
System security begins at the hardware level, specifically with the motherboard. When vulnerabilities exist in this fundamental component, the entire security chain can collapse. Recently, four critical CVEs were discovered in Gigabyte motherboards that allow malware to operate at the UEFI level, effectively bypassing secure boot protections. These vulnerabilities represent a serious threat to system integrity that every IT professional should understand.
Understanding Computer Security Layers
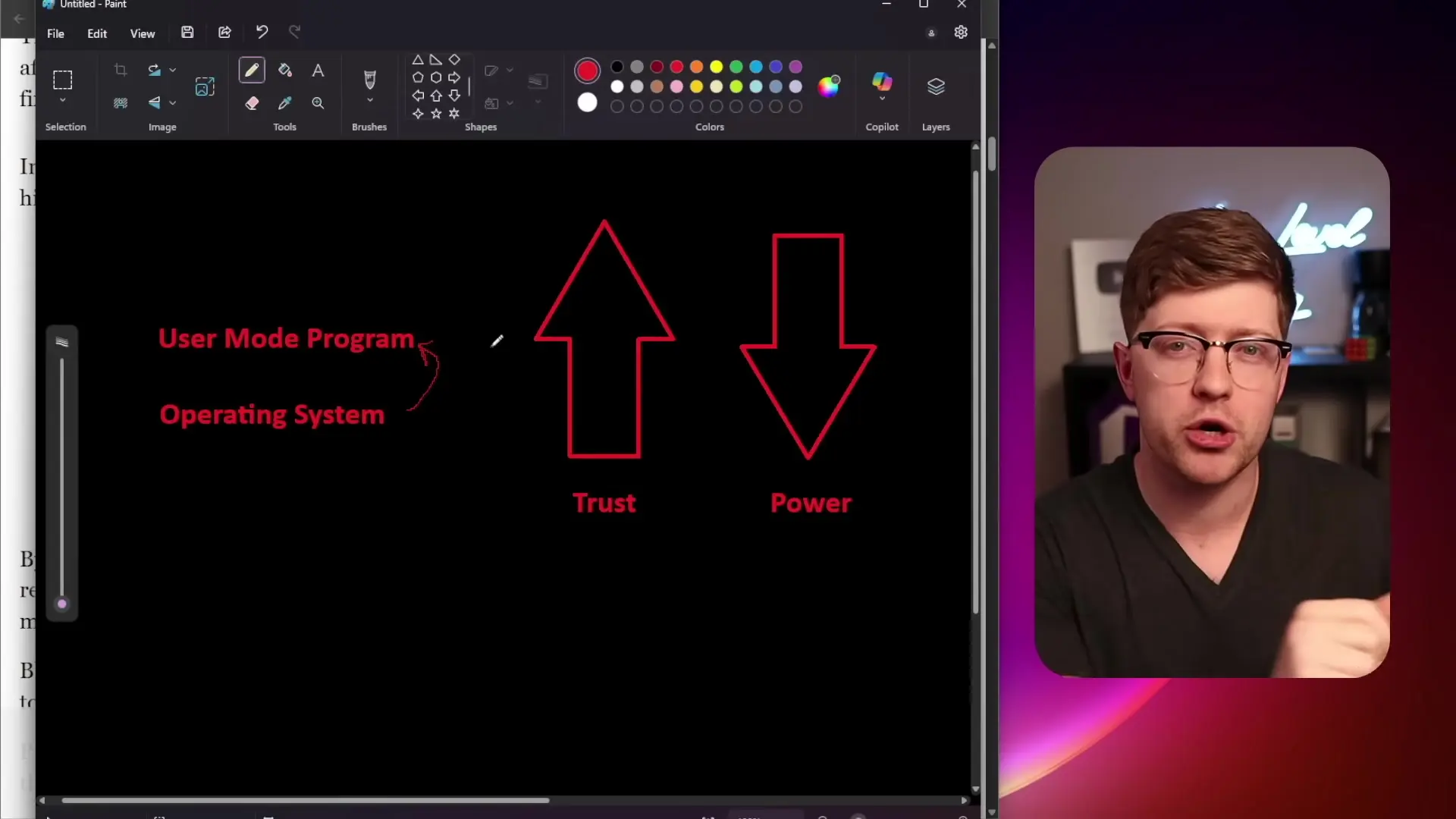
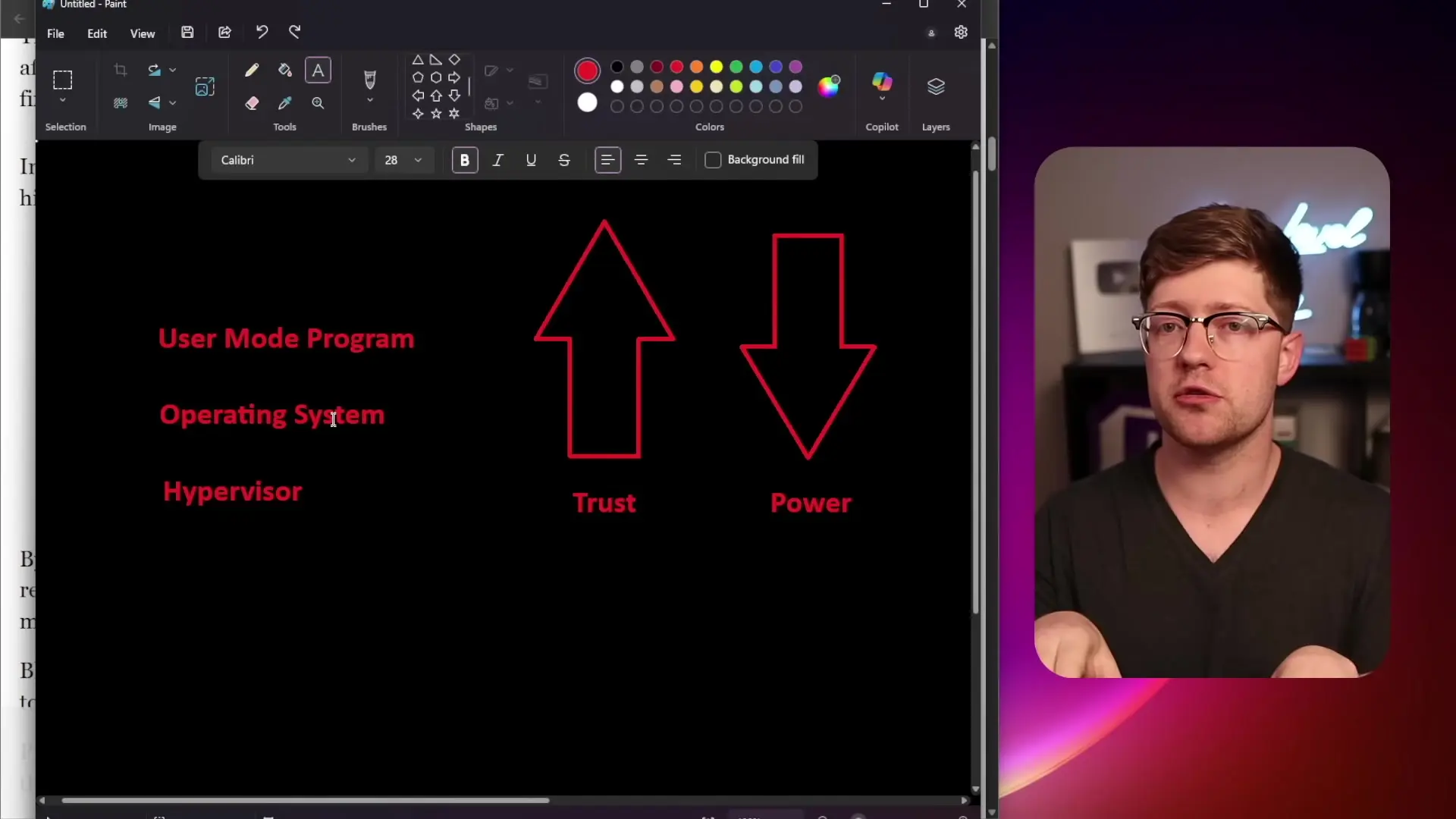
To grasp why these vulnerabilities are so dangerous, we need to understand the layered security model of modern computers. Most people are familiar with user mode programs (like browsers or text editors) being supervised by the operating system. The OS ensures these programs don't access resources they shouldn't. However, this is just the visible part of a much deeper security architecture.
Contrary to common belief, the operating system (typically considered ring zero) is not the lowest level of the system. Below the OS are additional rings that form the foundation of computer security:
- Ring -1: The hypervisor layer, which manages multiple operating systems on the same hardware
- Ring -2: System Management Mode (SMM), the most privileged level that your computer boots into initially
When your computer powers on, it starts in SMM and uses the UEFI (Universal Extended Firmware Interface) to initialize hardware and load higher layers. This process establishes a chain of trust where each layer verifies the integrity of the layer above it before allowing execution.
The Chain of Trust and How It Can Break
Computer security relies on a root of trust that begins with the motherboard firmware. As the system boots, each layer checks the cryptographic signature of the next layer, verifying its integrity before passing control. This process continues all the way up to the operating system and user applications.
An important aspect of this architecture is that as you move up the chain, the trust level increases while the inherent power decreases. The motherboard firmware has the most power but requires careful verification, while user applications have the least power but operate in a more trusted environment.
The Four Gigabyte Motherboard Vulnerabilities
The recently discovered vulnerabilities affect the System Management Interrupt (SMI) handlers in Gigabyte motherboards. These handlers process requests from the operating system to the motherboard firmware. The vulnerabilities allow an attacker with operating system access to write arbitrary code to System Management RAM (SMRAM), which should be strictly protected.
The technical issue involves a flawed implementation where the motherboard firmware checks only a four-byte signature at an attacker-controlled memory address. If this signature matches an expected value, the firmware allows writing to any location in SMRAM. This essentially hands over control of the most privileged execution level to potentially malicious code.
The Mechanics of the Vulnerability
When a system management interrupt is triggered, the CPU places values in registers (like RBX and RCX) that the SMI handler uses to determine what operation to perform. In the vulnerable implementation, the handler allows the caller to specify an arbitrary memory address and then performs only minimal validation before allowing write access to protected memory regions.
This flaw completely undermines the security model by allowing code running at the operating system level to modify the firmware that's supposed to be verifying the operating system's integrity—creating a circular trust problem that breaks the entire security chain.
UEFI-Level Malware and Bootkits
These vulnerabilities enable the installation of what security researchers call "bootkits"—malware that persists at the firmware level. Unlike rootkits that maintain persistence within the operating system, bootkits operate below the OS. This means that even completely reinstalling the operating system won't remove the infection.
Known examples of such malware include Black Lotus, Cosmic Strand, and Mosaic Aggressor. These threats are so serious that even government agencies like the NSA have published guidance on addressing them.
What makes bootkits particularly dangerous is their position in the security hierarchy. Since they operate at the SMM level—which has the most power and the least inherent trust—they can modify any software that loads afterward, including security tools designed to detect them. This creates a perfect stealth mechanism where the malware can hide its own presence by manipulating what the operating system and security software can see.
Attack Requirements and Limitations
Exploiting these vulnerabilities isn't trivial. An attacker would need to:
- First gain code execution as a user-mode program (through browser exploits, malicious email attachments, etc.)
- Escalate privileges to gain operating system (ring zero) access
- Use this privileged access to trigger the vulnerable SMI handlers
While these requirements create some barriers to exploitation, they're not insurmountable for sophisticated attackers, especially in targeted operations against high-value systems.
Remediation and Protection
The severity of these vulnerabilities raises difficult questions about remediation. Once a motherboard has been compromised at the firmware level, it's extremely challenging to verify that the infection has been completely removed.
Security experts recommend these steps for potentially affected systems:
- Check if your Gigabyte motherboard is affected by these CVEs
- Apply any available firmware updates from the manufacturer
- Use security software that can detect known bootkit signatures before they're installed
- Consider hardware replacement for systems suspected of compromise
- Implement defense-in-depth strategies to prevent initial compromise and privilege escalation
It's worth noting that these vulnerabilities originated in firmware provided by American Megatrends (AMI) that Gigabyte incorporated into their motherboards. While AMI did notify manufacturers about the issue, it appears that Gigabyte did not implement the necessary patches in a timely manner.
Could Modern Programming Languages Have Prevented This?
Some have wondered whether memory-safe languages like Rust could have prevented these vulnerabilities. In theory, yes—these are memory corruption issues that memory-safe languages are designed to prevent. However, there are significant challenges to using such languages in embedded environments like motherboard firmware.
Firmware development requires operating in restricted environments without standard libraries ("no_std" and "no_main" modes in Rust). Additionally, embedded programming inherently involves global mutable state and direct hardware manipulation—practices that run counter to Rust's safety principles and would require extensive use of "unsafe" code blocks, partially defeating the purpose.
The Broader Implications for Motherboard Function in Computer Security
These vulnerabilities highlight the critical role motherboards play in the overall security architecture of computing systems. The motherboard isn't just a platform for connecting components—it's the foundation of the entire security model. When vulnerabilities exist at this level, no amount of operating system hardening or application security can fully compensate.
As computing systems become more complex and security threats more sophisticated, hardware manufacturers must prioritize security at every level of development. This includes rigorous testing of firmware implementations, prompt patching of discovered vulnerabilities, and transparent communication with users about security issues.
Conclusion
The four CVEs discovered in Gigabyte motherboards represent a serious security concern that undermines the fundamental trust model of modern computing. By allowing malware to operate at the UEFI level and bypass secure boot, these vulnerabilities can lead to persistent, nearly undetectable compromises that survive operating system reinstallation.
Understanding the layered security architecture of computers and the critical role of motherboard firmware helps illustrate why these vulnerabilities are so significant. For system administrators and security professionals, this case serves as a reminder that security must be considered at all levels of the technology stack, from the hardware foundation to the user-facing application layer.
As we continue to rely on increasingly complex computing systems for critical infrastructure and sensitive operations, ensuring the integrity of our hardware becomes more important than ever. The discovery and disclosure of these vulnerabilities, while concerning, represents an important step in addressing these challenges and building more secure systems for the future.
Let's Watch!
4 Critical Motherboard Vulnerabilities That Bypass Secure Boot
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence