
In 1997, the U.S. National Institute of Standards and Technology (NIST) launched a global search for what would become the Advanced Encryption Standard (AES). This wasn't just another cryptographic competition—it was a quest to establish the foundation of digital security for decades to come. After years of rigorous evaluation of 15 submitted algorithms, one emerged victorious: Rijndael. Today, this algorithm—now known simply as AES—secures everything from your hard drives to internet communications, with dedicated hardware support in most modern processors.
Encryption Fundamentals: The Building Blocks
Before diving into AES implementation specifics, we need to understand what encryption actually does. At its core, encryption transforms plaintext (original data) into ciphertext (encoded data) using a secret key. The process should ensure that without the key, the ciphertext remains meaningless to anyone intercepting it.
In computing terms, plaintext, ciphertext, and keys are all just sequences of bits (zeros and ones). The simplest encryption approach is the exclusive OR (XOR) operation, where each bit of plaintext is combined with the corresponding bit of the key.
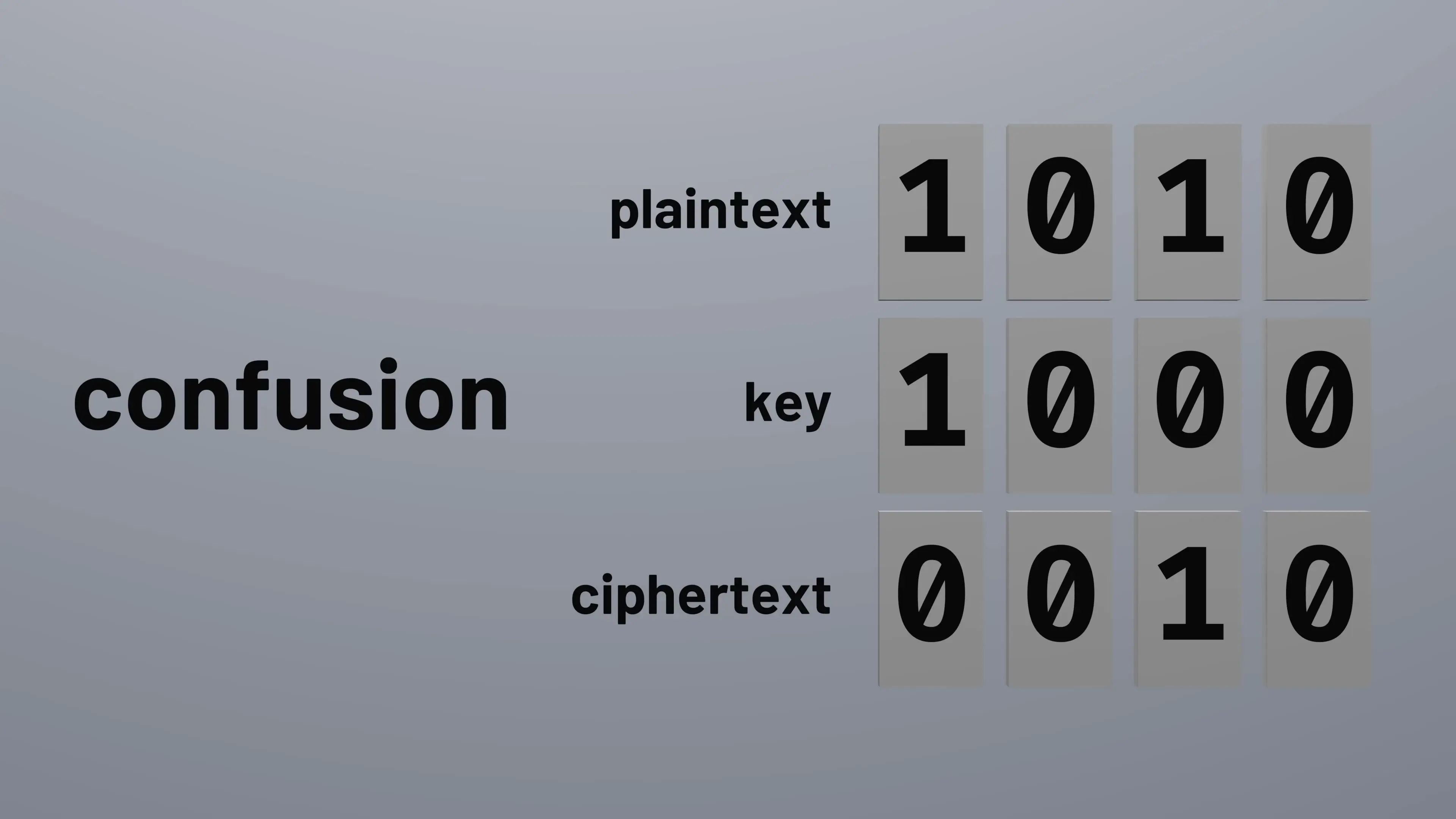
When the key bit is 1, the plaintext bit flips (0 becomes 1, 1 becomes 0). When the key bit is 0, the plaintext bit remains unchanged. This simple operation, known as a one-time pad when used with a truly random key of the same length as the plaintext, is theoretically unbreakable—but with a critical limitation: the key can never be reused.
Confusion and Diffusion: The Twin Pillars of Modern Encryption
Claude Shannon, the father of information theory, identified two essential properties for strong encryption algorithms in the 1940s: confusion and diffusion. These principles remain fundamental to AES algorithm implementation today.
- Confusion: Complicates the relationship between the key and the ciphertext. Each bit of the ciphertext should depend on multiple bits of the key, making analysis difficult.
- Diffusion: Spreads the statistical patterns of the plaintext across the entire ciphertext. Ideally, changing just one bit of plaintext should change approximately half the bits in the ciphertext.
Our simple XOR cipher fails at both properties: it lacks confusion because each ciphertext bit depends on exactly one key bit, and it lacks diffusion because changing one plaintext bit affects only the corresponding ciphertext bit. A secure algorithm like AES needs to excel at both.
Inside AES: Block-Based Encryption Architecture
AES is a block cipher, meaning it processes fixed-size blocks of data rather than individual bits or bytes. Specifically, AES operates on 128-bit (16-byte) blocks, arranging this data in a 4×4 grid called the "state."

The encryption process involves multiple rounds of transformations on this state, with each round using a different round key derived from the original key through a key expansion process. AES supports three key lengths—128, 192, and 256 bits—with longer keys providing more security through additional transformation rounds.
Key Expansion: Creating Round Keys
One of the first steps in AES implementation is key expansion. Rather than using the original key directly for all operations, AES derives multiple round keys from it. This expansion process ensures that each bit of the expanded keys depends on multiple bits of the original key, enhancing confusion.
The key expansion algorithm uses a combination of operations including byte rotations, substitutions, and XOR operations with constant values to generate unique round keys that appear unrelated to each other but are all deterministically derived from the original key.
The AES Encryption Process: Transformation Rounds
AES encryption consists of multiple rounds of transformations. Each round (except the final one) includes four distinct operations:
- SubBytes: A non-linear substitution where each byte is replaced with another according to a predefined substitution table (S-box)
- ShiftRows: A transposition step where each row of the state is shifted cyclically a certain number of steps
- MixColumns: A mixing operation which operates on the columns of the state, combining the four bytes in each column using a linear transformation
- AddRoundKey: Each byte of the state is combined with a byte of the round key using the XOR operation
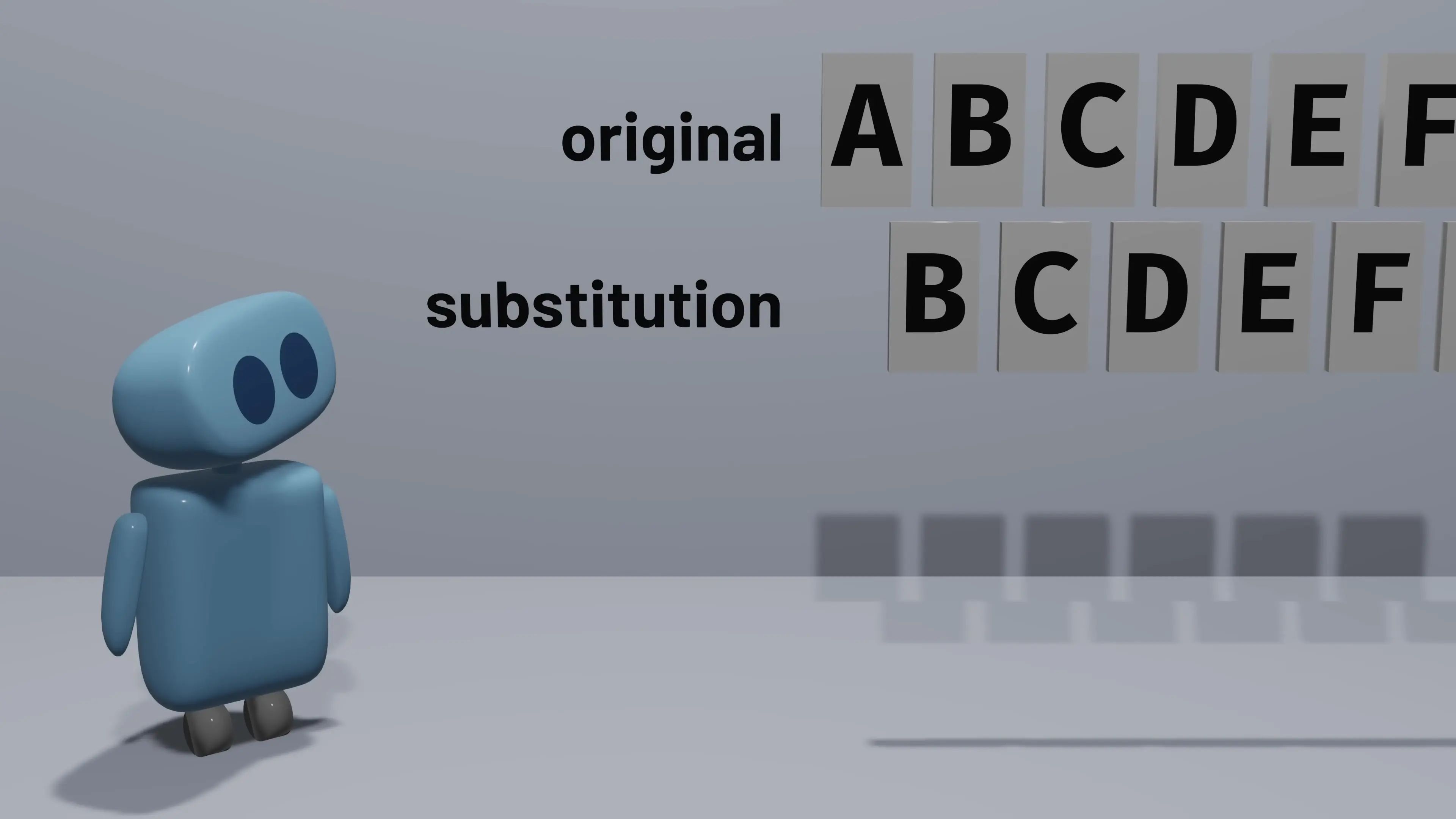
The SubBytes operation provides confusion by replacing each byte with another according to a carefully designed substitution box (S-box). This substitution is non-linear and designed to resist linear and differential cryptanalysis.
# Simple example of AES SubBytes operation in Python
import pyaes
def demonstrate_subbytes(input_byte):
# The AES S-box for SubBytes transformation
s_box = pyaes.aes._sbox
# Apply S-box substitution
substituted = s_box[input_byte]
print(f"Original byte: {input_byte} (0x{input_byte:02x})")
print(f"Substituted byte: {substituted} (0x{substituted:02x})")
# Example with byte value 149
demonstrate_subbytes(149)ShiftRows and MixColumns provide diffusion by ensuring that changes to one byte affect multiple bytes in subsequent rounds. The ShiftRows operation cyclically shifts the bytes in each row, while MixColumns applies a mathematical transformation to mix the bytes in each column.
AES Implementation Approaches
AES can be implemented in various ways, from software implementations in languages like Python and Java to hardware implementations in FPGAs and dedicated circuits. Each approach offers different trade-offs between speed, security, and resource usage.
- Software Implementation: Flexible and portable, suitable for most applications. Python AES implementation is common for educational purposes and non-performance-critical applications.
- Hardware Implementation: FPGA-based hardware implementation of AES Rijndael algorithm for encryption and decryption offers significant performance advantages, especially for high-throughput applications.
- Hybrid Approaches: Modern CPUs include AES-NI (Advanced Encryption Standard New Instructions) that accelerate AES operations while maintaining the flexibility of software implementation.
# Basic AES encryption example in Python using the PyCryptodome library
from Crypto.Cipher import AES
from Crypto.Random import get_random_bytes
from Crypto.Util.Padding import pad, unpad
# Generate a random 16-byte (128-bit) key
key = get_random_bytes(16)
# Create data to encrypt (must be multiple of 16 bytes)
data = b"AES encryption demonstration"
# Create cipher object and encrypt the data
cipher = AES.new(key, AES.MODE_CBC)
# Pad the data to ensure it's a multiple of 16 bytes
ct_bytes = cipher.encrypt(pad(data, AES.block_size))
# Initialization vector needed for decryption
iv = cipher.iv
print(f"Original data: {data}")
print(f"Encrypted data: {ct_bytes.hex()}")
# Decryption
cipher = AES.new(key, AES.MODE_CBC, iv)
pt = unpad(cipher.decrypt(ct_bytes), AES.block_size)
print(f"Decrypted data: {pt}")AES in Modern Security Applications
AES has become the backbone of modern cryptographic security, used in countless applications:
- Securing internet traffic through protocols like TLS/SSL
- Full-disk encryption for data storage protection
- Secure communications in messaging applications
- VPN connections for secure remote access
- Wireless network security (WPA2/WPA3)
- Smart card and secure element applications
The algorithm's strength comes from its careful design incorporating both confusion and diffusion principles, along with its resistance to known cryptanalytic attacks. Even after more than two decades, AES remains secure against practical attacks when properly implemented.
Conclusion: The Enduring Legacy of AES
The Advanced Encryption Standard represents one of the most successful outcomes of open cryptographic development. Through careful design focusing on the principles of confusion and diffusion, AES provides strong security while maintaining reasonable performance across diverse implementations.
Understanding how AES works—from its block structure to its transformation rounds—provides valuable insights into modern cryptographic design. Whether implemented in Python for educational purposes or in hardware for high-performance applications, AES continues to protect our digital world with remarkable effectiveness.
As computing power increases and new cryptanalytic techniques emerge, AES implementations with longer key lengths (AES-192 and AES-256) provide a margin of security that should protect sensitive information well into the future.
Let's Watch!
How AES Encryption Works: From One-Time Pads to Modern Security
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence