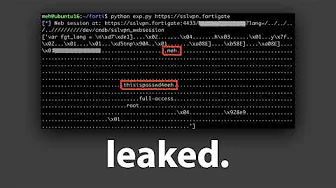
A significant security crisis is unfolding for FortiGate, a major provider of network security solutions. Hackers have leaked configuration files, VPN credentials, and private keys for over 15,000 FortiGate devices on the dark web. This breach follows a troubling pattern, as a similar incident in 2021 exposed credentials for approximately 500,000 FortiGate VPN accounts. These repeated security failures raise serious questions about the security architecture of devices that are specifically designed to protect networks.
The Scope of the FortiGate Security Breach
The latest leak involves a massive 1.6 GB archive containing sensitive information from thousands of FortiGate devices. All compromised devices were running FortiOS versions 7.0.6 through 7.2.2, indicating that unpatched vulnerabilities are at the heart of this security disaster. The leaked data includes IP addresses, configuration files, and even private keys that could give attackers complete access to these security devices.
What makes this situation particularly alarming is that these are not ordinary devices - FortiGate produces Next Generation Firewalls (NGFW) that organizations rely on as their primary network security defense. These devices are specifically designed with dedicated processors for network traffic forwarding, content inspection, and security rule application.
How the Vulnerabilities Work: Authentication Bypass and More
The most recent attacks exploited a critical authentication bypass vulnerability (CVE-2022-40684) discovered in 2022. This vulnerability allows attackers to forward packets through the firewall and execute administrative commands without proper authentication. The exploit works by manipulating HTTP headers to trick the firewall's internal communication system.
The vulnerability stems from a fundamental flaw in how the device handles inter-process communication. By adding a specific forwarded header to an HTTP request, attackers can convince the firewall that an unauthenticated packet is actually an internal, trusted communication. The firewall fails to validate that the header information matches the actual source of the request, creating a critical security hole.
Using this vulnerability, attackers can arbitrarily add SSH public keys to the firewall and then establish SSH connections with the corresponding private key, gaining administrative access to the device. For this attack to work, the firewall must have SSH exposed to the internet - a common configuration for administrative access.
Previous Vulnerabilities: Directory Traversal and Memory Dumping
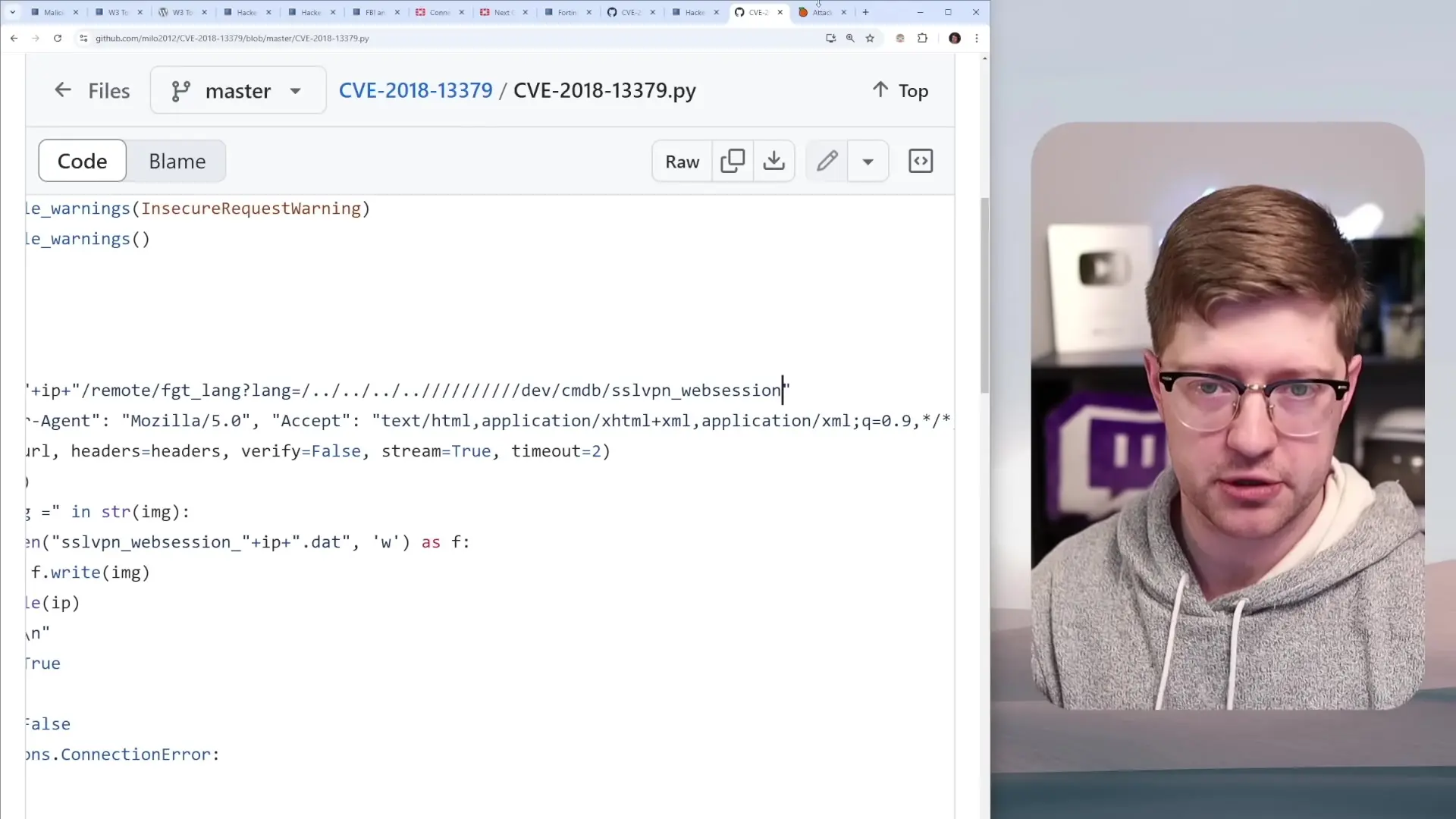
The 2021 breach exploited a vulnerability from 2018 (CVE-2018-13379) that allowed for arbitrary file reading without authentication. This was a directory traversal vulnerability with a twist - instead of using the traditional "../" pattern, attackers could manipulate the language parameter to access sensitive files.
By setting the language parameter to a specific pattern and padding it to 40 bytes, attackers could access a device file that contained the raw memory of web sessions. This memory dump revealed plaintext passwords and other sensitive information.
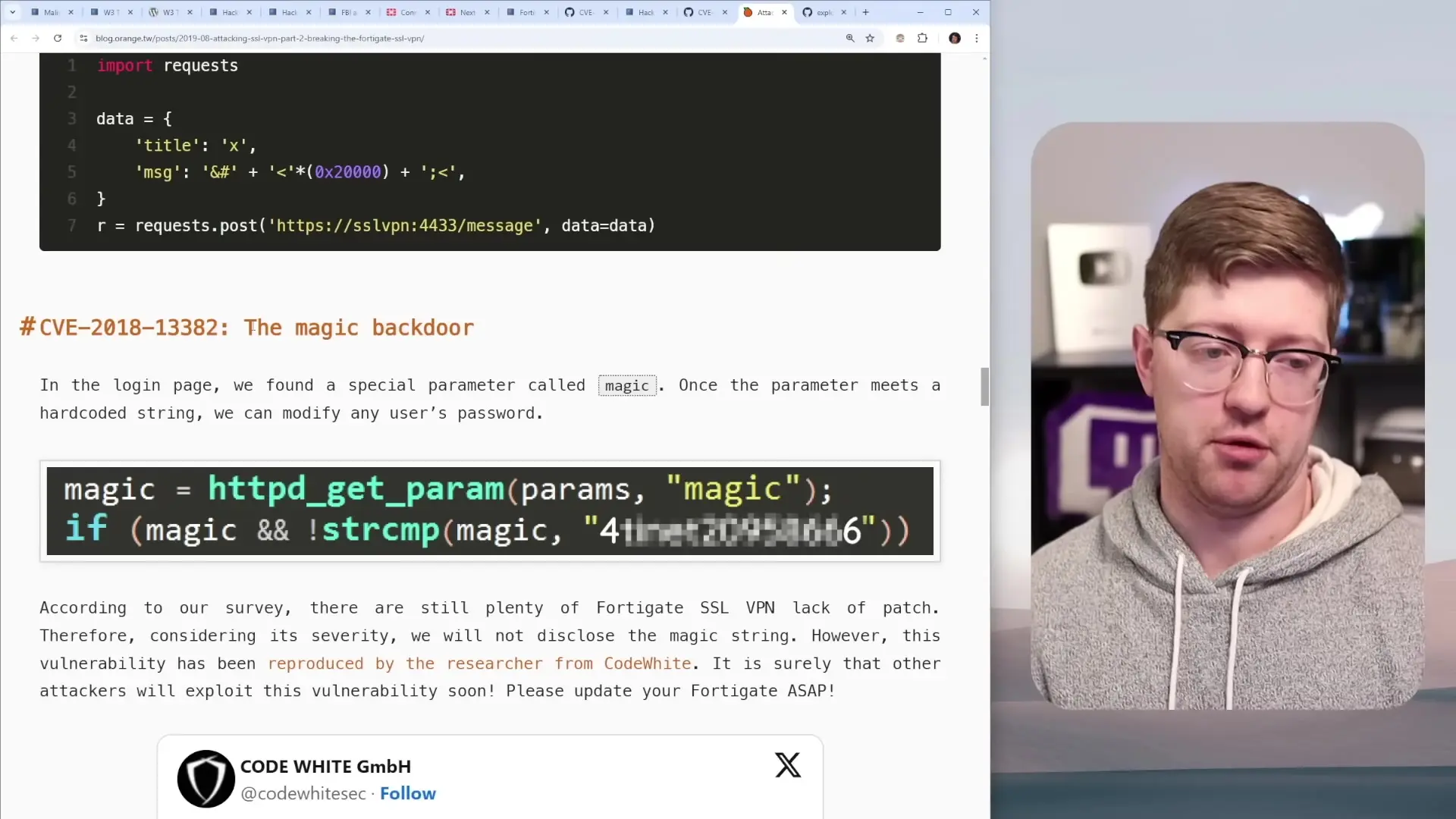
The "Magic" Backdoor: Intentional or Negligent?
Perhaps the most disturbing finding was what security researchers called a "magic" backdoor. During their investigation, researchers discovered a special parameter called "magic" in the login page. When this parameter matched a hard-coded string in the firmware, it allowed anyone to modify any user's password without authentication.
This is not merely a vulnerability but appears to be an intentionally created backdoor. With no credentials required beyond knowing a username, attackers could reset passwords and gain administrative access to the firewall. This type of backdoor represents an extreme security risk and raises serious questions about FortiGate's development practices.
Security Implications and Best Practices
These vulnerabilities highlight several critical security concerns for organizations using network security appliances:
- Firmware updates are absolutely critical - many compromised devices were running outdated versions with known vulnerabilities
- Security devices themselves must be scrutinized - even dedicated security appliances can contain serious vulnerabilities or backdoors
- Administrative interfaces should never be directly exposed to the internet without additional protection layers
- Regular security audits should include penetration testing of network security devices
- Organizations should implement defense in depth, not relying solely on perimeter firewalls for security
Understanding the Nature of Software Backdoors
Software backdoors represent one of the most serious threats in cybersecurity. Unlike typical vulnerabilities that result from coding mistakes, backdoors are often deliberately implemented features that bypass normal authentication mechanisms. They can be added by developers for legitimate purposes like troubleshooting or emergency access, but they fundamentally undermine security by creating privileged access paths that circumvent normal security controls.
The "magic" parameter backdoor discovered in FortiGate devices is particularly concerning because it appears to be an intentional feature. The presence of a hard-coded string that, when matched, allows password changes suggests deliberate implementation rather than an accidental vulnerability. This raises serious ethical questions about security product development and transparency.
Conclusion: The Ongoing Challenge of Security Device Trust
The repeated security breaches affecting FortiGate devices highlight a fundamental challenge in cybersecurity: how can organizations trust the very devices designed to protect them? When security appliances contain vulnerabilities or backdoors, they transform from defensive assets into potential entry points for attackers.
For organizations using FortiGate devices, immediate patching is essential. More broadly, this situation serves as a reminder that security is a continuous process requiring vigilance at all levels - even with dedicated security devices. The presence of apparent backdoors in security products also emphasizes the need for greater transparency and accountability from security vendors.
As security professionals continue to defend against increasingly sophisticated threats, they must remember that no single device or vendor can provide complete protection. A comprehensive security strategy must include regular updates, defense in depth, and a healthy skepticism about the security of security products themselves.
Let's Watch!
Uncovering Hidden Backdoors in FortiGate Firewalls: A Security Crisis
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence