
Virtual machines (VMs) are widely considered secure sandboxes where potentially malicious code can be safely executed without affecting the host system. But how true is this assumption? While VMs are designed to isolate guest environments from the host operating system, certain vulnerabilities in hypervisor code can create pathways for malware to escape containment and compromise your host machine.
What is a Virtual Machine Escape Bug?
A virtual machine escape bug is a vulnerability that allows code running inside a guest VM to break out of its isolation and execute commands on the host operating system. These exploits target flaws in the hypervisor code—the software layer that creates and manages virtual machines. While rare, these vulnerabilities represent a significant security concern for anyone using virtualization technology.
VM escape vulnerabilities are particularly dangerous because they undermine the fundamental security principle that makes virtual machines useful for security testing in the first place: isolation. When this isolation is compromised, any malware running in the guest environment could potentially gain access to sensitive data or execute arbitrary code on the host system.
Understanding VM Architecture and Security Boundaries
To understand how VM escape vulnerabilities work, we need to first understand the architecture of virtual machines and how they maintain isolation. Virtual machines rely on memory management units (MMUs) and CPU features that create mappings between physical and virtual memory. These mechanisms ensure that the memory of the guest cannot interact with the memory of the host, creating the sandbox environment.
However, there's an important exception to this isolation: device interfaces. For a VM to be useful, it needs to interact with real hardware components like screens, network adapters, and other peripherals. These interfaces represent necessary communication channels between the guest and host environments—and they're precisely where VM escape vulnerabilities typically emerge.
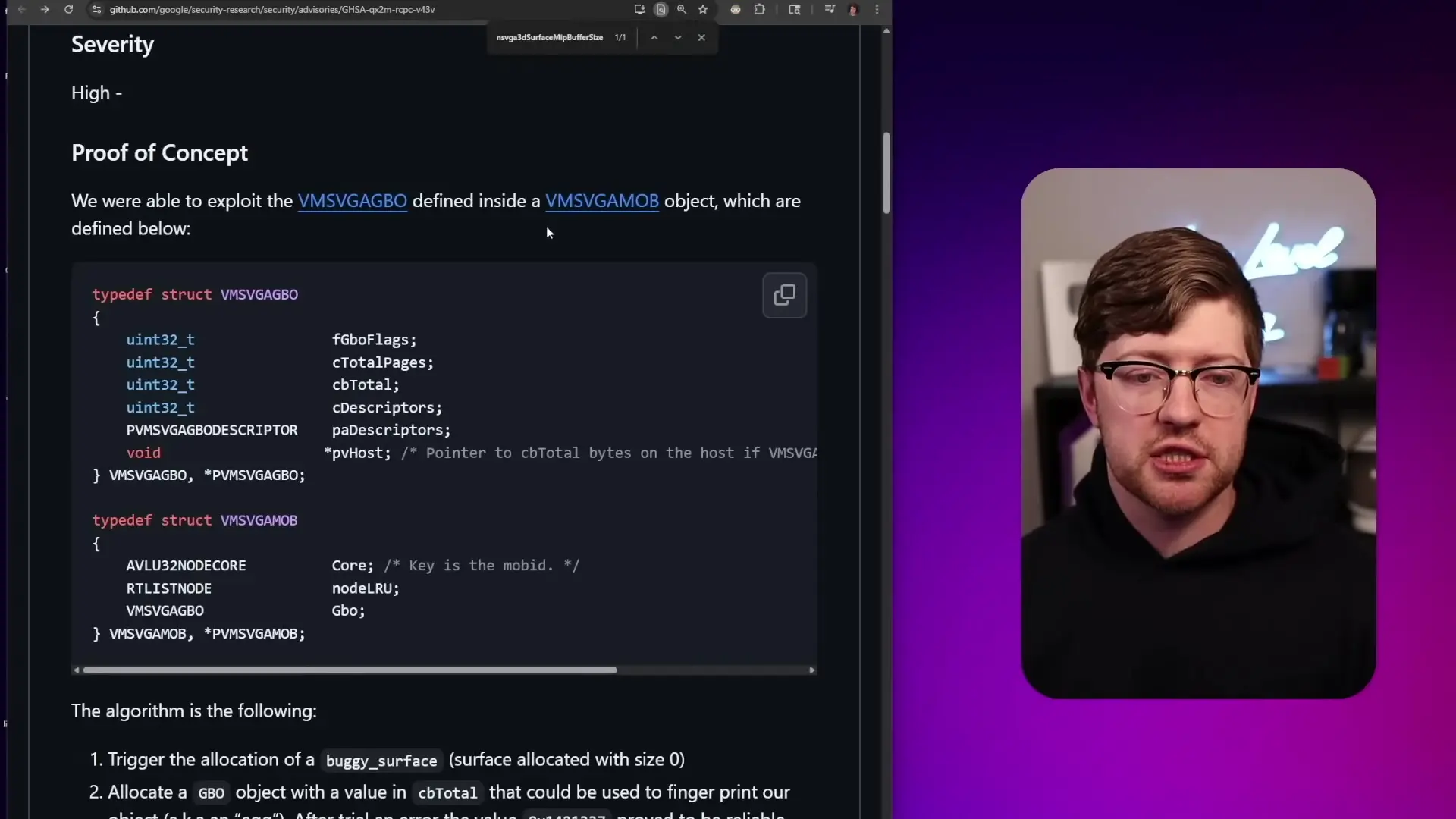
Case Study: VirtualBox VGA Interface Vulnerability
One notable example of a VM escape vulnerability was discovered in VirtualBox's VGA interface. This vulnerability involved an integer overflow in the VM SVGA 3D surface MIP buffer size function. Let's break down how this exploit works:
- The vulnerability allowed attackers to manipulate memory allocation so that zero bytes were allocated for a buffer
- However, VirtualBox incorrectly tracked the size of this buffer as being greater than zero
- This mismatch between actual and tracked buffer size created an exploitable condition
- By requesting a surface with specific dimensions that would cause an integer overflow when multiplied
- The attacker could create a situation where data could be read beyond intended boundaries
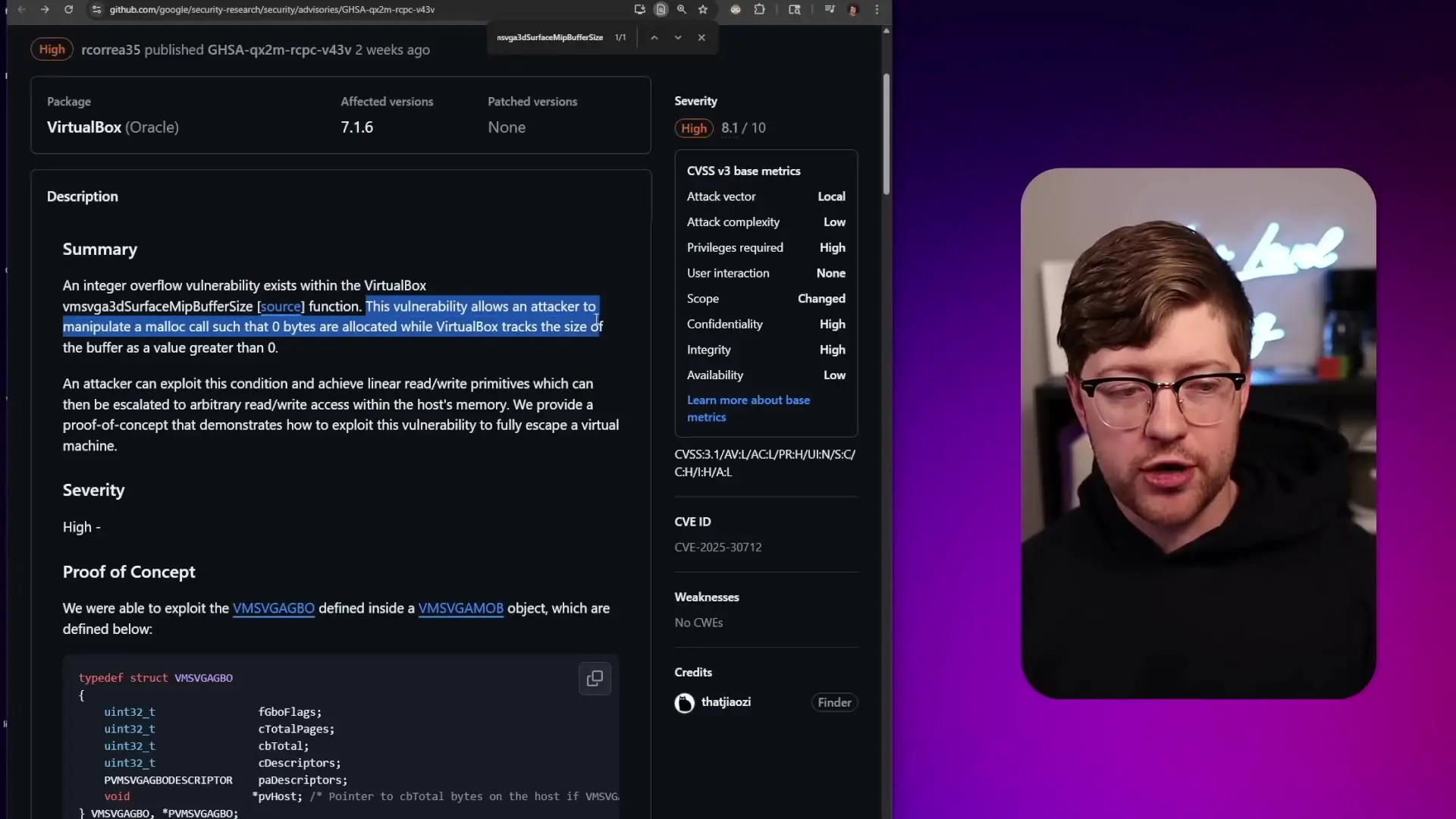
This vulnerability allowed attackers to perform arbitrary reads of host kernel memory, effectively bypassing Address Space Layout Randomization (ASLR)—a critical security feature. By leaking details about the memory map of the host operating system, attackers could then perform arbitrary writes, eventually gaining the ability to execute code on the host system.
The Mechanics of VM Escape Exploits
VM escape exploits typically follow a pattern of vulnerability exploitation that involves several stages:
- Identifying a vulnerability in device emulation code (network adapters, graphics cards, etc.)
- Exploiting the vulnerability to gain read access to host memory
- Using the leaked information to bypass security protections like ASLR
- Leveraging the information to achieve arbitrary write capabilities
- Overwriting function pointers or other control structures to execute arbitrary code
- Escalating privileges on the host system
In the VirtualBox case, the exploit used a zero-width surface to leak memory from the kernel. By copying data from this corrupted surface to a valid transfer surface, attackers could request readbacks that contained host system memory content. This information disclosure vulnerability then enabled further exploitation.
Other Examples: Network Adapter Vulnerabilities
VM escape vulnerabilities aren't limited to graphics interfaces. Another documented example involved a vulnerability in a VirtIO network adapter driver. In this case, an attacker was able to disable the standard driver inside the virtual machine, instantiate a custom kernel-mode driver that exploited a vulnerability in the VirtIO implementation, and ultimately execute code on the host system.
This type of exploit demonstrates that any code that must run on the host OS to support VM functionality represents a potential attack surface. If there are bugs in this code, they can potentially be exploited by a determined attacker.
Mitigating the Risk of VM Escape Vulnerabilities
While VM escape vulnerabilities are concerning, there are several steps you can take to minimize the risk:
- Keep your hypervisor software updated with the latest security patches
- Minimize the attack surface by disabling unnecessary device emulation
- Use nested virtualization when testing particularly suspicious code
- Consider using more hardened virtualization solutions for high-security environments
- Implement network segmentation to limit the impact of a potential VM escape
- Monitor for unusual activity that might indicate exploitation attempts
The Reality of VM Escape Threats
It's important to put VM escape vulnerabilities in perspective. Successfully exploiting these vulnerabilities is extremely complex and requires significant expertise. The likelihood of an average user encountering malware capable of VM escape is relatively low. However, for high-value targets or in environments where virtualization is used as a primary security boundary, these threats should be taken seriously.
The existence of VM escape bugs reminds us that no security measure is perfect. Every sandbox is ultimately just code, and all code can potentially contain bugs. As attackers become more sophisticated, awareness of these vulnerabilities becomes increasingly important for security professionals and system administrators.
Conclusion
Virtual machines remain a valuable and generally effective security tool, providing isolation that helps protect host systems from malicious code. However, the existence of VM escape vulnerabilities demonstrates that this protection isn't absolute. Understanding the mechanisms behind these exploits and taking appropriate precautions can help ensure that your virtualized environments remain as secure as possible.
For security professionals, these vulnerabilities highlight the importance of defense in depth—never relying on a single security boundary, no matter how robust it may seem. By staying informed about emerging threats and maintaining good security practices, you can continue to benefit from virtualization technology while minimizing the associated risks.
Let's Watch!
Virtual Machine Escape: How Secure is Your VM Against Malware?
Ready to enhance your neural network?
Access our quantum knowledge cores and upgrade your programming abilities.
Initialize Training Sequence