X-Middleware-Subrequest` header was originally designed to prevent infinite recursion when middleware functions make API calls to the same server. Without this mechanism, a middleware function calling an API endpoint on the same server would trigger the middleware again, potentially causing an infinite loop and CPU exhaustion.
To prevent this recursive loop, Next.js implemented a system where middleware functions add the `X-Middleware-Subrequest: true` header to internal API calls. When Next.js detects this header, it assumes the request is coming from another middleware function and skips further middleware processing.
The vulnerability arises because there was no verification that the request with this header actually originated from within the application. Any external attacker could simply add this header to their requests and trick Next.js into believing it was an internal subrequest, effectively bypassing all middleware security checks.
The Severity of the Vulnerability
This vulnerability is particularly concerning because of its simplicity and the widespread use of Next.js for building modern web applications. With just a single HTTP header modification, attackers can bypass authentication, authorization, and other security controls implemented in middleware.
# Example of exploiting the vulnerability with curl
curl -H "X-Middleware-Subrequest: true" https://vulnerable-nextjs-app.com/protected-routeFor applications that rely on middleware for implementing security controls, this vulnerability could lead to unauthorized access to sensitive data, administrative functions, or protected resources. The simplicity of the exploit makes it particularly dangerous, as it requires minimal technical knowledge to execute.
How the Vulnerability Was Fixed
The Next.js team has addressed this vulnerability by implementing a more secure approach to handling middleware subrequests. Instead of relying solely on the presence of a header that can be easily spoofed, they've introduced a secret subrequest ID system.
With this fix, each session now has a secret subrequest ID that is unknown to external users. When middleware makes an internal API call, it includes this secret ID in the request. The receiving middleware then verifies that the subrequest ID matches the expected value. If an attacker attempts to bypass middleware by adding the `X-Middleware-Subrequest` header, the request will be rejected because it won't contain the correct secret ID.
How to Protect Your Next.js Applications
If you're using Next.js in your applications, here are the steps you should take immediately to protect against this vulnerability:
- Update to the patched versions of Next.js: 13.5.3 or 14.4.2.5, which include the fix for this vulnerability.
- If you cannot update immediately, implement a temporary mitigation by adding code to your middleware that explicitly rejects requests containing the 'X-Middleware-Subrequest' header from external sources.
- Review your application's security architecture to ensure you're not solely relying on middleware for critical security controls.
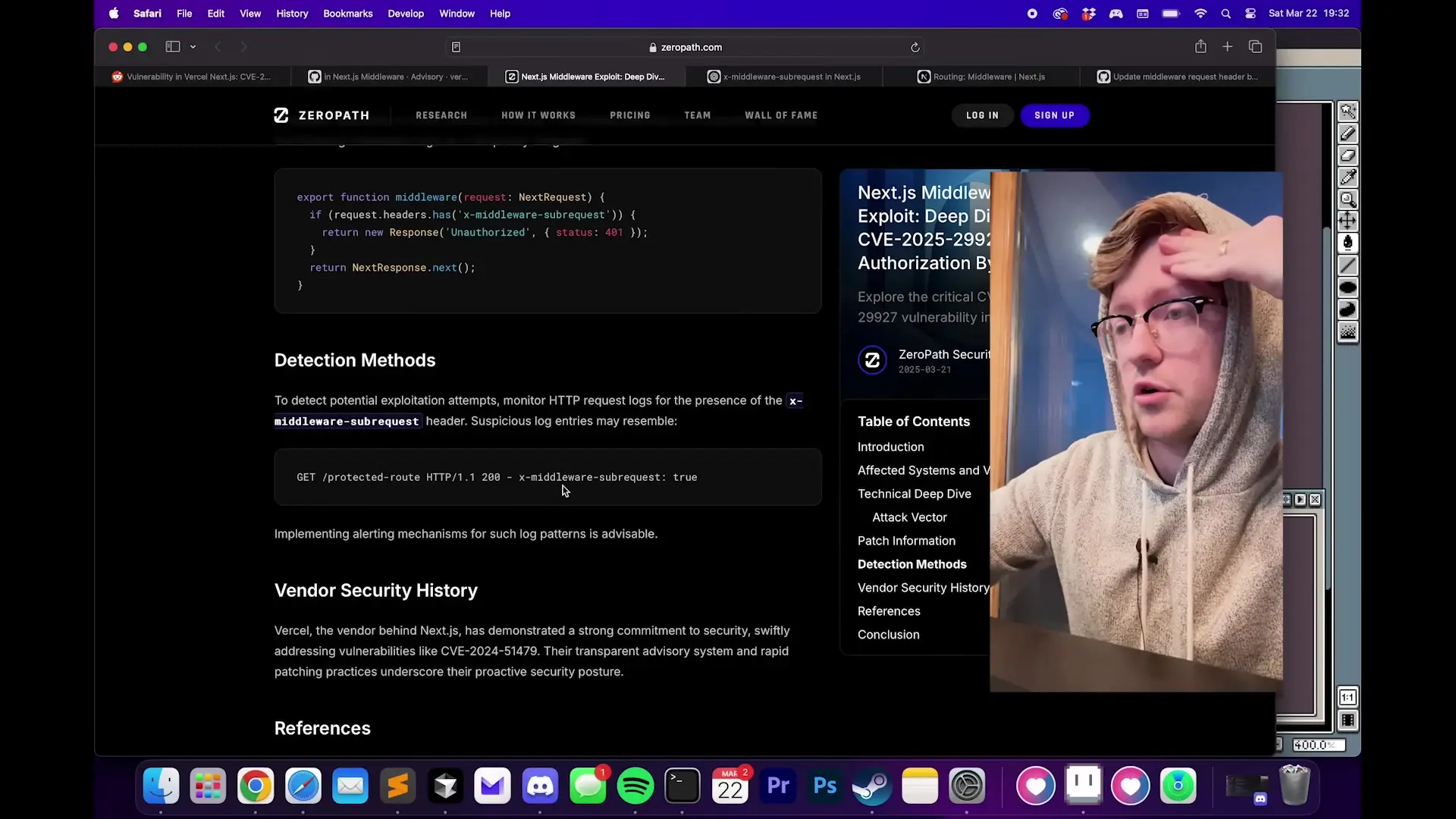
- Monitor your logs for suspicious requests that might indicate exploitation attempts.
// Example middleware fix if you cannot update Next.js
export function middleware(request) {
// Check for potentially malicious header
if (request.headers.get('x-middleware-subrequest') === 'true') {
// Drop potentially malicious requests
return new Response('Unauthorized', { status: 401 });
}
// Continue with normal middleware processing
// ...
}Lessons for Middleware Security
This vulnerability highlights several important security principles for developers working with middleware and web frameworks:
- Never trust client-provided headers for security decisions without proper verification
- Implement defense in depth by not relying solely on middleware for critical security controls
- Be cautious about special header flags that modify application behavior, especially those that bypass security checks
- Regularly update dependencies to ensure you have the latest security patches
Conclusion
The Next.js middleware vulnerability serves as a reminder of how seemingly small implementation details can lead to significant security risks. By understanding how this vulnerability works and taking appropriate mitigation steps, you can protect your applications from potential exploitation.
This incident also emphasizes the importance of security awareness in the development process and the need for regular security audits and updates to web frameworks and libraries. As web applications become increasingly complex, vigilance in addressing security vulnerabilities becomes ever more critical.
If you're using Next.js in production environments, prioritize updating to the fixed versions and review your application's security architecture to ensure you're protected against this and similar vulnerabilities.
Let's Watch!
Critical Next.js Middleware Vulnerability: How to Protect Your Web Applications
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence