
A groundbreaking vulnerability affecting all Intel CPUs has been discovered by researchers at ETH Zurich, demonstrating once again how modern processor architecture can be exploited in ways previously thought impossible. This vulnerability, called Branch Privilege Injection (BPI), represents a significant advancement in CPU microarchitecture attack surfaces and continues the legacy of critical hardware vulnerabilities that began with Meltdown and Spectre in 2016.
Understanding the Foundation: CPU Privilege Levels and Branch Prediction
To comprehend this vulnerability, we first need to understand two fundamental concepts in modern CPU architecture: privilege levels and branch prediction.
Privilege Levels: The Cornerstone of Security
CPUs operate with different privilege levels that create isolation between user applications and the operating system. For example, your web browser runs at a lower privilege level and cannot directly access memory allocated to the Windows operating system, which runs at a higher privilege level. This isolation is a critical security boundary in computing systems.
When Meltdown and Spectre were discovered, they fundamentally broke this isolation by exploiting shared CPU cache between privilege levels, enabling what's known as timing side-channel attacks. These attacks could measure load times to leak information from privileged memory spaces.
Branch Prediction: The Performance Optimizer
Branch prediction is a performance optimization technique in modern CPUs. When the processor encounters an indirect branch (a jump or call instruction where the destination is determined by a register value), the branch predictor attempts to guess where the code will go next based on previous patterns. These predictions are stored in branch prediction tables within the CPU's branch prediction unit.
The purpose is efficiency—loading from main memory is significantly slower than loading from cache. By predicting execution paths, the CPU can preload instructions and data, significantly improving performance.
Branch Privilege Injection: The Magic Behind the Vulnerability
The ETH Zurich researchers discovered something remarkable: a race condition in the branch prediction hardware that allows for what they call Branch Privilege Injection. Here's how it works:
- When a branch misprediction occurs, the correct prediction isn't immediately inserted into the branch prediction table—it waits until the branch 'retires' or completes execution.
- The researchers found that if they make a system call (syscall) from user mode at precisely the right moment, they can create a situation where the branch prediction entry isn't inserted until after the CPU has switched to kernel (privileged) mode.
- This timing allows them to insert a privileged branch prediction instruction into the branch predictor from unprivileged code.
- Once this prediction is in place, they can influence where the kernel's speculative execution will go when it runs independently later.
In essence, they found a way to manipulate the kernel's execution path through speculative execution, despite not having the privileges to directly interact with kernel code.
The Real-World Impact: From Theory to Practical Exploitation
The implications of this vulnerability are profound. Using Branch Privilege Injection, the researchers demonstrated they could:
- Bypass Kernel Address Space Layout Randomization (KASLR) by leaking the base address of the kernel
- Extract sensitive data from kernel memory, including password information from /etc/shadow
- Control speculative execution in privileged contexts from unprivileged code
This attack works by training the branch predictor through a series of carefully timed operations that exploit the race condition. When the kernel later executes code containing indirect branches, the manipulated branch predictor causes it to speculatively execute instructions chosen by the attacker.
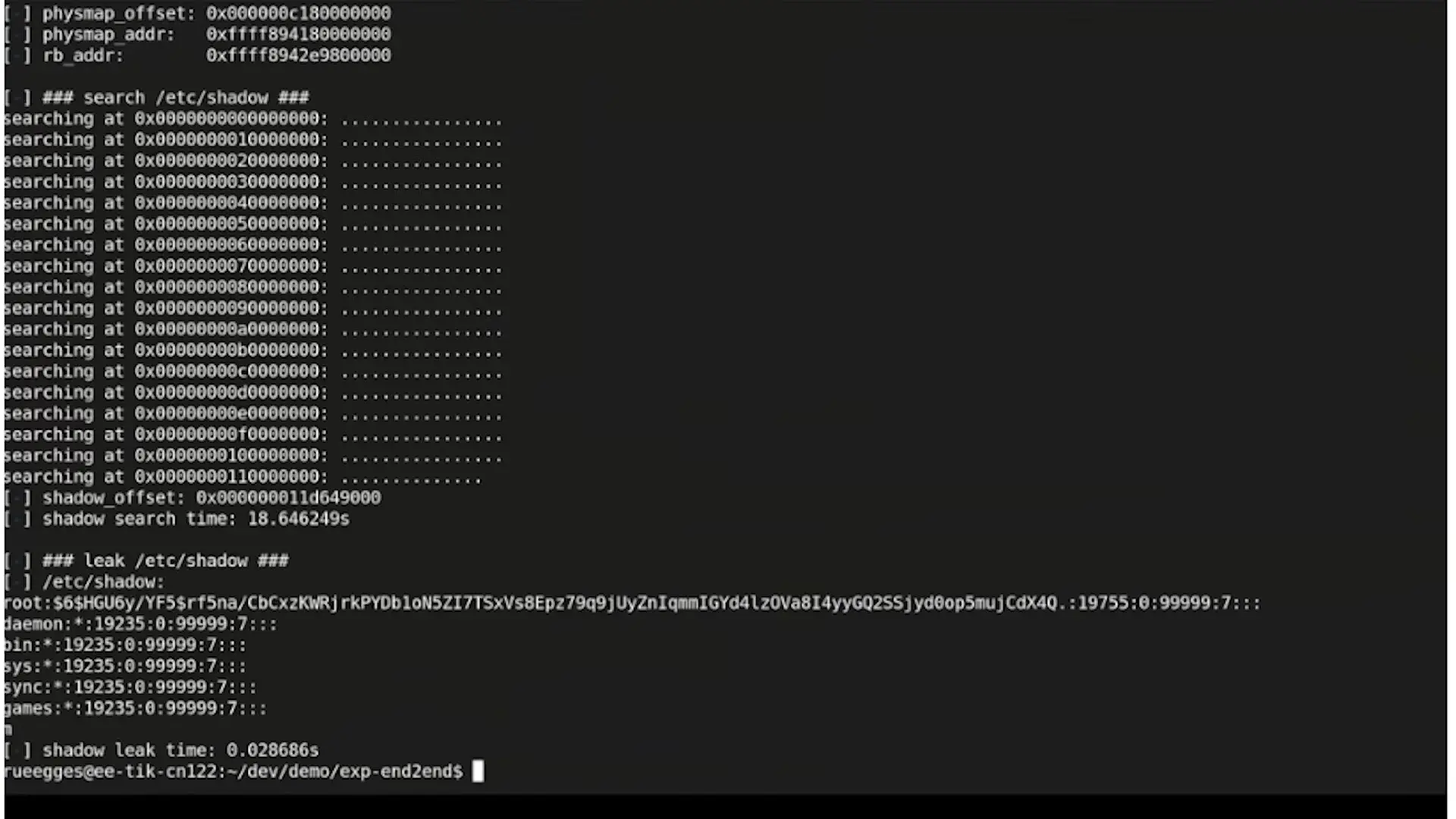
Even though the CPU eventually corrects these mispredictions, the speculative execution leaves traces in the cache. Using the same flush+reload techniques from Spectre and Meltdown, attackers can extract the sensitive information loaded during speculative execution.
Technical Deep Dive: The Mechanics of the Exploit
The BPI attack consists of several crucial steps that together create a powerful information disclosure vulnerability:
1. Branch Predictor Training
The attacker first conducts a series of training runs from user mode that establish specific patterns in the branch predictor. These patterns are designed to influence indirect branches that will later be executed by the kernel.
2. Exploiting the Race Condition
By precisely timing a syscall instruction, the attacker exploits the race condition in the branch prediction hardware. This allows them to insert entries into the privileged branch prediction table that would normally be inaccessible from user mode.
3. Speculative Execution Hijacking
When the kernel later executes code containing indirect branches (such as those in compression functions mentioned in the research), the manipulated predictor causes it to speculatively execute instructions at addresses controlled by the attacker.
4. Information Disclosure via Side Channel
Finally, using what researchers call a "disclosure gadget," the attacker measures cache access times to determine which data was loaded during speculative execution, effectively leaking privileged information.
/* Simplified pseudocode demonstrating the attack concept */
// Step 1: Train branch predictor
for (int i = 0; i < TRAIN_ITERATIONS; i++) {
// Execute sequence that populates branch predictor
indirect_branch(target_address);
}
// Step 2: Exploit race condition with syscall
timing_sensitive_operation();
syscall(); // CPU switches to kernel mode
// Step 3: Kernel executes with poisoned branch predictor
// (happens independently when kernel runs)
// Step 4: Measure cache access times to extract data
for (int i = 0; i < PROBE_ADDRESSES; i++) {
time_t access_time = measure_access_time(probe_address[i]);
if (access_time < THRESHOLD) {
// Data was cached during speculative execution
// Information leaked!
}
}Implications for CPU Security and Future Mitigations
This vulnerability is particularly significant because it affects hardware that was supposedly hardened after the discovery of Meltdown and Spectre. It demonstrates that despite years of mitigations and improvements, fundamental architectural vulnerabilities continue to be discovered in modern CPUs.
For system administrators and security professionals, this research highlights the ongoing importance of:
- Keeping systems updated with the latest microcode and OS patches
- Implementing defense-in-depth strategies that don't rely solely on hardware isolation
- Understanding that hardware vulnerabilities often require years to fully mitigate through CPU design changes
- Monitoring for unusual system behavior that might indicate exploitation attempts
Conclusion: The Ongoing Evolution of Hardware Security
The discovery of Branch Privilege Injection represents another milestone in our understanding of CPU security. It demonstrates that the boundary between privilege levels—one of computing's most fundamental security mechanisms—continues to face sophisticated challenges from researchers and potential attackers.
As CPU architectures continue to prioritize performance optimizations like branch prediction and speculative execution, we can expect more discoveries in this space. Each vulnerability found helps chip manufacturers improve their designs and helps the security community better understand the complex interplay between performance and security in modern computing systems.
For those interested in learning more, the ETH Zurich researchers will be presenting their findings at Black Hat 2025, where they'll provide an even more detailed explanation of this remarkable vulnerability and its implications for hardware security.
Let's Watch!
Branch Privilege Injection: The Intel CPU Vulnerability That Shocked Security Experts
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence