
WinRAR, the popular file compression software known for its seemingly endless 40-day free trial, has become the target of sophisticated hacking campaigns. Security researchers have identified multiple critical vulnerabilities being actively exploited by threat actors, including a Russia-aligned group called Romcom. These vulnerabilities allow attackers to deploy malware through seemingly innocent compressed files, potentially compromising entire systems without users even realizing it.
Understanding the WinRAR Vulnerability
The most recent vulnerability (CVE-2025-8088) exploits how WinRAR handles Alternative Data Streams (ADS), a feature of the NTFS file system used by Windows. ADS allows files to store additional metadata, but this functionality has become a security liability when improperly implemented.
When a user opens a malicious RAR file, what appears to be a simple document extraction actually triggers a complex attack. The vulnerability allows attackers to use directory traversal techniques (using '../' patterns) to write files to locations outside the intended extraction directory.
How the Attack Works
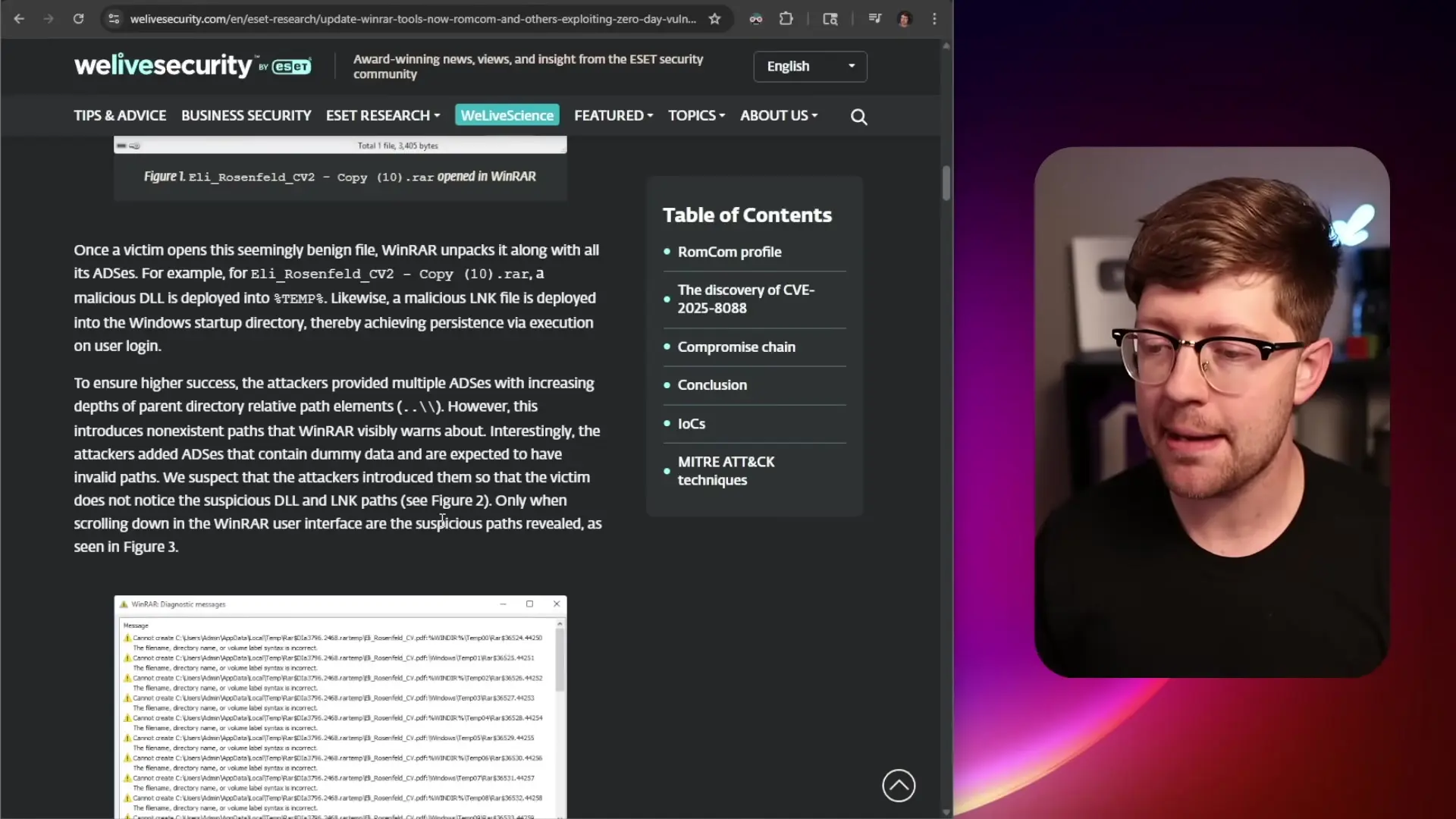
The attack follows a deceptively simple pattern:
- An attacker creates a RAR file containing what appears to be a legitimate document (like a resume or PDF)
- Hidden within the file's Alternative Data Streams are malicious payloads with directory traversal patterns (../)
- When the user extracts the RAR file, WinRAR fails to properly sanitize these paths
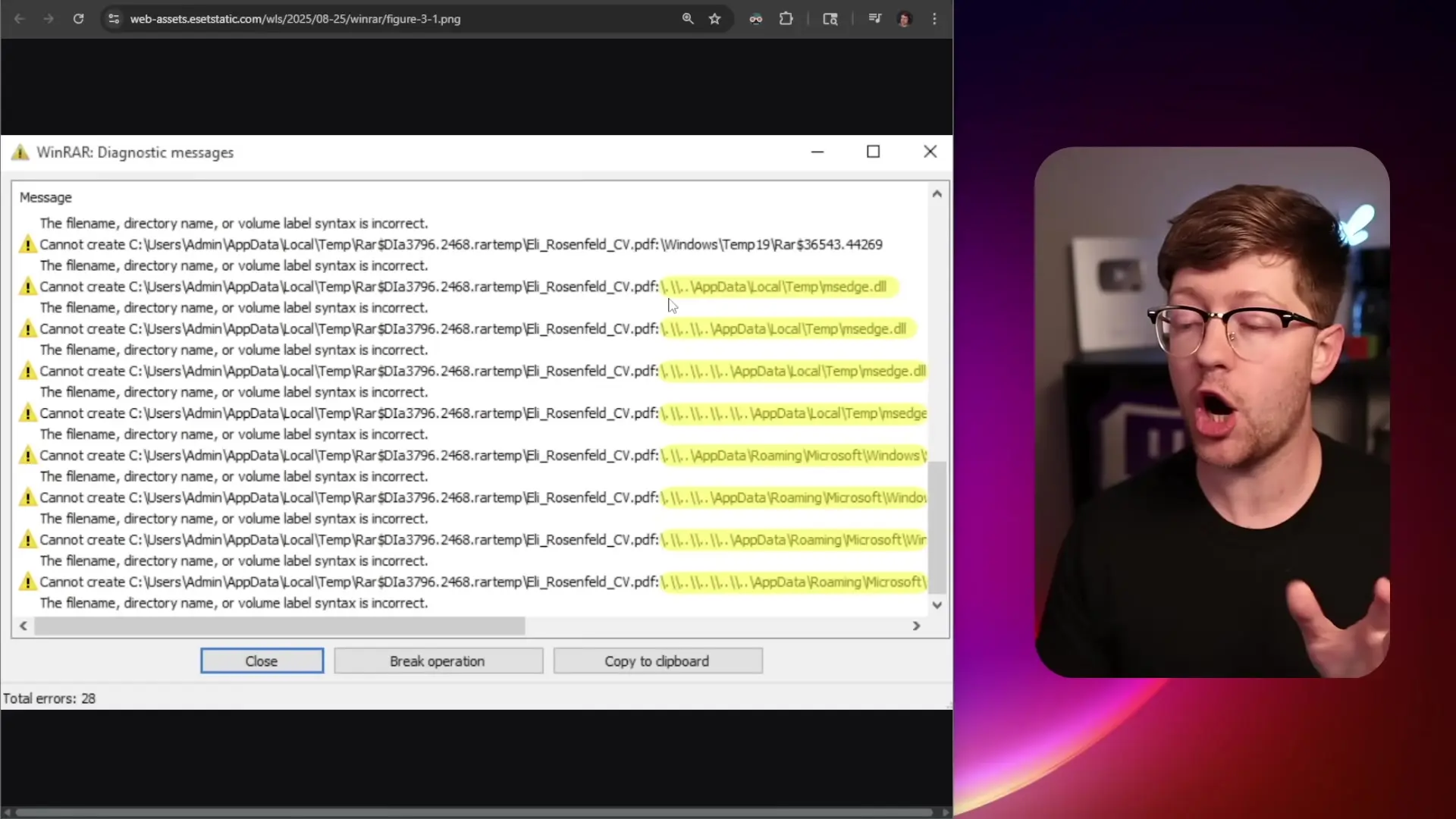
- The malware places DLL files in system locations like 'AppData\Local\Temp'
- These DLLs are later loaded by legitimate applications (like MS Edge), executing the malicious code
What makes this attack particularly dangerous is the obfuscation technique used. The extraction process displays numerous temporary files being created, which most users dismiss as normal operation. Meanwhile, the malicious files are being placed in system directories where they'll be automatically executed later.
Directory Traversal: A Common Vulnerability Pattern
Directory traversal vulnerabilities are surprisingly common in file compression utilities. They occur when software fails to properly sanitize file paths, allowing attackers to write files outside the intended directory structure.
In the case of WinRAR, the vulnerability specifically involves the handling of Alternative Data Streams. When WinRAR extracts a file with ADS containing directory traversal sequences (../), it fails to properly validate these paths, allowing files to be written to sensitive system locations.
Previous WinRAR Vulnerabilities
This isn't the first time WinRAR has faced serious security issues. Another recent vulnerability (CVE-2023-38831) involved how WinRAR handles files with identical names. When a user attempts to open a document.pdf file, a bug allows WinRAR to execute scripts from a folder with the same name, creating another attack vector.
These types of logic and sanitization issues are particularly dangerous because they don't require sophisticated memory corruption techniques. Attackers can simply craft files in specific ways to trigger the vulnerability, making exploitation relatively straightforward.
Protecting Your Systems from WinRAR Exploits
- Update WinRAR immediately to the latest version that patches these vulnerabilities
- Consider using alternative compression tools with strong security records
- Never open compressed files from untrusted sources
- Implement endpoint protection solutions that can detect and block suspicious file operations
- Use zero-trust security approaches that limit application permissions and monitor for unusual behaviors
The Broader Security Implications
The WinRAR vulnerabilities highlight a critical security concept: even commonly used utilities can become attack vectors. While memory corruption vulnerabilities get significant attention in security circles, logic flaws and input sanitization issues can be equally dangerous and often easier to exploit.
For developers, these vulnerabilities serve as important reminders about the necessity of proper input validation, especially when handling file paths. Any software that processes user-controlled input must carefully sanitize that input to prevent directory traversal and similar attacks.
Conclusion
File compression utilities like WinRAR are essential tools for many users, but they can also introduce significant security risks when vulnerabilities are discovered. The recent directory traversal vulnerabilities in WinRAR demonstrate how seemingly innocuous file operations can be weaponized by attackers.
By understanding these attack vectors and implementing proper security measures, users and organizations can protect themselves from these threats. Always keep your software updated, be cautious about the files you open, and consider implementing advanced security solutions that can detect and block suspicious activities.
Let's Watch!
5 Critical WinRAR Vulnerabilities Exposing Your System to Hackers
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence