Reverse engineering is one of the most powerful skills you can develop whether you're a cybersecurity analyst or a programmer looking to deepen your understanding of how software works. In this guide, we'll walk through solving the Flag Casino challenge from Hack the Box, demonstrating practical reverse engineering techniques that will help you understand the inner workings of binary files.
Understanding Reverse Engineering
Reverse engineering is the art of taking compiled computer code and figuring out what the original author intended. While reverse engineering real software has ethical and legal implications, Capture The Flag (CTF) challenges provide a perfect legal playground for developing these skills. These challenges are specifically designed to be reverse engineered, allowing you to practice without legal concerns.
Our goal with the Flag Casino challenge is to extract a hidden flag from a binary that doesn't readily reveal its secrets. The flag earns us points in the CTF competition, but more importantly, solving the challenge teaches valuable reverse engineering skills.
Initial Analysis of the Binary
When approaching any reverse engineering challenge, the first step is to understand what type of file we're dealing with. Let's examine our target file:
$ file casino
casino: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=85b64ad08b1d4e890e7192b9aae7b3fd6bc02d4c, not strippedThis tells us we're working with a 64-bit ELF binary, compiled for Linux systems. The "not stripped" part is good news—it means the binary might contain debug symbols that make our analysis easier.
Next, let's use the 'strings' command to extract readable text from the binary:
$ strings casinoThe strings output reveals several interesting function names: exit, srand, puts, printf, and scanf. This gives us our first clue: the program uses randomness (srand) and takes user input (scanf). For a casino-themed challenge, this makes perfect sense.
Using IDA Pro for Disassembly
To get a deeper understanding of the binary, we need to disassemble it. IDA Pro is one of the most powerful open source reverse engineering tools available for this purpose.
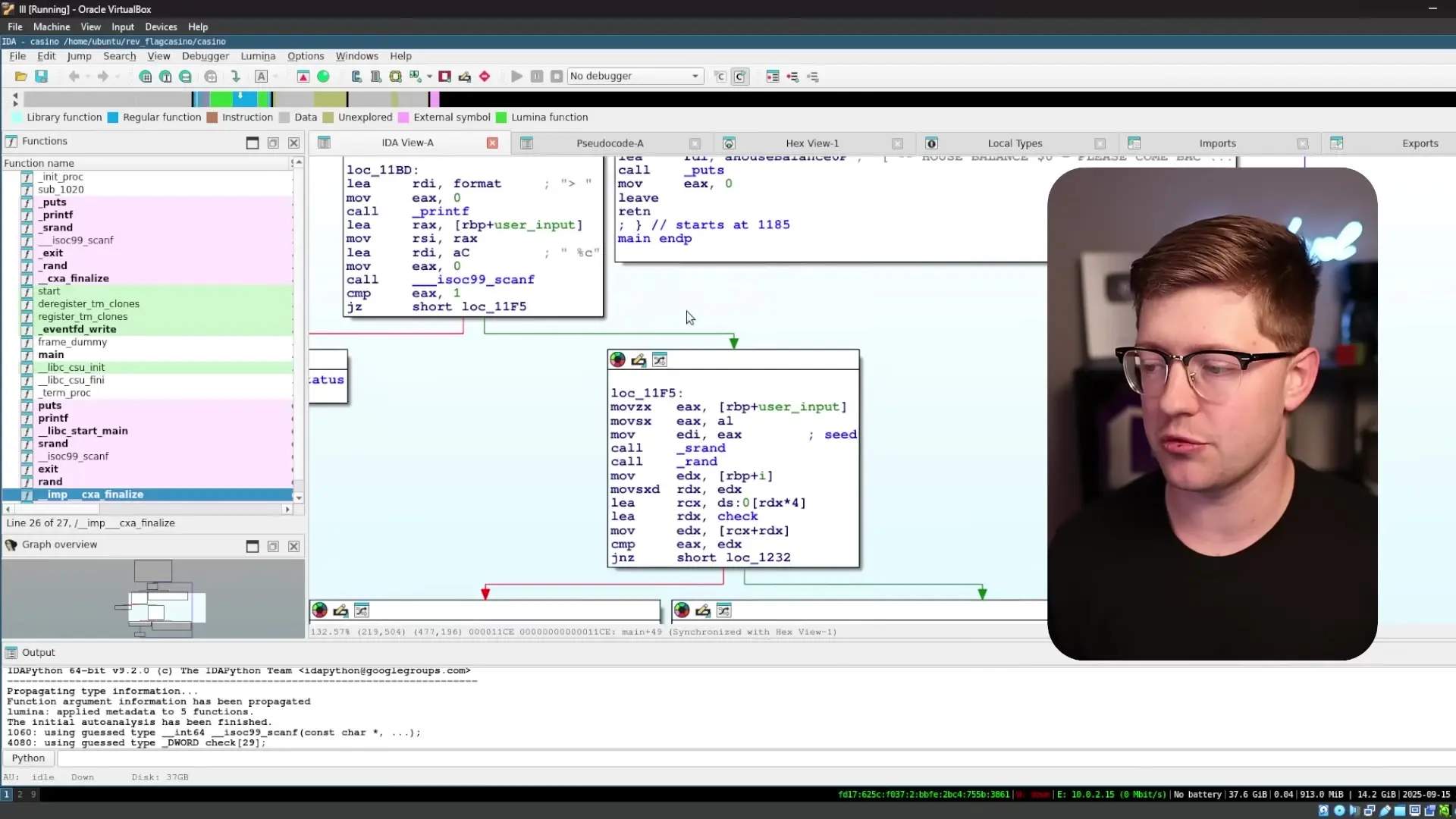
After loading the binary into IDA Pro, we can see the disassembled code. The program starts by displaying a welcome message, then asks the user to place bets. What's particularly interesting is how it handles the user input.
IDA's decompiler feature gives us a C-like representation of the assembly code, making it much easier to understand what's happening. Looking at the decompiled code, we can see that the program:
- Takes a character input from the user
- Uses that character to seed the random number generator with srand()
- Calls rand() to generate a number
- Compares that random number against a predefined value in a check array
- If they match, it allows you to continue; if not, it activates a security system and exits
Understanding the Randomness Vulnerability
The key insight here is that the program's security relies on the randomness of rand(), but rand() is deterministic when seeded with the same value. This is a classic example of a predictable randomness vulnerability.
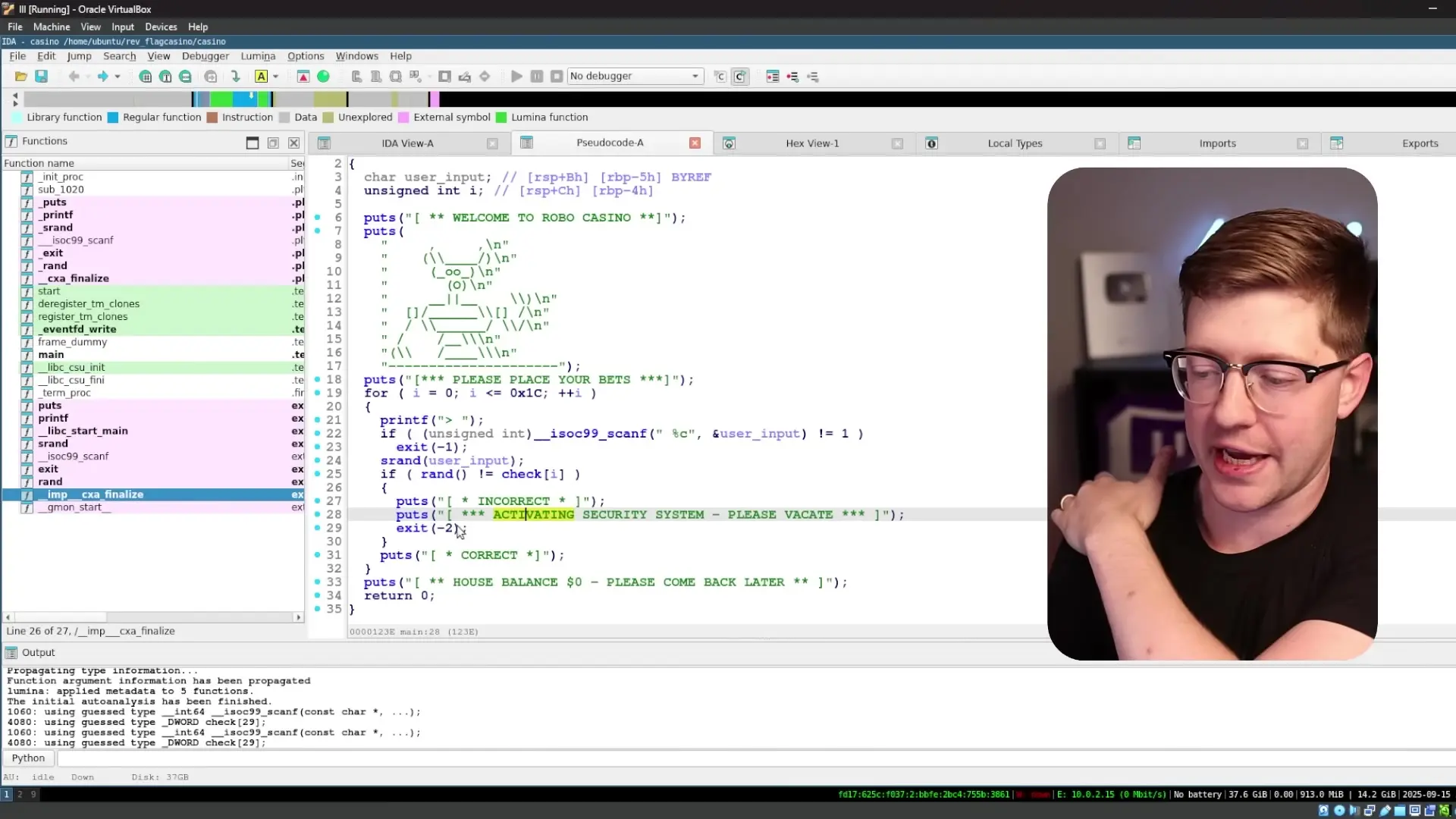
Let's look at the man page for rand() and srand() to understand how they work:
The rand() function returns a pseudo-random integer in the range from 0 to RAND_MAX inclusive.
The srand() function sets its argument as the seed for a new sequence of pseudo-random integers to be returned by rand().This means that if we know what value is expected from rand(), we can work backward to determine what seed value (user input) would generate that random number.
Exploiting the Vulnerability
Since our input is a single character (a byte), there are only 256 possible values we can input. We can create a lookup table that maps each possible input value to the resulting random number:
#include <stdio.h>
#include <stdlib.h>
int main() {
for (int i = 0; i < 256; i++) {
srand(i);
printf("%d:%08x\n", i, rand());
}
return 0;
}This C program creates a lookup table showing what random number is generated for each possible input value from 0 to 255.
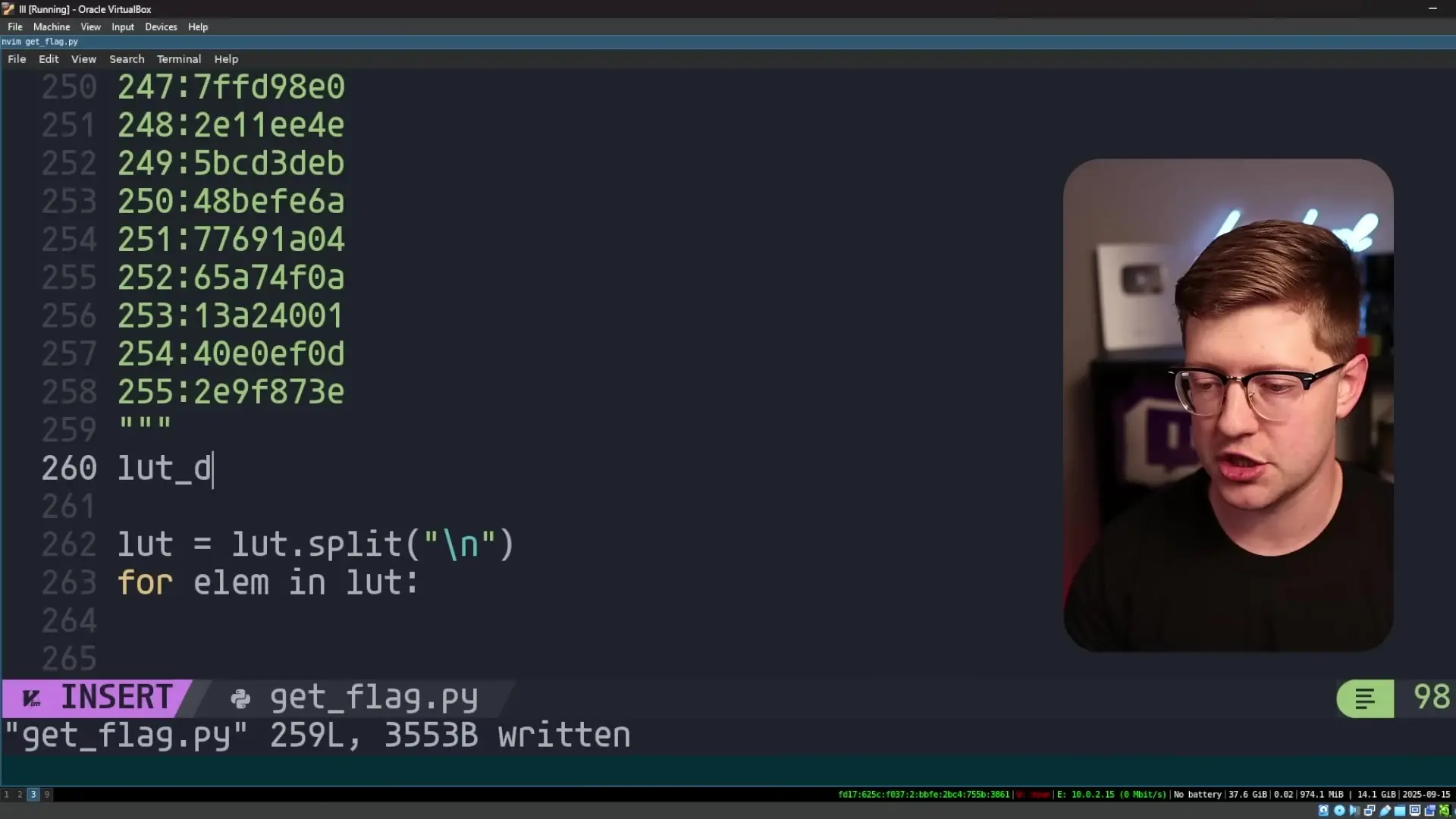
After compiling and running this program, we can look up the expected values from the check array in our table. For example, if the first value in the check array is 0x244B28BE, we can find which input value generates that random number.
In our case, the input value 72 (the ASCII code for 'H') generates the expected first random number. We can verify this by running the original program and inputting 'H' as our first bet.
Extracting the Complete Flag
To extract the complete flag, we need to identify all the values in the check array and find the corresponding input characters for each one. We can use IDA's Python scripting capabilities to extract the check array data:
# Extract check array data using IDAPython
data = get_bytes(0x4080, 0x40F4 - 0x4080)
hex_data = data.hex()Then, we can write a Python script to process this data and map each check value to the corresponding input character using our lookup table:
# Create a dictionary mapping random values to input characters
lookup = {}
for i in range(256):
srand(i)
random_val = rand()
lookup[random_val] = i
# Process the check array and find the corresponding characters
flag = ""
for check_val in check_array:
if check_val in lookup:
flag += chr(lookup[check_val])
print(flag)Running this script would give us the complete flag, which is likely in the format HTB{...} since this is a Hack the Box challenge.
Key Takeaways from Reverse Engineering
This challenge demonstrates several important reverse engineering concepts:
- Understanding binary file formats and using tools like 'file' and 'strings' for initial analysis
- Using disassemblers like IDA Pro to convert machine code into readable assembly
- Recognizing common vulnerabilities such as predictable randomness
- Creating lookup tables to map inputs to outputs when brute-forcing is feasible
- Using scripting to automate the exploitation process
Conclusion
Reverse engineering is a powerful skill that helps you understand how software works at a fundamental level. Through challenges like Flag Casino, you can practice these skills in a legal and ethical environment. The techniques demonstrated in this walkthrough—using tools like IDA Pro, analyzing code flow, and exploiting vulnerabilities in randomness—are applicable to many real-world reverse engineering scenarios.
Whether you're interested in cybersecurity, software development, or just curious about how programs work under the hood, developing reverse engineering skills will deepen your understanding of computer systems and make you a more effective technologist.
Let's Watch!
Mastering Reverse Engineering: Hack the Box Casino Challenge Walkthrough
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence