
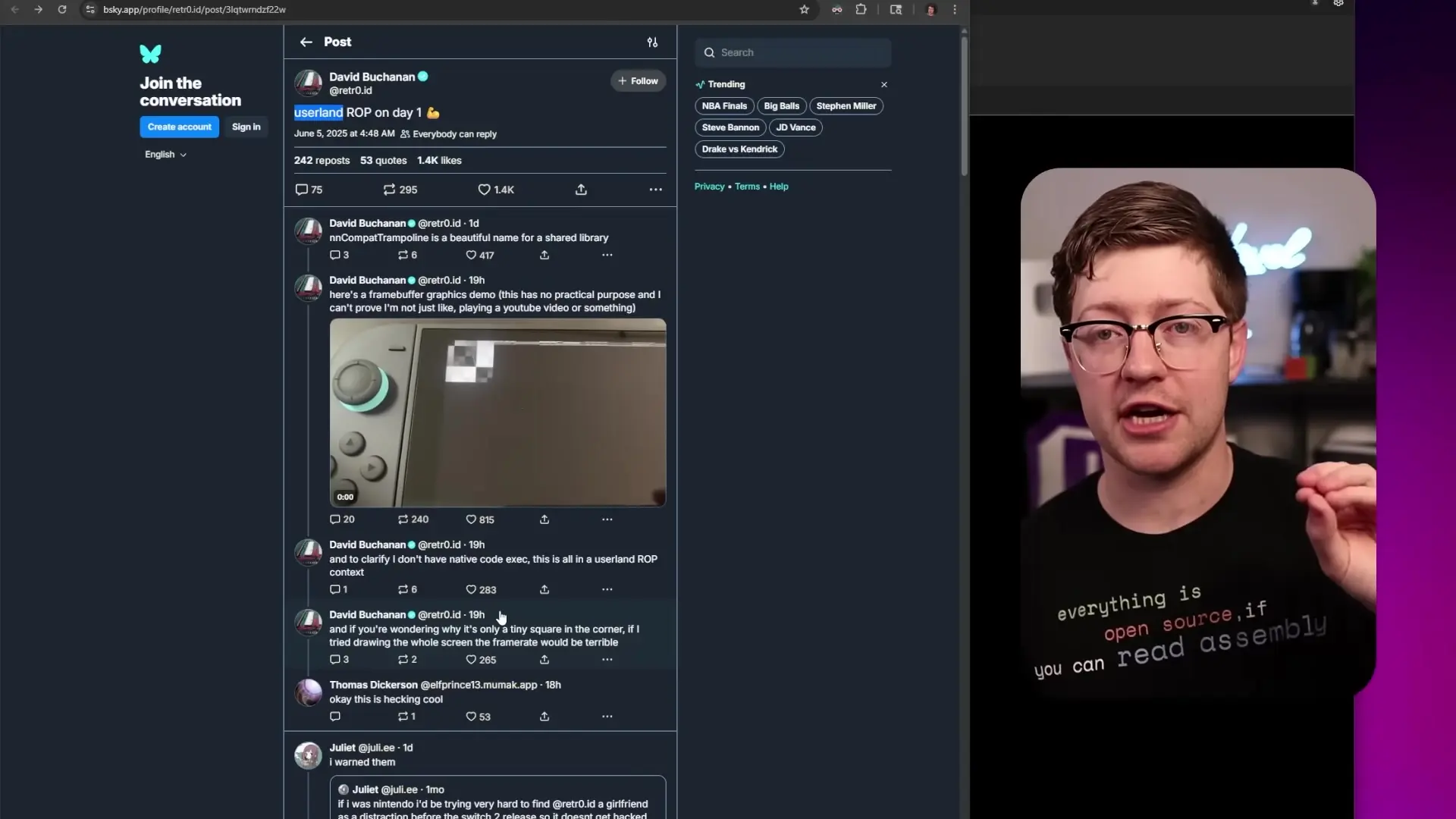
The gates of Nintendo's guarded kingdom are starting to collapse. Within just 48 hours of the Nintendo Switch 2's release, security researcher David Buchanan has already managed to execute the first successful exploit on the new gaming console, challenging recent claims that the system was 'unhackable'.
Buchanan announced his achievement on BlueSky, demonstrating what he called a 'userland ROP chain' that allows arbitrary writing to the console's frame buffer. While this doesn't constitute a full jailbreak, it represents a significant first step in compromising the system's security architecture.

Understanding the Exploit: What is a Userland ROP Chain?
To understand the significance of this exploit, we need to dive into some technical concepts. In modern computing security, code execution is typically restricted by protections like NX (Non-Executable) stacks, which prevent attackers from simply injecting and running their own code.
Return-Oriented Programming (ROP) is an advanced exploitation technique that bypasses these protections. Instead of injecting new code, ROP chains use existing code fragments (called 'gadgets') within the program that end with a return instruction. By controlling the return address on the stack, attackers can chain these gadgets together to create functional programs using code that already exists in the system.
// Simplified example of how security verification works
function didNintendoWriteTheFirmware() {
computeSignature = calculateSignature(firmware);
if (verifySignature(computeSignature) == false) {
return false; // Prevent unauthorized code from running
}
return true; // Allow Nintendo code to run
}The Security Architecture of Modern Gaming Consoles
Modern computing systems, including gaming consoles like the Switch 2, implement a hierarchical security model with multiple protection domains:
- Userland: Where applications and games run with limited privileges
- Kernel: The core of the operating system with elevated privileges
- Secure World (ARM TrustZone): A hardware-isolated environment for handling sensitive operations
Buchanan's exploit currently operates only in the userland domain, which means it has significant limitations. While he can manipulate the frame buffer to display custom graphics, he cannot yet modify the system's core functionality or run unauthorized software.
The Road to a Full Jailbreak: Challenges Ahead
For a complete jailbreak of the Nintendo Switch 2, security researchers would need to overcome multiple additional layers of protection:
- Find a vulnerability to escalate privileges from userland to kernel access
- Bypass TrustZone security to gain access to the secure world
- Potentially defeat hardware security modules (HSMs) that verify firmware signatures
- Overcome any fault injection detection mechanisms
These are significant challenges, especially as Nintendo has likely implemented lessons learned from vulnerabilities in the original Switch.
Fault Injection: The Hardware Attack Vector
Prior to the Switch 2's release, reports suggested that Nintendo had implemented protections against fault injection attacks—a sophisticated hardware-based exploitation technique.
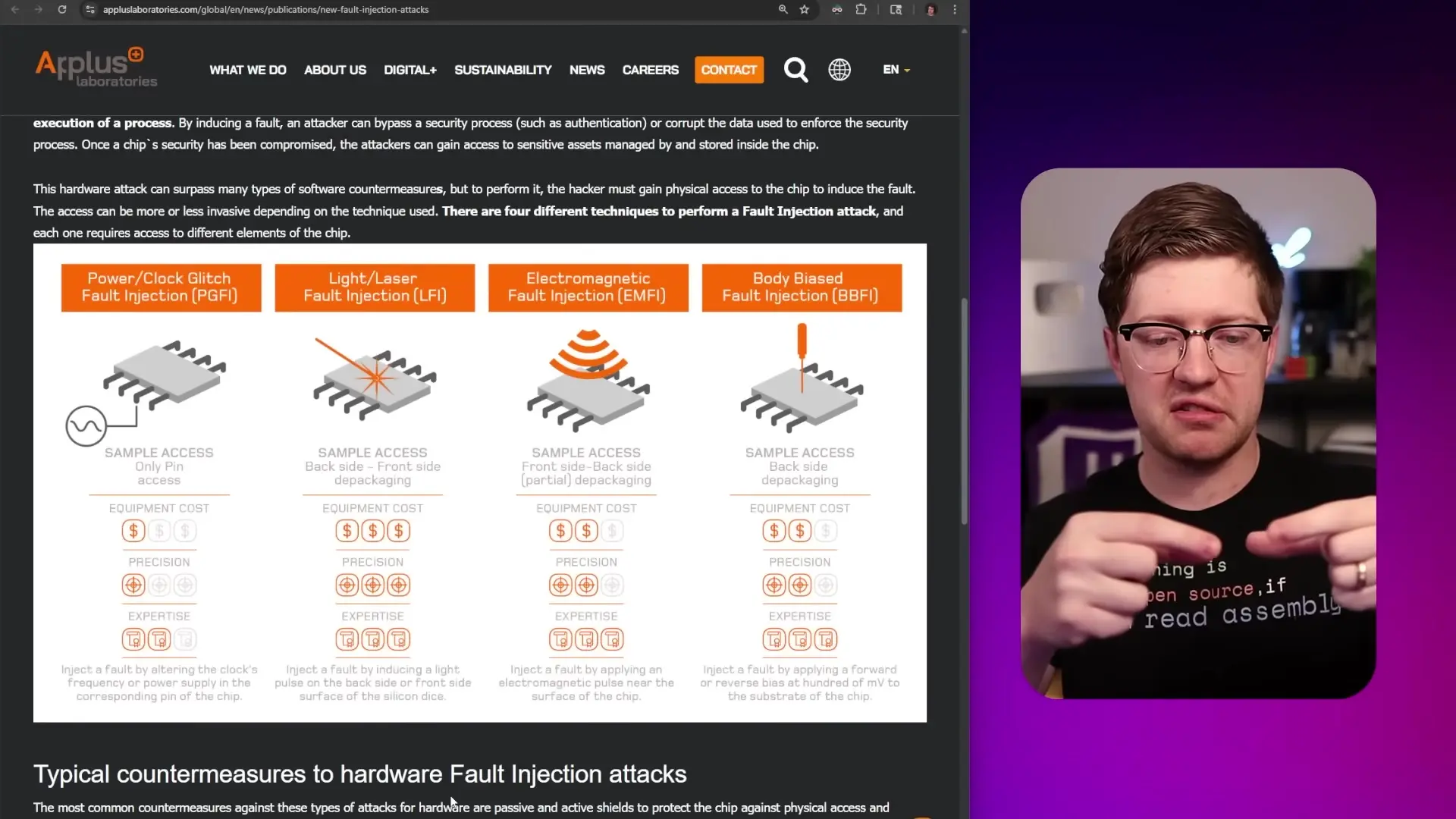
Fault injection involves physically manipulating hardware—using techniques like power glitching, electromagnetic pulses, or even laser attacks—to cause the processor to skip critical security instructions. For example, an attacker might use precisely timed laser pulses to make the processor skip the instruction that would reject unauthorized firmware.
The Switch 2 reportedly incorporates detection mechanisms that can identify such tampering attempts and brick the device in response, representing a significant deterrent to hardware-based attacks.
The Security Arms Race Continues
The quick discovery of an exploit in the Nintendo Switch 2 highlights the ongoing security arms race between console manufacturers and security researchers. Despite Nintendo's apparent confidence in their new security measures—with some reports even claiming the console was 'unhackable'—this early breach demonstrates that no system is impervious to determined analysis.
While the current exploit is limited in scope, it provides a foothold for further security research. The coming months will likely see continued efforts to probe the Switch 2's defenses, potentially leading to more comprehensive exploits.
Implications for Console Security
For manufacturers like Nintendo, these early exploits highlight the importance of continuous security updates and the limitations of claiming any system is 'unhackable.' For security researchers and enthusiasts, these developments represent the first steps in understanding the new console's architecture.
It's worth noting that while some pursue these exploits to enable unauthorized software or piracy, many security researchers operate under responsible disclosure principles, helping manufacturers identify and address vulnerabilities before they can be widely exploited.
Conclusion: The Beginning of a New Security Chapter
The discovery of a userland exploit within 48 hours of the Nintendo Switch 2's release marks just the beginning of what will likely be a long security saga. While Nintendo has clearly implemented more sophisticated protections than in previous generations, the fundamental principle of security research remains unchanged: given sufficient time and resources, determined researchers will find ways to circumvent even the most robust protections.
As this story develops, it will provide valuable insights not just for gaming enthusiasts, but for the broader field of embedded systems security, demonstrating both the ingenuity of security researchers and the challenges faced by hardware manufacturers in protecting their platforms.
Let's Watch!
Nintendo Switch 2 Security Breach: First Exploit Found Within 48 Hours
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence