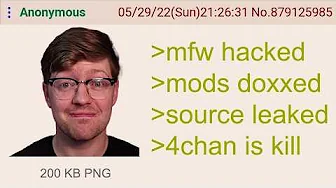
The recent security breach at 4chan serves as a stark reminder of the critical importance of maintaining updated code and following modern security practices. This major breach resulted in the site's source code being leaked and moderator identities being exposed, creating significant privacy and safety concerns. By examining what happened and how the attack was executed, we can extract valuable lessons about security vulnerabilities in legacy systems.
The Breach: What Happened and What Was Exposed
The 4chan breach began with the site going offline for over 24 hours. When it returned, hackers had gained access to the system and made unauthorized changes, including reactivating a previously deleted board called "QA" (Question and Answer). This attack appears to have been motivated by community frustration over the deletion of this popular board.
The breach resulted in several critical exposures:
- The complete source code of the website
- Email addresses of administrators and moderators (including some .edu and .gov domains)
- User IP information and potentially identifying data
- Internal site architecture and security mechanisms
Technical Analysis: How Outdated Code Created Vulnerabilities
Examining the leaked source code reveals several critical security issues that likely contributed to the breach. The 4chan architecture represents what could be called "OG internet" - a PHP backend rendering HTML to the frontend, which was standard practice in the early days of web development but lacks many modern security features.
1. Outdated PHP and Deprecated Functions
One of the most significant issues was the use of severely outdated PHP code. The codebase relied on functions that had been deprecated for nearly a decade, including the notorious MySQL_real_escape_string() function. This function was deprecated in PHP 5.5.0 (2013) and completely removed in PHP 7.0.0, yet it was still being used as a core security function in the 4chan codebase.
// Example of problematic code similar to what was found
function try_escape_string($string) {
return mysql_real_escape_string($string); // Deprecated since 2013
}
// Used in queries like this
$query = "SELECT o_secret FROM mod_users WHERE username = '" . try_escape_string($username) . "'";The problem with mysql_real_escape_string() is that while it works reasonably well for ASCII character sets, it has known vulnerabilities when dealing with non-ASCII characters. Attackers could potentially use characters from other languages to bypass the escaping mechanism and inject malicious SQL code.
2. Unrotated Encryption Keys
Another alarming discovery in the code was evidence suggesting encryption keys had not been rotated for approximately 10 years. Security best practices dictate that encryption keys should be regularly rotated to limit the damage potential if they're compromised.
// Example of problematic key management found in the code
$encryption_key = file_get_contents("www/keys/2015/encryption_key");3. Questionable Third-Party Dependencies
The codebase also relied on potentially unmaintained third-party libraries. For example, the two-factor authentication implementation used a Google Authenticator package maintained by a developer whose own website returned a 500 internal server error when checked, suggesting abandoned or poorly maintained code.
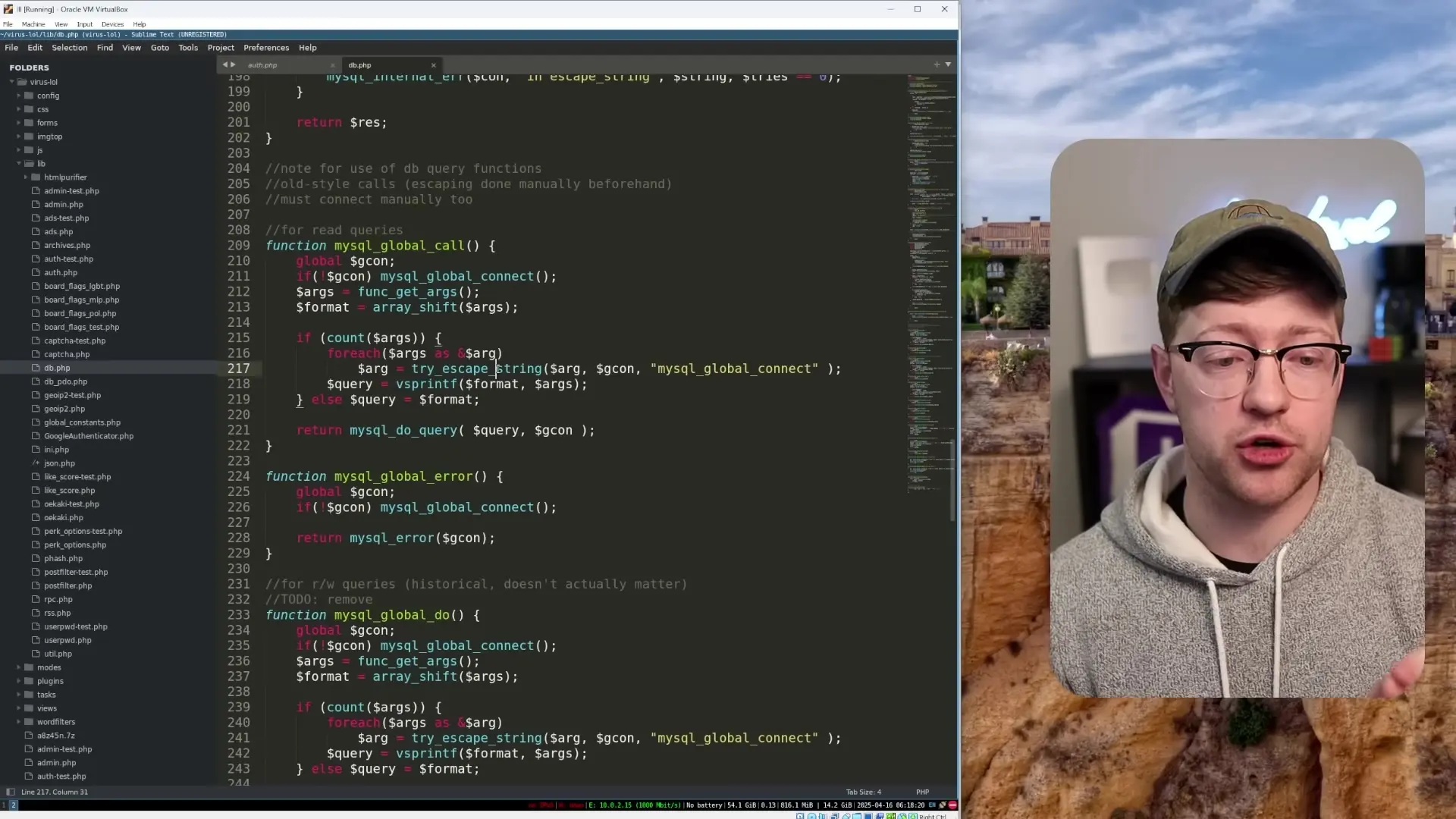
The Likely Attack Vector: SQL Injection
Based on the code analysis, the most probable attack vector was SQL injection - one of the most common vulnerabilities in web applications. The site's custom MySQL global call function attempted to sanitize user input, but relied on the deprecated mysql_real_escape_string() function.
SQL injection allows attackers to insert malicious SQL code into queries, potentially enabling them to:
- Extract sensitive data from databases
- Add unauthorized admin users
- Modify database content
- Execute administrative operations on the database
- In some cases, issue commands to the operating system
The vulnerability was likely exploited using non-ASCII character sets to bypass the escaping mechanism, a technique that's well-documented for bypassing this particular deprecated function.
Security Implications and Consequences
The breach has several serious implications, particularly for the site's moderators. 4chan users are notorious for their ability to track down individuals based on minimal information - as demonstrated by past incidents where they located objects using only sky patterns or other minimal visual cues.
With moderator email addresses exposed (including some from educational and government domains), these individuals face potential harassment or doxxing. Additionally, the exposure of user IP information raises privacy concerns, especially for users who may have posted sensitive or controversial content.
The incident has also fueled conspiracy theories about government involvement with the site, due to the presence of .gov email addresses among the moderators.
Key Security Lessons for Developers
This breach offers several valuable lessons for developers and organizations maintaining web applications:
- Regularly update programming languages and frameworks to maintain security patches
- Replace deprecated functions with modern, secure alternatives (use prepared statements instead of string escaping for SQL)
- Implement a key rotation policy for all encryption and authentication mechanisms
- Carefully vet and regularly review third-party dependencies
- Conduct regular security audits, especially for legacy systems
- Implement proper input validation and sanitization at multiple levels
- Use parameterized queries or ORM frameworks to prevent SQL injection
Modern Alternatives to Legacy Practices
For developers working with SQL databases, modern security practices recommend using prepared statements or parameterized queries instead of string escaping:
// Modern approach using prepared statements
$stmt = $pdo->prepare("SELECT o_secret FROM mod_users WHERE username = ?");
$stmt->execute([$username]);
$result = $stmt->fetch();Additionally, modern web applications often use frameworks that handle security concerns automatically, implementing best practices by default and reducing the risk of developer error.
Conclusion: The High Cost of Technical Debt
The 4chan breach demonstrates the real-world consequences of technical debt and neglected security practices. While maintaining legacy systems can be challenging, this incident shows that the cost of not upgrading can be far greater than the investment required to keep systems current and secure.
For organizations running legacy applications, this breach serves as a powerful reminder to prioritize security updates, conduct regular code audits, and implement modern security practices - even when working with older codebases. The alternative could be a catastrophic breach with lasting consequences for both the organization and its users.
Let's Watch!
The 4chan Security Breach Anatomy: Critical Lessons in Code Security
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence