
Cisco is experiencing significant security challenges with two major vulnerabilities recently discovered in their products. Both flaws have been added to CISA's Known Exploited Vulnerabilities (KEV) catalog, indicating they're actively being exploited by threat actors. These vulnerabilities affect Cisco's SNMP implementation and VPN stack, potentially allowing attackers to execute code remotely on affected devices.
Understanding the SNMP Vulnerability
The first vulnerability exists in Cisco's Simple Network Management Protocol (SNMP) implementation. SNMP is a protocol used for collecting and organizing information about managed devices on IP networks. Network administrators use SNMP to monitor device performance, track operational statistics, and manage configuration settings remotely.
SNMP works by allowing devices to expose various properties that administrators need to monitor. These properties include metrics like device uptime, CPU temperature, failed login attempts, and more. An SNMP manager collects logs from these devices, which broadcast data typically on UDP port 161.
The vulnerability stems from how Cisco's implementation processes Object Identifiers (OIDs). OIDs are used in SNMP to identify specific properties on a device. They consist of long strings of numbers that form part of a hierarchical tree structure, with each number corresponding to a specific device property.
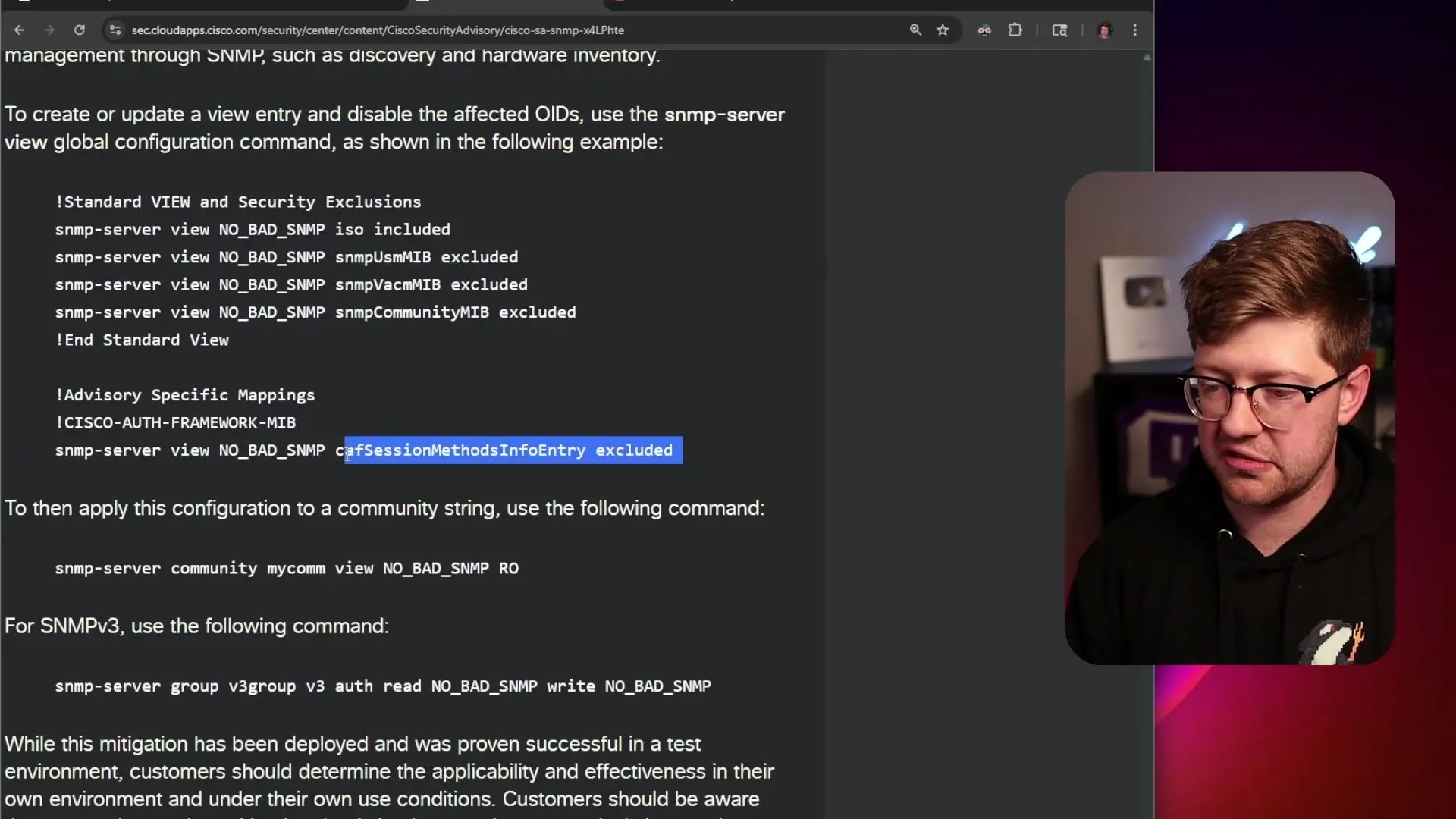
The flaw occurs in the parsing of these OID strings. When an attacker sends a specially crafted OID request to a vulnerable device, it can trigger a buffer overflow or memory corruption vulnerability. This can lead to denial of service conditions on some devices or even remote code execution with root privileges on others.
This vulnerability affects two types of Cisco devices: traditional IOS devices (smaller routers like the 2800 series) and IOS XE devices (larger, Linux-based firewall systems). While the IOS devices might simply restart after exploitation, the IOS XE devices can be compromised to allow code execution with elevated privileges.
The VPN Stack Vulnerability
The second vulnerability affects Cisco's VPN implementation. This flaw received a CVSS score of 9.9 (out of 10), indicating its critical severity. The vulnerability allows authenticated users with valid VPN credentials to send malformed HTTPS requests to a server, potentially triggering a buffer overflow that can lead to code execution with root privileges.
What makes this vulnerability particularly concerning is that it affects devices that are often exposed directly to the internet, making them more accessible to potential attackers who have obtained valid credentials.
Vulnerability Severity and Exploitation Requirements
Interestingly, the SNMP vulnerability received a CVSS score of 7.7, while the VPN vulnerability scored 9.9. This discrepancy raises questions about the scoring methodology, as both vulnerabilities require authentication and can lead to similar outcomes (remote code execution as root).
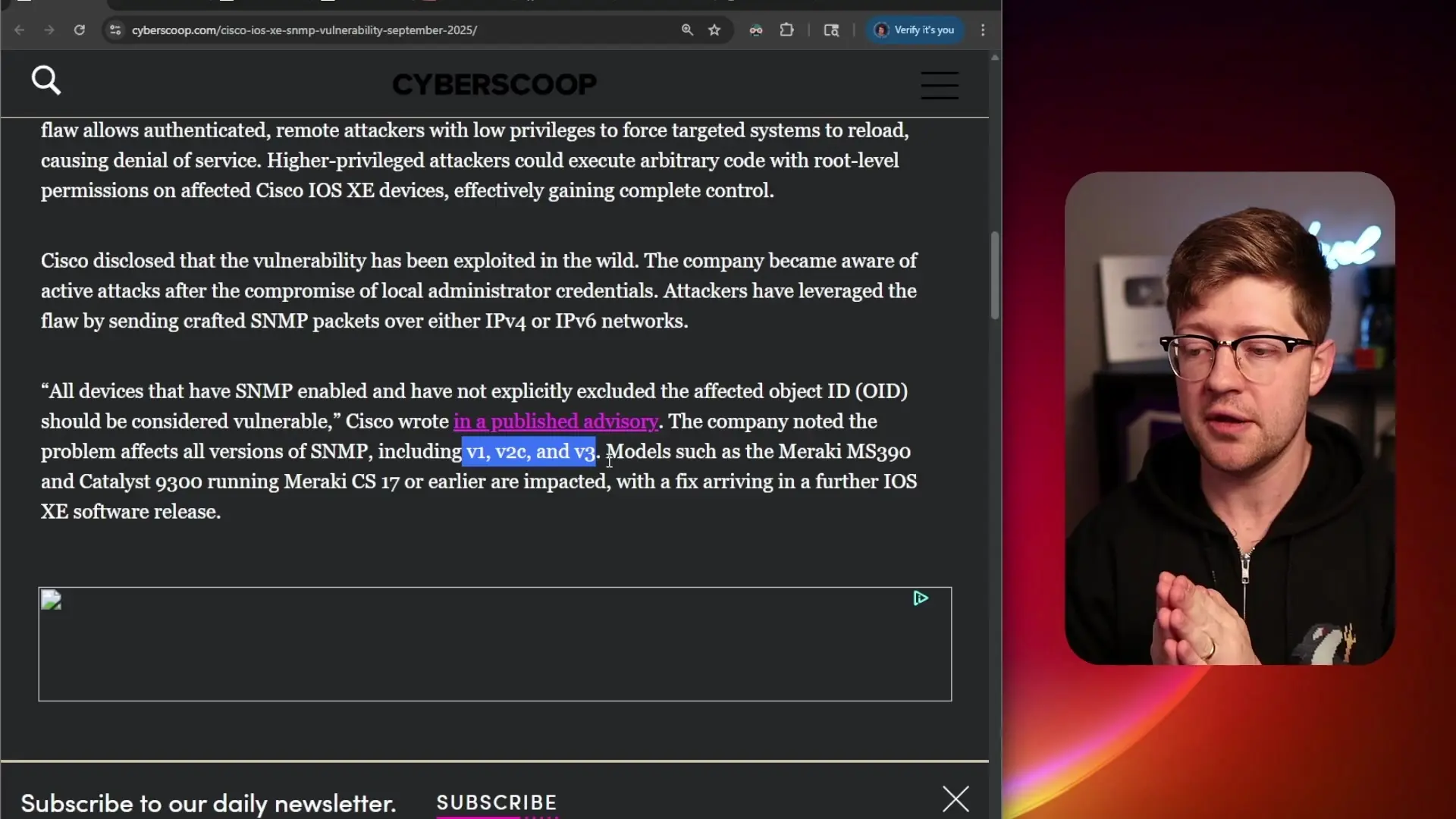
For the SNMP vulnerability to be exploited, an attacker needs to know the SNMP community string (effectively a password) and have network access to the device's SNMP port (161/UDP). While this does require some level of authentication, SNMP community strings are often not changed from their defaults in many networks, and thousands of Cisco devices with UDP port 161 exposed to the internet can be found on services like Shodan.
The VPN vulnerability requires valid VPN credentials, which might be considered a higher barrier to entry as these are typically more carefully managed than SNMP community strings. However, both vulnerabilities ultimately lead to similar outcomes in terms of device compromise.
Mitigation Strategies
Cisco has released advisories with specific mitigation strategies for network administrators. For the SNMP vulnerability, recommendations include:
- Upgrading to SNMP v3, which offers stronger authentication and encryption
- Implementing firewall rules to limit access to SNMP ports
- Disabling specific vulnerable Management Information Bases (MIBs)
- Applying available patches as soon as possible
For the VPN vulnerability, administrators should:
- Apply the latest security patches
- Implement strong authentication mechanisms
- Monitor for suspicious VPN authentication attempts
- Consider implementing additional network segmentation to limit the impact of a potential compromise
Broader Network Security Implications
These vulnerabilities highlight an important principle in network security: even authenticated protocols can contain vulnerabilities that bypass authentication mechanisms. Network administrators should not rely solely on authentication as a security measure but should implement defense-in-depth strategies.
This includes limiting network access to management interfaces like SNMP and VPN services, implementing proper network segmentation, regularly updating community strings and credentials, and applying security patches promptly.
Could Memory-Safe Languages Have Prevented These Issues?
An interesting question is whether these vulnerabilities could have been prevented if Cisco had implemented their software in a memory-safe language like Rust instead of C/C++. The answer is nuanced and depends on the specific implementation details.
For IOS XE devices, which run on Linux, it might theoretically be possible to rewrite the user-mode components in Rust to prevent memory corruption issues. However, for traditional IOS devices that run on Cisco's proprietary operating system with direct hardware access, the situation is more complex.
Embedded systems like network routers often require global mutability - the ability to write to specific memory addresses to control hardware components. This concept is fundamentally at odds with Rust's core principles, which aim to prevent global mutability and enforce strict data hiding. While Rust can be used for embedded development, it presents significant challenges in this context.
Additionally, rewriting large, established codebases is an enormous organizational undertaking that involves significant time, resources, and potential for introducing new bugs during the transition.
Conclusion
The recent Cisco vulnerabilities serve as a reminder that network security requires constant vigilance. Even well-established protocols and products from major vendors can contain serious security flaws that put organizations at risk.
Network administrators should take these vulnerabilities seriously, especially given that they are being actively exploited in the wild. Implementing the recommended mitigations, limiting network exposure of management interfaces, and maintaining a regular patching schedule are essential steps to protect against these and future vulnerabilities.
As we continue to rely heavily on network infrastructure for critical business operations, securing these systems against evolving threats remains a top priority for organizations of all sizes.
Let's Watch!
Critical Cisco Vulnerabilities: SNMP and VPN Security Flaws Explained
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence