
In the world of software development, security should always be a top priority. However, a recent incident involving a free VPN service called "Big Mama VPN" demonstrates how easily security standards can be compromised when users install seemingly innocent applications. This case serves as a critical warning sign for developers about the importance of thorough security assessment and the potential dangers lurking in free services.
The Big Mama VPN Incident: A Case Study in Security Failure
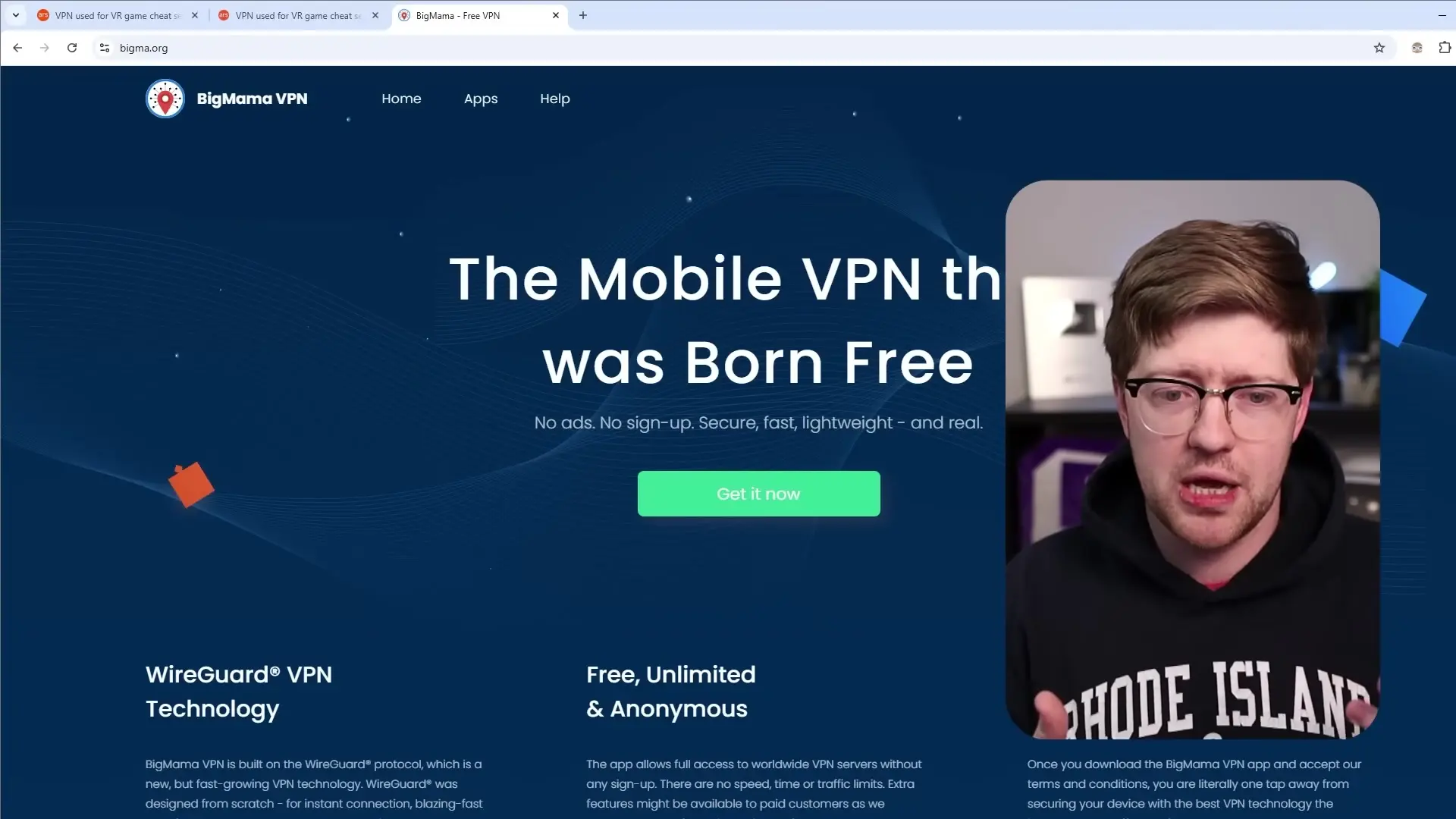
The story begins with a virtual reality game called Gorilla Tag. Players looking to gain an advantage in the game were directed to videos promoting a free VPN application called Big Mama VPN. The app claimed to create network delays that would give players an edge in the game. However, what these users didn't realize was that they were becoming part of something much more concerning.
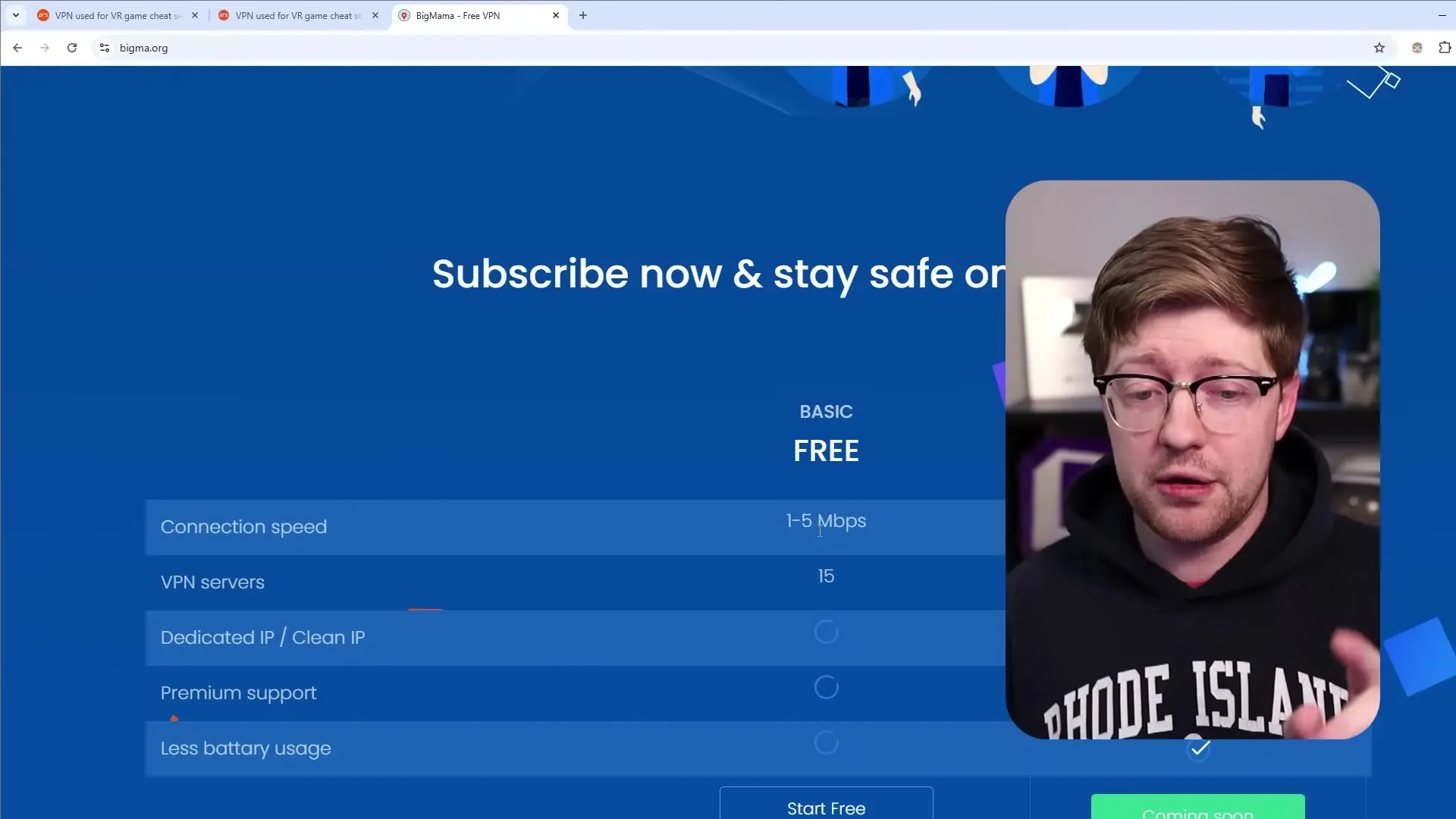
Upon investigation, security researchers discovered that Big Mama VPN was actually enrolling users in a peer-to-peer network that sold access to their residential IP addresses. In essence, when users installed this VPN, they were unwittingly allowing their devices to become proxy servers through which others could route internet traffic.
How the Deception Worked
What makes this case particularly troubling is how transparent yet deceptive the service was. On their website, Big Mama VPN openly stated: "The devices running Big Mama VPN are securely bound into an anonymous peer-to-peer Network. The network can be accessed by our commercial clients who use it for secure Global routing of their internet traffic." This disclosure was cleverly buried among legitimate-looking VPN features and marketing language.
The application used WireGuard VPN technology, which is known for being fast and reliable. This legitimate technology helped mask the questionable practices happening behind the scenes. When questioned about their practices, the company's responses contradicted information on their own website, claiming they log user activity to cooperate with law enforcement while simultaneously stating elsewhere that they "never snoop on any data that passes via the VPN network."
Security Implications for Developers
This incident highlights several critical warning signs that developers should be aware of when integrating third-party services or recommending solutions to users:
- Free services often come with hidden costs - in this case, users' network security was the price
- Legitimate-looking websites can mask malicious intentions
- Technical jargon and complex terms of service can hide concerning practices
- Security vulnerabilities can extend beyond the immediate application to affect entire networks
Security researchers from Cisco Talos reported seeing traffic from the Big Mama proxy being used in brute force attacks against corporate systems. Even more concerning, Trend Micro discovered a vulnerability in the VPN that could potentially allow proxy users to access the local networks of devices running the VPN - essentially opening up home networks to potential intrusions.
Developing Warning Systems: Standards for Software Security
For software developers, this case underscores the importance of implementing proper security standards and developing warning systems within applications. When creating software that might connect to external services, consider implementing these safeguards:
- Implement thorough vetting processes for third-party integrations
- Create clear software update warning systems that alert users to potential security risks
- Develop software-defined visibility (SDV) into network connections your application makes
- Establish software development verification processes that check for security vulnerabilities
- Design user-friendly warnings that clearly communicate risks without technical jargon
The Broader Implications for Network Security
This incident demonstrates a fundamental truth about security: you can't simply transfer trust from one entity to another without verification. Many users turn to VPNs because they don't trust their ISP, but then place blind trust in VPN providers who may have even more questionable practices.
For developers, this means adopting a zero-trust approach to security architecture. Never assume that a service is secure simply because it claims to be or appears legitimate. Always verify, test, and implement multiple layers of protection.
Best Practices for Software Development Security
To avoid falling victim to similar security pitfalls in your development projects, consider these best practices:
- Always read the fine print when integrating third-party services
- Implement proper network security monitoring in applications that connect to the internet
- Consider the entire security chain, not just individual components
- Educate users about potential risks in clear, understandable language
- Regularly audit your application's network connections and data handling practices
- Stay informed about emerging security threats and vulnerabilities
Conclusion: Trust But Verify
The Big Mama VPN incident serves as a powerful reminder that in software development, security cannot be an afterthought. Free services often come with hidden costs, and what appears to be a simple utility can potentially compromise entire networks.
As developers, we have a responsibility to maintain high security standards and to implement proper warning systems that protect our users. By staying vigilant and applying rigorous security practices, we can help prevent similar incidents and build more trustworthy software ecosystems.
Remember: when it comes to security, if you're not paying for the product, you might be the product - or worse, your network might be the product being sold to others without your knowledge.
Let's Watch!
The Dangerous Truth About Free VPNs: Security Warning for Developers
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence