
Is your home router secretly part of a botnet? This question isn't as far-fetched as it might sound. Thousands of home routers remain vulnerable to exploitation, with security researchers recently identifying ongoing attacks specifically targeting ASUS routers exposed to the internet. These compromised devices are being repurposed as operational relay boxes for sophisticated cyberspace espionage campaigns.
Understanding Operational Relay Box Networks
Operational relay box networks represent the modern evolution of traditional botnets. According to the National Cyber Security Center of the Netherlands, these networks function like continuously reconfiguring mazes, with entrance and exit points that shift every 60-90 days to evade detection.
When attackers target a network, instead of connecting directly (which would expose their IP address in logs), they route their traffic through multiple compromised devices. This creates a complex chain that masks their true origin, making attribution and tracking nearly impossible.
These techniques have reportedly been employed in sophisticated campaigns like Salt Typhoon, which has targeted critical U.S. infrastructure including power grids and telecommunications providers.
The Alarming State of Router Security
What's particularly concerning about these vulnerabilities is that they aren't novel or sophisticated. After decades of development, Small Office/Home Office (SOHO) router manufacturers continue to struggle with basic security principles.
While memory corruption vulnerabilities in C-based systems might be somewhat understandable due to the language's complexity, we're still seeing something far more basic and inexcusable: command injection vulnerabilities.
Command Injection: An Unforgivable Security Flaw
Command injection vulnerabilities occur when software fails to properly sanitize user input before passing it to system functions. This basic security mistake essentially gives attackers the ability to execute arbitrary commands with the same privileges as the running program.
char buffer[100];
char command[150];
printf("What is your name? ");
scanf("%99s", buffer); // Even with bounds checking
// Vulnerable command construction
snprintf(command, sizeof(command), "echo Your name is %s", buffer);
system(command); // Executing with user inputIn the example above, an attacker could input something like "Steve; ls;" which would not only echo their name but also execute the 'ls' command, listing all files in the current directory. This represents just the beginning of what's possible with command injection.
What makes command injection particularly dangerous compared to other software exploits is that it requires no knowledge of memory maps or complex exploitation techniques. Unlike buffer overflow attacks that need to bypass Address Space Layout Randomization (ASLR), command injection provides immediate code execution with minimal effort.
The Remote Management Problem
A key factor enabling these attacks is the exposure of router management interfaces to the internet. While most routers ship with their HTTP server accessible only from the LAN (local network) side, many have options to enable "remote management" that exposes these interfaces to the WAN (internet) side.
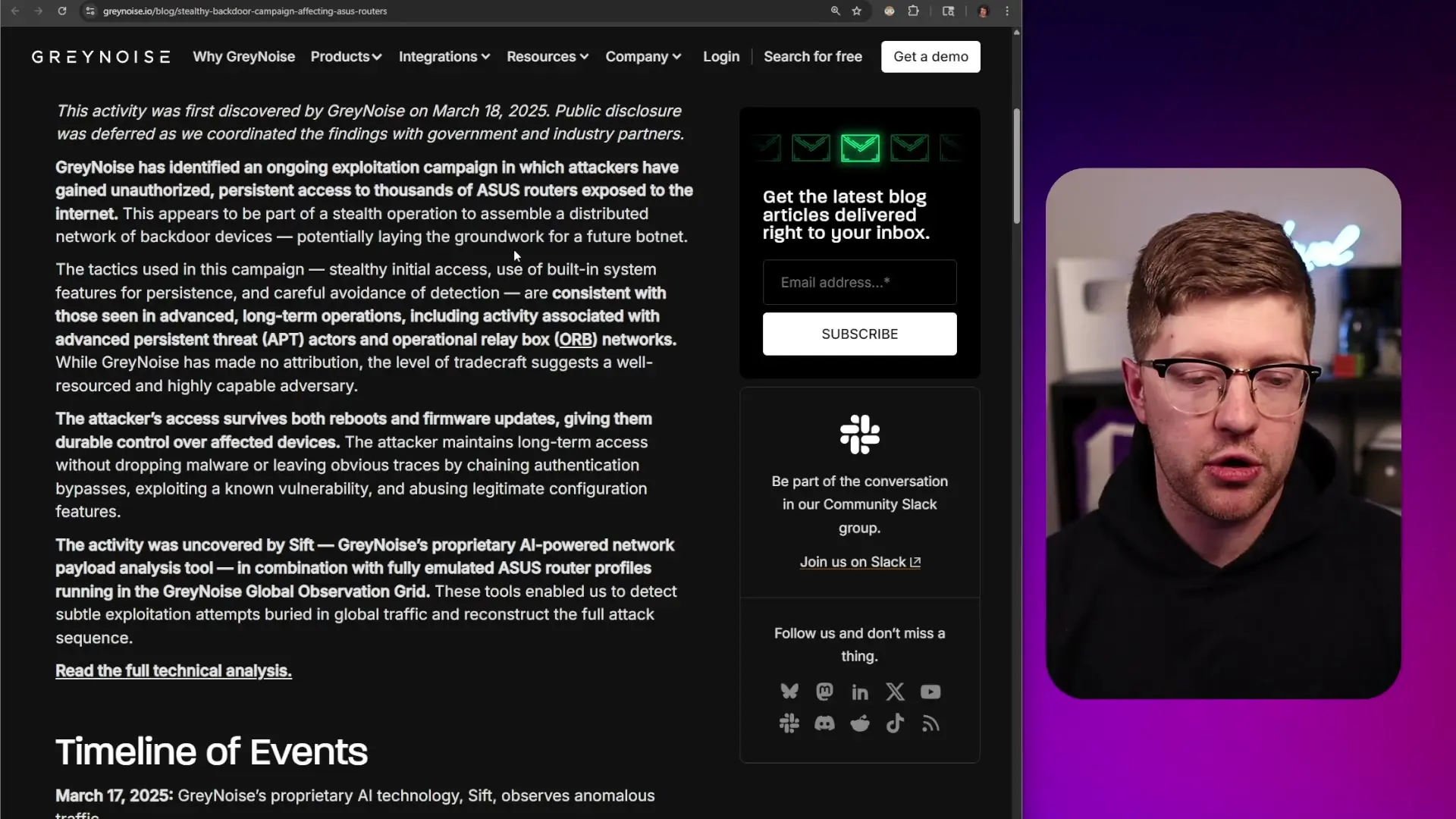
Security researchers at Grey Noise detected a campaign specifically targeting routers with exposed management interfaces, installing backdoor SSH daemons that wait for connections on non-standard ports. These backdoors provide persistent access even after some security measures are implemented.
Protecting Your Router from Software Exploits
While manufacturers like ASUS have released patches for identified vulnerabilities, the reality is that many users rarely if ever update their router firmware. Additionally, once a device has been compromised at the root level, a simple firmware update may not be sufficient to remove all traces of the infection.
Sophisticated attackers can modify bootloaders or store malicious code in non-volatile memory that persists across firmware updates, waiting to reactivate after the system restarts.
Essential Router Security Measures
- Regularly update your router's firmware to the latest version
- Perform a factory reset after applying security-related updates
- Set strong, unique administrator passwords
- Disable remote management features (never expose management interfaces to the internet)
- Consider replacing older routers that no longer receive security updates
- Monitor for unusual network activity or performance degradation
- Use a separate firewall device for additional protection when possible
The Broader Implications for Network Security
The prevalence of these software security exploits highlights a critical weakness in our digital infrastructure. Home routers represent a perfect target for attackers: they're always on, rarely updated, and sit at the gateway between private networks and the internet.
As these devices continue to proliferate in homes and small businesses worldwide, the security practices of router manufacturers become increasingly important. Unfortunately, the evidence suggests that many aren't taking this responsibility seriously enough, continuing to ship products with fundamental security flaws that have been well-understood for decades.
For security professionals and network administrators, this situation emphasizes the importance of defense in depth, never trusting edge devices alone to provide adequate protection for sensitive systems and data.
Conclusion
The ongoing exploitation of home routers serves as a stark reminder that software vulnerabilities and exploits continue to threaten our digital security. By understanding these threats and implementing proper security practices, users can significantly reduce their risk of becoming unwitting participants in global cyber espionage networks.
Whether you're a security professional or simply a concerned home user, taking the time to properly secure your network edge devices is an essential step in protecting your digital presence in an increasingly hostile online environment.
Let's Watch!
7 Critical Router Security Exploits That Could Put Your Network at Risk
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence