
In an alarming security discovery, researchers have uncovered a technique that allows anyone with $20 and basic technical knowledge to gain control of thousands of compromised systems worldwide. This vulnerability class, centered around expired domains with traffic, represents a significant but underappreciated threat to organizations globally—including government networks.
Backdooring the Backdoors: The Expired Domain Vulnerability
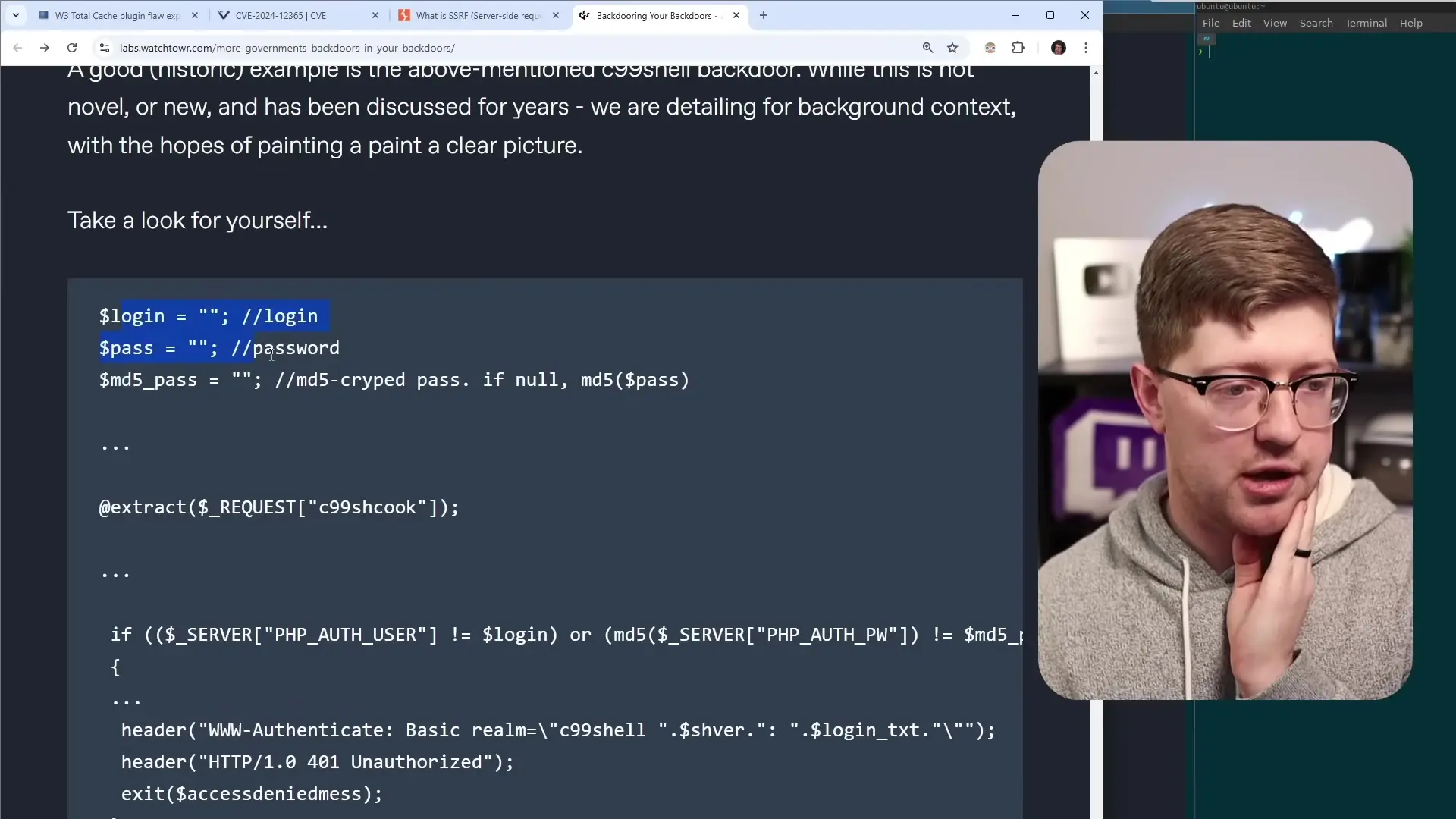
The technique, described by security researchers as "backdooring your backdoors," involves purchasing expired domains that were previously used in malware command and control (C2) infrastructure. When these domains expire, the malicious implants already deployed on victim systems continue attempting to call home to these addresses. By purchasing these expired domains, researchers effectively hijacked the communication channel between compromised systems and their original attackers.
This approach allows for what researchers call "mass hacking on autopilot"—gaining access to systems without having to identify vulnerabilities, develop exploits, or perform initial compromises. Instead, they simply inherit access from the original attackers who failed to properly decommission their infrastructure.
The Scale of the Problem: 4,000+ Compromised Systems and Counting
The research team, which documented their findings in detail, discovered over 4,000 unique and live backdoors connecting to domains they had purchased. These compromised systems spanned multiple sectors and countries, including:
- Government networks in Bangladesh, China, and Nigeria
- Universities and higher education institutions across Thailand, China, South Korea, and other countries
- Numerous private sector organizations
The researchers collected over 300 megabytes of logs from these compromised systems—a substantial amount of data that continues to grow as more systems connect to the domains they control.
Why Expired Domains Present a Unique Security Challenge
This vulnerability highlights a fundamental security issue: attackers often neglect proper cleanup after achieving their objectives. When hackers compromise systems, they typically focus on immediate goals—data exfiltration, credential theft, or establishing persistence. Once these goals are accomplished, they may abandon their infrastructure without properly decommissioning it.
Several factors contribute to this problem:
- Domain registrations expire if not renewed, creating opportunities for takeover
- Malware and backdoors often contain hardcoded domain names that continue attempting connections
- Organizations frequently fail to detect and remove all components of an intrusion
- Attackers rarely implement proper security measures in their own infrastructure
Platforms like expireddomains.net make it easy for anyone to identify and purchase recently expired domains, potentially including those previously used in malicious campaigns.
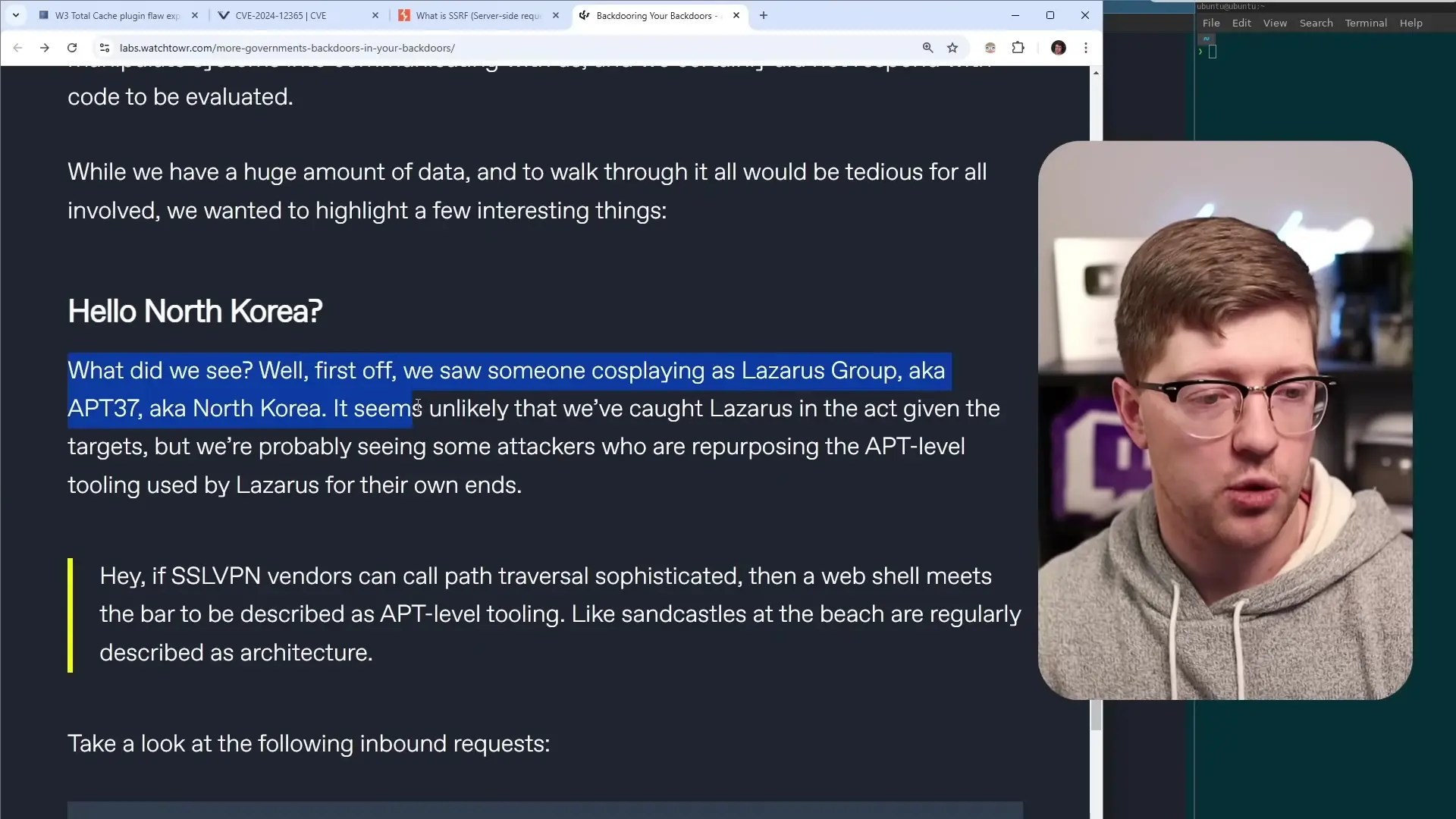
The Broader Impact on Internet Security
This research has already led to significant changes in internet security practices. Following a related study on TLS certificate validation, Google petitioned the CA/Browser Forum to eliminate the use of WHOIS for ownership validation when issuing certificates. This highlights how exploiting abandoned infrastructure can drive important security improvements.
Responsible Research Practices
It's worth noting that the researchers conducted their work ethically. They intentionally obscured compromised host names in their published findings to ensure their research didn't put any systems at additional risk. This approach to responsible disclosure is critical when dealing with active security vulnerabilities.
Protecting Against Expired Domain Attacks
Organizations can take several steps to protect themselves against these types of attacks:
- Implement robust network monitoring to detect and block unusual outbound connections
- Regularly scan systems for malware and unauthorized software
- Use DNS filtering services to block connections to known malicious domains
- Maintain an inventory of legitimate domains used by your organization and ensure they don't expire
- Implement a security incident response plan that includes complete removal of all malware components
The Human Element in Cybersecurity
Perhaps the most important takeaway from this research is the reminder that attackers are human too. Even sophisticated threat actors make mistakes, leaving behind infrastructure that can be commandeered by others. This human element creates opportunities for defenders but also highlights the importance of thorough security practices.
As one security researcher noted, "there is a general common belief, backed up with a significant amount of evidence, that hackers are in general pretty bad at securing networks." This observation underscores why expired domains with traffic represent such a significant vulnerability—they exploit the human tendency to focus on immediate objectives rather than proper cleanup.
Conclusion: The $20 Security Lesson
The ability to gain access to thousands of compromised systems for the price of a domain registration—roughly $20—highlights a critical but often overlooked aspect of cybersecurity. Organizations must not only defend against initial compromise but also ensure that any successful breaches are fully remediated.
For security professionals, this research serves as a reminder to think holistically about security—considering not just how to prevent attacks, but how to ensure complete cleanup after incidents. And for attackers, it's a stark warning that their own infrastructure may become their greatest vulnerability.
As we continue to see the exploitation of expired domains with traffic and abandoned infrastructure, organizations must adapt their security practices to address this persistent threat vector.
Let's Watch!
The $20 Threat: How Expired Domains Enable Massive Security Backdoors
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence