Security professionals are raising alarms about a critical vulnerability in Erlang's SSH implementation that allows unauthorized access to servers without any credentials. This authentication bypass vulnerability represents one of the most serious security flaws discovered recently, with potential implications for telecommunications infrastructure, banking systems, and other critical services built with Erlang.
Understanding the Erlang SSH Vulnerability
This vulnerability is specifically found in Erlang's Open Telecom Platform (OTP) SSH implementation - not in the widely-used OpenSSH. While this limits the scope of affected systems, it's important to note that Erlang is extensively used in telecommunications, banking, e-commerce, and instant messaging platforms, making this vulnerability particularly concerning for those sectors.
Erlang was originally developed by Ericsson, a major manufacturer of telecommunications equipment, which means this vulnerability could potentially affect critical infrastructure components. The severity of this flaw cannot be overstated - it allows attackers to execute commands on a server without providing any authentication credentials whatsoever.
Technical Analysis of the Authentication Bypass
The core issue stems from a fundamental logic error in the SSH implementation. Unlike memory corruption vulnerabilities that are common in C-based systems, this is a pure logic flaw where the server fails to verify if authentication has been completed before accepting and processing channel request messages.
- The SSH protocol normally requires a sequence of steps: banner exchange, key exchange, opening a message channel, and then authentication
- In a properly implemented SSH server, no commands should be executed until after successful authentication
- The vulnerability in Erlang's implementation allows attackers to send command requests over the channel before authentication occurs
- The server processes these commands with the same privileges it would grant to an authenticated user
This vulnerability is particularly dangerous because it doesn't require sophisticated exploitation techniques. A simple, properly crafted message sent at the right time in the SSH connection sequence is all that's needed to gain unauthorized access.
Demonstration of the Erlang Client Authentication Bypass
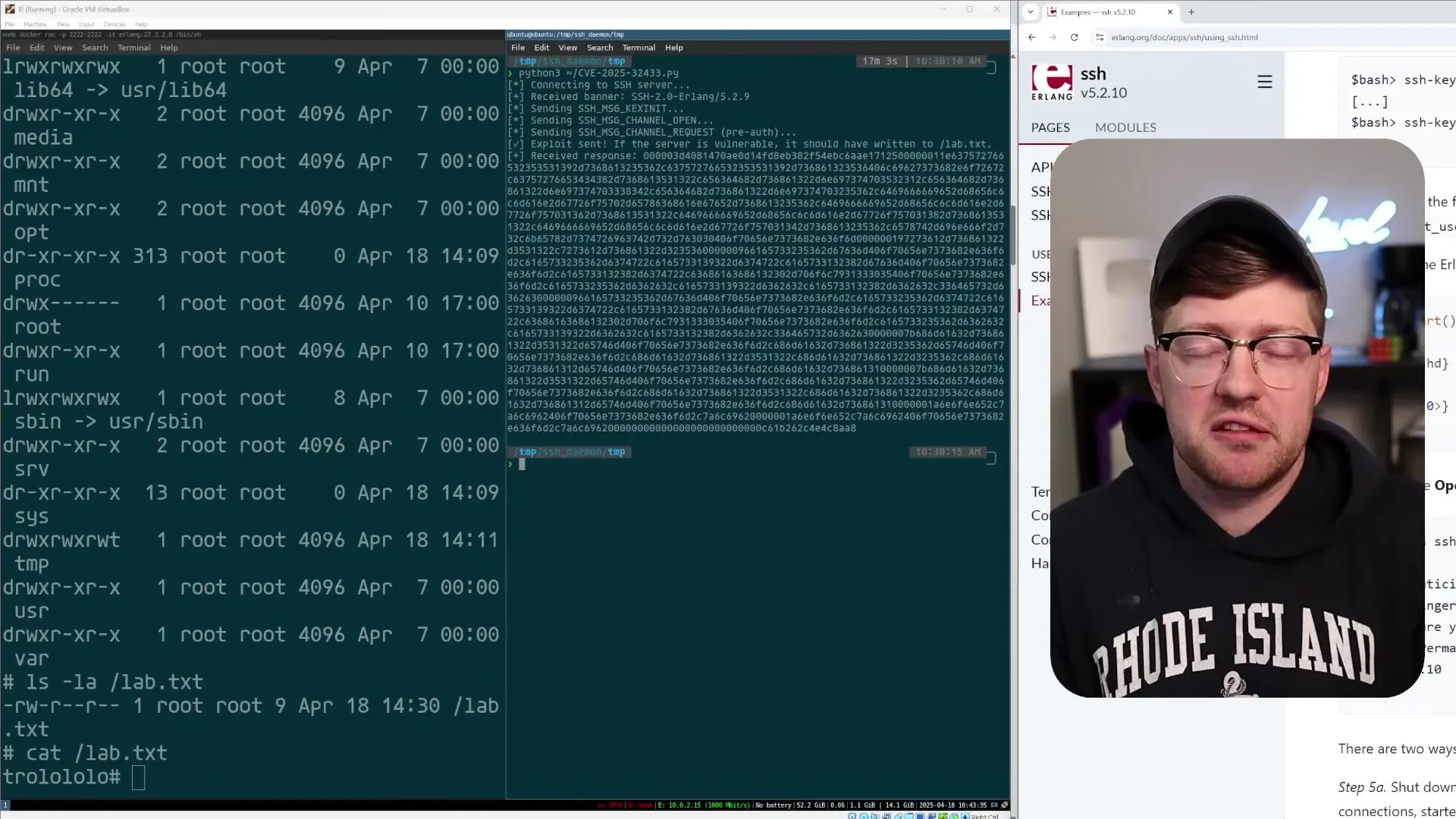
To demonstrate how this vulnerability works in practice, we can set up a vulnerable Erlang SSH server and then execute the exploit against it. The proof of concept is remarkably straightforward.
% Starting a vulnerable Erlang SSH server
use_ssh() ->
application:start(ssh),
ssh:daemon(2222, [
{system_dir, "/tmp/ssh_daemon/"},
{user_dir, "/tmp/ssh_daemon/"}
]).With this server running on port 2222, an attacker can use a specially crafted exploit that follows these steps:
- Connect to the SSH server and exchange version banners
- Perform the initial key exchange to establish an encrypted channel
- Instead of proceeding with authentication, immediately send a channel request message
- Execute arbitrary commands on the server without providing any credentials
AI's Role in Vulnerability Research
Interestingly, this vulnerability was further analyzed with the help of AI tools. When security researchers at Platform Security discovered the vulnerability announcement, they used AI to analyze the differences between vulnerable and patched versions of the code. The AI identified the exact nature of the vulnerability and even helped create a working proof-of-concept exploit in Python.
This represents an emerging trend in security research where AI tools are being used to accelerate vulnerability discovery and exploitation. While this can help defenders better understand threats, it also potentially lowers the barrier for creating sophisticated exploits.
Why Memory-Safe Languages Aren't Always the Answer
An important lesson from this vulnerability is that memory-safe languages like Erlang don't automatically prevent all security issues. While languages such as Rust, Go, and Erlang eliminate entire classes of memory corruption vulnerabilities, they can't prevent logic errors in protocol implementations.
In fact, there's an argument to be made that reimplementing well-tested protocols in new languages can introduce new vulnerabilities. The OpenSSH codebase, despite being written in C, has undergone extensive security auditing and fuzzing over many years. Reimplementing SSH in a memory-safe language requires not only getting the memory management right but also correctly implementing all the protocol logic.
Mitigation and Recommendations
If you're using Erlang's SSH implementation in your systems, here are the recommended steps to mitigate this vulnerability:
- Update to the latest patched version of Erlang/OTP immediately
- If updates cannot be applied right away, consider disabling SSH access to Erlang systems
- Implement network-level controls to restrict SSH access to trusted sources only
- Monitor for unusual SSH connection attempts that might indicate exploitation attempts
- Consider using OpenSSH as an alternative if possible, as it's not affected by this specific vulnerability
Conclusion
The Erlang SSH authentication bypass vulnerability serves as a powerful reminder that security issues can exist in any codebase, regardless of the programming language used. This particular vulnerability demonstrates that logic errors can be just as devastating as memory corruption bugs, especially in security-critical components like SSH servers.
For organizations using Erlang in their infrastructure, this vulnerability should prompt a thorough review of security practices and implementation choices. As we've seen, even well-designed systems can contain fundamental flaws in their security logic, and constant vigilance is required to maintain robust security postures in today's complex software ecosystems.
Let's Watch!
Critical Erlang SSH Authentication Bypass Vulnerability: A Security Analysis
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence