
In the cybersecurity world, alarming headlines about massive data breaches can trigger panic and contribute to developer burnout. Recently, headlines claiming "16 billion passwords exposed in record-breaking data breach" spread across major publications, suggesting unprecedented access to credentials from platforms like Facebook, Google, and Apple. But before you reset every password you own, let's examine what's really happening behind these sensationalist claims.
Dissecting the '16 Billion Password' Headline
When you first encounter a headline about 16 billion exposed passwords—roughly two passwords for every human on Earth—it's natural to assume a catastrophic breach has occurred at a major tech company. However, security experts quickly clarified that this wasn't a new breach at all, but rather a compilation of previously leaked credentials collected over time.
Bleeping Computer and other reputable security sources confirmed that these credentials weren't freshly stolen but instead represented an aggregation of data from various sources, including:
- Credentials harvested by info-stealer malware over time
- Data from previous breaches that had already been disclosed
- Credentials obtained through credential stuffing attacks
- Information compiled from various dark web marketplaces
This clarification is crucial for developers who might feel overwhelmed by the constant barrage of security threats, potentially leading to developer burnout when trying to address every headline-making vulnerability.
Understanding Info-Stealers: The Real Threat
While the 16 billion figure may be misleading in context, info-stealer malware remains a legitimate security concern that developers should understand.
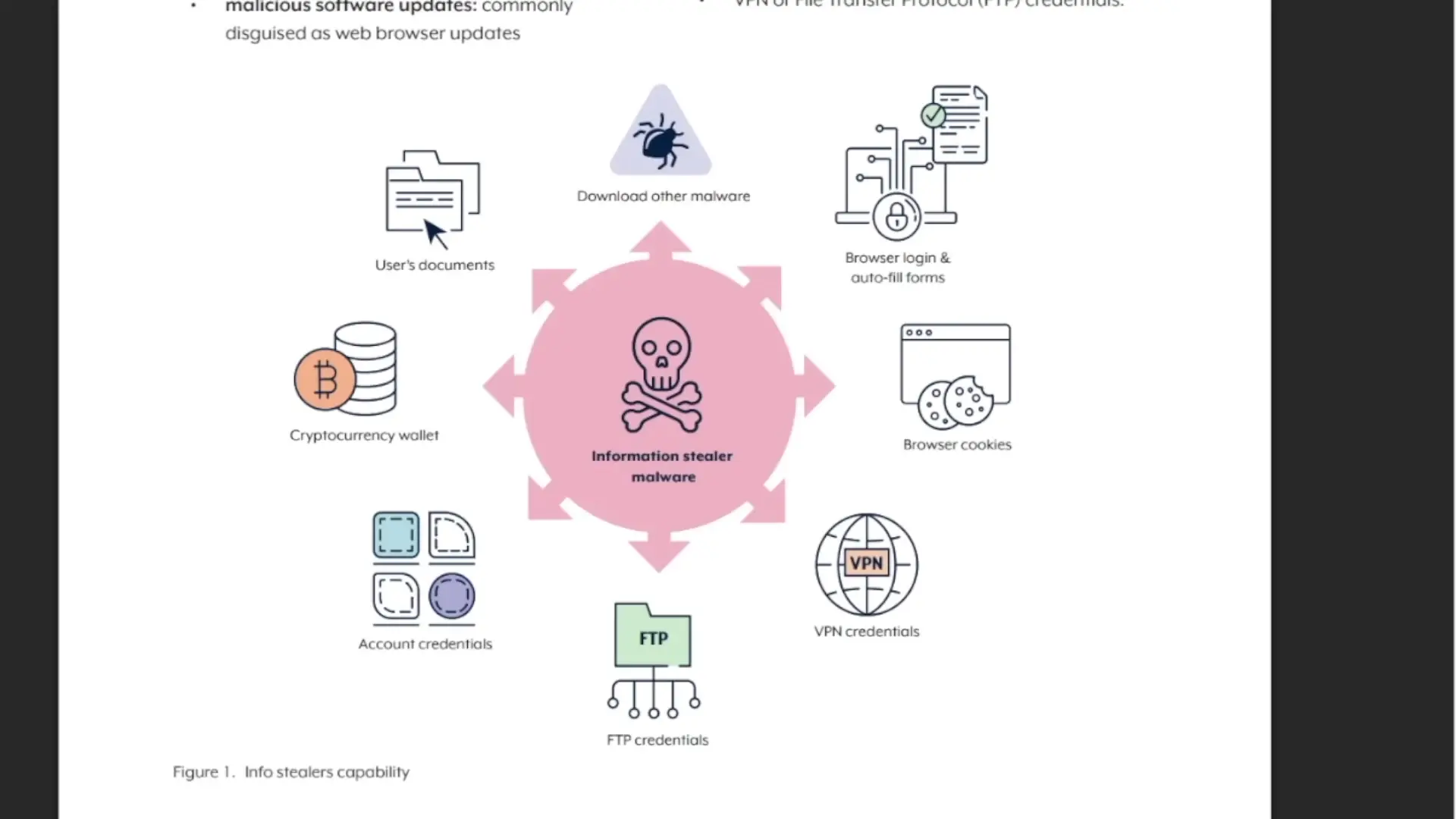
Info-stealers are malicious programs designed to extract sensitive information from infected systems. They typically operate by:
- Searching for credentials stored in browsers and applications
- Locating decrypted credentials in memory or at rest
- Extracting the information and sending it to command and control (C2) servers
- Enabling attackers to use these credentials for account takeovers
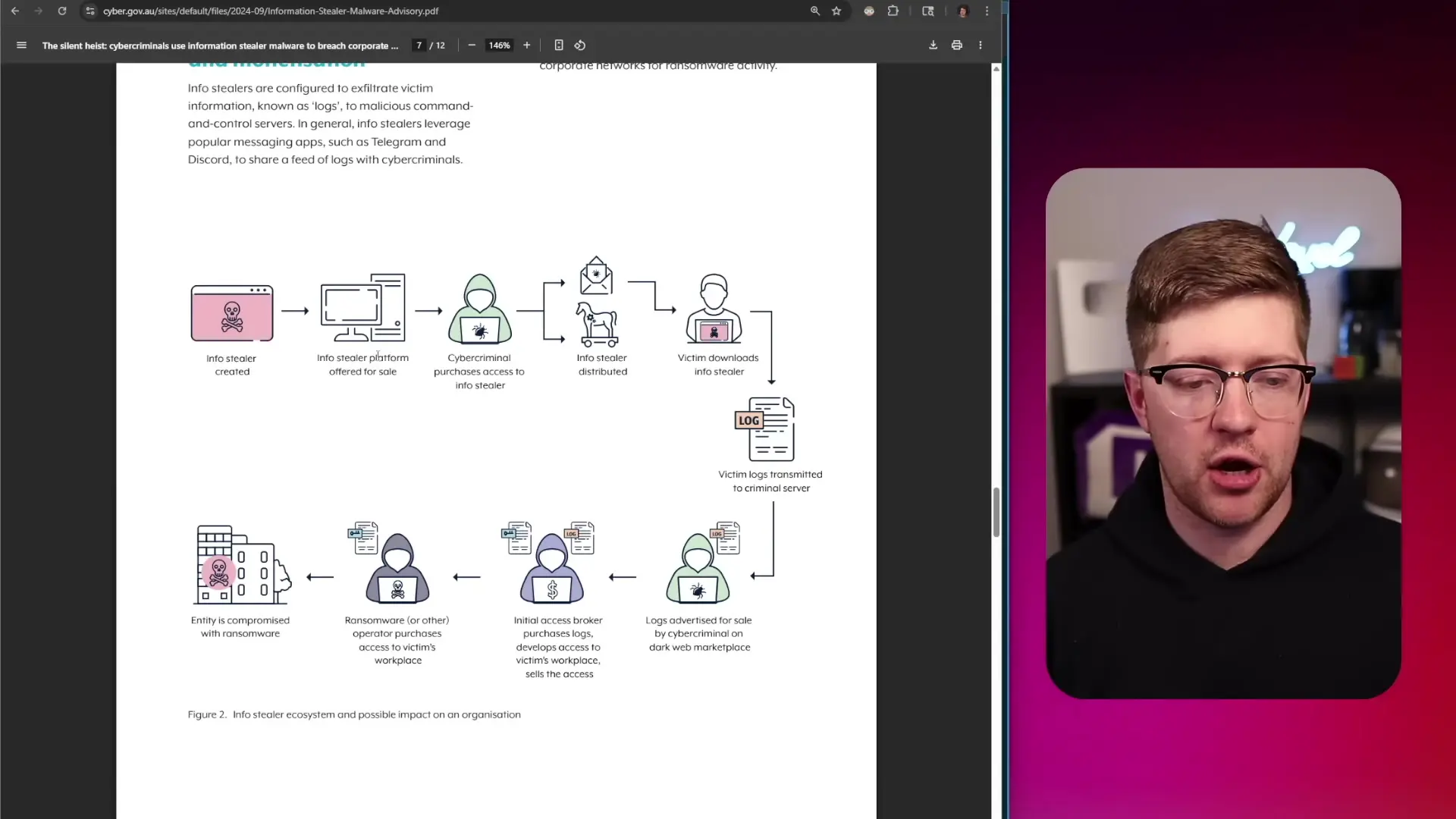
The typical attack flow involves malware authors creating and distributing their tools through various channels. Victims become infected through phishing, social engineering, or exploitation of vulnerabilities. Once installed, the malware harvests credentials and sends them to attackers who can then sell or use them for further attacks.
The Danger of Cybersecurity Clickbait
Sensationalist reporting in cybersecurity doesn't just misinform—it can actively harm security efforts and contribute to developer fatigue. When major publications like Forbes amplify misleading claims without proper verification, several negative consequences follow:
- Security alert fatigue leads to developers ignoring even legitimate threats
- Organizations may misallocate resources to address non-existent or overstated threats
- Users become desensitized to security warnings, potentially ignoring critical advisories
- The spread of fear, uncertainty, and doubt (FUD) undermines rational security planning
- Developer burnout increases as teams scramble to address each new "catastrophic" threat
When headlines suggest that major platforms like Google or Apple have been directly compromised, it creates unnecessary panic. For developers responsible for security, constantly responding to these alarms can lead to significant burnout and prevent them from focusing on genuine security improvements.
Practical Security Measures for Developers
Rather than reacting to every alarming headline, developers should focus on implementing these fundamental security practices to prevent credential theft and reduce security-related burnout:
- Use a reputable password manager (like Apple Keychain, 1Password, or Bitwarden)
- Implement multi-factor authentication (MFA) for all sensitive accounts
- Avoid SMS-based two-factor authentication in favor of authenticator apps
- Consider hardware security keys that implement FIDO2/WebAuthn standards
- Adopt passkey technology where available to eliminate password vulnerabilities
- Regularly review authorized applications and revoke unnecessary access
- Keep systems and applications updated to protect against known vulnerabilities
Understanding Passkeys: The Future of Authentication
One promising development in credential security is the adoption of passkeys. Unlike traditional passwords, passkeys use asymmetric cryptography (public-private key pairs) to authenticate users without transmitting or storing a shared secret.
Passkeys offer several advantages that can help prevent developer burnout from password management concerns:
- Phishing resistance: Since there's no shared secret to steal, phishing becomes ineffective
- No password to remember: Reduces cognitive load and the need for password rotation
- Strong security by default: Uses cryptographic keys rather than guessable strings
- Cross-device compatibility: Modern implementations work across multiple platforms
- Reduced attack surface: Eliminates password database breaches
// Example of WebAuthn registration in JavaScript
async function registerPasskey(username) {
// Get challenge from server
const challenge = await fetchRegistrationChallenge(username);
// Create credentials using WebAuthn API
const credential = await navigator.credentials.create({
publicKey: {
challenge: base64URLToBuffer(challenge),
rp: { name: "Your Service", id: "example.com" },
user: {
id: new TextEncoder().encode(username),
name: username,
displayName: username
},
pubKeyCredParams: [{ type: "public-key", alg: -7 }],
authenticatorSelection: {
authenticatorAttachment: "platform",
userVerification: "required"
}
}
});
// Send credential to server for verification
return sendCredentialToServer(credential);
}Evaluating Security News to Prevent Developer Fatigue
To avoid developer burnout from constantly responding to security headlines, establish a framework for evaluating security news:
- Check multiple reputable sources before acting on security news
- Look for technical details rather than sensationalist claims
- Assess the actual impact on your systems and users
- Prioritize response based on real risk, not headline size
- Develop standard procedures for common threat types to reduce decision fatigue
By implementing these strategies, developers can maintain good security hygiene without succumbing to the fatigue that comes from reacting to every alarming headline.
Conclusion: Balancing Security Awareness and Developer Wellbeing
While security threats like info-stealers are real, the cybersecurity industry's tendency toward sensationalism can lead to unnecessary panic and developer burnout. By focusing on fundamental security practices, adopting modern authentication methods like passkeys, and critically evaluating security news, developers can maintain robust security without the constant stress of responding to exaggerated threats.
Remember that good security is about consistent practices rather than reactive responses to headlines. By implementing proper password management, using multi-factor authentication, and staying informed through reputable sources, you can protect your systems and users while preventing the developer fatigue that comes from security alarmism.
Let's Watch!
The Truth About the '16 Billion Password Leak': Security Facts vs Clickbait
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence