
Memory corruption vulnerabilities have been the gateway for hackers to infiltrate systems for decades. Despite numerous security mitigations implemented over the years, attackers continue to find ways to exploit vulnerable software and inject malicious code. The fundamental problem? Pointers - those critical references that tell the CPU where to find data or which instruction to execute next.
The Persistent Threat of Memory Corruption
Security engineers have spent years developing mitigations to protect against memory corruption vulnerabilities. When hackers target software, they're often looking for ways to manipulate pointers - particularly the return pointer that tells the CPU where to go after a function completes execution, or data pointers that can be redirected to attacker-controlled memory.
Traditional memory protection mechanisms include stack canaries, address space layout randomization (ASLR), and data execution prevention (DEP). While these provide some protection, they all share a critical weakness: their secrets exist within the same privilege boundary as the code they're trying to protect.
Understanding the Limitations of Current Mitigations
Let's examine a simple vulnerable C program to understand how traditional protections work and why they sometimes fail:
int main() {
char buffer[16];
printf("AO\n");
gets(buffer);
return 0;
}This code contains a classic buffer overflow vulnerability through the notorious gets() function, which reads user input without checking buffer boundaries. When we analyze this binary using tools like checksec, we might find various protections enabled:
- RELRO (Relocation Read-Only): Makes relocations read-only after they're resolved
- Stack Canaries: Places special values between buffers and return addresses to detect overflows
- NX (No-Execute): Prevents execution of code on the stack
- PIE (Position Independent Executable): Randomizes the base address of the executable
The problem is that all these mitigations can be bypassed with sufficient information leakage. For example, a single memory leak might reveal a canary value, allowing an attacker to preserve it during an overflow attack.
Introducing Pointer Authentication Codes (PACs)
The ARM specification 8.3 introduced a revolutionary concept: Pointer Authentication Codes (PACs). This technology creates a cryptographic signature for pointers, making them extremely difficult to forge without access to secret keys stored at a higher privilege level.
PACs work by using a Message Authentication Code (MAC) algorithm to verify whether a pointer has been tampered with. The MAC is stored in the unused high-order bits of 64-bit pointers, taking advantage of the fact that modern systems don't actually use all 64 bits for memory addressing.
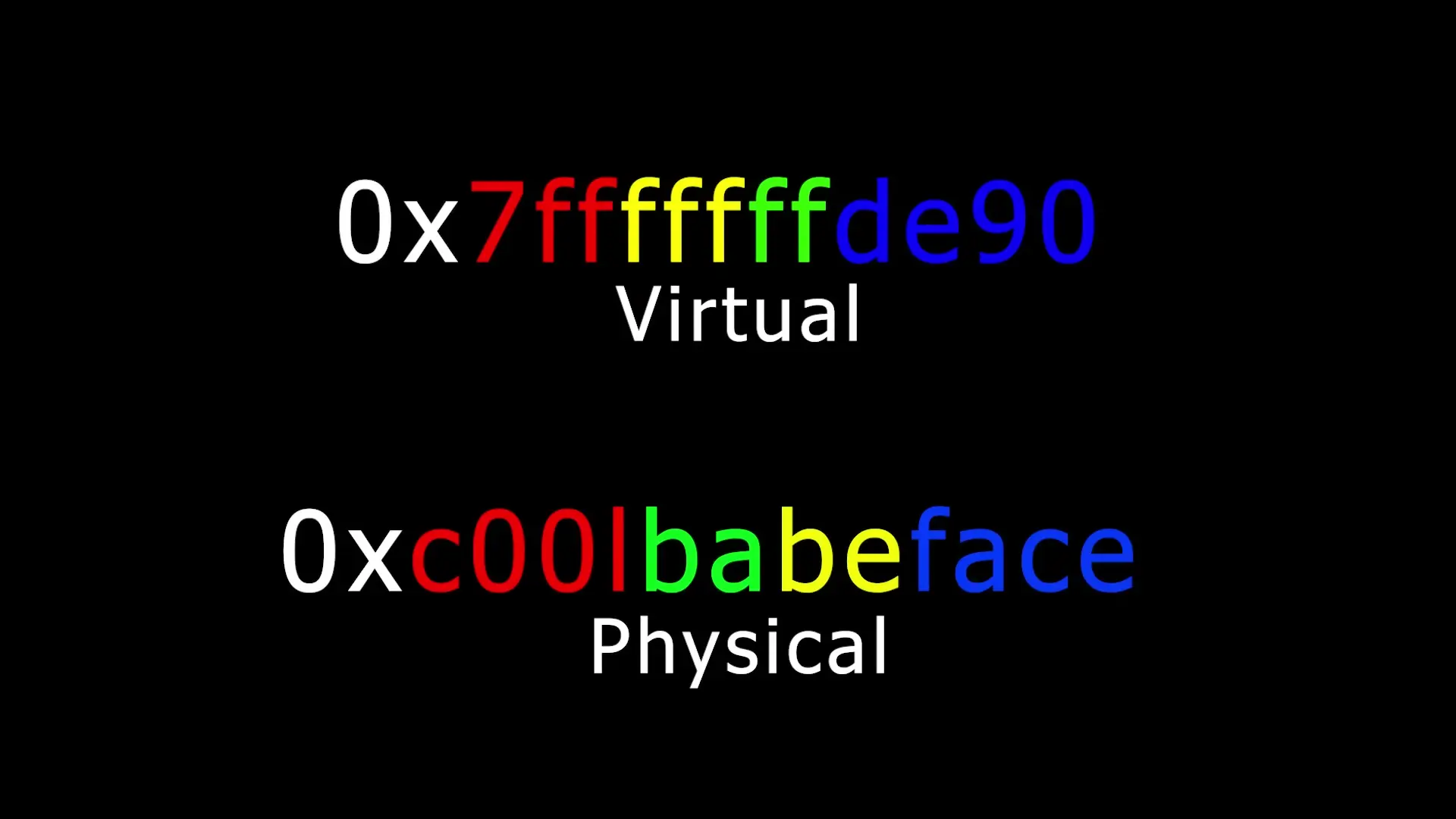
How PACs Create a New Security Boundary
What makes PACs particularly effective is that they establish a new security boundary. The cryptographic keys used to generate and verify these authentication codes are stored in special registers that are only accessible from a higher privilege level (typically the kernel). This means that even if an attacker gains arbitrary read/write capabilities within a process, they cannot generate valid authentication codes without access to these protected keys.
When a function is called, the CPU generates a PAC for the return address and stores it in the unused bits of the pointer. When the function returns, the CPU verifies this authentication code before jumping to the address. If the verification fails (indicating the pointer was tampered with), the CPU generates an exception, preventing the attack.
PACs in Action: Assembly Level Implementation
At the assembly level, PACs introduce new instructions to handle pointer authentication. For example, in ARM64 architecture:
- PACIA: Pointer Authentication Code, using key A for Instruction addresses
- AUTIA: Authenticate Instruction Address using key A
- PACDA: Pointer Authentication Code, using key A for Data addresses
- AUTDA: Authenticate Data Address using key A
When examining the assembly code of a PAC-enabled program, you'll notice these instructions at function entry and exit points. For example, at the beginning of a function, you might see PACIA instructions signing the return address, and at the end, you'll find AUTIA instructions verifying it before returning.
main:
PACIASP ; Sign the return address with key A
... (function body) ...
AUTIASP ; Authenticate return address before returningImplementing PACs in Your Code
Modern compilers like Clang provide built-in functions to work with pointer authentication. For example, you can use the ptrauth.h header in Clang to sign and authenticate pointers explicitly:
#include <ptrauth.h>
struct Data *data = malloc(sizeof(struct Data));
// Sign the pointer
struct Data *signed_data = ptrauth_sign_unauthenticated(data, ptrauth_key_process_dependent_data, 0);
// Later, authenticate the pointer before using it
struct Data *authenticated_data = ptrauth_auth_data(signed_data, ptrauth_key_process_dependent_data, 0);
if (authenticated_data == data) {
print_data(authenticated_data);
}This allows developers to build security boundaries within their applications, cryptographically verifying that sensitive pointers haven't been tampered with before using them.

Benefits and Limitations of Pointer Authentication
The primary benefit of PACs is that they create a cryptographic barrier that's extremely difficult to bypass without access to the secret keys. Unlike other mitigations that can be defeated with a single memory leak, PACs require attackers to either guess a cryptographic signature (practically impossible) or find a way to elevate privileges to access the keys.
- Significantly increases the difficulty of exploiting memory corruption vulnerabilities
- Protects both code pointers (return addresses, function pointers) and data pointers
- Integrates with existing code with minimal performance impact
- Creates a true security boundary between user and kernel space
However, PACs are not a silver bullet. They don't prevent the initial memory corruption, only the exploitation of that corruption. Additionally, they're currently only available on ARM64 architectures that support the PAC feature, though similar concepts are being explored for other architectures.
The Future of Memory Safety
Pointer Authentication Codes represent a significant advancement in the ongoing battle against memory corruption vulnerabilities. As this technology becomes more widespread, we can expect to see it combined with other memory safety techniques to create increasingly robust defenses against exploitation.
While memory-safe programming languages like Rust offer an alternative approach by preventing memory corruption at compile time, PACs provide a hardware-based solution for existing codebases written in languages like C and C++. This allows organizations to enhance the security of their legacy systems without complete rewrites.
As we continue to build more complex software systems, technologies like Pointer Authentication Codes will be essential in creating the secure foundation needed to resist increasingly sophisticated attacks.
Let's Watch!
How Pointer Authentication Codes Revolutionize Memory Safety
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence