
A new critical vulnerability discovered in Apple's AirPlay protocol is being described as potentially the biggest bug of 2025. This isn't hyperbole—the flaw affects millions of Apple devices and third-party products that implement the AirPlay SDK, creating a widespread security crisis that security professionals are racing to address.
What Makes This Vulnerability So Dangerous?
The security research team at Oolgo Security Research has identified over 20 bugs in the Apple AirPlay Protocol, with the most severe being a zero-click remote code execution (RCE) vulnerability. What makes this particularly alarming is the "zero-click" nature—attackers can execute malicious code on your device without requiring any user interaction whatsoever.
The primary vulnerability (CVE-2025-24252) affects macOS and involves a "use after free" memory safety issue. A second critical vulnerability affects the AirPlay SDK itself, which is used by countless third-party manufacturers in speakers, receivers, and other AirPlay-compatible devices.
Understanding the Technical Details: Use After Free Vulnerability
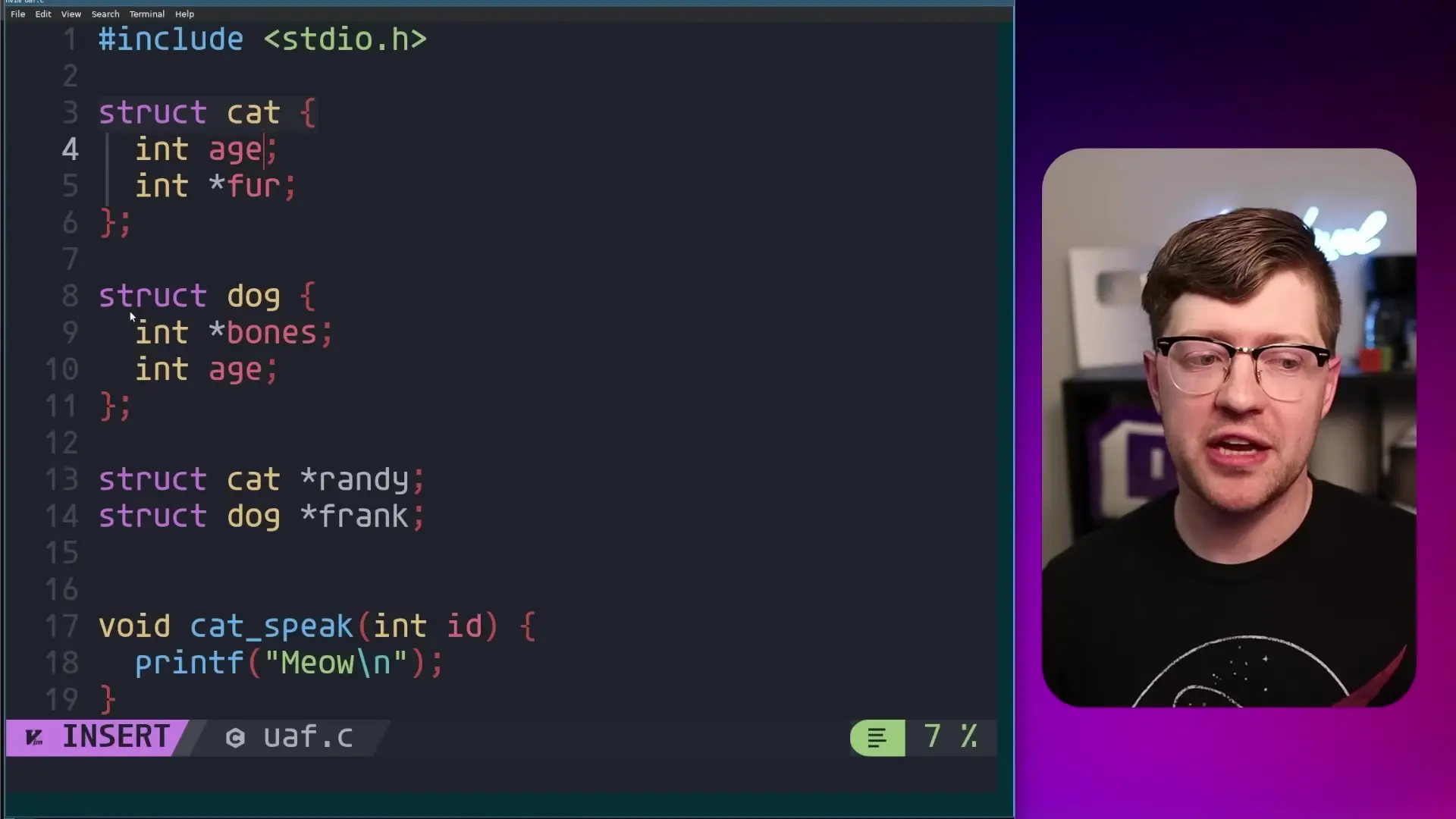
The macOS vulnerability (CVE-2025-24252) is a use-after-free bug, a memory safety issue that occurs when a program continues to use memory after it has been freed (returned to the system). This creates a dangerous scenario where the same memory location can be treated as two different types of data structures—a condition known as "type confusion."
This type confusion leads to what security experts call a "write what where" primitive—essentially giving attackers the ability to write arbitrary data to any location in the process's memory. With this capability, attackers can overwrite critical memory structures like virtual function tables or global offset tables, redirecting program execution to their malicious code.
// Simplified example of type confusion vulnerability
struct Cat {
int age; // 4 bytes
char* name; // 8 bytes (on 64-bit systems)
};
struct Dog {
char* name; // 8 bytes (on 64-bit systems)
int* bones; // 8 bytes (on 64-bit systems)
};
// If we can trick the program into treating a Cat as a Dog:
// Setting cat.age can overwrite dog.bones pointerThe AirPlay SDK Vulnerability: Stack-Based Buffer Overflow
The second major vulnerability affects the AirPlay SDK, which is used by third-party manufacturers to implement AirPlay compatibility in their devices. This is a stack-based buffer overflow—one of the most fundamental and dangerous types of memory corruption bugs. Security researchers demonstrated a successful attack against a smart speaker, gaining complete root access to the device.
What's particularly concerning is that this vulnerability affects any device implementing the AirPlay SDK. This means potentially millions of speakers, receivers, smart TVs, and other IoT devices are vulnerable, many of which may never receive security updates.
The Wormable Threat: Network-Wide Compromise
Perhaps the most alarming aspect of these vulnerabilities is that they are "wormable"—meaning an infected device can automatically spread the exploit to other vulnerable devices on the same network. This creates a scenario similar to biological viruses:
- An attacker compromises one device on a network (like an iPhone)
- The compromised device spreads the exploit to other vulnerable devices on that network
- When those devices connect to new networks, they continue spreading the exploit
- The infection can spread exponentially across networks and devices
This wormable nature makes the vulnerability especially dangerous in public spaces like coffee shops, airports, or offices where many Apple devices connect to shared networks.
How to Protect Your Devices
Given the severity of these vulnerabilities, immediate action is recommended to protect your devices:
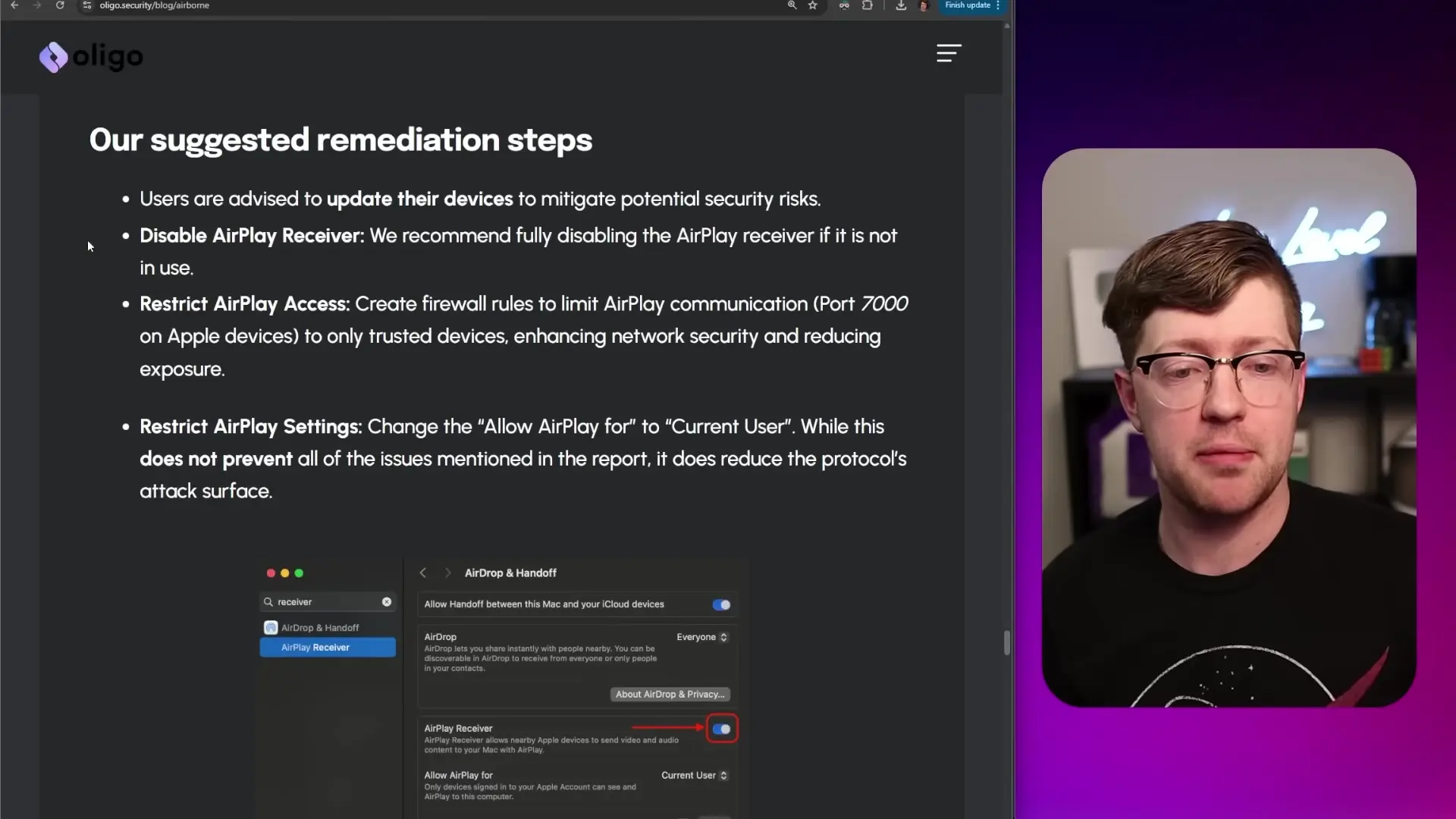
- Update all Apple devices immediately with the latest security patches
- Disable AirPlay receiver functionality if you're not actively using it
- Monitor for network traffic on TCP port 7000 (the AirPlay port)
- Check manufacturer websites for firmware updates for AirPlay-compatible speakers, TVs, and receivers
- Consider using network segmentation to isolate potentially vulnerable IoT devices
Could Modern Programming Languages Have Prevented This?
An interesting aspect of these vulnerabilities is that they represent exactly the types of memory safety issues that modern programming languages like Rust are designed to prevent. Both use-after-free and buffer overflow vulnerabilities are fundamentally memory safety problems:
- Use-after-free is a temporal memory safety violation (using memory at the wrong time)
- Buffer overflow is a spatial memory safety violation (accessing memory outside intended boundaries)
Rust's ownership model and borrow checker would have prevented both of these vulnerabilities at compile time, making this class of bugs impossible in properly written Rust code. This highlights why many security-focused organizations are increasingly adopting memory-safe languages for systems programming.
The Broader Implications
This vulnerability serves as a stark reminder of the security challenges inherent in widely deployed protocols and SDKs. When a vulnerability exists in a software development kit used by numerous manufacturers, the impact multiplies dramatically as each affected device becomes a potential attack vector.
For Apple, this represents one of the most significant security incidents in recent years. For the broader technology industry, it highlights the ongoing struggle with memory safety issues in systems programming languages like C and C++, and may accelerate the adoption of safer alternatives.
Conclusion
The Apple AirPlay vulnerabilities discovered by Oolgo Security Research represent a perfect storm of security issues: they affect millions of devices, require no user interaction, can spread autonomously across networks, and in many cases may never be patched. While Apple has released patches for their own devices, the broader ecosystem of AirPlay-compatible devices presents a much larger challenge.
For users, the best protection is to stay vigilant with updates and limit the attack surface by disabling unnecessary features. For the industry, this incident may serve as a catalyst for broader adoption of memory-safe programming practices and languages.
Let's Watch!
Apple AirPlay Zero-Click RCE: The Biggest Security Bug of 2025 Explained
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence