While many developers focus extensively on authentication, authorization often becomes an afterthought—despite being crucial for application security. In fact, broken Access Control ranks as the #1 web application security risk according to OWASP. This comprehensive guide will help you understand authorization systems, implement proper permission policies, and avoid the common security pitfalls that plague many applications.
Authentication vs. Authorization: Understanding the Difference
Before diving into authorization systems, it's important to clarify the distinction between authentication and authorization. Authentication answers the question "Who are you?" by verifying a user's identity, typically resulting in a user object with basic information like email and name. Authorization, on the other hand, answers "What are you allowed to do?" by determining if an authenticated user has permission to perform specific actions on particular resources.
Many developers mistakenly stop at authentication, assuming that once a user is logged in, they should have access to everything. This oversight creates significant security vulnerabilities in applications.
The Problem with Ad-hoc Authorization Logic
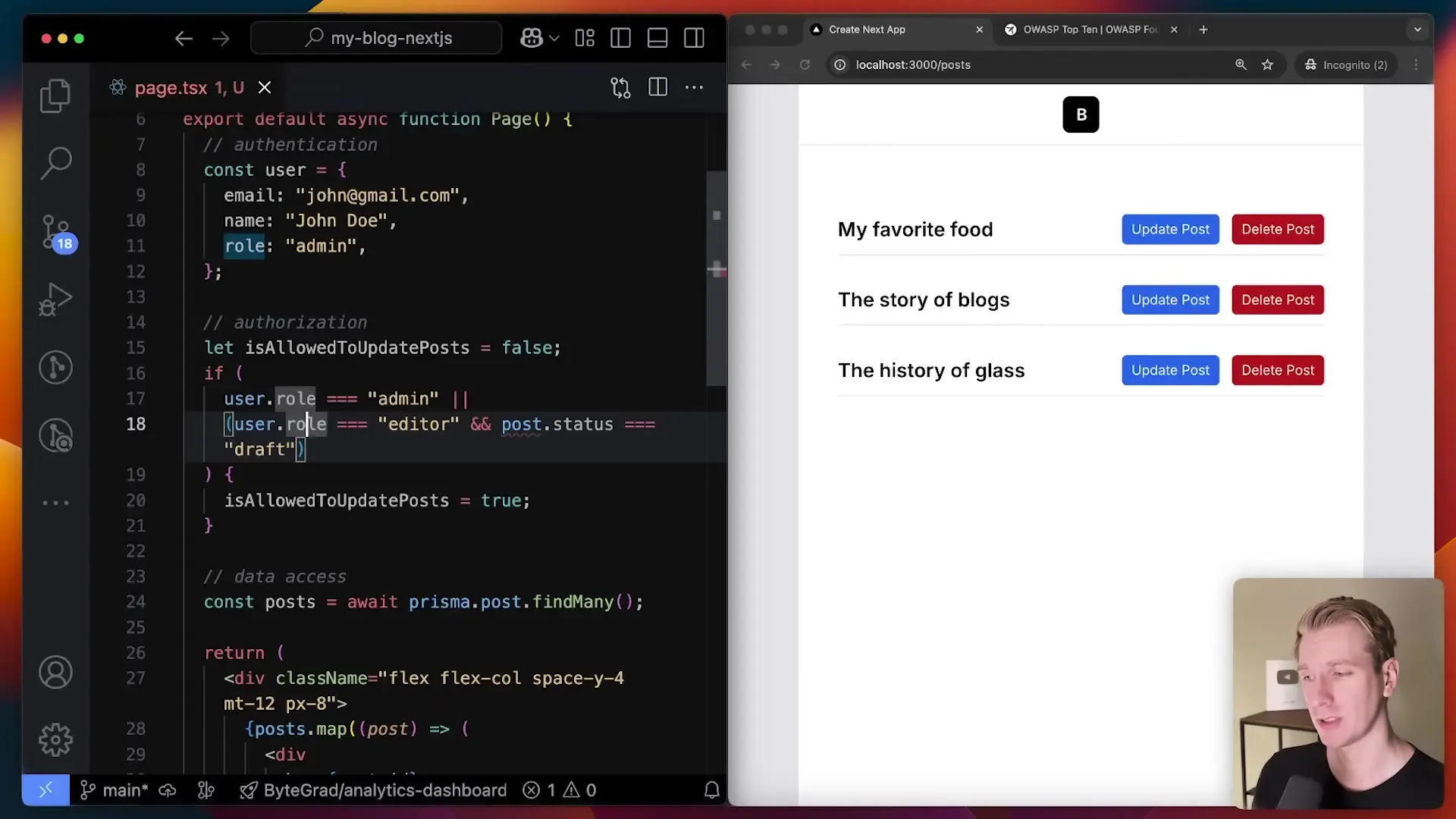
Let's examine a typical scenario in a content management system. Consider a blog application where users can view, create, update, and delete posts. A naive approach might implement authorization logic directly in the UI components:
// Problematic approach - permission logic scattered throughout the codebase
const canUpdatePost = user.role === 'admin' ||
(user.role === 'editor' && post.status === 'draft' && user.experienceLevel === 'senior');
// Conditional rendering based on permissions
{canUpdatePost && <button>Update Post</button>}This approach quickly becomes problematic for several reasons:
- Permission logic becomes scattered throughout the codebase
- Changes to permission rules require updates in multiple places
- Complex conditions lead to error-prone spaghetti code
- Testing and auditing security becomes difficult
- Business logic and authorization logic get intertwined
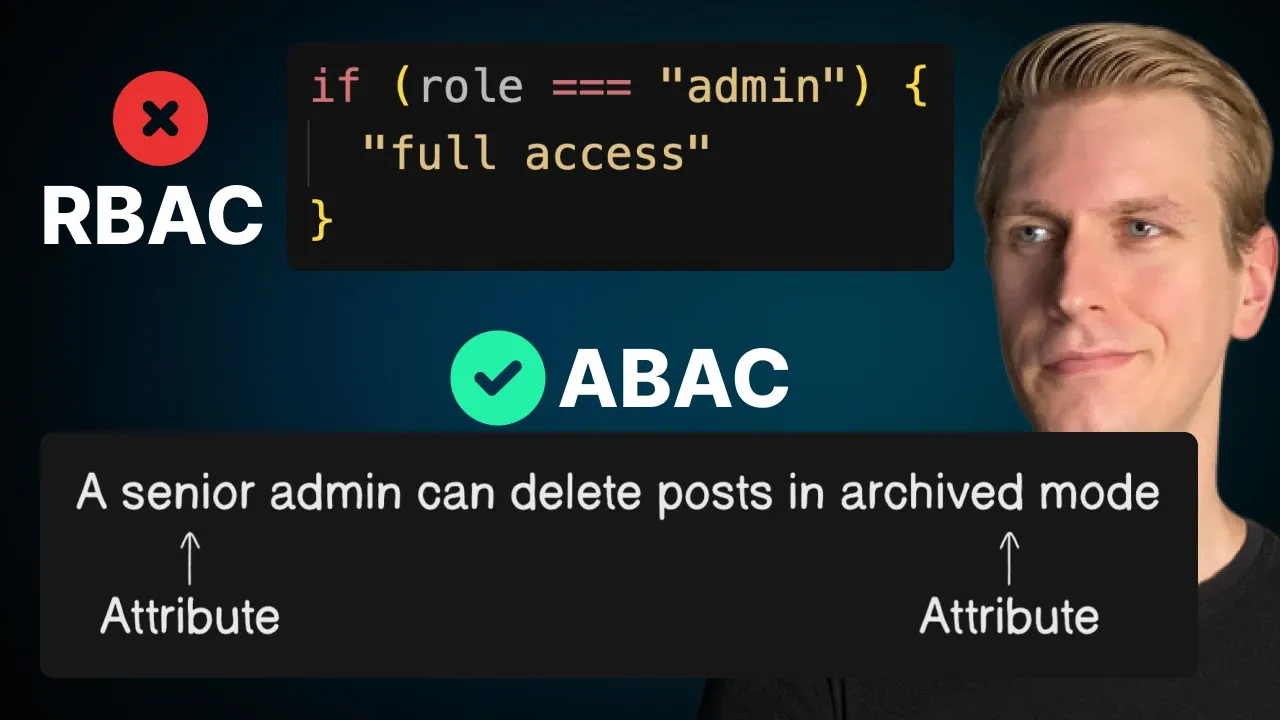
Role-Based Access Control (RBAC): A Structured Approach
Role-Based Access Control (RBAC) offers a more structured approach to authorization. RBAC organizes permissions around roles, actions, and resources. Users are assigned roles, and roles are granted permissions to perform specific actions on particular resources.
Here's how you might implement a basic RBAC system in your application:
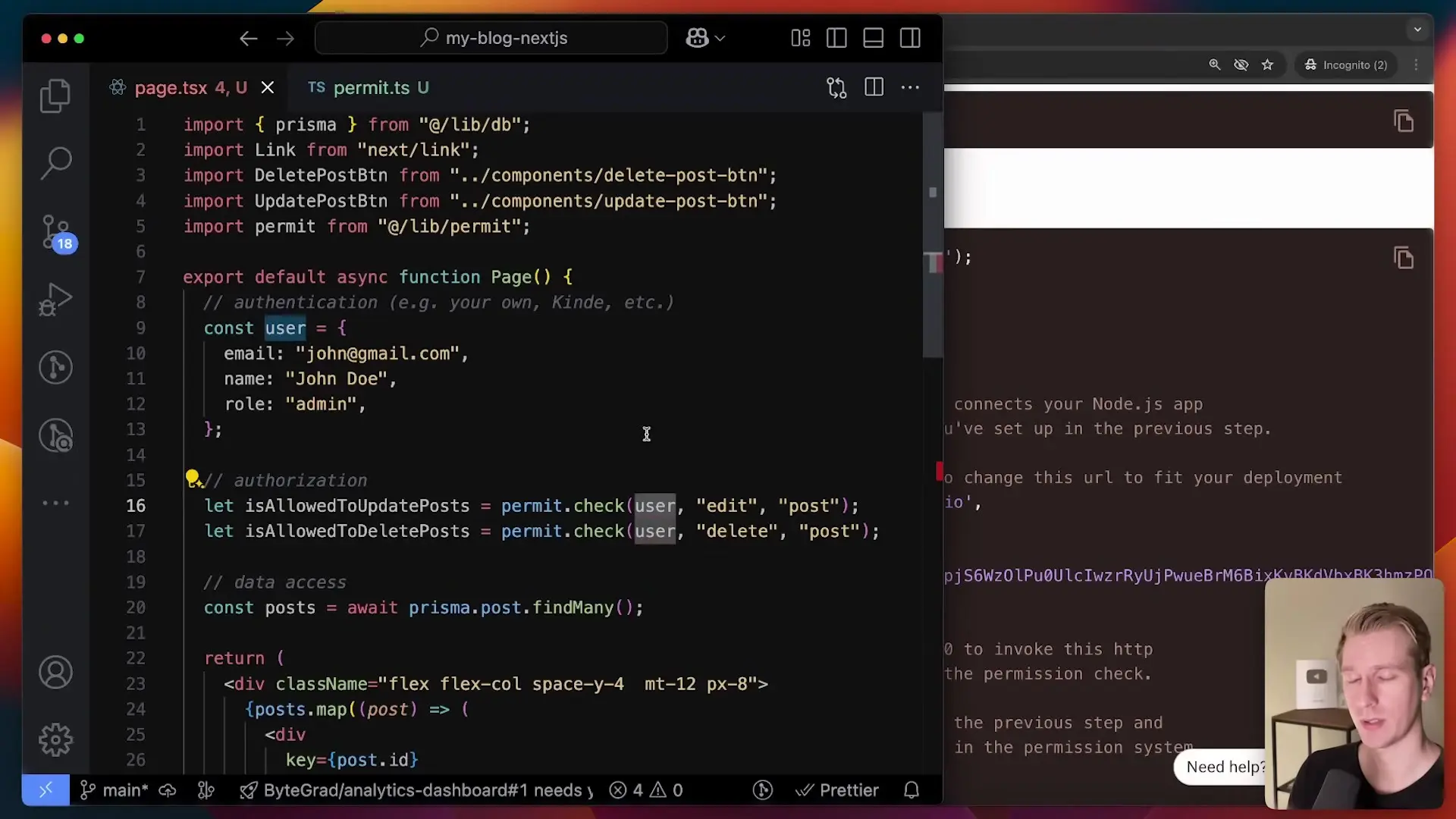
// Centralized permissions configuration
const permissions = {
viewer: ['view:post'],
editor: ['view:post', 'create:post', 'edit:post'],
admin: ['view:post', 'create:post', 'edit:post', 'delete:post']
};
// Permission checking function
function checkPermission(user, action, resource) {
if (!user || !user.role) return false;
const userPermissions = permissions[user.role] || [];
return userPermissions.includes(`${action}:${resource}`);
}
// Usage in components
{checkPermission(user, 'edit', 'post') && <button>Edit Post</button>}
{checkPermission(user, 'delete', 'post') && <button>Delete Post</button>}This approach offers several advantages:
- Centralizes permission logic in one place
- Makes permission changes easier to implement and maintain
- Provides a clear structure for authorization rules
- Separates business logic from authorization concerns
- Makes security auditing more straightforward
Beyond RBAC: Attribute-Based Access Control (ABAC)
While RBAC works well for simpler applications, it can become limiting as your application grows in complexity. This is where Attribute-Based Access Control (ABAC) comes in. ABAC extends beyond roles to consider attributes of the user, resource, action, and environment when making authorization decisions.
For example, ABAC can handle complex rules like: "Editors can only edit posts that are in draft status and were created within their department, but only during business hours."
With ABAC, permission decisions consider:
- User attributes (role, department, seniority, etc.)
- Resource attributes (status, owner, sensitivity level, etc.)
- Action attributes (type of operation, potential impact, etc.)
- Environmental attributes (time, location, device, etc.)
Relationship-Based Access Control (ReBAC): The Evolution of Authorization
The latest evolution in authorization systems is Relationship-Based Access Control (ReBAC). ReBAC focuses on the relationships between entities when determining access permissions. This model is particularly powerful for applications with complex data relationships.
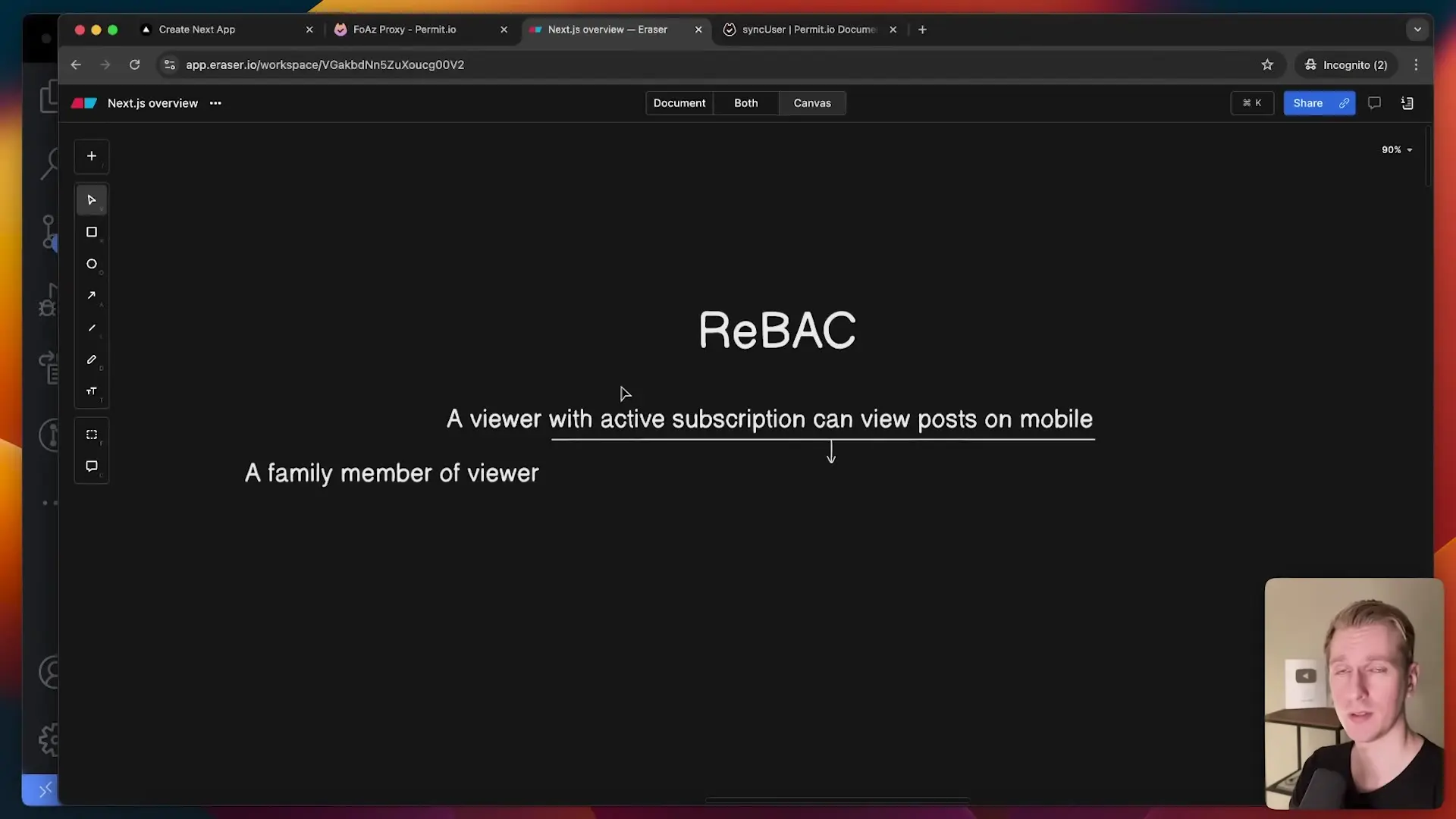
ReBAC can handle scenarios like: "Users can view documents shared with teams they belong to" or "Managers can approve expenses submitted by their direct reports." This approach aligns naturally with graph databases and modern application architectures.
Implementing Authorization in Your Application
When implementing authorization in your application, consider these best practices:
- Centralize authorization logic in a dedicated service or module
- Enforce permissions consistently across all access points (UI, API, etc.)
- Implement authorization checks on both client and server sides
- Use a declarative approach to define permission policies
- Consider using specialized authorization tools or services
- Regularly audit and test your authorization system
- Document your permission model for developers and stakeholders
Authorization Management Tools
While you can build custom authorization systems, specialized tools like Permit can significantly simplify implementation. Such tools provide:
- Visual policy editors for non-technical stakeholders
- SDKs for various programming languages
- Support for multiple authorization models (RBAC, ABAC, ReBAC)
- Policy versioning and audit logs
- Performance optimization through caching
- Separation of policy definition from application code
Using dedicated authorization tools also allows policy changes without requiring application redeployment, which is particularly valuable in enterprise environments where permission requirements evolve frequently.
Conclusion: Authorization as a First-Class Citizen
Authorization should be treated as a first-class citizen in your application architecture, not an afterthought. By implementing a robust permission model using RBAC, ABAC, or ReBAC (depending on your application's complexity), you can significantly enhance your application's security posture and prevent the most common security vulnerability—broken access control.
Remember that while authentication tells you who a user is, authorization determines what they can do. Both are essential components of a secure application, but authorization often requires more careful design and implementation. By centralizing your permission logic and using appropriate authorization models, you can create applications that are both secure and maintainable.
Let's Watch!
Authorization Systems Explained: Beyond Basic Authentication for Secure Apps
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence