
A concerning trend is emerging in the gaming industry as major publishers deploy increasingly invasive kernel-level anti-cheat software. This development has reached a critical point where these security systems are now actively conflicting with each other, as evidenced by EA's Battlefield 6 beta refusing to install on systems with Riot Games' Valorant already present.
Understanding Kernel-Level Anti-Cheat Software
To understand the gravity of this situation, we need to examine how computers operate at different privilege levels. Modern operating systems function in two primary execution modes: kernel mode and user mode. The kernel represents the highest privilege level where the operating system itself runs, while user mode is where regular applications operate with limited system access.
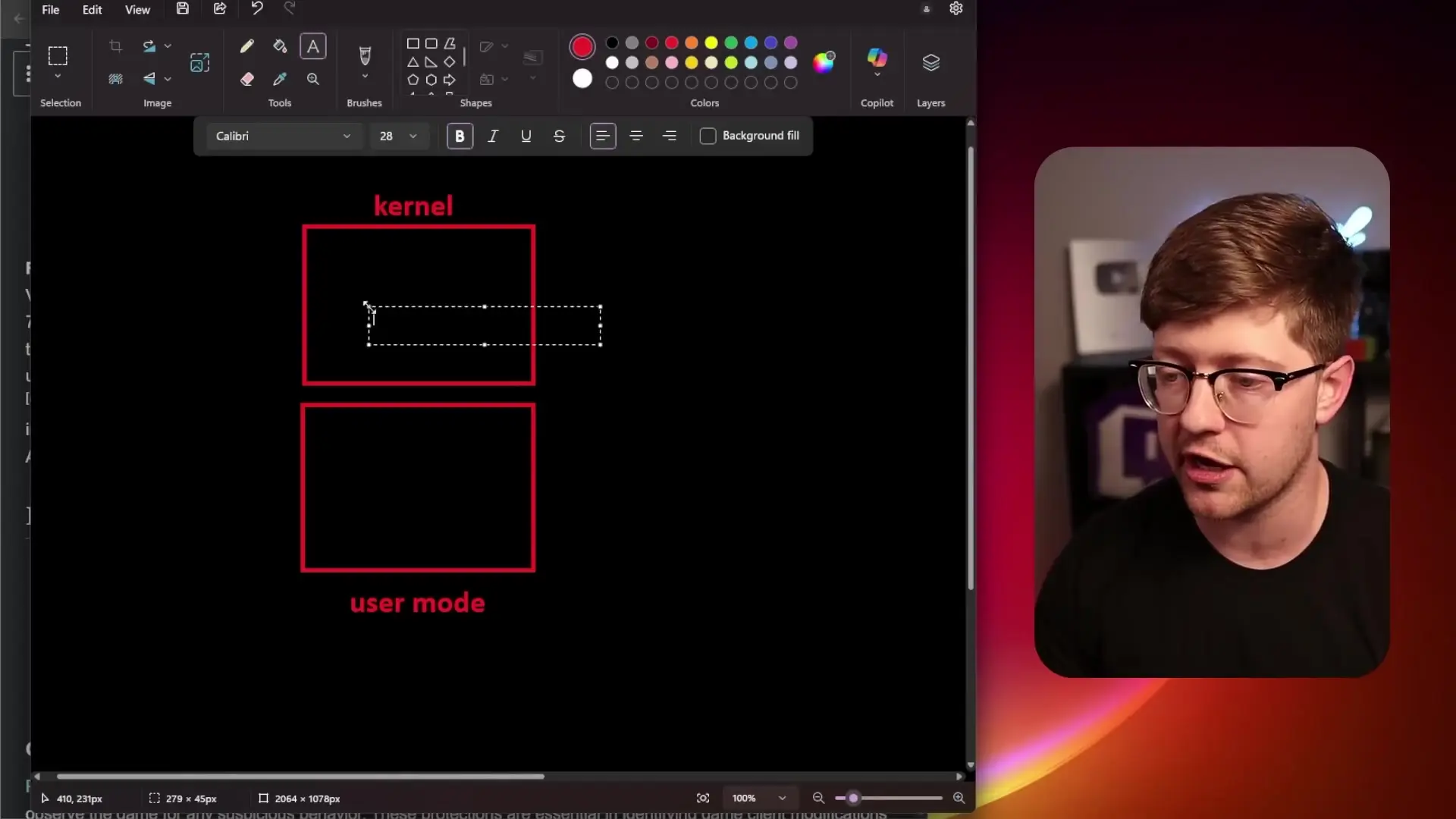
Traditionally, game cheating software operates at the user level, allowing it to read and manipulate memory from other user-level applications like games. This enables cheaters to access information that should be hidden, such as enemy positions behind walls or other obstructions, providing unfair advantages.
To counter these cheating methods, game publishers have escalated their anti-cheat technology to the kernel level, giving them privileged access to monitor all running processes and detect potential cheating software. While this approach may be effective against cheaters, it introduces significant security and privacy concerns for all players.
The Battlefield vs. Valorant Conflict: A Symptom of a Larger Problem
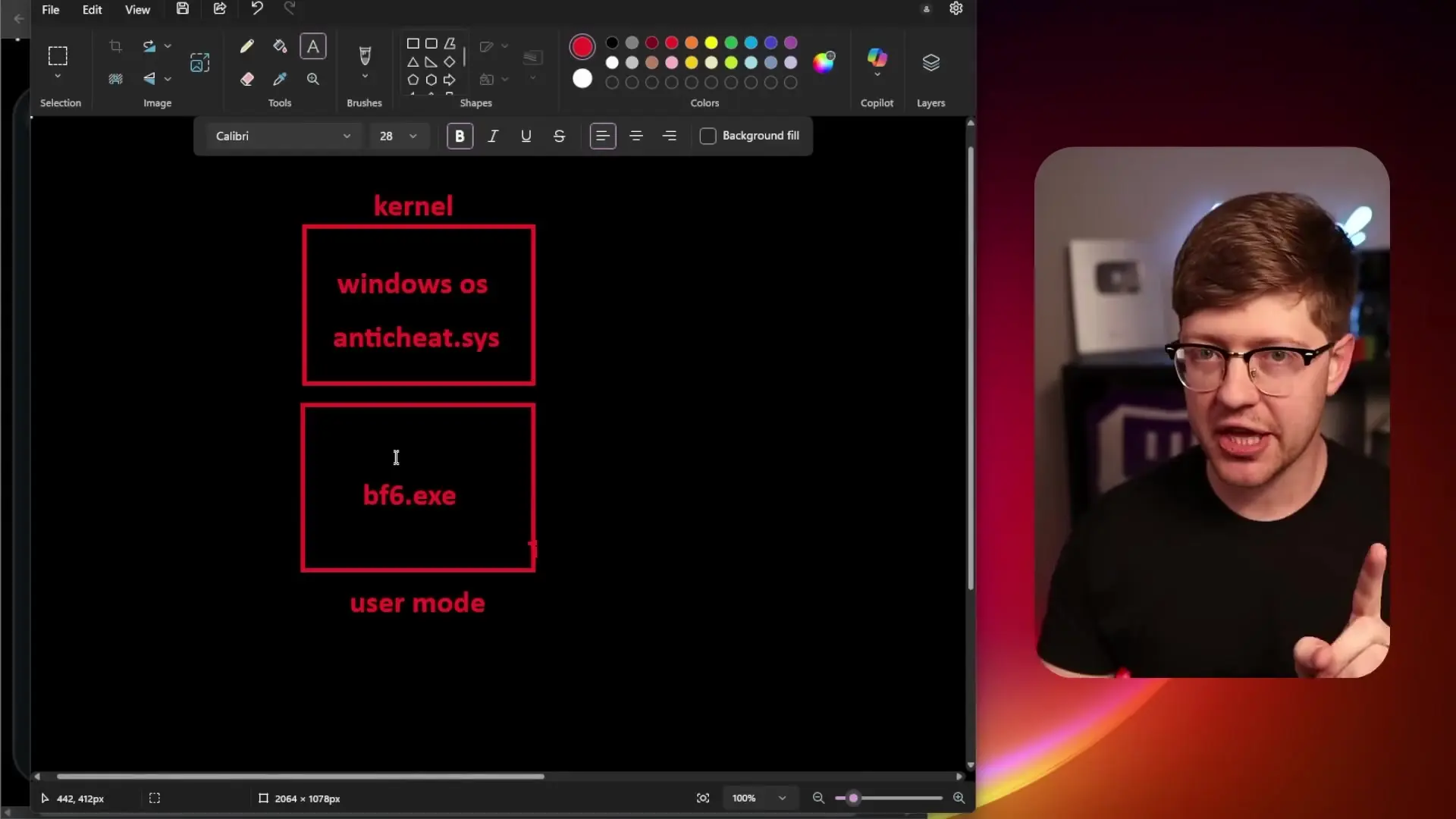
The recent incident where Battlefield 6 beta refused to install on systems with Valorant already present highlights a growing compatibility crisis. When attempting to install the Battlefield beta, affected users received an error message stating: "Security violation: The application has failed to start due to a general software incompatibility. Please uninstall the following conflicting software: Valorant."
This incompatibility stems from the particularly invasive nature of Riot's Vanguard anti-cheat system. Unlike most anti-cheat software that only runs when the associated game is active, Vanguard loads as a boot driver, meaning it starts when your computer boots up and continues running until shutdown, regardless of whether you're playing Valorant or not.
The Technical Invasiveness of Vanguard
Vanguard's approach to anti-cheat is exceptionally aggressive from a technical standpoint. It inserts what developers call "hooks" into system calls of the operating system. In practical terms, this means Vanguard is effectively impersonating core Windows functions.
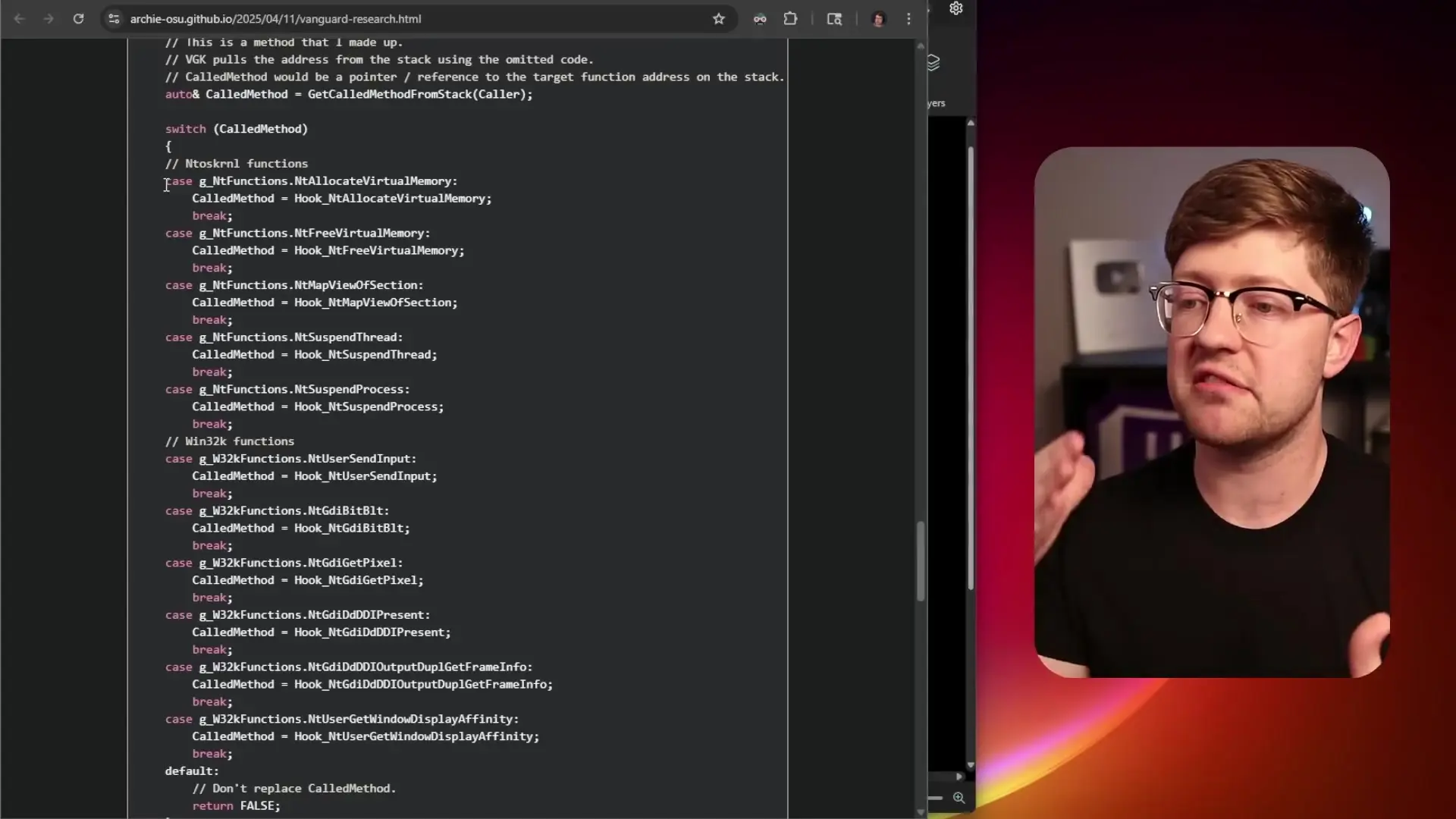
When Vanguard is active, basic system operations like memory allocation, thread management, and process control are intercepted by Riot's software before reaching the actual Windows kernel. Additionally, Vanguard employs sophisticated memory protection techniques that swap out memory pages in real-time if someone attempts to inspect them, making it nearly impossible to analyze its behavior.
The Serious Security and Privacy Implications
The proliferation of kernel-level anti-cheat software raises two major categories of concerns:
- Privacy violations: With kernel-level access, these programs can potentially monitor all activities on your computer, not just gaming-related processes. This could include sensitive personal information or activities unrelated to gaming.
- Security vulnerabilities: Code running at the kernel level can introduce critical vulnerabilities that affect the entire system. A bug or exploit in anti-cheat software could lead to system crashes or provide attack vectors for malware.
There have already been documented cases of ransomware groups exploiting vulnerabilities in kernel-level anti-cheat software. For example, certain malware has leveraged vulnerabilities in gaming anti-cheat systems to disable antivirus protection, highlighting how these privileged programs can become security liabilities.
The Kernel Territory War
As each major publisher develops their own kernel-level anti-cheat solution—Riot with Vanguard, EA with Easy Anti-Cheat, Epic with their own system—we're witnessing what amounts to a territorial war inside the Windows kernel. Each anti-cheat system uses different hook points and techniques that can potentially interfere with one another.
This situation is creating a fragmented gaming landscape where certain games cannot coexist on the same system. The logical conclusion of this trend could be that gamers might need separate computers for different game publishers—one for Riot games, another for EA titles, and so on—which represents an absurd and costly outcome for consumers.
The CrowdStrike Incident: A Warning Sign
The risks of kernel-level software were dramatically illustrated by the CrowdStrike incident in July 2024. A vulnerability in CrowdStrike's Falcon EDR (Endpoint Detection and Response) system—another kernel-level security product—caused widespread system crashes globally, disrupting businesses and services worldwide for approximately 12 hours.
This incident demonstrates how software running at the kernel level can have catastrophic consequences when it malfunctions. The gaming industry's rush to implement kernel-level anti-cheat systems could be setting the stage for similar widespread disruptions.
Potential Solutions and Future Outlook
Microsoft has recognized the growing risks associated with kernel-level software and is working on solutions to move security products out of the kernel. They're developing APIs that would allow anti-virus and potentially anti-cheat software to perform their functions without requiring kernel-level access.
For gamers concerned about these issues, there are limited options currently available:
- Use separate computers for gaming and personal activities
- Selectively install games to avoid conflicting anti-cheat systems
- Monitor and participate in community discussions about anti-cheat practices
- Support game developers who implement less invasive anti-cheat solutions
The Future of Software Development and Security
The current situation with kernel-level anti-cheat software highlights broader challenges in the future of software development. As software becomes more integrated into our daily lives, the balance between security, functionality, and privacy becomes increasingly complex.
For software developers and engineers, this situation presents important lessons about the responsibilities that come with privileged access to users' systems. The gaming industry's anti-cheat arms race demonstrates how competitive pressures can lead to technical decisions that potentially compromise user security and privacy.
Conclusion
The kernel-level anti-cheat war represents a troubling trend in gaming software development. While the goal of preventing cheating is understandable, the methods being employed introduce significant risks to system stability, security, and user privacy. As the industry continues to evolve, finding a balance between effective anti-cheat measures and responsible software practices will be crucial for both developers and gamers.
Until more balanced solutions emerge, gamers should remain aware of what software they're installing and the potential risks associated with kernel-level programs that have complete access to their systems. The future of gaming shouldn't require sacrificing security and privacy in the name of fair play.
Let's Watch!
Kernel-Level Anti-Cheat Wars: The Hidden Security Crisis for Gamers
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence