
A concerning security vulnerability has emerged in Call of Duty multiplayer games, allowing attackers to execute malicious code on other players' computers during gameplay. This exploit represents a significant security threat that goes beyond typical in-game cheating, potentially giving hackers direct access to victims' systems.

Understanding the Remote Code Execution Vulnerability
The exploit takes advantage of buffer overflow vulnerabilities in the peer-to-peer networking architecture of certain Call of Duty titles. When a player acts as the host in a multiplayer session, their computer processes network packets from all connected players. Attackers can craft specially designed packets that overflow a stack-allocated buffer in the game's network handling code, ultimately allowing them to control what code executes on the host's machine.
This type of attack, known as Remote Code Execution (RCE), can manifest as seemingly harmless pranks like spawning notepad windows or opening browser tabs, but the same technique could potentially be used for more malicious purposes such as stealing personal information or installing malware.
Technical Breakdown of the Exploit
The vulnerability appears to stem from Call of Duty's networking protocol, which is reportedly built on top of a Quake 3-style implementation. By reverse engineering this protocol, security researchers have been able to recreate the networking stack and inject malformed packets that trigger the vulnerability.
At the core of this exploit is a classic buffer overflow attack targeting the stack. When a function executes, it stores local variables and a return pointer on the stack. By overflowing a buffer, attackers can overwrite this return pointer and redirect program execution to their own code.
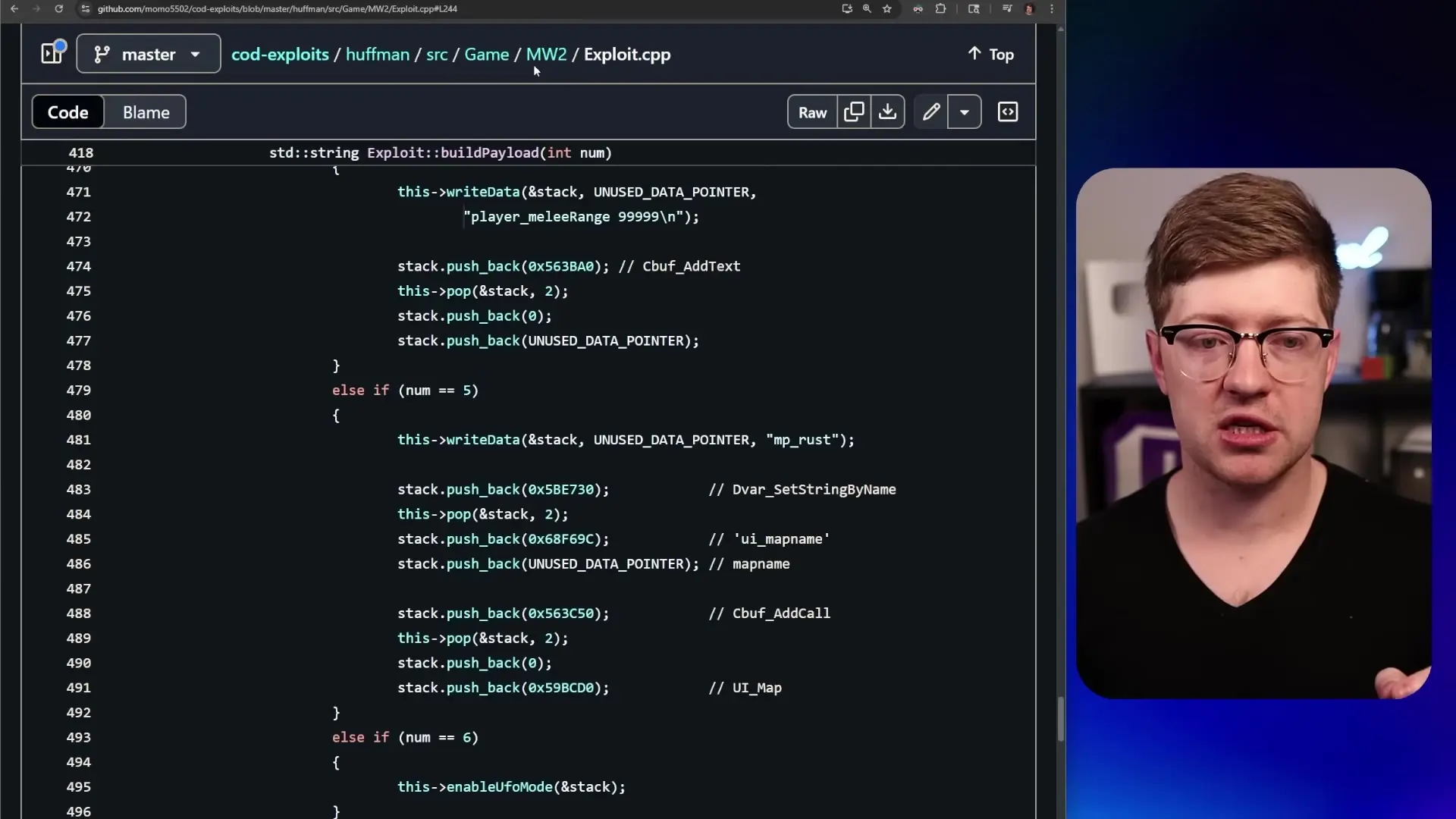
Using a technique called Return-Oriented Programming (ROP), attackers can chain together existing code fragments to perform complex operations like allocating new memory pages, writing shellcode to those pages, changing memory protection settings, and executing the shellcode—all without injecting new executable code directly.
History of the Vulnerability
This isn't the first time such vulnerabilities have appeared in Call of Duty games. Similar exploits were documented as far back as 2017 in earlier titles like Modern Warfare 2. The persistence of these issues suggests that core networking code may have been reused across multiple game iterations without adequate security reviews.
The recent exploits in Call of Duty World War II, particularly the Game Pass PC version, demonstrate that these fundamental security issues continue to plague the franchise.
Why Anti-Cheat Software Doesn't Prevent These Attacks
Traditional anti-cheat systems are designed to detect unauthorized programs interfering with game code or unusual in-game behaviors. However, they're not equipped to identify or prevent memory corruption vulnerabilities in the game's own code.
Anti-cheat software typically monitors for:
- External programs injecting code into the game process
- Unauthorized modifications to game files
- Suspicious input patterns or game state modifications
- Known cheat signatures or behaviors
However, when the vulnerability exists within the game's own networking code, and the attack comes through legitimate game channels (network packets), anti-cheat systems have no way to distinguish malicious packets from legitimate ones.
Which Players Are Most at Risk?
The vulnerability primarily affects players who are serving as the host in peer-to-peer multiplayer sessions. This is most common in games that don't use dedicated servers, such as the Game Pass PC version of Call of Duty World War II.
Players on platforms with dedicated server infrastructure (like Steam versions) or console versions that don't use peer-to-peer hosting may be at lower risk, though the exact implementation details across platforms aren't fully documented.
Protecting Yourself from RCE Exploits
Until these vulnerabilities are patched by the developers, players should consider taking the following precautions:
- Avoid playing on peer-to-peer hosted matches in affected Call of Duty titles
- Opt for versions that use dedicated servers when possible
- Keep your game and system updated with the latest security patches
- Consider using a gaming-specific user account with limited system permissions
- Monitor for unusual system behavior during or after gameplay sessions
The Broader Implications for Game Security
This vulnerability highlights a critical area of game security that often receives less attention than anti-cheat measures. While preventing in-game cheating is important for fair play, protecting players from system-level exploits is essential for basic security.
Game developers need to implement more rigorous security testing for networking code, especially when that code is reused across multiple titles. Memory-safe programming practices, proper input validation, and regular security audits could help prevent these types of vulnerabilities.
Conclusion
The remote code execution exploits in Call of Duty represent a serious security concern that goes beyond typical gaming cheats. By understanding how these vulnerabilities work and taking appropriate precautions, players can better protect themselves while enjoying their favorite games. Meanwhile, this should serve as a wake-up call for the gaming industry to prioritize security as much as gameplay features in future development.
Let's Watch!
Gaming Security Alert: Remote Code Execution Exploits in Call of Duty Multiplayer
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence