
A significant security vulnerability has been discovered in the Apple AirPlay protocol that security researchers are calling one of the most serious exploits of the year. This zero-click RCE (Remote Code Execution) vulnerability allows attackers to execute malicious code on target devices without any user interaction, simply by being on the same network as the victim.
The Scope and Severity of the AirPlay Exploit
The security research team at Oolgo Security Research has identified over 20 bugs in the Apple AirPlay Protocol, culminating in a dangerous zero-click RCE vulnerability (CVE-2025-24252). What makes this discovery particularly alarming is its dual impact: it affects not only Apple's own implementation of AirPlay but also the AirPlay SDK (Software Development Kit) used by numerous third-party manufacturers.
This means the vulnerability extends beyond Apple's ecosystem to potentially affect any device that implements the AirPlay SDK, including speakers, receivers, and other compatible hardware from various manufacturers. The zero-click remote exploit requires no user interaction - an attacker simply needs to be on the same Wi-Fi network to potentially compromise vulnerable devices.
Understanding the Technical Nature of the Vulnerability
The primary vulnerability affecting macOS is a use-after-free bug. In systems programming, memory is allocated from the heap for operations and should be returned (freed) when no longer needed. The vulnerability occurs when the program continues to use a pointer to memory that has already been freed.
This can lead to type confusion, where two different pointers reference the same memory location but interpret it as different data types. The result is a "write-what-where" primitive that allows attackers to write arbitrary data to any location in the process's memory space.
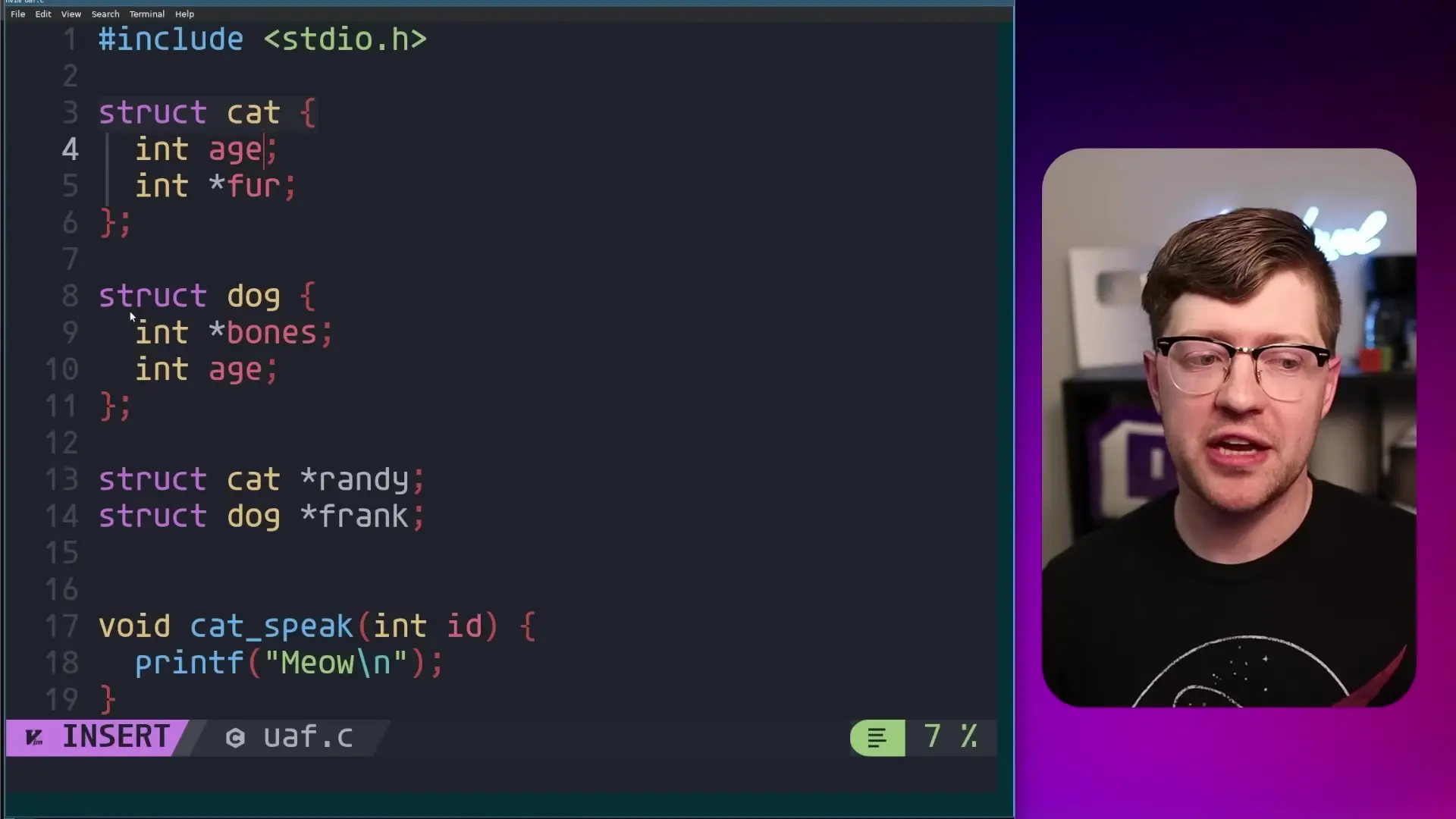
The following simplified example illustrates how type confusion can occur:
struct Cat {
int age; // 4 bytes
char *name; // 8 bytes (on 64-bit systems)
};
struct Dog {
char *bones; // 8 bytes (on 64-bit systems)
int age; // 4 bytes
};
// If memory for a Cat is freed but still accessible,
// and then interpreted as a Dog, setting cat->age
// could overwrite dog->bones pointerThe second major vulnerability is a stack-based buffer overflow in the AirPlay SDK. This occurs when data written to a buffer exceeds its allocated space, allowing attackers to overwrite adjacent memory. These vulnerabilities can be chained together to achieve full remote code execution.
The Wormable Nature: What Makes This Exploit Particularly Dangerous
Perhaps the most concerning aspect of this zero-click RCE is that it's wormable. This means that once an attacker compromises one device, they can use it as a pivot point to attack other devices on the same network or on new networks that the infected device connects to later.
For example, if your iPhone is compromised while connected to a public Wi-Fi network, the malware could remain dormant until you connect to your home network. At that point, it could automatically spread to other AirPlay-compatible devices in your home, creating a self-propagating network of compromised devices.
This wormable characteristic is particularly dangerous for IoT devices like smart speakers, which can serve as persistent network entry points or command-and-control servers for attackers. These devices often remain powered on and connected to networks continuously, providing a permanent foothold for attackers.
Mitigation and Protection Strategies
If you're concerned about this zero-click remote exploit, here are the recommended steps to protect your devices:
- Update all Apple devices immediately with the latest security patches
- Disable AirPlay receiver functionality on devices when not in use
- Monitor for suspicious traffic on TCP port 7000 (the port used by AirPlay)
- Consider using network segmentation to isolate IoT devices from critical systems
- Contact manufacturers of third-party AirPlay-compatible devices to confirm if and when security updates will be available
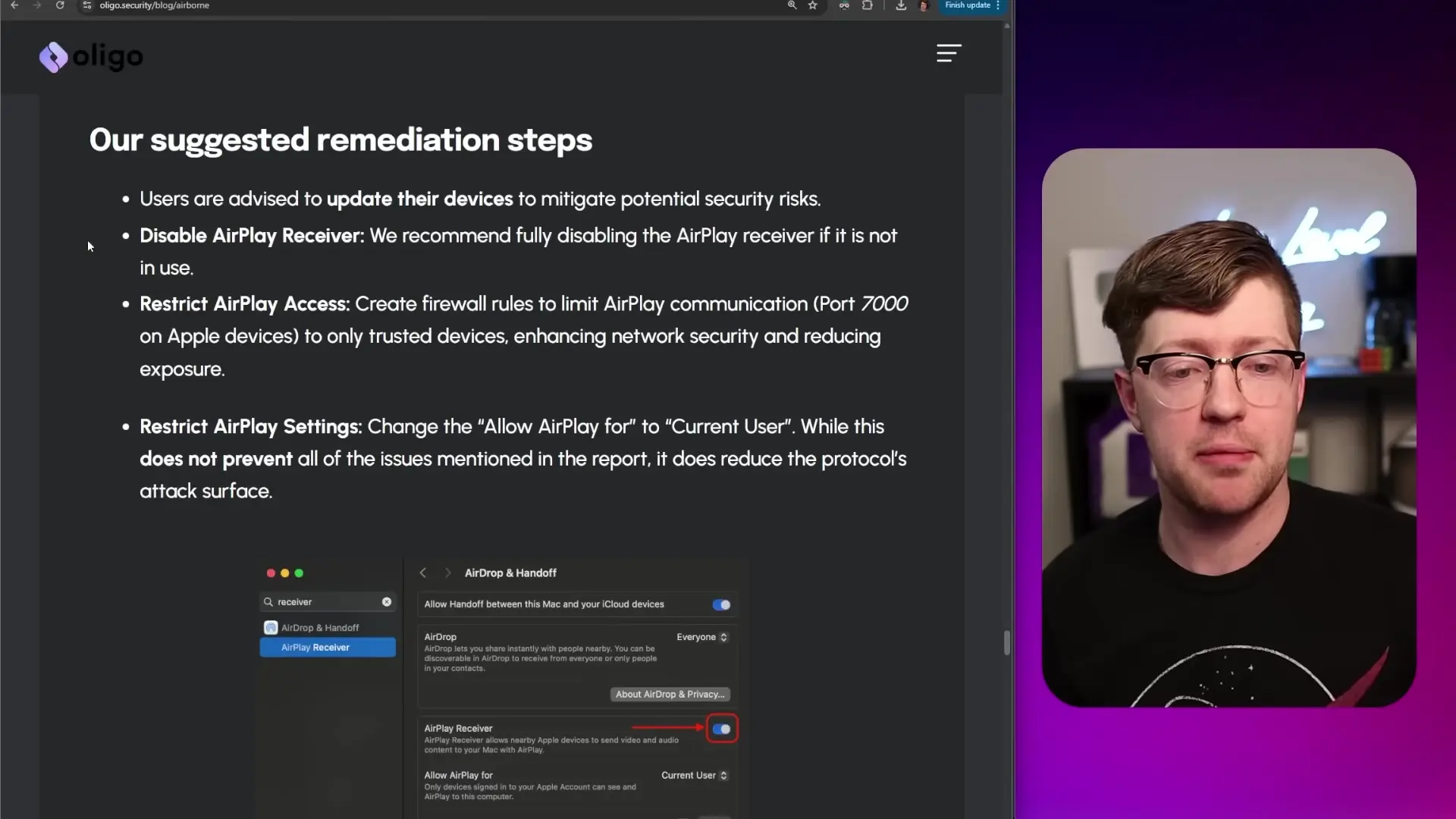
For third-party devices using the AirPlay SDK, the situation is more complex. Each manufacturer must independently update their implementation with the patched SDK version, which could take time or may not happen at all for older devices.
Could Memory-Safe Languages Have Prevented This?
An interesting question is whether modern memory-safe programming languages could have prevented these vulnerabilities. The answer is yes - memory-safe languages like Rust are specifically designed to prevent both spatial memory violations (buffer overflows) and temporal memory violations (use-after-free bugs).
Rust's ownership model and borrow checker enforce strict rules at compile time that make these classes of vulnerabilities impossible without explicitly using unsafe code blocks. The compiler would have caught and prevented both the use-after-free and buffer overflow vulnerabilities that form the basis of this exploit.
Conclusion: Broader Implications for Security
The discovery of this zero-click RCE vulnerability in AirPlay highlights several important lessons for the security community. First, it demonstrates how vulnerabilities in widely-used protocols can have cascading effects across entire ecosystems of devices. Second, it underscores the continued prevalence of memory safety issues in systems programming, even in software from security-conscious companies like Apple.
Finally, it serves as a reminder of the importance of prompt patching and the challenges of securing IoT devices that may not receive timely updates. As our homes and workplaces become increasingly connected, the security implications of protocol-level vulnerabilities grow exponentially more serious.
This AirPlay exploit represents a perfect storm of security concerns: it affects multiple device types, requires no user interaction, can spread autonomously, and exploits fundamental memory safety issues that have plagued C and C++ codebases for decades. By understanding its mechanics, we can better appreciate the importance of secure coding practices and prompt security updates in our increasingly connected world.
Let's Watch!
Critical Zero-Click RCE Vulnerability in Apple AirPlay: What You Need to Know
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence