
Ubuntu recently announced it will be the first major Linux distribution to adopt Sudo RS, a Rust-based implementation of the sudo command. This decision has sparked both excitement and controversy in the developer community, but understanding the security implications reveals why this architectural change matters.
Understanding Sudo's Security Significance
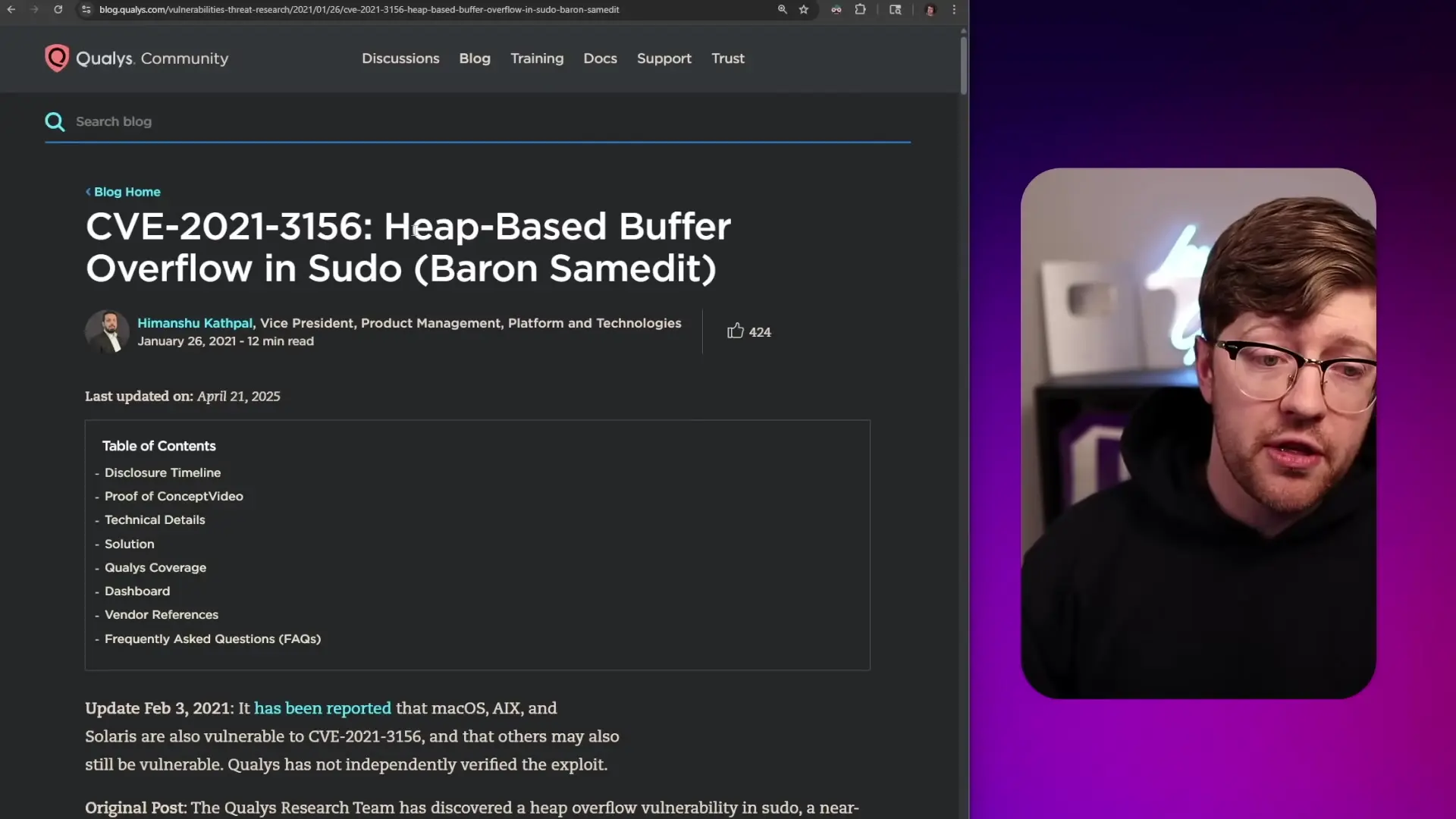
Sudo is a critical component in Linux systems that serves as a privilege boundary. When you run the sudo command, it operates as a set UID binary, meaning it's elevated to the privileges of its owner (root). This functionality is essential for system administration but creates a significant security risk if vulnerabilities exist in the code.
The current C implementation of sudo has experienced several vulnerabilities throughout its history, including heap-based buffer overflows. When such vulnerabilities exist in a set UID binary like sudo, they create privilege escalation primitives—allowing any user to potentially gain root access to the system.
The Memory Safety Advantage of Rust
Rust provides a compelling solution to these security concerns through its memory safety guarantees. Unlike C, Rust's compiler enforces strict memory safety rules that prevent common vulnerabilities like buffer overflows, use-after-free bugs, and data races at compile time.
When a potential memory violation occurs in Rust code, the program will panic and terminate rather than continue execution with corrupted memory—a much safer failure mode than the alternative where attackers can exploit memory corruption to execute arbitrary code.
- Rust eliminates entire classes of memory-related vulnerabilities
- Memory safety is enforced by the compiler, not developer discipline
- Unsafe operations must be explicitly marked, making code reviews more effective
- Memory errors result in program termination rather than exploitable states
According to security researchers, approximately 70% of all software vulnerabilities have been memory corruption related. By addressing this fundamental issue, Rust significantly reduces the attack surface of critical system components.
The Practical Case for Sudo RS
The decision to rewrite sudo in Rust isn't about following trends or replacing working software for the sake of change. It's a strategic security improvement that addresses real-world risks at a critical privilege boundary.
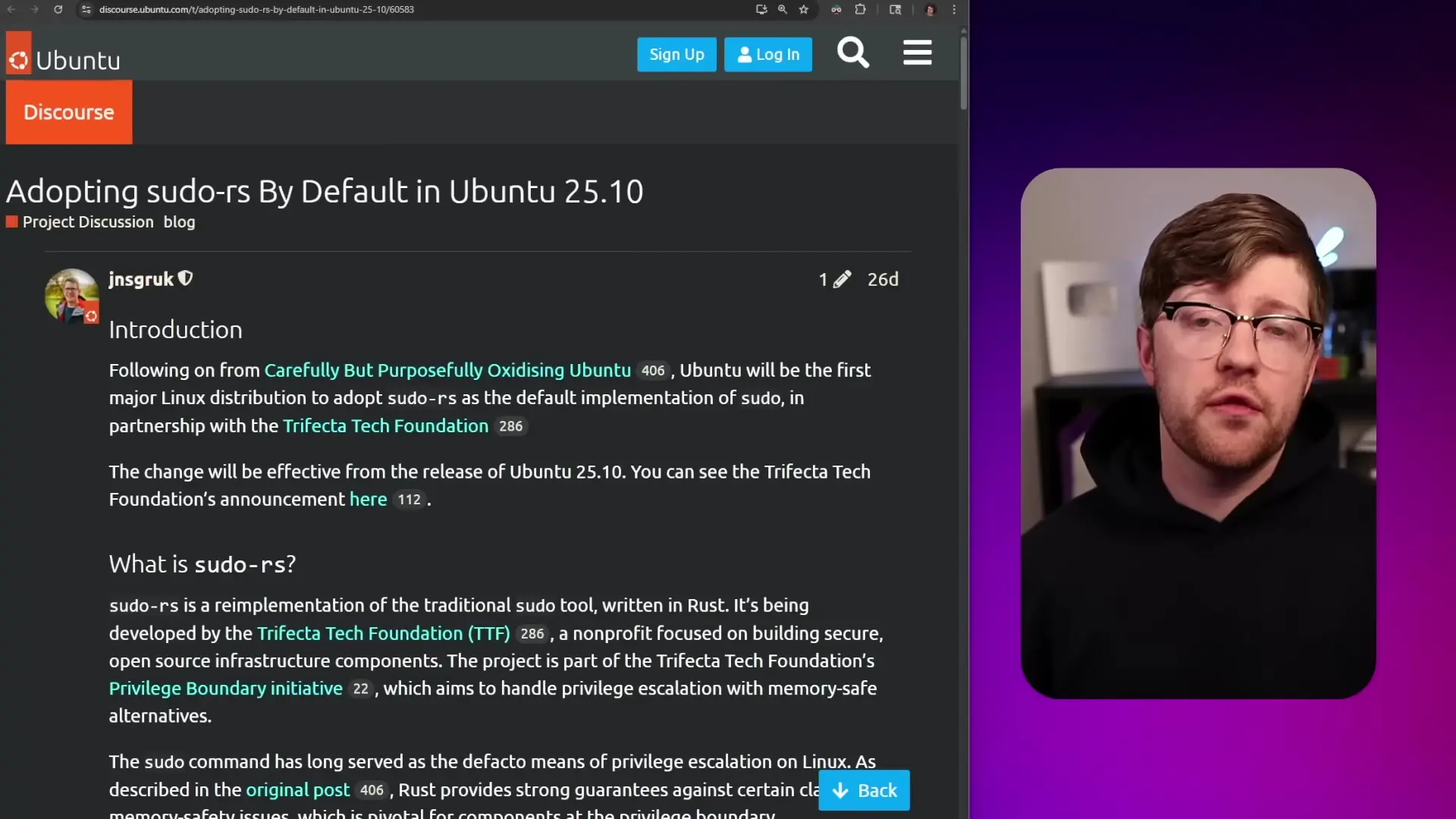
While sudo works correctly most of the time, the consequences of a single vulnerability can be severe. A memory corruption bug in sudo can potentially compromise the entire system, giving attackers root access. By reimplementing sudo in Rust, Ubuntu is proactively addressing this risk vector.
Addressing Common Criticisms
Some critics argue that rewriting working software is unnecessary or that skilled C programmers can write secure code. While experienced developers can certainly write safer C code, the reality is that human error is inevitable. Even seasoned programmers with decades of experience can introduce memory safety bugs that might remain undiscovered until exploited.
Others point to examples of logic bugs in Rust programs as evidence that Rust isn't a security panacea. This criticism misses the point—Rust eliminates memory safety issues but doesn't prevent all bugs. Logic errors, authentication flaws, and other non-memory vulnerabilities can still exist in Rust code. However, removing memory corruption from the equation is still a significant security improvement.
A Targeted Approach to Memory Safety
Not all software needs to be rewritten in Rust. A pragmatic approach focuses on components that stand at privilege or trust boundaries. Software that runs with elevated privileges, processes untrusted input, or mediates access between security domains should prioritize memory safety.
For performance-critical software without security implications, C remains an excellent choice. High-performance libraries like FFmpeg, which powers much of the internet's video processing, benefit from C's performance characteristics and the ability to use inline assembly for optimization.
The Future of System Security
Ubuntu's adoption of Sudo RS represents a significant step toward a more secure computing future. As more critical system components adopt memory-safe implementations, the overall security posture of operating systems will improve.
This approach is particularly important as the software development ecosystem continues to grow. With more developers entering the field and tools like AI code generation becoming commonplace, the risk of memory safety bugs in critical infrastructure increases. Memory-safe languages provide guardrails that protect against these risks regardless of developer experience.
The transition to Rust for sudo demonstrates a thoughtful, security-focused approach to software architecture evolution. Rather than rewriting everything, Ubuntu is strategically targeting a critical security boundary where memory safety provides the most benefit.
Conclusion
Ubuntu's adoption of Sudo RS represents an important milestone in the evolution of system security. By replacing a critical privileged component with a memory-safe implementation, Ubuntu is addressing a significant attack vector and setting a precedent for how security-critical software should be developed.
While Rust isn't the solution to every software security problem, it effectively eliminates an entire class of vulnerabilities that have plagued systems for decades. For components that operate at privilege boundaries, this security improvement is well worth the investment in rewriting established code.
As we look to the future of secure computing, memory safety will likely become a baseline requirement for software that operates in privileged contexts. Ubuntu's move is an early step in what may become a broader shift toward safer system architectures.
Let's Watch!
Why Sudo's Rust Makeover Matters for Linux Security
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence